Threat Actor Groups use COVID-19 pandemic theme
1. Executive Summary
The worldwide epidemic of Corona virus (COVID-19) affects more than 1.2 million people in 212 countries. For the APT group, which mainly uses social engineering techniques as the initial infection, the Corona virus is a good topic to attract the attention of targets. Accordingly, several hacking activities of the APT group who recently exploited the Corona virus have been discovered.
The ThreatRecon team has identified hacking activities that have exploited the Corona virus in about 27 countries to date. The attacker mainly used the current report, news articles, etc. related to the Corona virus to create a malware that contains a macro script or vulnerability. Among these hacking activities, in addition to malware in the form of document files, malwares of types such as shortcut (LNK) files and Android (APK) files were identified.
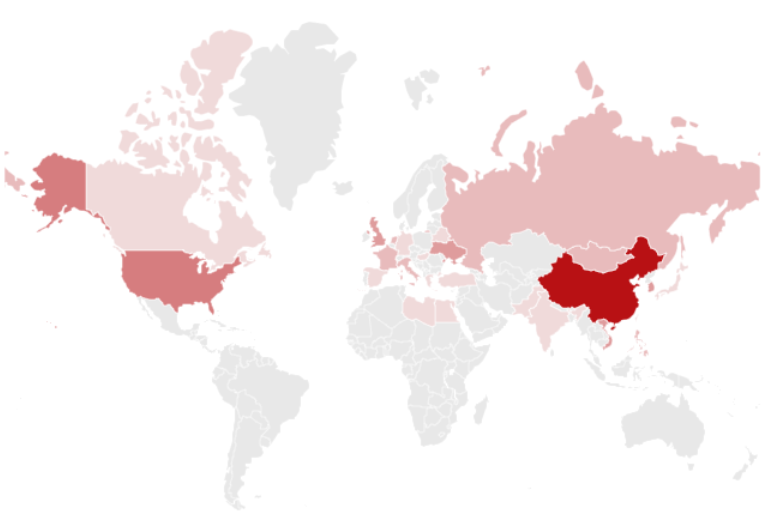
The following the countries in which hacking activity that used corona virus theme has occurred to date. The darker the color means the more frequently the attack occurred that country.
[Figure 1: Countries where hacking activity that used Corona virus theme is found]
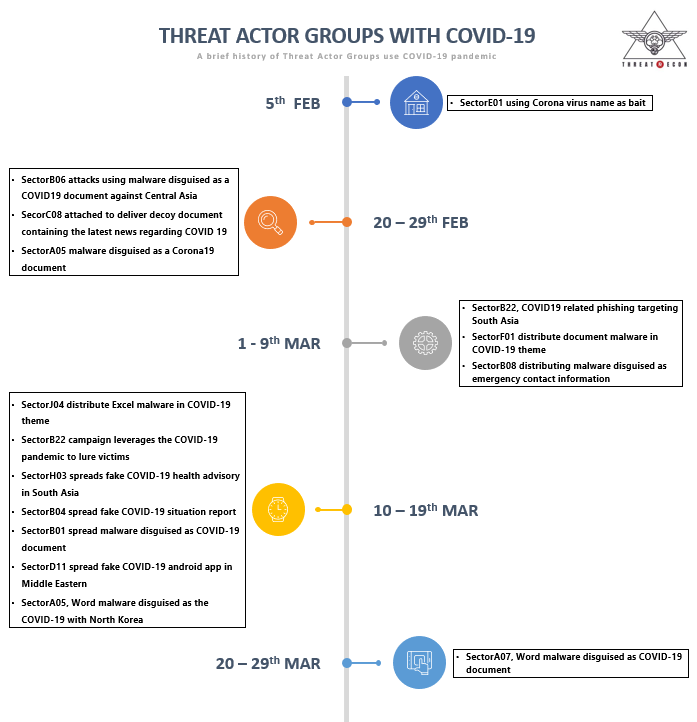
The following is a timeline of hacking activity using the Corona virus theme found from February to March 2020. This hacking activity began to take place in earnest in March.
[Figure 2: Timeline of hacking activity using Corona virus theme]
2. Hacking activity using the Corona Virus (COVID-19) theme
In a total of 13 hacking groups, hacking activities used corona virus theme were identified. The contents of malware in the form of document files found in mostly hacking activities was identical to the contents of an actual news article or report. The following is a hacking activity for each group with the theme of Corona virus.
2-1) SectorA Groups: Malware disguised as Guidelines for Corona Virus
The activities of the SectorA05 and SectorA07 groups in SectorA were discovered, these activities have been found in South Korea, the United States, the United Kingdom, and China.
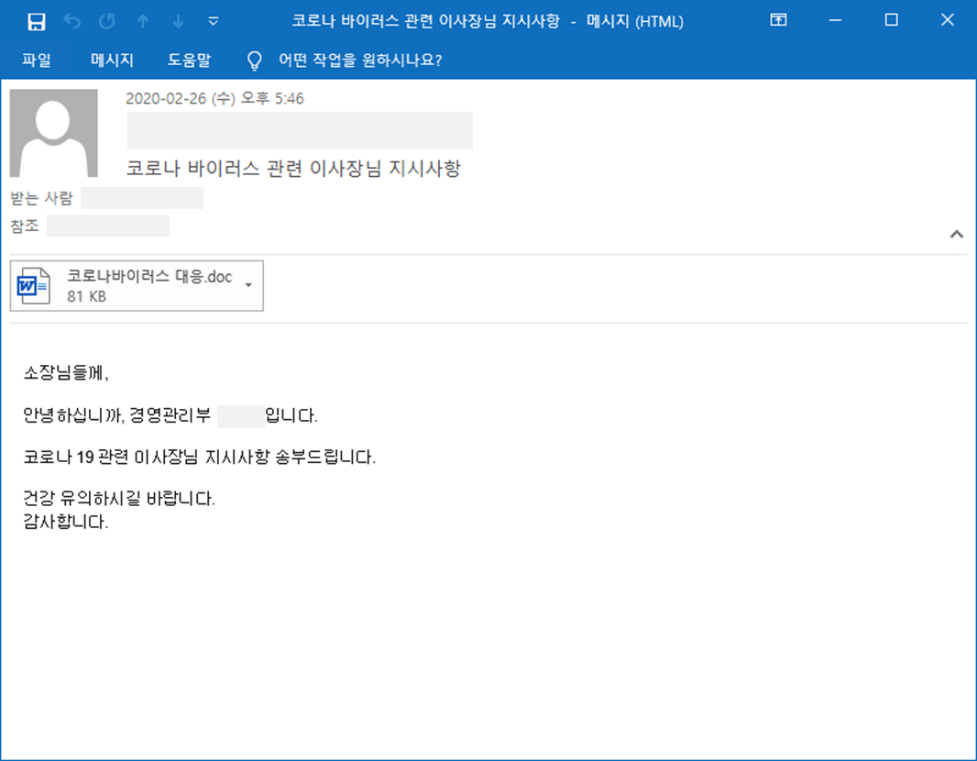
The attacker used the MS Word file type malware written in Korean, disguised as a “Guidelines for Corona Virus” document. This activity was targeted at organizations affiliated with the Ministry of Foreign Affairs of Korea, and when executing malware, the macro script included in it downloads and executes the PowerShell script from the attacker’s server.
[Figure 3: Spear Phishing email targeting organizations affiliated with the Ministry of Foreign Affairs in Korea]
[Figure 4: Malware disguised as “Guidelines for Corona Virus” document]
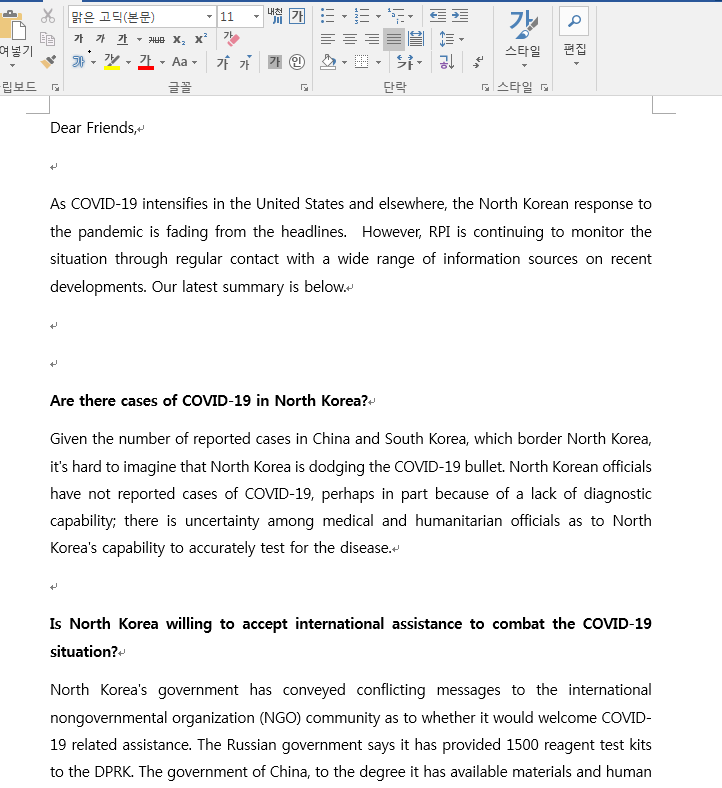
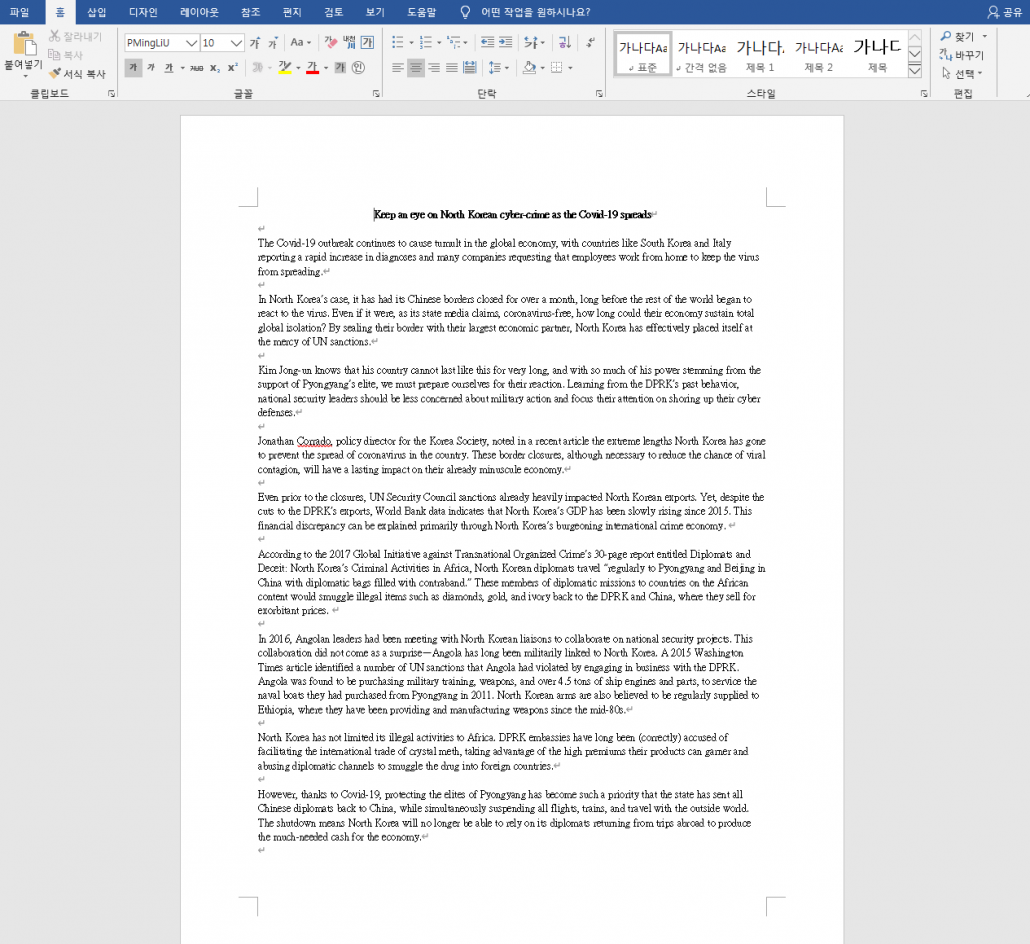
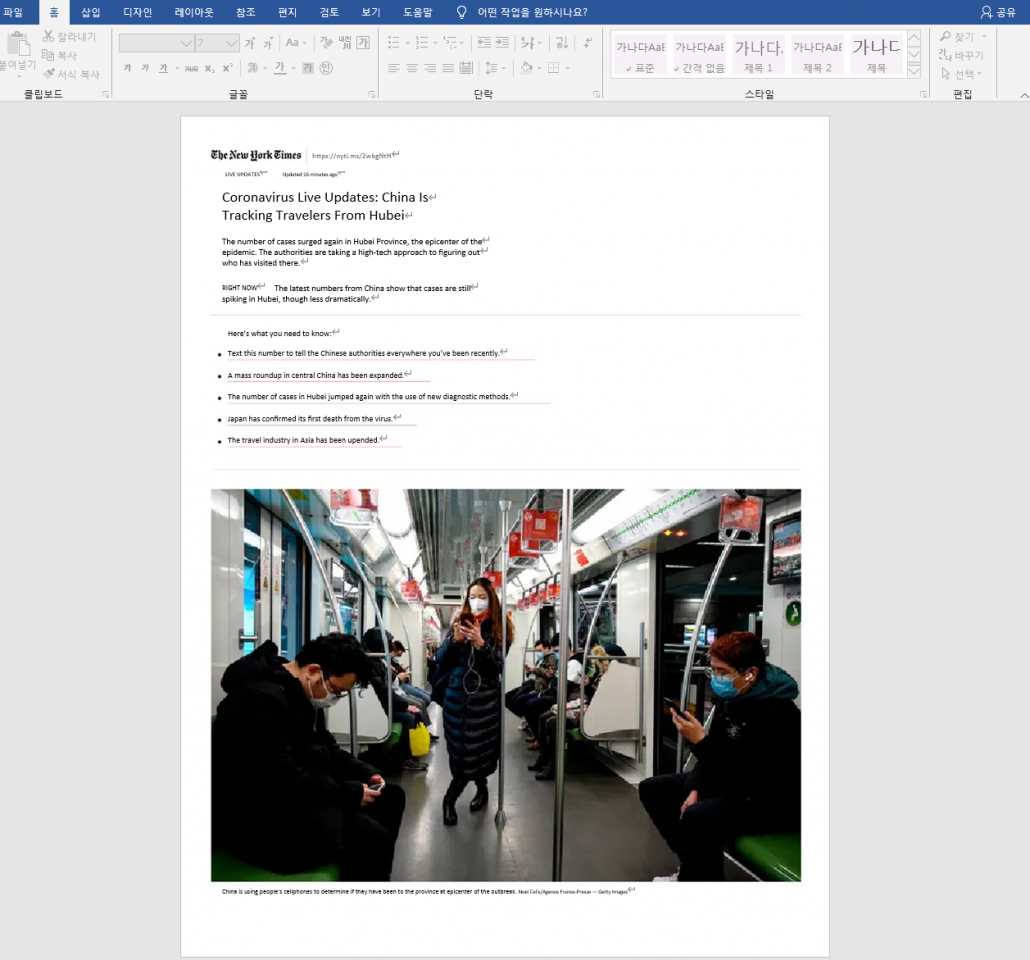
There have been documents found about the North Korean Corona virus situation, and malicious documents using the actual article text related to “North Korea’s Corona virus-themed cybercrime activity”. The found document is written in English, and when executed, additional macro code is downloaded from the attacker’s server using the macro script included inside.
Some of the malware downloaded from the attacker’s server was a Python script to replace the default template for MS Word installed on MacOS. This means that the attacker targeted both Windows and Mac OS users.
[Figure 5: Malware disguised as “North Korea’s Corona Virus Situation”]
[Figure 6: Malware using actual article content on the topic “Corona virus-themed North Korean cyber activity”]
2-2) SectorB Groups: Hacking activities targeting countries located in Asia
A total of five groups of activities were found in SectorB01, SectorB04, SectorB06, SectorB08 and SectorB22 within Sector B, while their extensive activities were have been found in 13 countries.: Mongolia, South Korea, Vietnam, China, Hong Kong, Russia, the United States, Kyrgyzstan, Pakistan, the Philippines, Taiwan, Belarus and Britain. Attackers mainly targeted countries located in Central Asia, East Asia and Southeast Asia, and most of the malicious codes found were in the form of RTF documents that included CVE-2017-11882 vulnerabilities.
Malware disguised as from the Mongolian Ministry of Foreign Affairs
The attackers distributed RTF documents that disguised as written by the Ministry of Foreign Affairs of Mongolia in government agencies in Mongolia, the document used the theme of “Corona virus prevalence”. This includes the CVE-2017-11882 vulnerability, and upon execution, it drops the malware in the form of a DLL file and downloads additional malware.
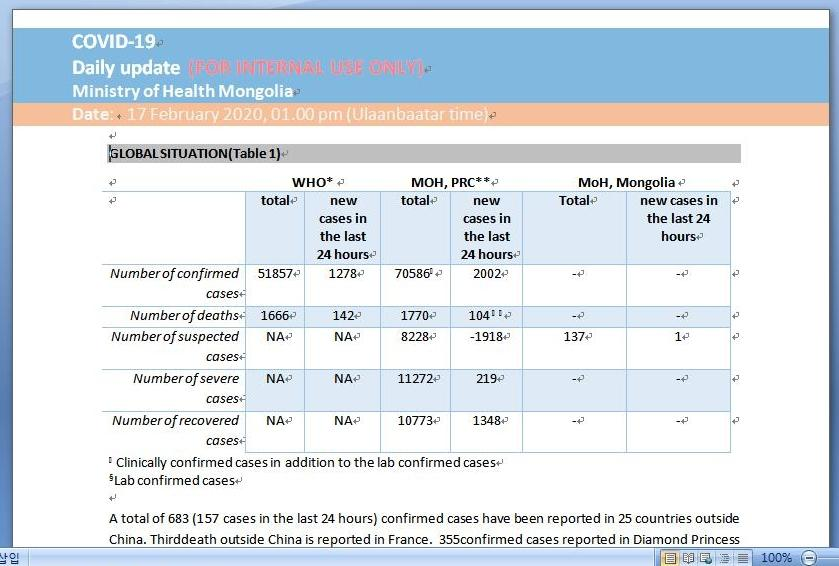
In addition, RTF documents disguised as written by the Ministry of Health of Mongolia were discovered using the same attack method as above, and this malicious document using the subject of the “Corona Virus Daily Report”.
[Figure 7: Malware with the theme of “corona virus prevalence” written in Mongolian]
[Figure 8: Malware disguised as a “daily report of the coronavirus” written by the Ministry of Health of Mongolia]
Malware disguised as Vietnam’s Prime Minister “Corona Virus guidelines”
An RTF file containing the same vulnerability that attacked Mongolia was found, which written in Vietnamese. The document was written on the subject of “Promoting Prevention and Management of COVID-19 Disease” presented by the Prime Minister of Vietnam.
[Figure 9: Malware on the subject of “Corona Prevention Guide” written in Vietnamese]
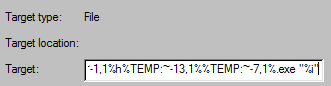
In Vietnam-targeted hacking activities, malware in the form of a shortcut (LNK) file disguised as a document file was also found. When executing the malware, a Visual Basic Script (VBScript) is executed to generate an executable file through an internal command, and a normal document popped up with the theme of the “Vietnamese Prime Minister for Corona Virus” pops up to avoid user suspicion.
[Figure 10: Command included in the malware of LNK file type disguised as a document file]
[Figure 11: Normal document that pops up when LNK file is executed]
Malware disguised as emergency contacts of certain religious groups in Korea
Among their hacking activities, Excel documents and PowerPoint (PPT) files that appeared to target South Korea were discovered. It was disguised as an emergency contact for a specific religious group involved in Corona virus infection.
The malware disguised as a document file is an SCR file using the Right to Left Override (RLO) method, and upon execution, additional malware is downloaded using a VBS script.
The C2 server used in the activity was also found in other hacking activities found in early March of the SectorB08 group in SectorB.
[Figure 12: Malware disguised as an emergency contact for a specific religious group]
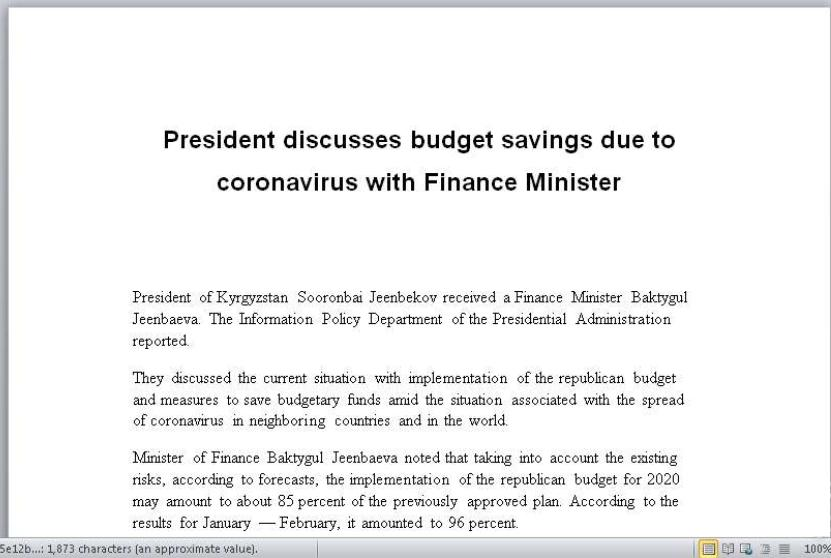
Malicious documents using CVE-2017-11882, the same vulnerability targeting Mongolia and Vietnam, were also discovered. It used the contents of a news article on discussions about “reduce the budget caused by the coronavirus” between the president of Kyrgyzstan and the finance minister.
[Figure 13: a malicious document about Kyrgyzstan’s budget cuts caused by the Corona virus]
Malware in the form of LNK files disguised as document files was also found in China. As in the case of Vietnam, VBS is executed when the malicious code is executed, and the actual report PDF file that WHO shared with the health authorities of each country is popped up.
[Figure 14: Report popped up to avoid user suspicion when running LNK files]
2-3) SectorC Groups: Malware disguised as being sent by the Ukrainian Public Health Center
The activities of the SectorC08 group in SectorC have been found, and their activities have been found in Ukraine, Russia, Hong Kong, the Philippines and the United States.
The attackers used malware in the form of MS Word file containing macro scripts. The document is disguised as being sent from a public health center in Ukraine and is written on the subject of “Corona Virus News”.
When the document is executed, the embedded macro script is executed to execute a downloader made of .NET, and additional malware is downloaded from the attacker’s server.
[Figure 15: Malware disguised as being transmitted by the Ukrainian Public Health Center]
2-4) SectorD Groups: Android malware disguised as an app for check the number of Corona virus infected
The activities of the SectorD11 group in SectorD were found, and their activities were found in Libya, Turkey, France and Egypt.
The attacker used the APK file disguised as a Corona infection status app. When the application is executed, call and SMS record, network information, location information collection and audio collection from infection device and transmits the collected information to the attacker server.
[Figure 16: Android malware disguised as an app to check the number of Corona virus infections]
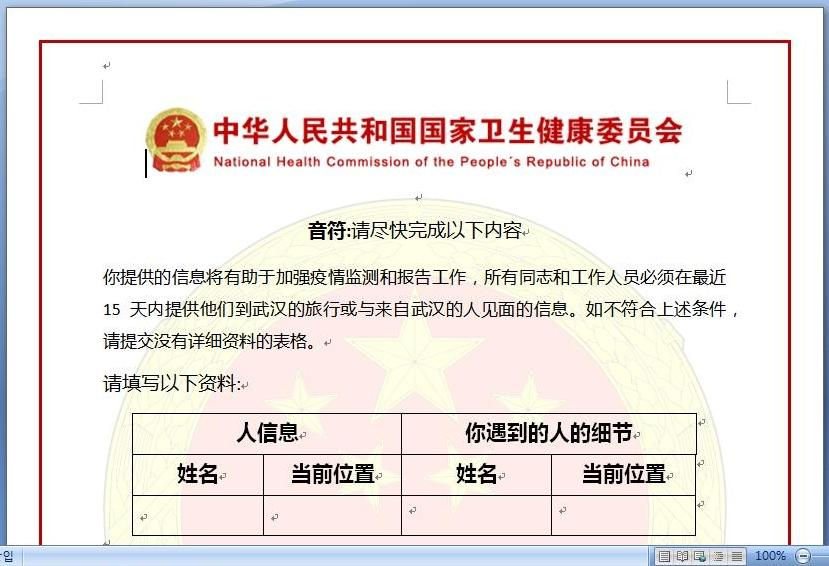
2-5) SectorE Groups: Malware disguised as the “Traveler Visit Area Survey” document
The activities of the SectorE01 group in SectorE were discovered, and their activities were found in China, Japan, Hong Kong, the United Kingdom and Italy.
The attacker used the MS Word file type malware containing the CVE-2017-8570 vulnerability. The document was disguised as a documented form, ordered by the Ministry of Health of China, to investigate the tourist’s visited area. In the main text, there is a sentence to submit the completed information by clicking the “Submit” button, and clicking the button downloads additional malicious code from the attacker’s server.
[Figure 17: Malware disguised as the “Traveler Visit Area Survey” document]
2-6) SectorF Groups: Malware disguised as a news article related to the corona virus
The activities of the SectorF01 group in SectorF were discovered, and their activities were found in China, Ukraine and Spain.
The attacker used the DLL Side Loading method to load malicious DLL files through the WPS Office program, a text editor developed in China.
In order to avoid user’s suspicion after loading the malicious DLL file when the program is executed, the normal file of the news article contents related to the Corona virus is popped up, and the backdoor is executed to collect information about the infected system.
[Figure 18: Normal file that pops up to avoid user suspicion when running malware]
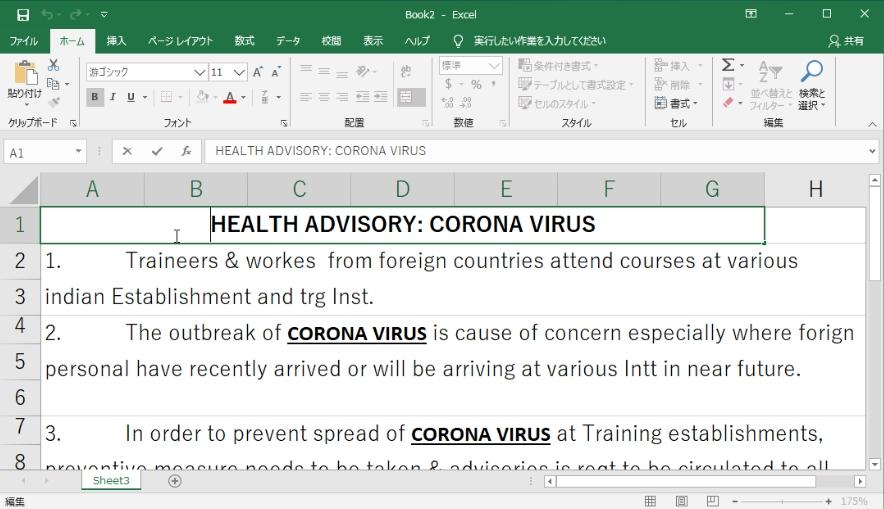
2-7) SectorH Groups: Malware disguised as a health advisory
The activities of the SectorH03 group in SectorH were discovered, and their activities were found in India, the Netherlands and Hungary.
The attacker used a malware in the form of MS Excel file containing macro scripts, disguised as a health advisory from the Indian government.
When a malicious document is executed, the built-in Remote Access Trojan is dropped, and it performs information collection functions such as collecting login information stored in the browser and collecting files stored in the system.
[Figure 19: Malware disguised as a health advisory]
2-8) SectorJ Groups: Spam mail using Corona virus theme
Among the cybercrime groups, the activities of the SectorJ04 group were found, and their activities were found in Germany, Italy, Canada, Greece, France, the United States, the Netherlands, and China.
The body of the spam mail was written in relation to the corona virus, and when a link included in the mail body is clicked, the malicious document containing the macro script is downloaded from the attacker’s server.
The malicious code in the form of MS office document retained the existing characteristics of the SectorJ04 group, which uses content related to MS Office.
When the malware is executed, ransomware or banking trojan is executed in the system.
[Figure 20: Malware in the form of a document file disguised as an office error message]
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.