Monthly Threat Actor Group Intelligence Report, October 2022 (ENG)
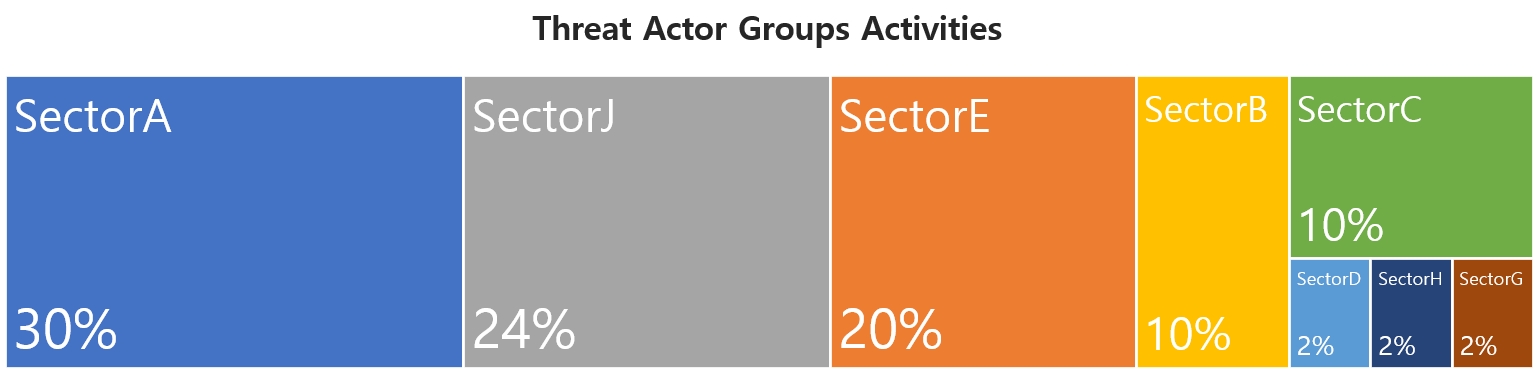
This report is a summary of Threat Actor group activities analyzed by NSHC ThreatRecon team based on data and information collected from 21 September 2022 to 20 October 2022. In October, activities by a total of 28 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 30%, followed by SectorE and SectorJ groups.
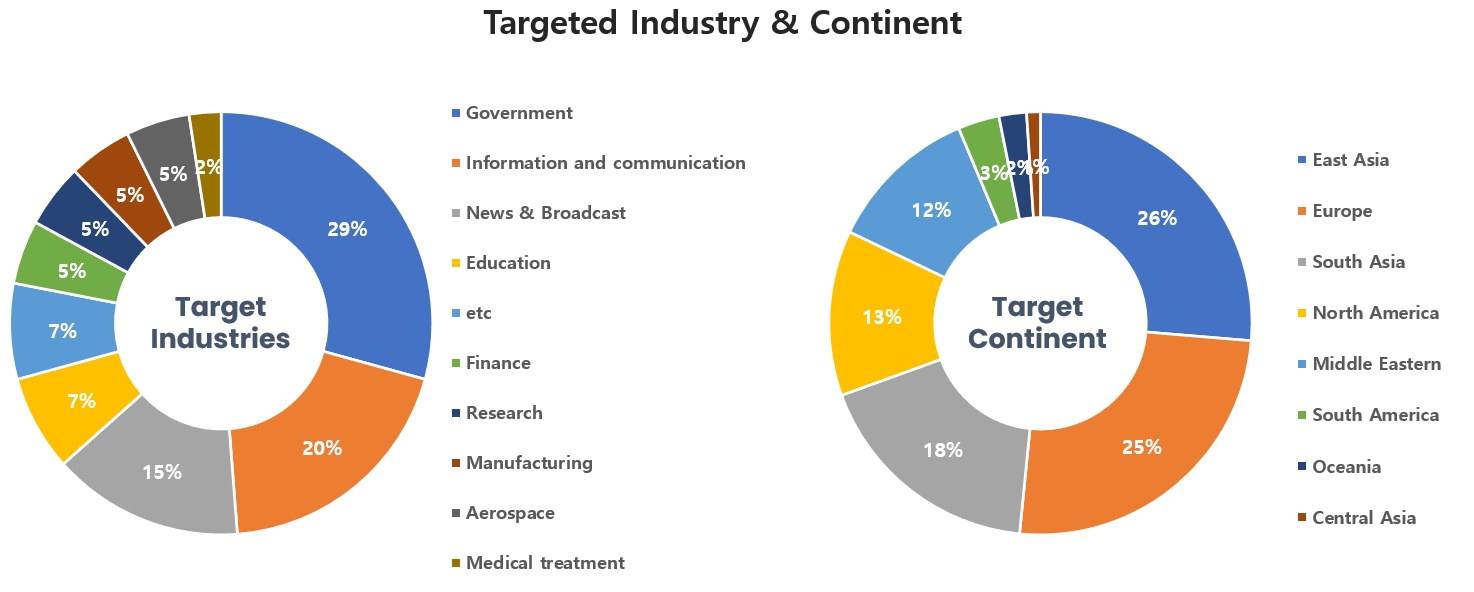
Threat Actors identified in October carried out the highest number of attacks on workers and systems in government agencies and info communication industries. Regionally, East Asia and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In October 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, and SectorA07 groups
SectorA01 was found to be active in Taiwan, England, India, Czech Republic, Hungary, Russia, the United States, South Korea, Netherlands, and Belgium. The group targeted on workers of various industries such as armory, finance, media, medicine, and aviation to carry out their attacks. For initial access, compressed ISO image files disguised as resumes were used, and the file contained PE (Portable Executable) format malware and a text file. In the final stage, an additional DLL file protected with Themida Protector was generated and executed to steal system controls.
SectorA02 group disseminated PE (Portable Executable) format malware for their activities. When the malware is executed successfully, it carries out the function of downloading and executing additional malware from the C2 server. In the final stage, the malware stole information such as infected system information and user input for encoding and transferring them to the C2 server.
SectorA05 group was found to be active in South Korea. The group targeted on workers of government entities, research institutes, media, political parties, and schools to carry out their attacks. The group sent out spear phishing emails related to failure of a mobile messenger service in South Korea. In the final stage, they used malwares protected with Themida Protect to steal system controls.
SectorA06 group was found to be active in Russia, the United States, England, Switzerland, Hong Kong, and Australia. The group disseminated LNK format malwares disguised as a normal document and a password file in a compressed file. In the final stage, malware was generated in the start programs folder to maintain persistency and use the WMI (Windows Management Instrumentation) commands to collect system information.
SectorA07 group was found to be active in South Korea. The group disseminated MS Word malwares disguised under issues related to a cryptocurrency company and utilized the template injection method where a template file inserted with malicious VBA script is downloaded and executed. In the final stage, WMI (Windows Management Instrumentation) command was used in the VBA script to collect OS version, computer name, and network information and transferring them to the C2 server.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In October 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorB01, SectorB03, SectorB04, SectorB22, SectorB58 groups
SectorB01 group was found to be active in the United States and Sri Lanka. The group targeted on workers of government institutions to disseminate ISO image file format malwares through cloud storage services such as Dropbox and Google Drive. DLL side loading technique of loading and executing a malicious DLL file using a normal program was used, and the malware carried out functions like keylogging, screen capturing, file uploading and downloading.
SectorB03 Group was found to be active in the United States, China, Vietnam, Hong Kong, Japan, Albania, and Arab Emirates. The group targeted on systems used in government institutions, electronics, and medical services for their attacks. The group exploited the Log4j vulnerability to upload a Web Shell with various functions such as file upload and download to gain initial access authorizations. The malware continuously monitors the infected system to collect information and steal system controls.
SectorB04 group exploited the Log4j vulnerability to gain initial access authorizations. Afterwards, PowerShell commands were used to generate and execute additional malware within the system, and the group used tools such as Cobalt Strike and Impacket for their attacks. The group was analyzed to have attempted to use ransomwares to encrypt important files and cause hindrance to system management.
SectorB22 group was found to be active in Romania. The group disseminated malwares and LNK format files together in a compressed file. A bait document was shown on the screen to hide the infection, and the malware continuously monitored the infected system for data collection and stealing system controls.
SectorB58 group was found to be active in Xinjiang Uygur Autonomous Region of China. The group targeted on individuals who are active in an online community for ethnic minorities in China, using Android malwares disguised under topics related to Al-Qaida military process translated in Uygur. In the final stage, the malware attempted to steal information such as text messages, contacts, call history and location information from the infected devices.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In October 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorC01 and SectorC08 groups
SectorC01 group was found to be active in Germany, Turkey, the United States, Italy, and Slovakia. The group used MS PowerPoint malwares disguised as documents related to OECD (Organization for Economic Co-operation and Development) meeting translation guidelines. In the final stage, the group used a open-source remote access tool Empire to steal system controls.
SectorC08 group was found to be active in Ukraine, Germany, Belarus, and Russia. The group used malwares disguised as government documents related to Russia and Ukraine and used a remote access tool UltraVNC to attempt information theft.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In October 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorD11 groups
SectorD11 group was found to be active in Iran and China. The group used a phishing website disguised as a webpage providing article translation services to disseminate Android malwares, then attempted to steal information such as text messages, photos, and phone call recordings from the targets.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In October 2022, activities by a total of 4 hacking groups were identified, and the groups were SectorE01, SectorE02, SectorE04, and SectorE05 groups
SectorE01 group was found to be active in France. The group disseminated a MS Word document format malware. The malware was disguised as IBAN (International Bank Account Number) list and details as well as contracts and utilized the template injection technique in which a template file inserted with malicious VBA scrips were downloaded and executed. In the final stage, the template file is seen to carry out system information collecting functions.
SectorE02 group was found to be active in Singapore, Pakistan, Bangladesh, China, and France. The group distributed document malwares under various formats such as MS Word, MS Excel, MS PowerPoints, and RTF (Rich Text Format). The document format malwares were disguised under titles such as “Repatriation of Bangladesh in Myanmar jail”, “Co-representative CEO and deputy director”, “Kashmir” which could interest the targets to lead them to execute the files. In the final stage, they used a technique of downloading additional files from the C2 server and executing them to steal system controls.
SectorE04 group was found to be active in Pakistan, Sri Lanka, England, and Hong Kong. The group sent out MS Word documents disguised as a list of medical workers approved by a Sri Lankan Administration Institution and form for receiving pension in this activity. The MS Word document malware utilizing the template injection technique downloads an additional OLE (Object Linking and Embedding) object containing a malicious macro from the C2 server and uses a C2 server domain that is like the web address of the administrative institution to deceive the targets.
SectorE05 group was found to be active in Pakistan. The group used CHM (Compiled HTML Help) format malware in their attacks, which were disguised under titles related to projects by Pakistan Gwadar’s STM, a Pakistani arms company. In the final stage, the malware registers itself in the scheduler to maintain persistency in the infected system and uses the Windows utility to send the computer and the username to the C2 server.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorG Group Activities
In October 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorG03 groups
SectorG03 group was found to be active in Israel. The group targeted on various industries such as IT, Engineering, Legislation, Communication, Branding and Marketing, Media, and government institutions to distribute multiple customized malwares and tools to carry out information stealing activities.
SectorG hacking groups primarily target countries that are politically rivals with the supporting government. Their recent purpose is to collect high-quality information about the politics, diplomacy, and government activities of people or countries who are opposed to the supporting government.
7. Characteristics of SectorH Group Activities
In October 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorH01 groups
SectorH01 group was found to be active in South Korea, Sweden, Italy, and Jamaica. The group disseminated PowerShell malwares to carry out information stealing activities such as keylogging and screenshotting.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, India, so it is analyzed that they will continue activities to collect advanced information regarding Indian government agencies’ military and politics to their need.
8. Characteristics of cybercrime group activities
In October 2022, activities by a total of 9 hacking groups were identified, and the groups were SectorJ03, SectorJ06, SectorJ09, SectorJ25, SectorJ45, SectorJ53, SectorJ64, SectorJ66, SectorJ68 groups
Unlike other government-supported hacking groups, they steal online information of monetary value in the real world or directly hacks specific companies and organizations to distribute ransomware in their internal networks, or steal important industrial confidential information and threaten to demand ransom in return.
SectorJ03 group was found to be active in Palestine, India, and Iraq. The group used malwares targeted on the Android platform to collect information such as text message information, photos, and phone call recordings from the target.
SectorJ06 group was found to be active in Spain, Portugal, Greece, Russia, Ukraine, Germany, Turkey, Denmark, England, the United States, Armenia, Brazil, Czech Republic, Mexico, Uruguay, Peru, India, Israel, Arab Emirates, Saudi Arabia, Lithuania, Iraq, Angola, Moldova, and South Korea. The group exploited OneDrive’s DLL (Dynamic Library Link) Side-loading vulnerability to use cryptojackers that mines cryptocurrencies.
SectorJ09 group continued using their hacking technique of inserting obfuscated skimming scripts in websites to collect username, address, email, phone numbers and credit card payment details at the payment page. In this activity, JavaScript malwares with a format like those that have been found in the past were identified.
SectorJ25 group was found to be active in China, the United States, Russia, and Singapore. The group targeted on cloud and container environments to use cryptojackers that mines cryptocurrencies.
SectorJ45 group was found to be active in the Netherlands, Sweden, South Korea, Germany, France, Norway, Thailand, Japan, Singapore, and Spain. The group targeted on users of the expired Internet Explorer service to exploit malvertising techniques that misuses advertisement services. In the final stage, the group collected information from the system and mined for cryptocurrencies in the target’s system.
SectorJ53 group was found to be active in Canada, Italy, Arab Emirates, the United States, Iran, China, Germany, Turkey, India, England, Israel, France, South Africa, Hong Kong, South Korea, Russia, Gibraltar, Denmark, Portugal, Ethiopia, Cote D’lvoire, Kazakhstan, Australia, Sweden, Taiwan, Japan, Argentina, Poland, Estonia, Netherland, Romania, Georgia, Hungary, Bulgaria, Thailand, Belgium, Iraq, Qatar, Mexico, Greece and Spain. The group used malwares disguised as invoice related files and used downloader malwares to download and execute PenTesting tools such as Sliver and Cobalt Strike in the final stage.
SectorJ64 group was found to be active in China, Sweden, and England. The group targeted on servers with vulnerabilities for their attacks, and attempted cryptomining in the final stage.
SectorJ66 group was found to be active in Vietnam, Spain, Portugal, Russia, Germany, Canada, Czech Republic, Japan, Chile, Turkey, Ukraine, Brazil, Poland, India, Italy, Hong Kong, Romania, Columbia, England, Venezuela, France, Tunisia, China, and the United States. The group used BPH (Bulletproof hosting) services that provides network infrastructure for carrying out malicious activities freely.
SectorJ68 group was found to be selling malwares with various functions such as cryptomining and information stealing as MaaS(Malware-as-a-Service) for monetary purposes.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
