Hacking activity of SectorD Group in 2021
Iranian government supported hacking group, SectorD
SectorD is a hacking group supported by the Irani government, where 18 subgroups have been identified as of now. They carry out hacking activities with the purpose of collecting advanced information such as political or diplomatic information of individuals and countries against the Iranian government. They usually use spear phishing emails and social network services with large number of users to approach specific individuals using social engineering techniques. They also steal identification information through phishing websites disguised as login pages of well-known universities or take advantage of known vulnerabilities to serve their hacking activities.
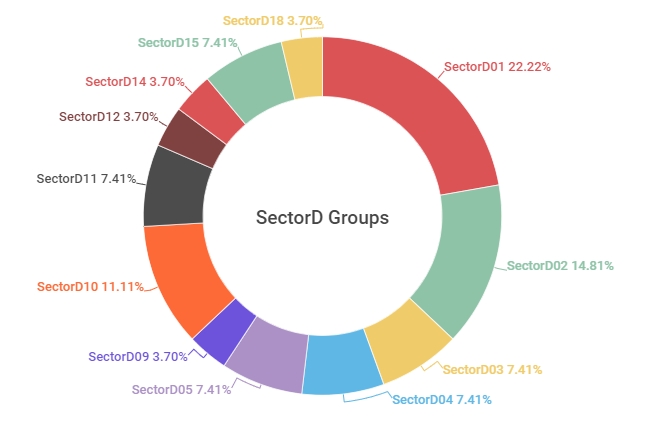
SectorD hacking groups show a trend of targeting countries around Iran for their attacks. Their main targets include various organizations such as government sectors, research institutions, universities, and individuals, and were recently identified to have been expanding their targets to the aerospace industry. Among the 18 SectorD subgroups, activities of SectorD01 group were the most prominent in 2021, followed by activities by SectorD02 and SectorD10 groups.
[Figure 1 : Activities of SectorD subgroups identified in 2021]
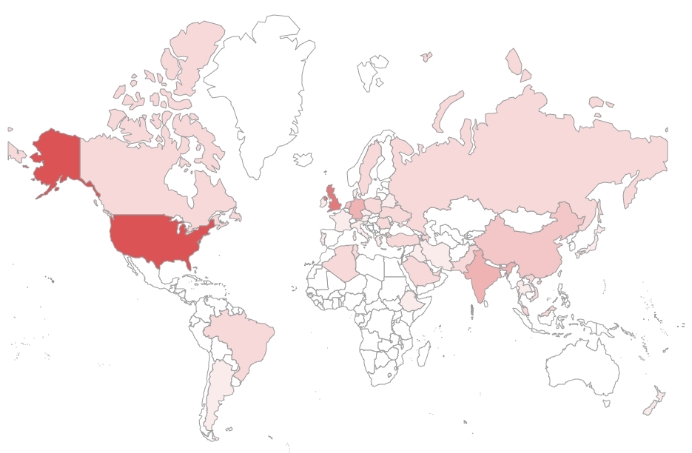
The following figure is a map of the countries targeted by SectorD groups in 2021. A darker shade of red means higher frequencies of attacks on the country. The countries that were targeted the most often were the United States and England, and countries in the Middle East and Southeast Asia.
[Figure 2 : Main targets of SectorD group in 2021]
Details of SectorD group activities in 2021
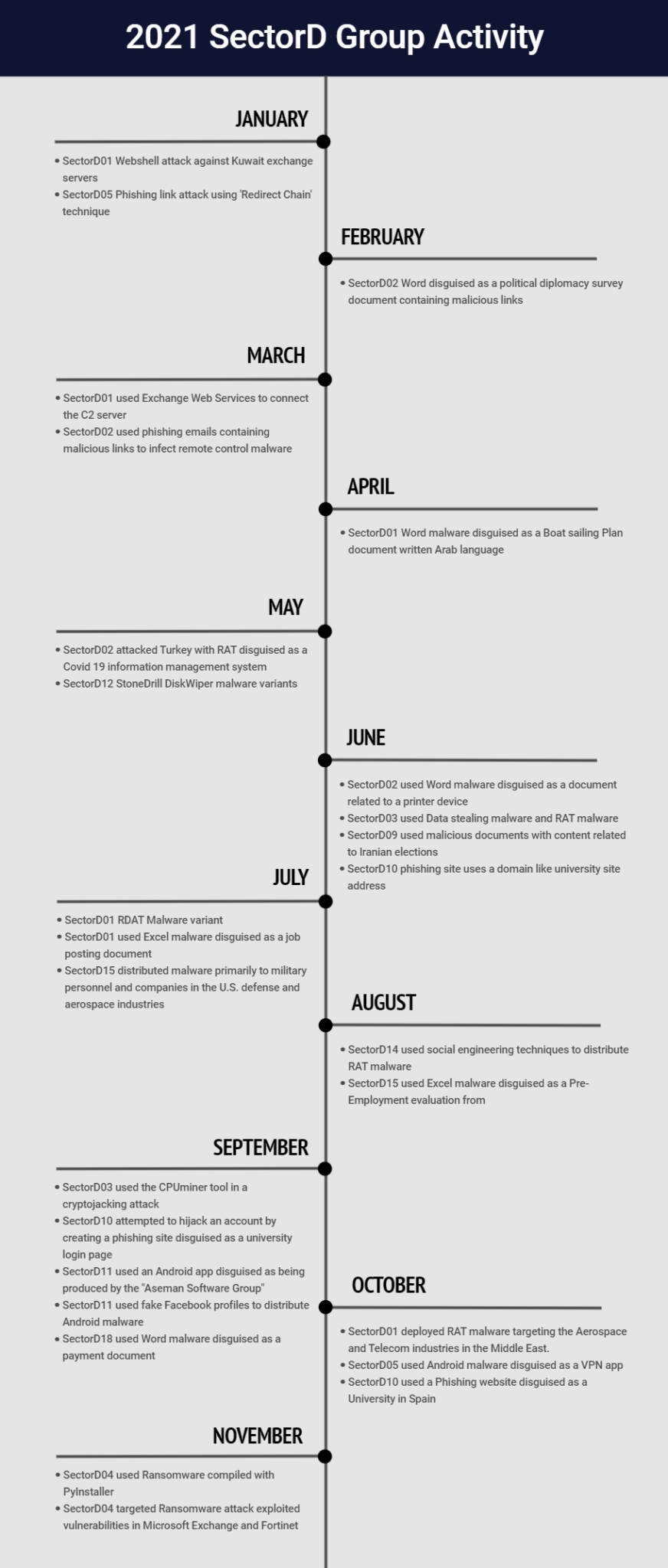
The following is the timeline and monthly details of hacking activities by SectorD groups, identified in 2021.
[Figure 3 : Main activity timeline of SectorD groups in 2021]
January Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 2 hacking groups were identified in January, and the groups were SectorD01 and SectorD05 groups.
SectorD01 group was found to be active in Kuwait. The group was found to have launched WebShell attacks on Kuwait exchange servers in this activity.
SectorD05 group was found to be active in the United States. The group sent out SMS with google apps script links and phishing emails to research institutions, universities, and media-related personnel with the purpose of stealing Gmail, Yahoo!, and Outlook account information.
February Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 1 hacking group were identified in February, and the group was the SectorD02 group.
SectorD02 group was found to be active in the Arab Emirates. The group was found to have used malware files disguised as word documents from Kuwait Ministry of Foreign Affairs for their attacks.
March Hacking Aactivities
Among the SectorD groups supported by the Iranian government, activities by a total of 2 hacking groups were identified in March, and the groups were SectorD01 and SectorD02 groups.
SectorD01 group was found to be active in India and the Netherlands. The group was found to have used EWS (Exchange Web Services) as the C2 server for their attacks in this activity.
SectorD02 group was found to be active in England, the United States, India, Azerbaijan, Bahrain, Israel, Saudi Arabia, Arab Emirates and Germany. The group sent out word documents and emails with links to countries in the Middle East, leading the victims to download malware files.
April Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 1 hacking group were identified in April, and the group was SectorD01 group.
SectorD01 group was found to be active in Netherlands. The DOTNET malware used in the attacks, that uses EWS (Exchange Web Services) as the C2 service, was identical to the malware identified in their previous activities.
May Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 2 hacking groups were identified in May, and the groups were SectorD02 and SectorD12 groups.
SectorD02 group was found to be active in Turkey and the United States. The group used malwares disguised as files related to COVID-19. They impersonated the government institution to lead the targets to execute the files without suspicion, and the malware downloads remote controlling tools upon execution.
SectorD12 group disguised their malware as a normal sticky note program to ensure continuity in the user’s PC, and this malware that can serve multiple functions receives commands from the C&C server.
June Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 4 hacking groups were identified in June, and the groups were SectorD02, Sectord03, SectorD09 and SectorD10 groups.
SectorD02 group was found to be active in Malaysia and Brazil. The group, similar to their past activities, used the MS word document malwares with macros inserted for their attacks this month.
SectorD03 group was found to be active in Azerbaijan, Russia, Malaysia, India, Rumania, Germany, France, England, and the United States. The group used malwares that steal information in this activity.
SectorD09 group was found to be active in England. The group used MS word document malwares with contents related to Iranian elections.
SectorD10 group continued using their attack technique of using phishing websites disguised as university libraries and portal webpages collect information from users.
July Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 2 hacking groups were identified in July, and the groups were SectorD01 and SectorD15 groups.
SectorD01 group was found to be active in the United States, England, and Pakistan. The group used MS excel file malwares with macros similar to their previous attack, in order to steal system information from the victims.
SectorD15 group was found to be active in India, Ukraine, England and the United States. The group used social engineering techniques to build trust with military personnel and workers of national defense and aerospace industries and pass on keylogger and backdoor malwares.
August Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 2 hacking groups were identified in August, and the groups were SectorD14 and SectorD15 groups.
SectorD14 group was found to be active in Turkey, Israel, Canada, and Tunisia. The group used social engineering techniques of impersonating workers in HR to approach their targets. In this activity, malwares showing correlation to attacks in July were identified.
SectorD15 group was found to be active in Brazil and the United States. The group used social engineering techniques to approach military personnel and companies of national defense and aerospace industries in the United States with the purpose of building trust, and directly pass on keylogger and backdoor malwares. In this activity, malwares showing correlation to attacks in July were identified.
September Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 4 hacking groups were identified in September, and the groups were SectorD03, SectorD10, SectorD11 and SectorD18 groups.
SectorD03 group was found to be active in Algeria, China, Poland, the United States, England, Vietnam, and Tunisia. The group used information-stealing malwares and CPUminer, a CPU mining software tool in this activity.
SectorD10 group was found to be active in Sweden. The group used phishing websites disguised as university libraries and portal websites to collect user information.
SectorD11 group was found to be active in Iran, the United States, Algeria, Iraq, and New Zealand. The group used android malwares using various subjects such as messengers and news media and showed a trend of using malwares disguised as applications often used by a specific country and industries to target their victims.
SectorD18 group was found to be active in Pakistan, Germany, and the United States. The group used MS word file malwares disguised as invoice documents, which, at the final stage, drops and executes malwares serving backdooring functions.
October Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 3 hacking groups were identified in October, and the groups were SectorD01, SectorD05 and SectorD10 groups.
SectorD01 group was found to be active in China and Israel. The group distributed RAT (Remote Administration Tool) malwares to companies in aerospace and communication industries in the Middle East, attempting to steal system controls of victims.
SectorD05 group was found to be active in Netherlands. The group used Android malwares using various subjects such as messengers and news media and used Android malwares disguised as VPN applications in this activity.
SectorD10 group used phishing sites disguised as university library and portal websites to collect user information, and used phishing site disguised as a university library in Spain for this activity.
November Hacking Activities
Among the SectorD groups supported by the Iranian government, activities by a total of 1 hacking group was identified in November, and the group was SectorD04 group.
SectorD04 group was found to be active in the United States, Germany, Luxembourg, Ukraine, Canada, Rumania, Belarus, Netherlands, Italy, Israel, Poland, Japan, Vietnam, Ireland, Singapore, Hong Kong, England, India, Argentina, China, Taiwan, Arab Emirates, Sweden, Russia, Palestine, Thailand, Austria, Ethiopia, Denmark, Greece, Columbia, Saudi Arabia, and Czech Republic. The group distributed ransomware that copies files in an encrypted saving space, sets a password, and deletes the original file.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.