Monthly Threat Actor Group Intelligence Report, May 2022 (ENG)
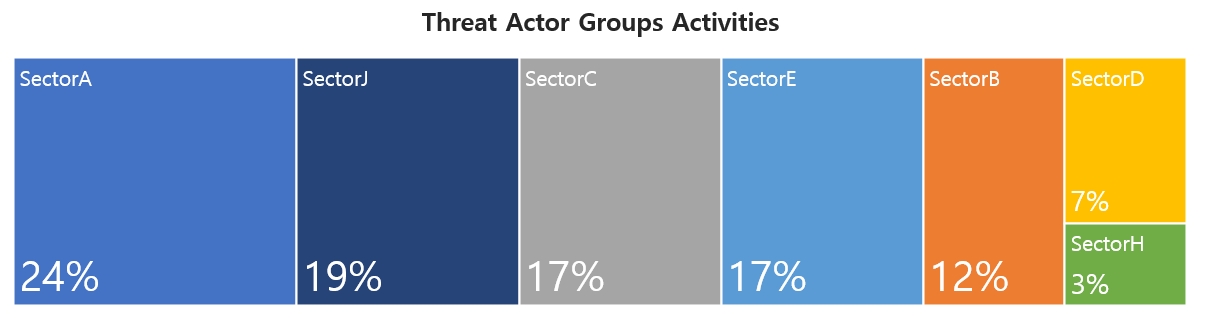
This report is a summary of Threat Actor group activities analyzed by NSHC ThreatRecon team based on data and information collected from 21 April 2022 to 20 May 2022. In this May, activities by a total of 36 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 24%, followed by SectorJ, SectorC and SectorE groups.
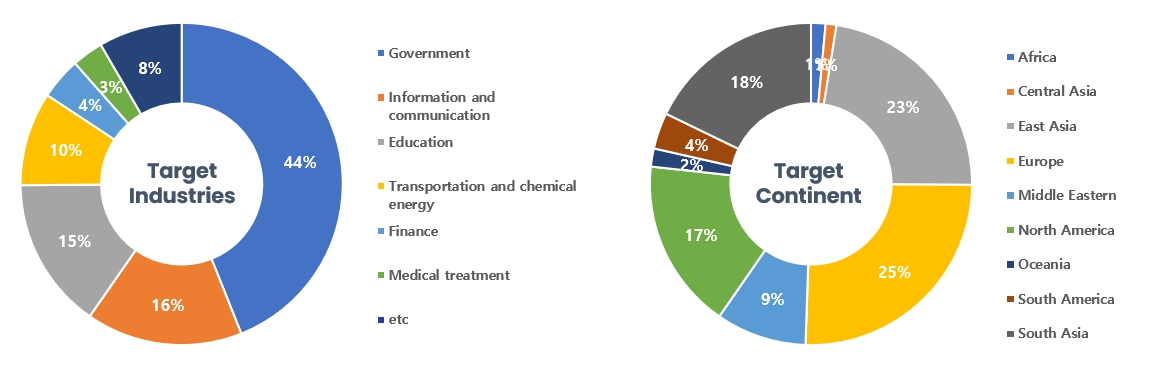
The Threat Actors carried out the highest number of attacks on workers and systems in government agencies and info-communication industries. Regionally, Europe and East Asia were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In May 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, and SectorA07 groups
SectorA01 group was found to be active in Rumania, Japan, Netherlands, and Spain. The group carried out attacks targeted on engineering companies in the field of energy and military, by applying initial access techniques on Log4Shell vulnerabilities to damage the systems.
SectorA02 group was found to be active in South Korea and Turkey. The group sent out spear phishing emails targeting news reporters and workers in the field of North Korean policies.
SectorA05 group was found to be active in South Korea, the United States and Japan. The group disseminated malwares in various formats to workers in the field of politics and diplomacy.
SectorA06 group was found to be active in South Korea and the United States. The group utilized CHM (Compiled HTML File), a help file format in their attacks.
SectorA07 group was found to be active in South Korea. The group attached malwares in spear phishing emails disguised as incident reports and cryptocurrency investment information.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In May 2022, activities by a total of 7 hacking groups were identified, and the groups were SectorB04, SectorB20, SectorB22, SectorB23, SectorB31, SectorB34, and SectorB53 groups
SectorB20 group was found to be active in China, Vietnam, Thailand, Singapore, the Philippines, Malaysia, Indonesia, Cambodia, and Brunei. The group used spear phishing emails attached with MS Word documents for the attack.
SectorB22 group was found to be active in Vietnam. The group disseminated malware disguised as a security software to steal system controls.
SectorB23 group was found to be active in South Korea. The group utilized CHM files in this attack, which were disguised as technical documents to provide help for users using a specific system.
SectorB31 group was found to be active in Russia. The group used MS Word documents written in Russian for their activities.
SectorB34 group was found to be active in India, Japan, and China. The group used RTF (Rich Text Format) malware that utilizes vulnerabilities for their attacks.
SectorB53 group was found to be active in Sweden, Taiwan, the United States, Macao, Hong Kong, China, India, and South Korea. The group targeted on Linux OS systems to disseminate ELF(Executable and Linkable Format) malwares.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In May 2022, activities by a total of 6 hacking groups were identified, and the groups were SectorC01, SectorC04, SectorC05, SectorC07, SectorC08 and SectorC15 groups
SectorC01 group was found to be active in Russia, Ireland, Columbia, Netherlands, Arab Emirates, Ukraine, Indonesia, Spain, Portugal, and Germany. The group sent out spear phishing emails containing data-collecting malwares to Ukraine.
SectorC04 group was found to be active in Belgium, Turkey, Indonesia, Russia, Sweden, Canada, Austria, and Taiwan. The group impersonated the Embassy of Turkey to send out phishing emails with the target as the Ministry of Foreign Affairs.
SectorC05 group was found to be active in Ukraine. The group used a variant of the malware loader which was used in a cyberattack targeted on a Ukrainian energy supplying company.
SectorC07 group was found to be active in Germany, Thailand, South Korea, the United States, Russia, England, Netherlands, France, Italy, Portugal, Spain, Bolivia, Croatia, Turkey, Argentina, Rumania, South Africa, and Mexico. The group disguised the malware as a protected file to lead the victim to disable security options and collected financial and credential information saved on the victim’s system.
SectorC08 group was found to be active in Ukraine and Israel, the group sent out spear phishing emails regarding to explosive installations, disseminating backdoor malwares with various functions such as system monitoring.
SectorC15 group was found to be active in Ukraine, South Korea, China, Israel, the United States, Singapore, Arab Emirates, Uzbekistan, Myanmar, and Vietnam. The group sent out COVID-19 related spear phishing emails with malwares attached which carried out various functions such as collecting basic information from systems, carrying out commands received from the C2 server or uploading and downloading files.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In May 2022, activities by a total of 3 hacking groups were identified, and the groups were SectorD01, SectorD10, and SectorD20 groups
SectorD01 group was found to be active in Jordan. The group disguised themselves as a technical skills training institution to send out spear phishing emails containing backdoor malware with various functions.
SectorD10 group was found to be active in the United States. The group used phishing websites disguised as university library and portal webpages to collect information of the targets.
SectorD20 group was found to be active in Iran, Malaysia, Israel, the United States, and France. The group used various vulnerabilities including the PowerShell vulnerability to gain initial access authorization with the purpose of collecting system information, together with ransomware attacks to gain monetary profit.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In May 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorE02, SectorE03, SectorE04, SectorE05 and SectorE06 groups
SectorE02 group was found to be active in Japan, Pakistan, England, Canada, Nepal, the United States, Poland, Sri Lanka, Vietnam, and Netherlands. The group disseminated various document format malwares such as MS Word and RTF files.
SectorE03 group was found to be active in Bangladesh. In this activity, the group utilized MS Excel documents inserted with VBA macro scripts.
SectorE04 group was found to be active in India and Austria. The group utilized MS Word documents using the template injection technique for this activity.
SectorE05 group was found to be active in Bangladesh and Pakistan. The group sent out multiple spear phishing emails attached with compressed files.
SectorE06 group was found to be active in Pakistan and Saudi Arabia. The group utilized malwares disguised as chat applications to target Android OS users.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In May 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorH03 groups
SectorH03 group was found to be active in India. The group disseminated Windows LNK files and MS Word documents disguised as university assignments, and installed RAT (Remote Access Tool) malware in the victim’s system. The installed malware carried out malicious functions such as stealing system information, keylogging, screen capturing and file downloading.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, India, so it is analyzed that they will continue activities to collect advanced information regarding Indian government agencies’ military and politics to their need.
7. Characteristics of cybercrime group activities
In May 2022, activities by a total of 8 hacking groups were identified, and the groups were SectorJ03, SectorJ09, SectorJ14, SectorJ20, SectorJ38, SectorJ48, SectorJ50, SectorJ53 groups
Unlike other government-supported hacking groups, they steal online information of monetary value in the real world or directly hacks specific companies and organizations to distribute ransomware in their internal networks, or steal important industrial confidential information and threaten to demand ransom in return.
SectorJ03 group was found to be active in Palestine and Israel. The group used malwares disguised as chat and match&date applications to target Android platforms, attempting to steal SMS data, photos, phone call recordings of the victims.
SectorJ09 group was found to be active in Turkey, Moldova, Palestine, Rumania, and Denmark. They continued using their hacking technique of inserting obfuscated skimming scripts in websites to collect username, address, email, phone numbers and credit card payment details at the payment page. In this activity, JavaScript malwares with a format like those that have been found in the past were identified, and they carried out hacking activities on organizations by using ransomwares.
SectorJ14 group was found to be active in South Korea, Japan, and Denmark. The group used malwares disguised as Japanese post office and media related Android apps to collect SMS data, photos, phone call recordings of the victims.
SectorJ20 group was found to be active in Malta and the United States. The group used steganography images with backdoor malwares hidden in, which were executed through the loader malware.
SectorJ38 group was found to be active in England, the United States, Australia, and Pakistan.
The group took advantage of the fact that virtual machine utilities were vulnerable to DLL Side Loading to load malicious DLL within the virtual machine utility, which executed Cobalt Strike at the final stage to steal system controls.
SectorJ48 group was found to be active in Finland, China, Ukraine, India, Canada, the United States, and Argentina. The group sent out spear phishing emails under the topic of security measures to disseminate PE (Portable Executable) format backdoor malware created using Metasploit.
SectorJ50 group was found to be active in Ukraine, the United States, Hungary, Malaysia, South Korea, and Japan. The group sent out payment related spear phishing emails to distribute backdoor malwares written in .NET.
SectorJ53 group was found to be active in Netherlands, Russia, France, Czech Republic, South Africa, England, India, the United States, Malaysia, Luxembourg, South Korea, Canada, and China. The group sent out invoice spear phishing emails to distribute downloader malwares which allows for the installation and execution of PenTesting tools such as Cobalt Strike and Sliver.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net
