Monthly Threat Actor Group Intelligence Report, August 2022 (ENG)
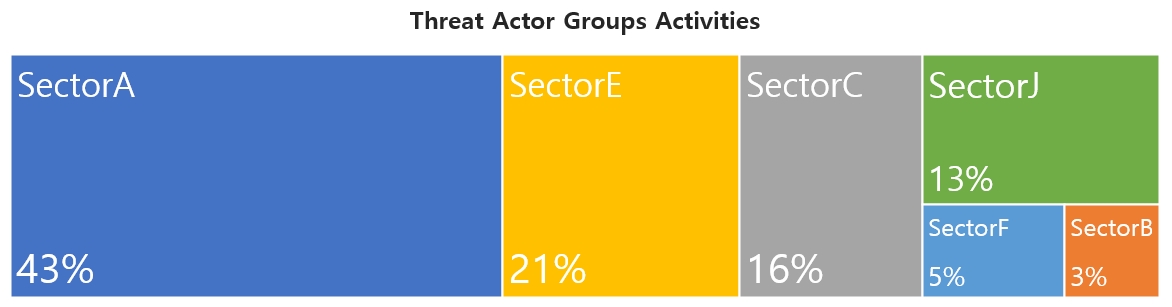
This report is a summary of Threat Actor group activities analyzed by NSHC ThreatRecon team based on data and information collected from 21 July 2022 to 20 August 2022. In August, activities by a total of 20 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 43%, followed by SectorE and SectorC groups.
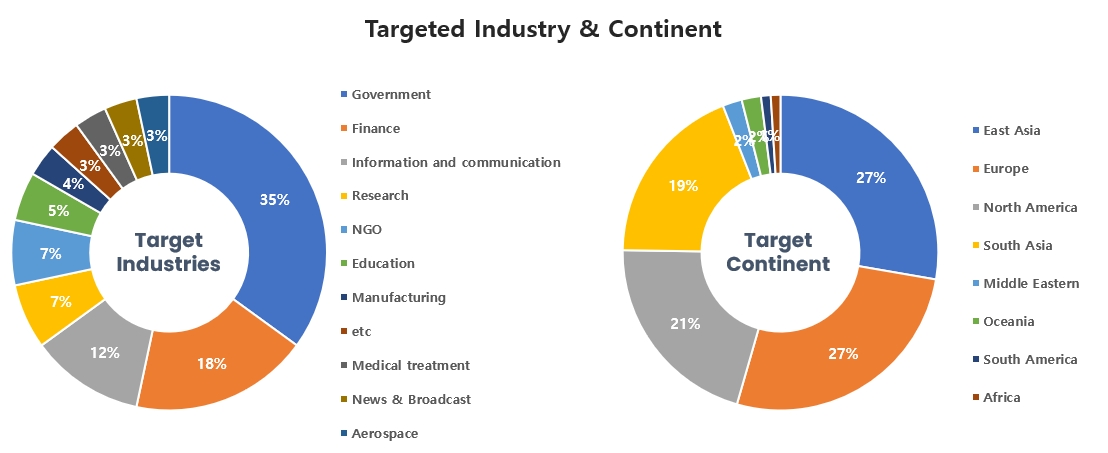
Threat Actors identified in August carried out the highest number of attacks on workers and systems in government agencies and financial industries. Regionally, East Asia and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In August 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, SectorA07 groups
SectorA01 group was found to be active in China, England, Brazil, Turkey, the United States, India, and Singapore. The group targeted on workers in the finance, IT, aerospace, and manufacturing industries to send out malwares disguised as engineer hiring documents of a specific cryptocurrency exchange.
SectorA02 group was found to be active in South Korea. The group distributed malwares disguised as document files under the title of “Business Contact” and “Transaction history”, and took over the web server of a South Korean manpower dispatch agency to use it as the C2 server.
SectorA05 group was found to be active in South Korea and the United States. The group sent out spear phishing emails disguised as notifications regarding NFT (Non-Fungible Token) reward tokens.
SectorA06 group was found to be active in Hong Kong, England, the United States, India, China, Italy, and Russia. The group disseminated Windows LNK format malwares to workers in finance industry. The malware was disguised under file names such as recruitment, salary negotiations, and revenue distribution in order to pull the attention of the targets.
SectorA07 group was found to be active in Russia and South Korea. The group disseminated MS Word format malwares utilizing the Template Injection technique. The Word format malware was disguised as a document created by a Korean learning center of a specific university and verified by a specific security solution in South Korea.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In August 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorB03 groups
SectorB03 group was found to be active in Czech Republic, the Philippines, Thailand, Vietnam, England, China, Belgium, Hungary, and Singapore. The group took over a video chatting app server, and altered files downloaded normally by users to download additional malwares.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In August 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorC08, SectorC14 groups
SectorC08 group was found to be active in Ukraine, the United States, Russia, the Philippines, Germany, Sweden, Spain, India and France. The group used MS Word format malware disguised as documents related to Ukraine, and utilized UltraVNC, a pentesting tool, in the final stage.
SectorC14 group was found to be active in the United States and England. The group targeted on workers of national security, NGO, IGO to utilize social engineering techniques and build trust with their targets on Social Network Services. Afterwards, they led the targets to access phishing websites and stole their email account credential information.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorE Group Activities
In August 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorE01, SectorE02, SectorE03, SectorE04, SectorE05 groups
SectorE01 group was found to be active in Pakistan, Rumania, India, and China. The group used template injection techniques to deliver MS Word format malwares disguised as documents by Pakistan government and Ministry of Defense.
SectorE02 group was found to be active in Ukraine, Pakistan, Singapore, Netherlands, Bangladesh, India, Austria, and Russia. The group used MS Word and RTF (Rich Text Format) document format malware disguised under topics such as meeting note format, components out-of-stock, and letters.
SectorE03 group used the technique of installing PE (Portable Executable) format malware in the target’s system and stealing system controls.
SectorE04 group was found to be active in the Philippines. The group distributed compressed files containing LNK format malware disguised as PDF file of 2022 meeting notes.
SectorE05 group was found to be active in Pakistan, the United States, India, England, and New Zealand. The group used delicately built phishing websites to lead targets to downloading android malwares.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
5. Characteristics of SectorF Group Activities
In August 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorF01 groups
SectorF01 group was found to be active in China, Hong Kong, Turkey, Vietnam, and Italy. The group disseminated MS Word format malwares disguised under titles such as law and legislation infringement related documents and marketing advertisements.
Hacking activities of SectorF carry the aim of collecting advanced information on governmental activities of countries neighboring supported government, such as political, diplomatic, and military activities, and to steal information related to cutting-edge technology for economic development of their country.
6. Characteristics of cybercrime group activities
In August 2022, activities by a total of 6 hacking groups were identified, and the groups were SectorJ01, SectorJ04, SectorJ14, SectorJ20, SectorJ26, SectorJ31 groups
Unlike other government-supported hacking groups, they steal online information of monetary value in the real world or directly hacks specific companies and organizations to distribute ransomware in their internal networks, or steal important industrial confidential information and threaten to demand ransom in return.
SectorJ01 group was found to be active in the United States. The group used XLL (Microsoft Excel add-on file) format malwares disguised as invoice related files, which collected various information from the target system such as base information or process list and sent them to the C2 server.
SectorJ04 group was found to be active in Austria and Germany. The group sent out phishing emails targeted on medical and healthcare companies, and the emails were attached with compressed IMG format files containing LNK format files disguised as resumes.
SectorJ14 group was found to be active in France and the United States. The group used Android malware disguised as Chrome web browser in order to steal Android smartphone information from various countries.
SectorJ20 group was found to be active in Malaysia, the United States, China, Netherlands, Lithuania, Bulgaria, and Nigeria. The group delivered OneDrive links through a spear phishing email, and led the targets to download compressed ISO files containing LNK format malware.
SectorJ26 group was found to be active in the United States, Germany, and France. The group targeted on law firms and airline corporations to deliver spear phishing emails attached with MS Word format malwares disguised as documents related to payment bills, resume, or legislation.
SectorJ31 group was found to be active in Germany, Hungary and Netherlands. The group acquired personal Google account credentials of the target organization, and used VPN server certifications exposed to the public to access the internal system of the target.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
