Hacking activity of SectorA Group in 2021
North Korea government supported hacking group SectorA
SectorA is a hacking group supported by North Korean government, in which 7 subgroups have been identified as of now. They collect political and diplomatic information regarding South Korea or carry out hacking activities with the purpose of securing other currencies.
They make use of various hacking strategies such as spear phishing attack with malicious documents attached, watering hole attack by hacking websites often visited by workers of the targeted organization and disseminating malwares, taking advantage of vulnerabilities of IT tools exposed outside of the targeting organization and phishing email attacks to steal user verification information of the targeted users.
They show an increase in frequency of using HWP file format, a type of file often used in public institutions in South Korea, or Microsoft Word document format malwares for their attacks, along with self-created malwares or tools released online.
Their main targets are government sectors, public companies, North Korea defectors and related organizations, with the purpose of collecting political and diplomatic information regarding South Korea, and financial industries such as cryptocurrency trade posts or financial investment companies with the purpose of securing overseas currencies. Additionally, it was confirmed that they have expanded their targets to medical and research institutions due to medical and disease control problems under the influence of COVID-19 in North Korea.
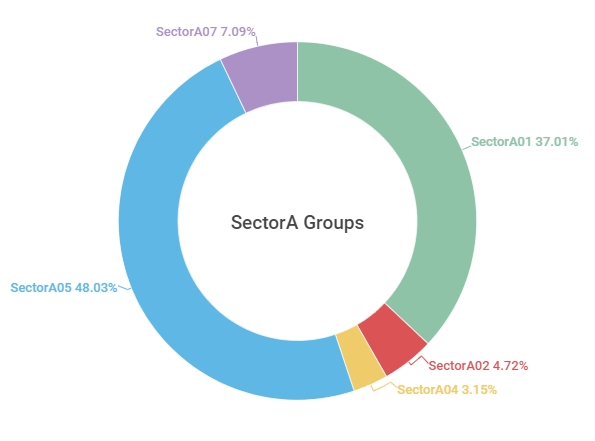
From analysing the activity amount of SectorA groups in 2021, SectorA05 group was found to be the most active, followed by SectorA01 and SectorA07.
[Figure 1 : Activities by SectorA subgroups in 2021]
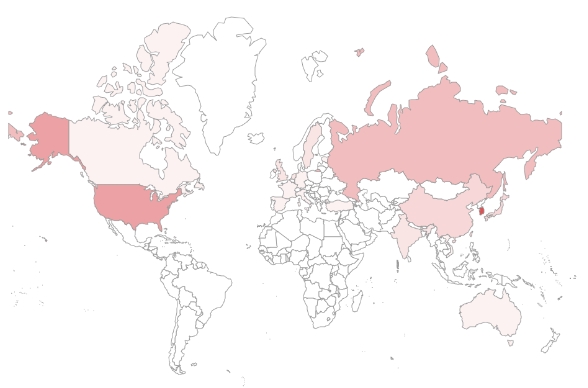
The following is a map of countries targeted by SectorA groups in 2021, and a darker shade of red means higher number of attacks. Countries with high frequency of attacks overall include South Korea, United States of America, followed by Russia and China.
[Figure 2 : Main targeted countries of SectorA group in 2021]
Activity details of SectorA groups in 2021
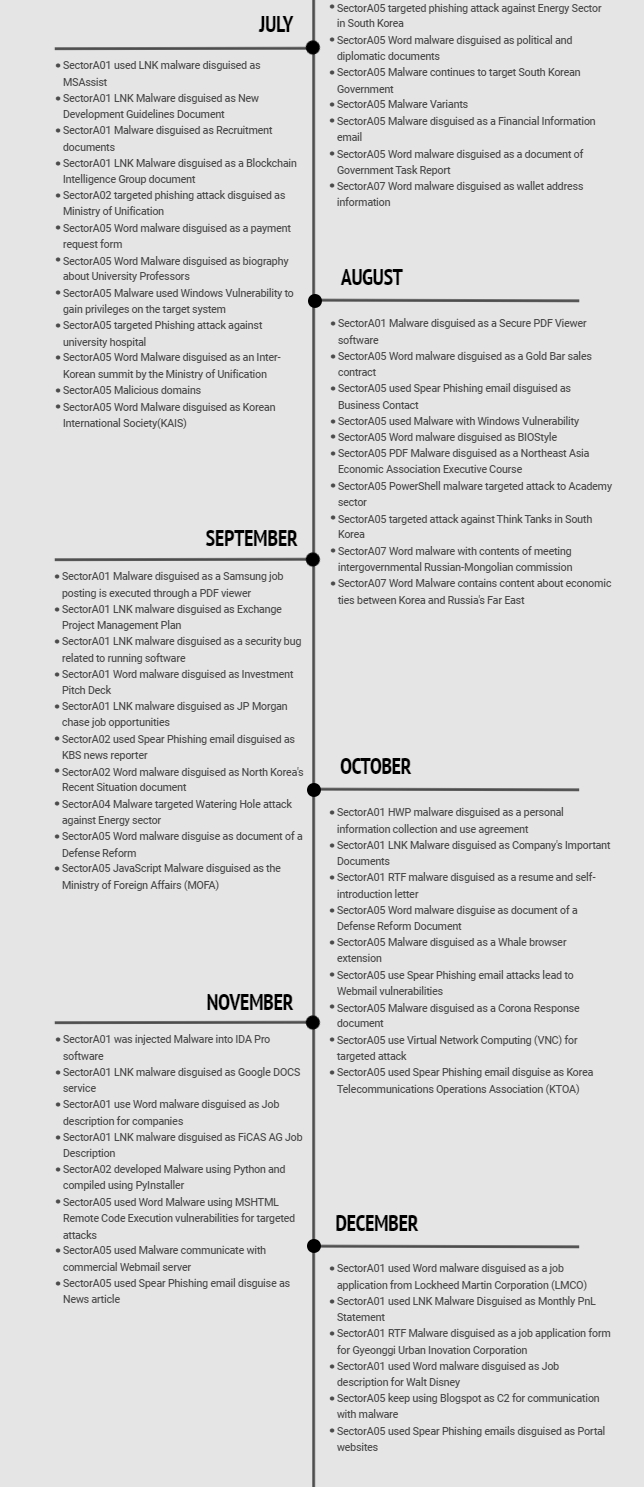
The following is details regarding the timeline and monthly activities of SectorA groups identified in 2021.
[Figure 3 : Timeline of main activities by SectorA groups in 2021]
January Hacking Activities
In January, activities by a total of 3 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA02, SectorA05 groups.
SectorA01 group was found to be active in India, United States, and Russia. The group released multi-platform malwares targeting Windows and Mac OS. They also used LNK format malwares, disguised as software files of Microsoft to avoid suspicion from users.
SectorA02 group was found to be active in Japan, Netherlands, Canada, and South Korea. The group targeted mobile devices for their attacks, and MS Word document format malwares with macro scripts included were identified. The document was disguised as a file regarding a specific meeting.
SectorA05 group was found to be active in South Korea and Sweden. The group distributed altered messenger programs through supply chains, which accesses FTP server to serve additional commands. They also served their attacks using keywords related to social issues such as “Biden Administration”, “COVID-19”.
February Hacking Activities
In February, activities by a total of 3 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA05, SectorA07 groups.
SectorA01 group was found to be active in France, United States, Canada, Spain, Australia, Switzerland, Russia, South Korea, Hong Kong, India, Singapore, Turkey, Italy, Ukraine, and Germany. The attackers used social engineering techniques to target specific security researchers. They created fabricated SNS (Social Networking Service) accounts to build trust with the targets to access and observe information continuously. Additionally, they used vulnerabilities of MS Word and macro scripts to release malwares in attacks targeting companies.
SectorA05 group was found to be active in Hong Kong and South Korea. The attackers used various types of malwares including keywords related to social issues such as “Biden”, “North Korean policies”, “COVID-19” to serve their attacks. They also used malwares disguised as Hancom Office modules of the Hancom company to serve their attacks, and collect information in the infected system, sending it to the Daum mail server.
SectorA07 group was found to be active in India, Italy, Philippines, Spain, United States, and Russia. In this activity, they targeted one of the main corporations in Italy, and are confirmed to have been carrying out activities within the corporation for 2 years. They were also seen to have targeted researchers studying South and North Koreas’ economic activities in Russia for their attacks.
March Hacking Aactivities
In March, activities by a total of 3 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA04, SectorA05 groups.
SectorA01 group was found to be active in South Korea, United States, United Arab Amirates, Singapore, Australia, Russia, China, and France. They were found to have been continuously disseminating malwares in LNK format that was previously distributed by them. Following from last January when they disguised malwares as Microsoft software files, they have expanded their attacks to be using normal documents with the malwares to avoid user suspicion and lead them to execute the files.
SectorA04 group was found to be active in South Korea. The group was found to have pretended to be the Ministry of Unification to continuously disseminate phishing mails targeted on researchers in the field of North Korean studies. Similar attacks pretending to be the Ministry of Unification have been occurring continuously, and they use attached files of emails or links included in the body of the emails to steal user information and disseminate malwares. The phishing address is disguised as a specific portal website of South Korea.
SectorA05 group was found to be active in South Korea and China. They used documents disguised as ‘Consent to using personal information’, ‘Compensation payment’, ‘questionnaires’, ‘question forms’ to serve attacks targeted on media and North Korea related workers. The group usually used HWP documents but have expanded their attacks in the form of disseminating Word documents recently.
April Hacking Activities
In April, activities by a total of 3 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA05, SectorA07 groups.
SectorA01 was found to be active in Taiwan, Hong Kong, Italy, China, Japan, France, South Korea, Sweden, Netherlands, Vietnam, England, Portugal, Australia, and United States. The group continuously disseminated malwares disguised as application forms or written payments to avoid user suspicion. The malware uses BMP files and macro scripts within, to create additional malwares and execute them.
SectorA05 group was found to be active in South Korea, Hong Kong, and Taiwan. The group targeted their attacks on workers in the field of diplomacy, national defense, security, and unification. The malware was disguised as ‘월간 KIMA’, a research report published by KIMA, and mostly used template injection method to download additional MS Word documents with macro scripts included.
SectorA07 group targeted workers in the field of policies against North Korea in Russia for their attacks, and malwares contained information on situations of South Korea and North Korea that workers in the field would be interested in.
May Hacking Activities
In May, activities by a total of 3 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA04, SectorA05 groups.
SectorA01 group was found to be active in United States, South Korea, Russia, Israel, and Netherlands. The group was continuously disseminating Word malwares and disguised as hiring posts of a specific company to avoid suspicion from the users.
SectorA04 group was found to be active in South Korea. The group continued to release phishing mails targeted at researchers in the field of policies against North Korea, continued from March. The domains used in phishing activities were mostly disguised as a specific portal website of South Korea, and continued to use a specific IP range.
SectorA05 group was found to be active in South Korea and Russia. The group were identified to have been attacking workers in the field of diplomacy, media, national defense and unification continuously. They attached normal files with malware files to avoid suspicion from the user and included detailed information regarding the attached files in the body of the email.
June Hacking Activities
In June, activities by a total of 4 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA04, SectorA05 and SectorA07 groups.
SectorA01 group was found to be active in Indonesia, Estonia, Germany, Russia, Thailand, Malta, Slovenia, Sweden, Czech Republic, Austria, Hong Kong, China, United States, and Israel. The group disguised the malware as documents related to a specific aircraft manufacturing company in Europe. The malware functions in the same way as the malware disguised as a specific munitions company and automobile manufacturing company, and uses macro script included inside to create additional DLL files, and uses ‘mavinject.exe’ file in the system folder to execute it.
SectorA04 group was found to be active in South Korea. The group targeted various industries such as manufacturing and media for their attacks, and downloads multiple payloads from the C2 server, starting from the Word malware, to execute them.
SectorA05 group was found to be active in South Korea and United States. The group targeted workers of important industries in South Korea such as national defense, national security, trade, energy and universities, and mainly uses phishing emails to collect information of the targets.
SectorA07 group was found to be active in South Korea. The group used MS Word malwares disguised as cryptocurrencies wallet address, and uses macro scripts included to download additional files from the C2 server for execution.
July Hacking Activities
In July, activities by a total of 3 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA02 and SectorA05 groups.
SectorA01 group was found to be active in United States, Russia, Taiwan, Sweden, and China. The group continued to release LNK format malware, disguised as documents related to a specific block chain company or a developer’s guide to avoid user suspicion.
SectorA02 group was found to be active in South Korea. The group targeted their attacks on workers in the field of unification. The phishing email impersonating a researcher of a specific national strategy research institution leads the user to activate the attached malware link, and aims to collect information regarding the user.
SectorA05 group was found to be active in South Korea, United States, and Russia. The group targeted their attacks on workers in the field of national defense, diplomatic securities, and university. They mostly use template injection method using a macro script in a MS Word document, to download additional payload for execution.
August Hacking Activities
In August, activities by a total of 3 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA05 and SectorA07 groups.
SectorA01 group was found to be active in Germany, Pakistan, and India. The group disseminated PDF malwares disguised as android wallet addresses, and used social engineering techniques to target industries related to cryptocurrencies for their attacks. The 2 PDF malwares used in the attack contains executable malwares within, which creates malwares in the target’s PC upon opening of the PDF document for execution.
SectorA05 group was found to be active in South Korea, Japan, Canada, and Hong Kong. The group targeted their attacks on workers in the field of media and universities. In past activities, they mainly made use of MS Word malwares, but used vulnerabilities of PDF files in addition for their attacks.
SectorA07 group was found to be active in Russia. The group used MS Word documents written in Russian for their attacks. The Word documents contained subjects related to economy between Russia and another country, and uses a macro script within to serve malicious functions.
September Hacking Activities
In September, activities by a total of 4 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA02, SectorA04 and SectorA05 groups.
SectorA01 group was found to be active in United States, Turkey, Taiwan, England, Japan, and South Korea. The group continued to disseminate LNK format malware. In order to avoid user suspicion, they used documents disguised in many forms such as documents of investment banks and securities companies and were found to have been using document images from the past continuously.
SectorA02 group was found to be active in South Korea. The group targeted specific public institutions and government sectors for their attacks. They used the watering hole technique of inserting malicious scripts into the target’s homepage, and from analysis, users approaching the website will be infected by additional malware.
SectorA04 group was found to be active in South Korea. The group targeted their attacks on specific public institutions and governmental sectors. They used the watering hole technique of inserting a malicious script into the target’s webpage, and users who access the page are expected to be infected with additional malware.
SectorA05 group was found to be active in South Korea. The group served hacking attacks targeted on workers in the field of Think tanks. The MS Word document used in the attack mainly uses the template injection method, by downloading additional payload for execution using the macro script included.
October Hacking Activities
In October, activities by a total of 2 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01 and SectorA05 groups.
SectorA01 group was found to be active in United States, China, England, Taiwan, Japan, Hong Kong, and South Korea. The group was identified to have been continuously disseminating LNK format malwares, continued from September.
SectorA05 group was found to be active in South Korea, Japan, Taiwan, and Poland. The group used malwares using the PIF (Program Information File) files for their attacks, disguised as files related to the COVID-19 virus.
November Hacking Activities
In November, activities by a total of 3 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA02 and SectorA05 groups.
SectorA01 group was found to be active in Vietnam, United States, Estonia, Ireland, Serbia, and Turkey. In this attack, the group used malwares disguised as binary code analysis tools, such as Reverse Engineer or Malware Analyst that cybersecurity researchers often make use of.
SectorA02 group was found to be active in South Korea. The group disseminated MS Word document format malwares in this activity, which are inserted with macro scripts that creates additional files and executes them.
SectorA05 group was found to be active in South Korea. The group disseminated Word file format malwares including vulnerabilities in their attacks, which contains information regarding policies against North Korea.
December Hacking Activities
In December, activities by a total of 3 hacking groups among North Korean government supported SectorA groups were identified, and they were SectorA01, SectorA05 and SectorA06 groups.
SectorA01 group was found to be active in England, Singapore, South Korea, and Spain. The group used documents disguised as hiring documents of a specific company to disseminate malware, which uses the template injection technique to download template from external servers to serve malicious functions.
SectorA05 group was found to be active in South Korea. The group distributed spear phishing emails to multiple targets in this activity.
SectorA06 group was found to be active in Hong Kong and United States. The group used LNK format malwares disguised as income statement and related files.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.