Hacking Activity of SectorC Group in 2019
SectorC Group Overview
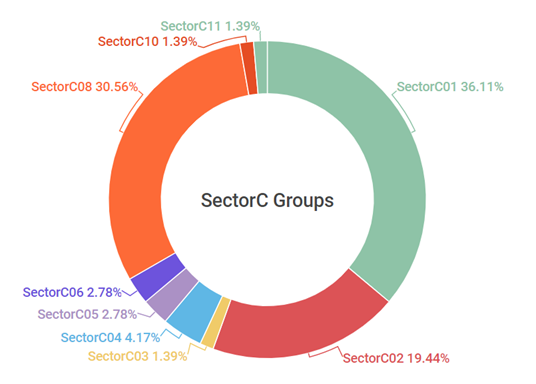
A total of 11 subgroups of SectorC have been found to date. In 2019, the activities of the SectorC01 group were most prominent, followed by the activities of the SectorC08 and SectorC02 groups. SectorC groups conduct extensive hacking activities around the world, and their activities are mainly found in SectorC’s neighboring countries.
[Figure 1: SectorC subgroup activity in 2019]
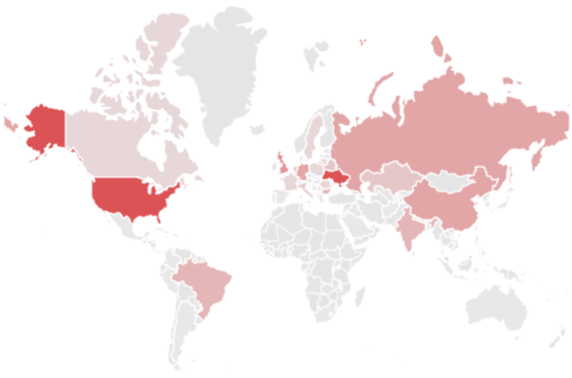
They aim to collect high-level information on political and diplomatic activities. Shown in red are the countries that the SectorC groups mainly targeted in 2019. The higher the frequency of hacking activity, the darker the color.
[Figure 2: The main target countries for SectorC groups in 2019]
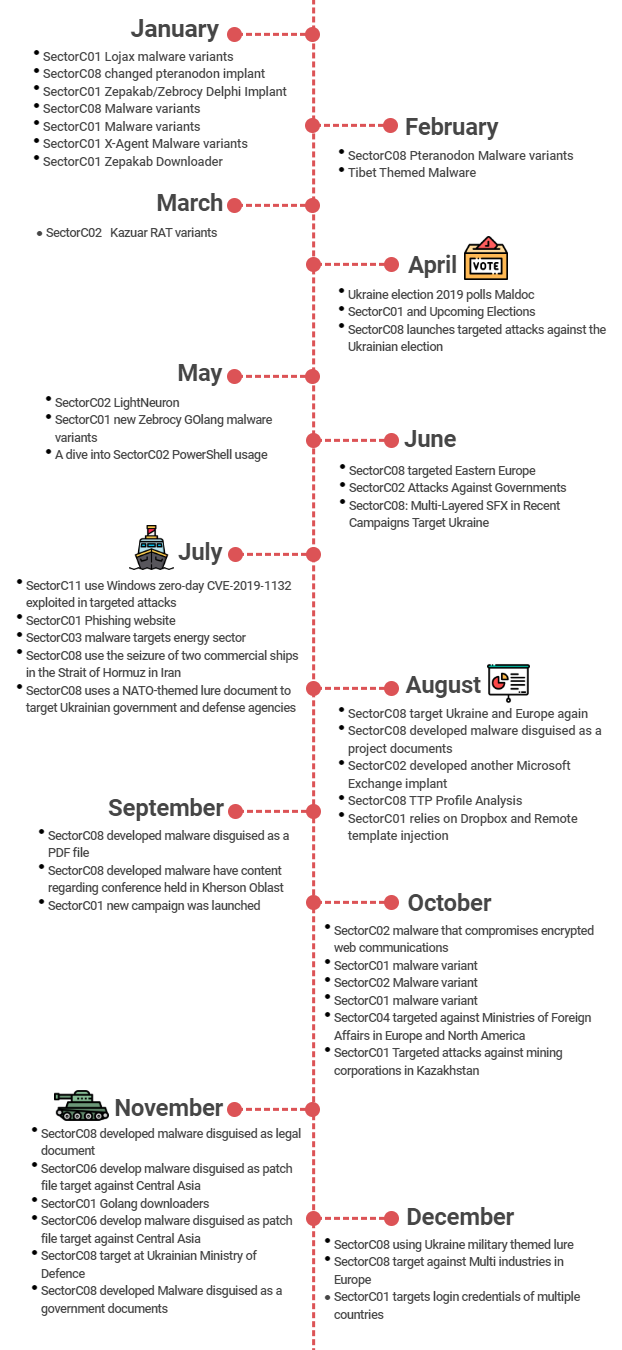
Below is the hacking activity timeline for the SectorC groups discovered in 2019.
[Figure 3: Timeline for SectorC group hacking activities in 2019]
Hacking Activity of SectorC Groups in 2019
The following is a description of the SectorC group’s monthly hacking activities.
January
SectorC targets included countries in Eastern Europe including Ukraine, Poland, Macedonia, and North America including the United States. Three hacking groups were found to be active.
Although hacking groups supported by SectorC have the characteristics of having very fast technological and strategic changes, but their malware continues to have identified characteristics of previous versions.
Their activities in Eastern Europe seem to be aimed at stealing information on military activities related to the North Atlantic Treaty Organization (NATO) and their activities in North America seem to be aimed at stealing information related to government activities.
Since SectorC is currently engaged in hacking activities in Eastern Europe and North America, it seems likely that their political and military related espionage will continue in those regions.
February
SectorC groups was found to have activity in a total of three hacking groups this February. Areas of activity are Eastern Europe (including Belarus and Ukraine), and North America (including the United States).
The basic hacking technique is like the past, with the code execution vulnerability present in the Microsoft Office suite and spear phishing with malicious code in the form of a Word file or PowerPoint file containing a macro designed for malicious purposes. Hacking activity targeting Eastern Europe uses malicious script files within 7ZipSFX files to gain initial infection.
Active areas of the SectorC hacking groups are recently found in countries in North America and Europe. They continue their hacking activity aimed at collecting high-level political and diplomatic information related to Western countries.
April
A total of three hacking groups, SectorC01, SectorC02, and SectorC10 were found among SectorC hacking groups this April, with hacking activity targeted at countries in Europe and North America, including Britain, the United States, and Germany.
This April, SectorC hacking groups aimed at stealing information on political and diplomatic activities in European countries. They basically used Spear Phishing techniques with malware and tried to target the presidential elections in certain Eastern European countries.
In addition, SectorC10 hacking activity targeting ICS/SCADA environments has been discovered, and this group has various capabilities and tools, such as WebShells, Backdoors, and performing Credential Harvesting and Remote Command Execution.
May
In May, a total of three hacking groups were found among the SectorC groups. They perform hacking activities mainly in Europe, South America, and Eastern Europe where political friction is frequent.
The SectorC01 group mainly utilized malware recently produced in the GO language for this month. This seems to be a strategic choice because the GO programming language has heterogeneous portability and high utilization.
The SectorC02 group installs information-collecting malware which targets Microsoft Exchange Servers. This is similar to malware used in hacking campaigns in countries located in Europe in the past and seems to be aimed at stealing e-mail information that can be used for various purposes.
The SectorC08 group conducts intensive hacking activities targeting countries in Eastern Europe where political friction continues. The malicious code found in May was in the form of an executable compressed file, 7ZipSFX, which has the characteristics of using both script files and known normal files together. This is like the activities of the SectorC08 group found in the past.
June
A total of three hacking groups, SectorC02, SectorC08, SectorC11 were found among the SectorC groups in June. They were active mainly in Europe – Moldova, Ukraine and Germany – where they frequently have political friction with.
They are constantly using spear phishing emails with malware, but there are gradual changes in the characteristics of the attached executable files. They continue to use open source programs such as the remote-control programs, UltraVNC, and start to develop their malware with open source code. This is presumably done to bypass security solutions and analyst detection and interferes with intelligence analysis efforts to track attackers.
SectorC groups are expected to continue hacking activities in countries which it has political and diplomatic conflicts with for the time being.
July
Among SectorC groups, a total of four hacking groups were found this July, including SectorC01, SectorsC02, SectorC08 and SectorC11 groups.
The four hacking group’s activities were found in Asia (including Singapore, China, India and Afghanistan), in Europe (including Germany, France and Ukraine), and South America (including Brazil) and Middle East (including Kuwait).
The target organizations of the SectorC hacking groups identified were mainly government agencies, financial institutions, investment institutions and non-profit organizations.
The SectorC01 group forged a legitimate fake website and encourage targets to enter their information on the phishing website.
The SectorC02 group steal important email information from Microsoft Exchange Server among internal systems connected to the Internet. Like other past hacking activities, the SectorC08 Group limits its activity to Europe. Spear phishing emails attached with 7ZipSfx were used as a major hacking technique. SectorC11 similarly utilizes spear phishing emails, but they use attachment documents that exploit Microsoft Office vulnerabilities. In July, the SectorC11 group utilized CVE-2019-1132, a zero-day vulnerability.
SectorC groups operates with a wide variety of technical spectra, as they have the history of being one of the oldest hacking groups. They continue to carry out several activities that match up the political purposes of the Russian government, so similar forms of hacking are likely to continue in the future.
August
Among the SectorC groups, the activities of three hacking groups, SectorC02, SecotorC03 and SectorC08 were found among SectorC hacking groups this August.
The hacking activity of SectorC02 group has been found in Brazil, Georgia. The hacking activity of SectorC03 group has been found in United States and United Kingdom. The hacking activity of SectorC08 group has been found in Ukraine, United Kingdom, Belarus, Sweden, Argentina, United States and China.
The SectorC groups used different attack vectors. SectorC02 group stole sensitive email information from internal Microsoft Exchange servers connected to the Internet while the SecotorC03 and SectorC08 groups used spear phishing emails with malware as their primary hacking technique, like their other hacking activities found in the past. However, the SectorC08 group has the characteristic of using 7ZipSfx compressed files as attachments against specific hacking targets.
The SectorC groups have many more attack technique at their disposal than threat actors of other groups because of their long history. Recently, they have been working to achieve the political objectives of their government, and this is expected to continue.
September
A total of two hacking groups, SectorC01 and SectorC08, were found among SectorC hacking groups this September.
SectorC01 group activity was found in Europe and North America (including Ukraine, Canada, Belgium and the United Kingdom), while SectorC08 group activity was found in Ukraine, China, the United States, South Korea and Brazil. The SectorC08 group used to hack only in Europe in the past, but this is the first time that hacking activity has been found in East Asia (including China and South Korea), and additional analysis of their purpose is required. Although the SectorC groups, where hacking activity was found, use different hacking techniques, their spear phishing emails display common characteristics.
The SectorC01 group attaches Microsoft Word document malware to spear phishing emails and uses remote template injection techniques to deliver malware in Microsoft Word files containing macro scripts to their targets.
Like past hacking cases, the SectorC08 group maintains their traditional hacking approach using spear phishing emails with 7ZipSPX compressed files attached. However, we also confirmed that their hacking activity uses the remote template injection method, and the text content of the lure document used for the template injection was related to a specific conference.
The SectorC groups have many varied attack techniques because of their long history, and they are likely to continue a similar form of hacking in the future, as they continue to do so in line with the political objectives of the SectorC government.
October
A total of three hacking groups, SectorC01, SectorC02 and SectorC04 were discovered among SectorC groups this October. Hacking activity of the SectorC01 group was found in the United States, Belarus, United Kingdom, Belgium, Ukraine and Canada. Hacking activity of the SectorC02 group was found in Belarus, Russian Federation, United Kingdom, Sweden, Georgia, Bulgaria, Brazil and Italy. Hacking activity of the SectorC04 group was found in Israel, Romania and Moldova.
The SectorC01 group used a spear phishing email which had an MS Word file attached. When executing the document file, it downloads a remote template hosted on Dropbox to download and execute a document which had a malicious macro script.
The SectorC02 group lured victims with malware disguised as legitimate software from illegal software download sites (warez) and monitors victim’s networks activity.
The SectorC04 group’s hacking campaign targeted government agencies performing diplomatic affairs. They used a spear phishing email that contained a link, and when the link was clicked, an image containing malware which was created with stenography was downloaded.
The purpose of the hacking activities of the SectorC groups to date is to collect high-level information such as information on political and diplomatic activities in countries that are located near to the government agencies supporting SectorC.
November
Among the Russian government backed SectorC groups, a total of three hacking groups were discovered this November, including SectorC01, SectorC06 and SectorC08.
SectorC01 group’s hacking activity was found in areas including Kazakhstan. The SectorC01 group used a spear phishing email with MS Word (Word) file. The document type malware named “gorodpavlodar.doc”, was distributed targeting to large mining companies in Kazakhstan.
SectorC06 group’s hacking activity was found in areas including China, Kazakhstan and Netherlands. The SectorC06 group attempted to hack using news from the past that Telegram messenger could be banned in Kazakhstan, which would allow them remote access to infected computers. This malware is like their malware discovered in the past. The identified file is a compressed file, containing an executable file using a document file icon.
SectorC08 group’s hacking activity was found in areas including the Italy, Bulgaria, United States and Ukraine. The SectorC08 group used spear phishing emails with malware in the form of MS Word files which used Remote Template Injection.
The purpose of the hacking activities of the SectorC groups to date is to collect high-level information such as political and diplomatic activities in countries that are located near to the government agencies supporting SectorC.
December
A total of two hacking groups, SectorC01 and SectorC08, were discovered among SectorC groups this December.
SectorC01 group’s hacking activity was found in areas including Germany, Australia, Canada, Peru, Poland, Malaysia, Japan, Mexico, South Africa, Sweden, Singapore, United States and China. SectorC08 group’s hacking activity was found in areas including Netherlands, Russia, Singapore, United States, Italy, Bulgaria, Lithuania, India, Ukraine, and Latvia.
The SectorC01 group attempted phishing to steal login credentials from US international intelligence agencies. The group used an international government department’s email service to disguise the courier service website.
The SectorC08 group used remote templates injection technique. The purpose of the hacking activities of the SectorC groups to date is to collect high-level information such as political and diplomatic activities in countries that are located near to the country supporting SectorC.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.