Hacking Activity of SectorD Group in 2019
SectorD Group Overview
A total of 15 subgroups of SectorD have been found to date. They perform hacking activities for the purpose of gathering high-quality information such as politics and diplomacy about individuals or countries that oppose the SectorD government. This article presents a summary of monthly activities of the SectorD Group which were discovered in 2019.
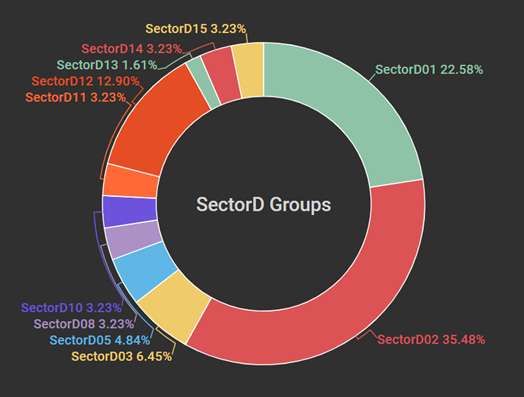
Figure 1 SectorD subgroup activity in 2019
SectorD groups tend to attack geographically close countries and mainly targets enterprises, universities, IT companies, research institutes, energy industries. They attach malicious documents to spear phishing emails and use known vulnerabilities to attack. Of the 15 groups, the activities of the SectorD02 group were most prominent this year, followed by the SectorD01 and SectorD12 groups.
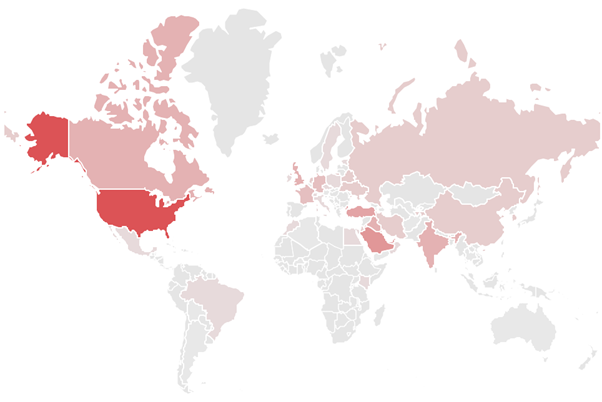
Below is a map of the countries that were targeted by the SectorD Group in 2019. The darker the red, the more frequent the attack. This shows that the SectorD Group has conducted frequent hacking activities against their neighboring countries in the Middle East and the United States.
Figure 2 The main target countries for the SectorD Group in 2019
Hacking Activity of SectorD Groups in 2019
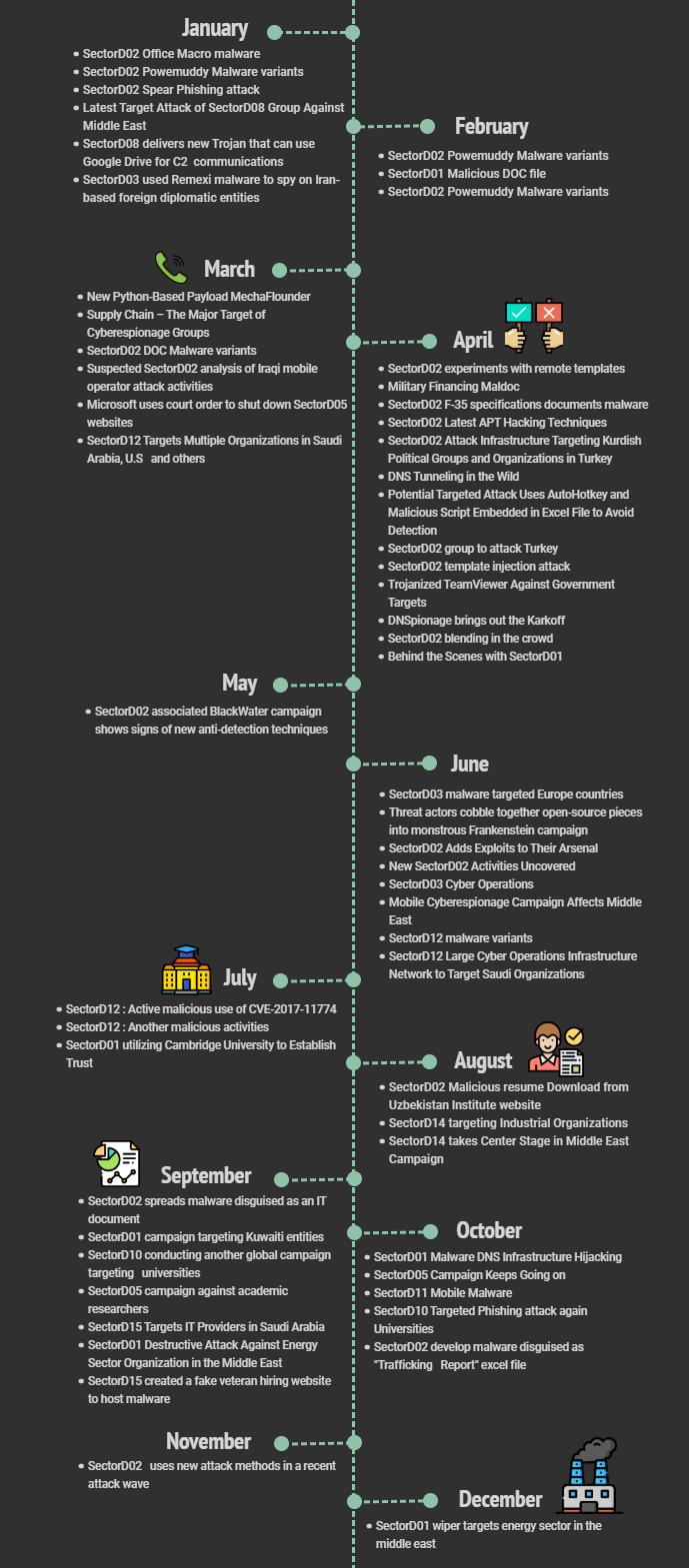
The following is a timeline and detailed monthly activity of the SectorD groups hacking activity found in 2019.
Figure 3 Timeline of main activities for the SectorD Group in 2019
January
SectorD targets were Europe including Belarus, Ukraine, and Sweden, East Asia including South Korea, and the Middle East centering on Saudi Arabia, Turkey, and Oman. Two hacking groups were found to be active.
Outside of the Middle East, their purpose seem to be to steal diplomatic related information from countries which have political and economic cooperation with other countries in the Middle East, such as Europe and East Asia. In particular, South Korea recently had diplomatic progress in which it agreed to cooperate in seven areas through summit talks with Qatar.
Hacking techniques used by SectorD continue to include spear phishing with Microsoft Word files which contained malicious macros.
Based on their hacking activities so far, it appears that SectorD is starting to expand its scope to include hacking countries with political and economic cooperation with Middle Eastern countries, rather than solely targeting countries in the Middle East.
April
A total of four hacking groups, SectorD01, SectorD02, SectorD05 and SectorD12 were found among SectorD hacking groups this April, with hacking activity targeted at countries in the Middle East, including the Sector’s political competitor Saudi Arabia, the United Arab Emirates, Jordan, Iraq and Turkey, and Ukraine, Estonia, Germany, and the United States, as well as South and East Asia.
SectorD hacking groups basically used Spear Phishing techniques with malware and example phishing documents were word files using confidential U.S. State Department forms. At the same time, malware in the form of compressed files that abused the recently discovered WinRAR’s vulnerability were also found. SectorD hacking groups mainly collected political, military and diplomatic information from countries in the Middle East that are its political competitors.
However, with the recent declaration of noncompliance with some treaties of a Nuclear Agreement it is part of, hacking aimed at collecting information on government activities are expected to intensify as conflicts are expected with other countries in many areas, including politics and diplomacy.
May
In May, a total of two hacking groups were found among SectorD groups. They perform hacking activities mainly on other Middle Eastern countries which they have political tensions with.
The SectorD01 group mainly conducted hacking activities for the purpose of collecting information using spear phishing emails with Microsoft Excel files that contain malicious macros, and malware using AutoHotKey and TeamViewer, both of which they have not used in the past.
The SectorD02 group also conducted hacking campaigns in the Middle East. They used spear phishing with malware for initial access, just like most other Sector groups. Recently, they used open-source penetration testing tools in their attacks, which seems to be an attempt to not leave traces of attack activity.
June
In June, a total of two hacking groups were found among SectorD groups. They targeted countries in the Middle East which they have a politically competitive relation with. Activities of each group were found in the following countries: SectorD02 group activity was discovered extensively in Middle Asia to Middle East, mainly in Hong Kong, Sweden, Tajikistan, United Arab Emirates, Saudi Arabia, Iraq, Jordan, France, United States and Mexico. SectorD11 group activity was discovered in Middle Asia to Middle East.
They are constantly using spear phishing emails attached to Microsoft Office document files. In particular, obfuscated macro scripts and PowerShell code are embedded in these document files to download additional malware. The SectorD11 group also develops and distributes malware that runs on Android smartphones for the purpose of monitoring civilians who are against SectorD government.
Currently, the SectorD hacking groups have increased the frequency of hacking activities against Western countries. This is mainly targeting the United States, which they have political and military disputes with, but also a pro-American nation in the Middle East. It is likely that the activities of SectorD hacking groups will be greatly dependent on how the US exerts its influence and military activities in the future.
August
Among the SectorD groups, the activities of two hacking groups, SectorD02 and SectorD14 were found among SectorD hacking groups this August.
The hacking activity of SectorD02 group was found in Tajikistan and Uzbekistan.
The hacking activity of SectorD14 group has been found in Canada, United States, United Arab Emirates and Kuwait. In particular, the SectorD14 group conducted hacking activities on Industrial Control Systems (ICS) owned by government agencies, and natural gas and oil companies related to countries located in the Middle East, which may be related to a recent drone attack.
The basic hacking techniques of the SectorD groups are similar to those in the past, using a Microsoft Word file with a malicious macro as an attachment to a spear phishing email.
At the moment, diplomatic measures involving the SectorD group’s government are under way in Western countries, mainly in the United States, and the aforementioned physical attacks on oil fields in Saudi Arabia may soon lead to cyber wars with physical conflicts between the Middle East and Western countries.
September
A total of six hacking groups, SectorD01, SectorD02, SectorD05, SectorD10, SectorD14, and SectorD15 were found among SectorD hacking groups this September.
SectorD hacking groups targeted countries which are political rivals with the SectorD government. Their hacking activity discovered in September targeted countries located in the Middle East (including Morocco, Kuwait and the United Arab Emirates), and other hacking targets were the United States, the United Kingdom, Canada, India, the Netherlands, the Philippines, Azerbaijan, Kenya, China, Australia, Hong Kong and Switzerland.
The basic hacking techniques of the SectorD groups are similar to the previous cases – sending a Microsoft Word file with a malicious macro to the hacking target using an attachment in a spear phishing email. In addition to these hacking techniques, the SectorD05 group has launched attacks against researchers from the United States, Middle East, and France, focusing on academic research on SectorD, or performing phishing attacks against people targeting SectorD dissidents in the United States.
The SectorD10 group also uses links in phishing emails to direct targets to spoofing sites that are disguised as user login pages, and perform hacking activities to steal user credentials entered by targeted individuals.
The SectorD15 group conducted hacking activity aimed at gathering information on IT suppliers located in Saudi Arabia, which is likely to lead to a supply chain attack.
At the moment, diplomatic measures involving the SectorD government are underway in Western countries, mainly the United States. Such diplomatic activities could eventually lead to physical conflicts between countries, and it may be that these hacking activities are being used in cyberspace as preliminary reconnaissance.
October
A total of six hacking groups SectorD01, SectorD02, SectorD05, SectorD10, SectorD11 and SectorD15 were discovered among SectorD groups this October. Hacking activity of the SectorD01 group was found in the United States and Ireland. Hacking activity of the SectorD02 group was found in Lebanon, Ireland, Iraq, South Korea and Canada. Hacking activity of the SectorD05 group was found in the United States and Israel. Hacking activity of the SectorD10 group was found in the United States. Hacking activity of the SectorD11 group was found in France, Saudi Arabia, the United States, Netherlands, Brazil and Russia. Hacking activity of the SectorD15 group was found in Algeria, the United Kingdom, the United Arab Emirates, Saudi Arabia and the United States.
The SectorD01 group modified malware that had DNS tunneling functions first discovered in November 2018 and reused it in this hacking activity.
The SectorD02 group attached a Microsoft Excel file containing a malicious macro to a spear phishing email. After that, the encoded VBS script would be decoded and executed using the the legitimate wscript.exe.
The SectorD05 group used social media to post malicious links that redirect to specific websites, or send SMS messages containing malicious links to individuals of opposition about government agencies. Sometime they used spear phishing emails that included malicious links.
The SectorD10 group was primarily hacking into universities in the United States and used emails containing malicious links redirect to phishing sites.
The SectorD11 group produced malicious APK files written in Persian and wanted to collect information from hacked Android-based smartphones.
The SectorD15 group created malicious websites using an American Gulf War veterans theme. The website, which says it will hire veterans, sends the input information to the attacker’s server.
SectorD groups conducted hacking activities targeting countries that are related to political rivalries to a certain country. The purpose of the recent hacking activities of the SectorD groups is to collect high-level information such as political and diplomatic activities of people or nations opposed to a specific government.
November
The SectorD15 group created malicious websites using an American Gulf War veterans theme. The website, which says it will hire veterans, sends the input information to the attacker’s server.
SectorD groups conducted hacking activities targeting countries that are related to political rivalries to a certain country. The purpose of the recent hacking activities of the SectorD groups is to collect high-level information such as political and diplomatic activities of people or nations opposed to a specific government.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.