Monthly Threat Actor Group Intelligence Report, November 2022 (ENG)
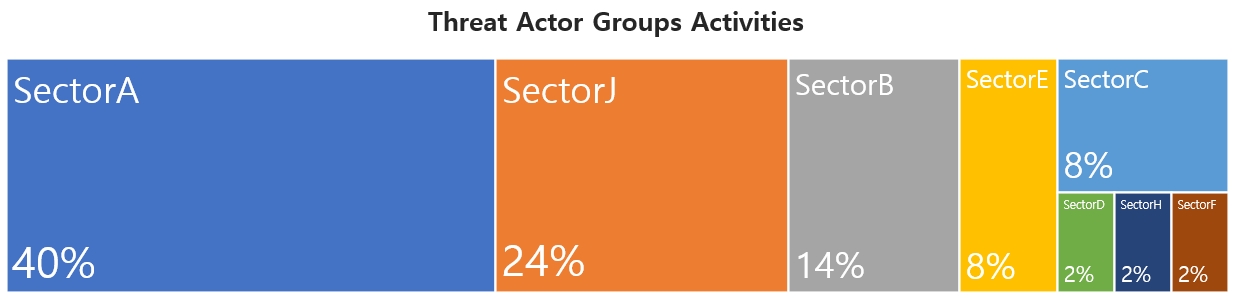
This report is a summary of Threat Actor group activities analyzed by NSHC ThreatRecon team based on data and information collected from 21 October 2022 to 20 November 2022. In November, activities by a total of 29 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 40%, followed by SectorJ and SectorB groups.
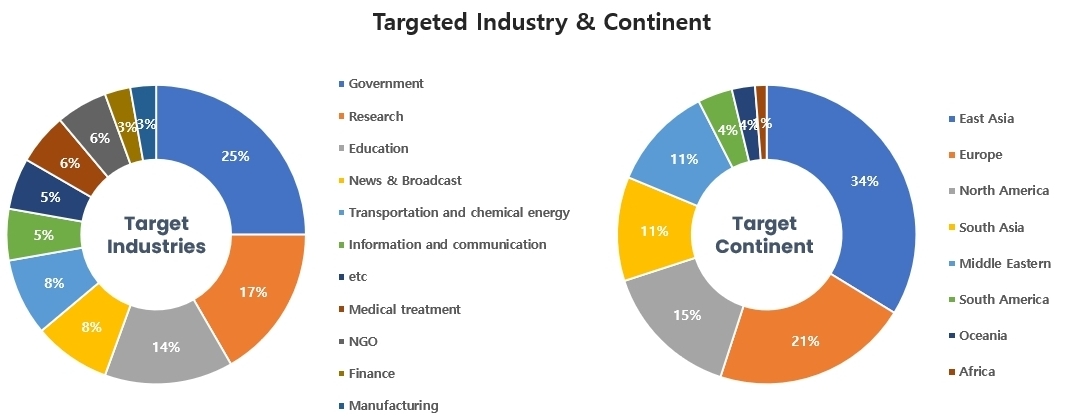
Threat Actors identified in November carried out the highest number of attacks on workers and systems in government agencies and research institutions. Regionally, East Asia and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In November 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, and SectorA07 groups
SectorA01 group was found to be active in South Korea, England, Romania, the United States, Armenia, Turkey, and Egypt. The group exploited a vulnerability of an electronic signature and data encryption/decryption solution to incapacitate security programs and penetrate into the internal system. Afterwards, additional malware was executed within the system to steal system controls.
SectorA02 group was found to be active in South Korea. The group targeted on workers of media and North-Korea related policies to distribute MS Word malwares. The document used in the attack was disguised under topics such as the Itaewon tragedy, issue report written by RIES (Research Institute of the East-West Economy & Society), and NLL (Northern Limit Line) that would interest the target.
SectorA05 group was found to be active in South Korea and France. The group targeted on workers of government entities, research institutes, energy and media industries to distribute MS Word documents disguised as News survey and resumes. The document was found to have been an maliciously edited and distributed copy of a document provided by the Ministry of Government Legislation.
SectorA06 group was found to be active in Japan. The group distributed Windows LNK format malwares disguised as Password files. In the final stage, msiexec (Windows Installer Utility) was used to download a MSI (Microsoft Installer) file from the C2 server and execute it to collect information and steal system controls.
SectorA07 group was found to be active in the United States and Singapore. The group used CHM (Compiled HTML Help) format files in their attack, which were disguised under subjects related to China’s head of state. In the final stage, the malware carried out the function of using PowerShell commands to collect computer and username information from the infected system to be sent to the C2 server.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In November 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorB04 SectorB05 SectorB22, SectorB31, SectorB38 groups
SectorB04 group was found to be active in Japan. The group targeted on government entities and diplomatic institutions for their attacks. For their initial access technique, they used a MS Word malware disguised under topics related to the U.S.-Japan alliance. In the final stage, additional malwares were generated and executed through the DLL side loading technique, providing the base for penetrating into the internal systems by collecting information from the infected system.
SectorB05 group was found to be active in China, the United States, Russia, Syria, and Xinjiang Uygur Autonomous Region. The group targeted on individuals active on China’s ethnic minority communities to disseminate Android malwares. The malwares were disguised as apps that were frequently used and could interest the targets, such as video sharing platform, video call, voice chat, translator, dictionary, and religion. In the final stage, the malware carries out the function of collecting information such as text messages, contracts, phone call history and location information.
SectorB22 group was found to be active in Poland, the Philippines, Myanmar, Thailand, the United States, Canada, Hong Kong, India, Australia, Taiwan, and Japan. The group targeted on workers of government entities, academia, foundations, and research fields to send out spear phishing emails. The email used as initial access contained a link to a Google Drive, leading the targets to download the malware. In the final stage, the malware carries out the function of collecting information such as process details, user and computer name, and OS information and sends them to the C2 server.
SectorB31 group attached a malware to a compressed file disguised under filenames related to an online shopping mall and information websites.
SectorB38 group was found to be active in Australia. The group disseminated MS Word document format malwares. The malware written in Vietnamese was disguised under topics related to info-communication application technologies and demand surveys. When executed, it utilizes the template injection technique to download template files containing malicious macros. In the final stage, DLL file is downloaded from the C2 server and executed as a rundll32.exe (Windows application program) file to steal system controls.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In November 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorC08 and SectorC13 groups
SectorC08 group was found to be active in Ukraine, Lithuania, and Russia. The group used malwares disguised as administrative and security regulation documents of government institutions and attempted to steal information through a remote access tool UltraVNC in the final stage.
SectorC13 group was found to be active in Russia and Belarus. The group targeted on the Ministry of Foreign Affairs to send out phishing emails disguised as diplomatic journals to lead the targets to execute an MS Word malware utilizing the template injection technique.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In November 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorD11 groups
SectorD11 group was found to be active in Germany. The group distributed Android malwares disguised as music player applications, attempting to steal information such as text messages, photos and phone call recordings from the targets.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In November 2022, activities by a total of 3 hacking groups were identified, and the groups were SectorE01, SectorE02, SectorE04 groups
SectorE01 group distributed a PE (Portable Executable) format malware. The malware was found to have been exploiting the digital signature details of a specific company. When executed, the malware uses the WMI (Windows Management Instrumentation) commands to collect installed software and services information from the infected system and sends them to the C2 server.
SectorE02 group was found to be active in Germany, Oman, the United States, and Netherlands. The group distributed MS Word and RTF (Rich Text Format) document malwares disguised under titles such as “Quality Assurance Program”, “Visiting Program”, “Update” to interest the targets. When executed, the malware uses a malicious macro script to download and execute additional malwares.
SectorE04 group was found to be active in England, Pakistan, Bulgaria, and Hong Kong. The group delivered ISO image files to the target as an initial access method, which contained a Windows LNK file, a bait document, and a PE(Portable Executable) format malware. In the final stage, the malware downloads additional malware from the C2 server, and uses it to steal system controls.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorF Group Activities
In November 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorF01 groups
SectorF01 group was found to be active in Taiwan, England and China. The group exploited vulnerabilities to obtain initial access to the target’s system, then generated and executed an ELF(Executable and Linkable Format) malware within the system. In the final stage, tools such as Mimikatz and Cobalt Strike was used to steal information and system controls.
Hacking activities of SectorF carry the aim of collecting advanced information on governmental activities of countries neighboring supported government, such as political, diplomatic, and military activities, and to steal information related to cutting-edge technology for economic development of their country.
7. Characteristics of SectorH Group Activities
In November 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorH03 groups
SectorH03 group was found to be active in Pakistan. The group distributed Windows LNK format malwares disguised as Adobe PDF documents for their attacks. The LNK file was seen to be the base file used in the initial access stage in order to set the grounds for additional attacks in the targeted system, and carries the function of downloading and executing other malwares.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, India, so it is analyzed that they will continue activities to collect advanced information regarding Indian government agencies’ military and politics to their need.
8. Characteristics of cybercrime group activities
In November 2022, activities by a total of 10 hacking groups were identified, and the groups were SectorJ03, SectorJ05, SectorJ06, SectorJ25, SectorJ26, SectorJ39, SectorJ44, SectorJ73, SectorJ75, SectorJ81 groups
Unlike other government-supported hacking groups, they steal online information of monetary value in the real world or directly hacks specific companies and organizations to distribute ransomware in their internal networks, or steal important industrial confidential information and threaten to demand ransom in return.
SectorJ03 group was found to be active in Palestine and Qatar. The group used MS Word documents of Hamas themes as the bait document, and attempted to steal information from the target’s system.
SectorJ05 group was found to be active in India, Netherlands, Switzerland, Ireland, the United States, and Romania. The group used malwares disguised as Google’s update file, which collects information from the target’s system and downloads and executes additional malwares depending on the attacker’s commands.
SectorJ06 group was found to be active in Brazil and the United States. The group targeted on servers with unpatched vulnerabilities to carry out ransomware attacks with the purpose of gaining financial profits.
SectorJ25 group was found to be active in China and Israel. The group used cryptojackers which mines for cryptocurrencies in cloud and container environments.
SectorJ26 group was found to be active in South Korea, India, Canada, the United States, Germany, Lithuania, Mexico, Thailand, Columbia, Kenya, Italy, Sweden, Hong Kong, Singapore, Netherlands, Pakistan, and England. The group used malwares disguised as tax billing PDF documents, and uses backdoor malwares for stealing system authorizations in the final stage.
SectorJ39 group was found to be active in Ukraine, China, Spain, Canada, Arab Emirates, England, Palestine and Czech Republic. The group used malwares disguised as PDF Reader update files, and uses backdoor malwares for stealing system authorizations in the final stage.
SectorJ44 group was found to be active in South Korea. The group used Surtr ransomwares with the aim of gaining financial profits, which encrypts files in the system and generates a ransom note to deliver contact points for financial discussions.
SectorJ73 group was found to be active in the United States, Denmark and Cyprus. The group targeted on the education industry to use Zeppelin ransomware for financial profit purposes, together with a backdoor malware to collect and leak data.
SectorJ75 group was found to be active in Sweden, Bolivia and the United States. The group used malware disguised as Network Scanning Software, and Somnia ransomware in the final stage.
SectorJ81 group was found to be active in Indonesia and China. The group used phishing websites that led the targets to click on them by luring them with prize winnings. When the target clicks on the link, they were redirected to an advertisement page that brings advertisement profit to the group, or disseminate Android malwares.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
