Hacking activity of SectorC Group in 2021
Russian government supported hacking group SectorC
SectorC is a Russian government supported hacking group in which 13 subgroups has been identified as of now. They collect information regarding governmental activities such as political and diplomatic activities from all around the world, including countries near Russia.
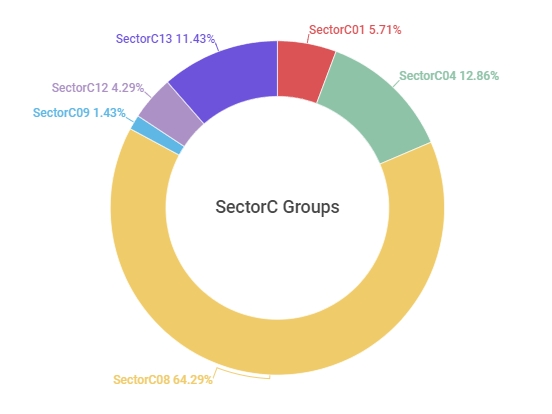
[Figure 1 : Identified percentage of activities by SectorC subgroups in 2021]
In 2021, their main targets were government institutions and Think Tanks which could affect the overall society in politics, economy, and diplomacy, and expanded their targets to public institutions associated with national defences. Among the 13 SectorC groups, activities of SectorC08 were the most prominent, followed by SectorC04 and SectorC13.
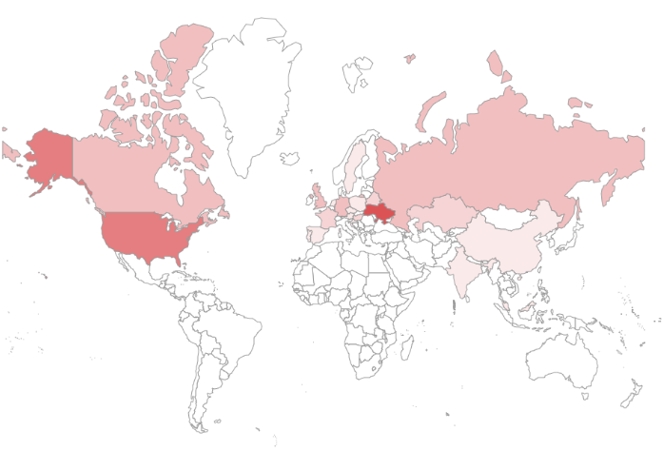
The following figure is a map indicating the targeted countries of SectorC group in 2021. A darker shade of red means a higher number of attacks, and we can deduce that SectorC group has been carrying out most amount of hacking activities against their bordering country, Ukraine, and the United States of America.
[Figure 2 : Main targeted countries of SectorC group in 2021]
Activity details of SectorC groups in 2021
The following is the timeline and details of monthly hacking activities of SectorC groups in 2021.
[Figure 3 : Timeline of main activities by SectorC groups in 2021]
January Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by two hacking groups were identified in January, which were SectorC01 and SectorC08 groups.
SectorC01 group made use of malware targeting android environments for their activities
SectorC08 group was found to be active in Ukraine, USA, Canada, Croatia, Austria. The attackers continued using the Template Injection hacking method in which a MS Word document containing macro scripts are downloaded from the attacker’s server.
February Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by three hacking groups were identified in February, which were SectorC01, SectorC08 and SectorC13.
SectorC01 group was found to be active in Kazakhstan, England, and Germany. The attacker used MS Word document containing macro scripts to create a downloader written in Delphi in their infected system. The used document was disguised under the subject of ‘Advanced statement’.
SectorC08 group was found to be active in Ukraine and France. They continued using the template injection method in which a MS Word document containing macro scripts is downloaded from the attacker’s server.
SectorC13 group was found to be active in Ukraine, Belarus, and France. They made use of MS Word documents under the subject of ‘Common security and defence policies of EUISS’, which, upon execution, accesses the attacker’s server to download scripts for later use such as PowerShell or VBScript.
March Hacking Aactivities
Among the SectorC groups supported by the Russian government, hacking activities by three hacking groups were identified in March, which were SectorC08, SectorC12 and SectorC13.
SectorC08 group was found to be active in Ukraine, USA, Jordan, Belarus and Canada. The group continued using the template injection method for their attacks, and Spear Phishing Email targeted at Ukraine border guards were discovered from their activities.
SectorC12 group was found to be active in Denmark, Kirgizstan, Kazakhstan, Ukraine, Moldova, Russian Federation, Tadzhikistan, Turkmenistan, Belarus, Argentina, Switzerland, Georgia, Azerbaijan, Armenia, Sweden, Austria, Portugal, Australia, Spain, Italia, France, Mexico, England, Germany, Panama, Netherlands, Canada, USA, and Uzbekistan. This group took advantage of the vulnerabilities of the SolarWinds software to carry out hacking activities to collect internal environmental information from governments and major corporations in various parts of the world.
SectorC13 group was found to be active in Spain, France, Belarus, Russia, Kuwait, and Singapore. This group made use of MS Word document disguised as official documents of governmental institutions, which downloads scripts such as PowerShell or VBScript from the C2 server upon execution of the Word file.
April Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by two hacking groups were identified in April, which was SectorC04 and SectorC08.
SectorC04 group was found to be active in Hongkong, Canada, Germany and USA. From this hacking activity, malwares related to attacks on supply chains of SolarWinds’s network managing software. The identified malwares were execution files written in Go, VBS file which downloads payload from the C2 server, WebShell also known as China Chopper, and the scale of damage instigated by the attack on the supply chain is still being investigated by various cybersecurity organizations.
SectorC04 group was found to be active in Ukraine, Russia, Bellis, and Croatia. The hacking group continued using the template injection method for their attacks, and most of the documents used in the activities were related to subjects such as Ukraine’s military activities or military pension.
May Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by one hacking group was identified in May, which was SectorC08.
SectorC08 was found to be active in Ukraine. The group continued using the template injection method for their attacks, and the documents used in the hacking activities were related to official documents of Ukraine or University lecture evaluation forms. In this activity, dual structured MS Word documents that downloads additional malware were identified.
June Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by four hacking groups were identified in June, which were SectorC01, SectorC04, SectorC08 and SectorC13.
SectorC01 group used spear fishing emails with the subject on international conferences, attached with MS Word malware which downloads a dropper that drops malwares upon file execution. They used commercial VPN services to evade detection and the same Exit VPN Node was discovered in targets such as infra-providing companies and cloud service companies.
SectorC04 group was found to be active in USA, Sweden, Ukraine, Russia, England, Uruguay, Turkey, Estonia, Czech Republic, Hungary, and Slovakia. This group sent out spear phishing emails targeted at various organizations in USA and Europe, and the C2 Server addresses used in the attacks were mostly disguised as email addresses related to US governmental institutions.
SectorC08 group was found to be active in Ukraine and Switzerland. In this activity, MS Words documents using template injection methods were discovered again and were disguised under various subjects such as ‘COVID-19 situation in the Balkan Peninsula’, ‘Bidding results’, ‘Ukraine Energy Department regulations on fuel retail prices’.
SectorC13 group was found to have used multiple network resources in this activity, and some of the domains were reportedly used to disseminate ransomware or botnets.
July Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by four hacking groups were identified in July, which were SectorC01, SectorC04, SectorC08 and SectorC09.
SectorC01 group was found to be active in China, Indonesia, Russia, USA, and Portugal. The group carried out hacking activities targeted on enterprise and cloud environment of western countries, and mainly used remote code execution vulnerabilities including the MS Exchange Server vulnerabilities and indiscriminate attacks to access the internal system and leak mail information.
SectorC04 group used Zero Day vulnerability, CVE-2021-1879 to target iOS users using the Safari browser. They targeted workers of Western European government organizations by sending malware links through Linkedin messages, and users who clicked on the link were redirected to a domain controlled by the attacker.
SectorC08 group was found to be active in Ukraine, Hungary, and USA. The group continuously used template injection method and malware documents with subjects related to Ukraine such as ‘customs application forms’, ‘police case report’, ‘COVID-19 situation within military forces’. On the other hand, FileStealer malware, which was believed to have been used by SectorC08 in file information collection, was discovered.
SectorC09 group was found to be active in Ukraine. In this activity, MS Word documents containing macro scripts were found, which creates a DLL format malware written in .NET and sends information collected in the infected systems to the C2 server through a referrer upon execution.
August Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by one hacking group was identified in August, which was SectorC08.
SectorC08 group was found to be active in Czech Republic, Ukraine, Hungary, Malaysia, USA, Netherlands, and Germany. The group continuously used the template injection method and various subjects related to law, Russian policies, COVID-19 were used as disguise.
September Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by two hacking groups were identified in September, which were SectorC08 and SectorC13.
SectorC08 group was found to be active in Ukraine and Germany. MS Word format malware that uses template injection methods were discovered in their activities again. Additionally, a domain impersonating a specific portal website was identified, and the group used the phishing pages to seize accounts and search history from the targets.
SectorC13 group was found to be active in Canada, Poland, Germany, England, Malaysia, USA, Switzerland, Kazakhstan, and India. In this activity, template injection was identified to have been carried out through MS Word documents containing information related to national defence, which was disseminated to participants of an international national defence conference.
October Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by three hacking groups were identified in October, which were SectorC08, SectorC12 and SectorC13.
SectorC08 group was found to be active in Ukraine. MS Word format malware using the template injection method was identified, and they used subjects related to a specific country’s core institutions and the military sector.
SectorC12 group was found to be active in Ukraine, Spain, Russia, China, Japan, Kazakhstan. The group used malware written in Go, and altered file icon and used vacation-spot related titles to disguise the malware as a MS Word document and lead the target to execute the file.
SectorC13 group was found to be active in Canada, Poland, Germany, England, Malaysia, USA, Switzerland, Kazakhstan, and India. The group used MS Word documents using the template injection method, disguised as documents of a specific country’s federal meeting.
November Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by two hacking groups were identified in November, which were SectorC08 and SectorC13.
SectorC08 group was found to be active in Ukraine. The group used MS Word documents using the template injection method, targeted at specific country’s military prosecuting office by using titles related to prosecutions.
SectorC13 group was found to be active in Ukraine. The group used MS Word documents using the template injection method, disguised as documents related to ceasefire agreements and population survey in a specific country.
December Hacking Activities
Among the SectorC groups supported by the Russian government, hacking activities by three hacking groups were identified in December, which were SectorC04, SectorC08 and SectorC13.
SectorC04 group was found to be active in India, England, USA, Belgium, Canada, Switzerland, Qatar, New Zealand, Singapore, France. The group used a similar method of using LNK files included in ISO image files to load malicious DLL files, which then downloads mock hacking tools such as Sliver or Cobalt Strike, to seize the system’s controls.
SectorC08 group was found to be active in Ukraine. The group used MS Word document malware utilizing the template injection method, to download PE (Portable Executable) malware in the target’s system and seize the controls.
SectorC13 group was found to be active in Ukraine, Hungary, Serbia. The group used MS Word using the template injection method, and word documents disguised as work report by a Russian politician.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net