Threat Actor targeting Vulnerable Links in Cyber Security (ENG)
Introduction
In Scotland, there is an old saying that “A chain is only as strong as its weakest link”. This idiom means that no matter how robust a chain is, if there is a weak link in the chain, the chain will no longer be a strong chain.
Similarly, a weak link exists in the world of cybersecurity as well. Despite how sturdy a security solution is, there will always be a weak link, and a single vulnerability connected to the weak link will affect the entire security solution, so organizations always need to be on alert for any vulnerabilities that may exist.
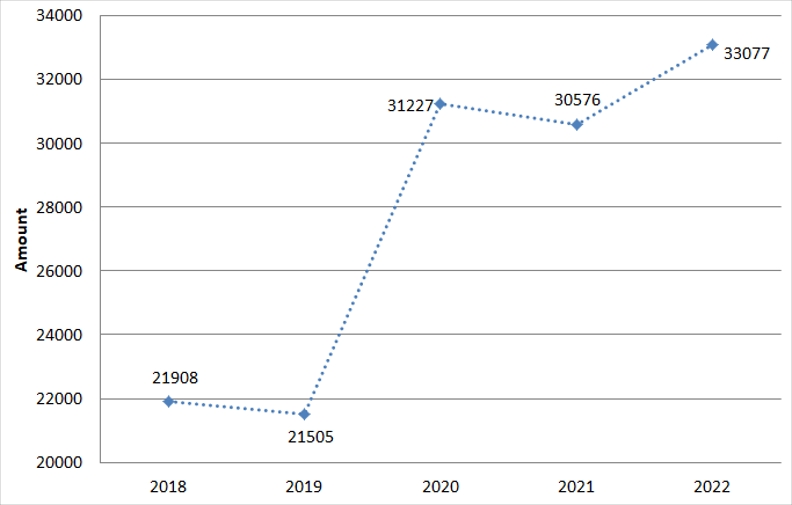
Definition and classification of most software vulnerabilities are controlled under the CVE (Common Vulnerabilities and Exposures) system. From the trend of vulnerabilities over the past 5 years, it is seen that the total number of vulnerabilities increased by more than 1.5 times from 200,000 in 2019 to over 300,000 since 2020 onwards, and considering that the vulnerabilities continue to exist in systems where the patch for removing the software vulnerability detected in the past have not been installed, the number of vulnerabilities that could be used in cyberattacks show a drastic increase.
[Figure 1: Trend of vulnerabilities over the past 5 years (Taken from: https://cve.mitre.org/)]
Nowadays, the number of software vulnerabilities that could be utilized in cyberattacks has been showing a steep increase, but the truth is that the security organization that should be carrying out inspections and take necessary measures regarding the vulnerabilities have limited resources to do so.
With regards to this background, ThreatRecon Team has utilized the ThreatRecon Platform which holds onto the data of vulnerabilities exploited at least once in actual cyberattacks to analyze such activities to help organizations carry out measures suitable for their environment. This report presents the explanation to the vulnerabilities exploited by threat actors in 2022 for various purposes, as well as an analysis to the type of software exploited and how such vulnerabilities were utilized in each stage of cyberattack.
THREAT ACTOR TARGETING VULNERABLE LINKS IN CYBERSECURITY
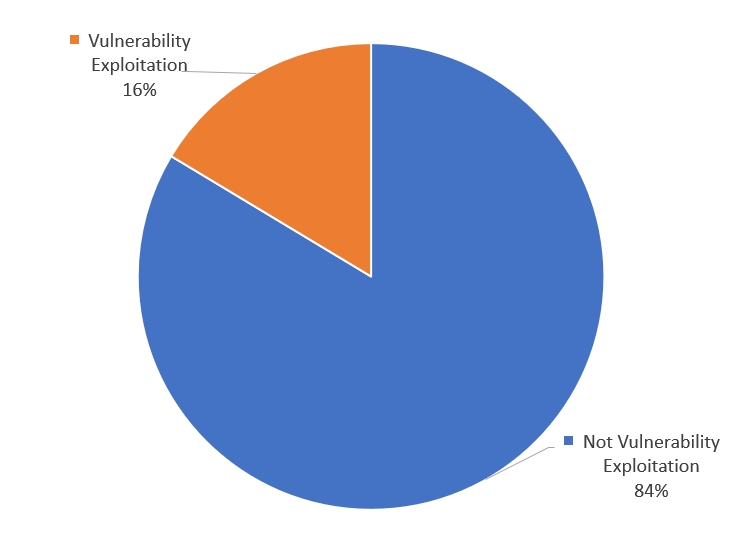
The distribution regarding percentage of vulnerability-exploiting cyberattacks in 2022 as analyzed by the ThreatRecon Team can be identified in [Figure 2]. 16% of all cyberattacks were vulnerability exploiting cyberattacks, and most cyberattacks that took up the 84% were not related to vulnerabilities. Most cyberattacks were carried out through leading the target to click on the phishing link or executing a malware through phishing emails, as well as using advertisement pages to target mass audience or taking advantage of stolen credentials.
If a threat actor aims to exploit a vulnerability without prior knowledge of the target’s system, and there are no systems affected by the vulnerability, the preparation process goes to waste, thus there is a need for Information Gathering regarding the target system before the attack. Threat actors need to identify the vulnerabilities within the target system through the process of information gathering and analyzing the target system to have better understanding of the structure, so if there are no known vulnerabilities, the threat actors need to find new vulnerabilities to carry out their attacks.
Vulnerability exploitation has such limitations, but threat actors are willing to invest resources to vulnerability research when the profit is deemed higher or when they aim to steal high-value information, so vulnerability exploiting attacks were able to takes up 16% of all cyberattacks in 2022.
[Figure 2: Percentage of vulnerability exploiting attacks among cyberattacks in 2022]
1) THREAT ACTOR EXPLOITING SOFTWARE VULNERABILITIES
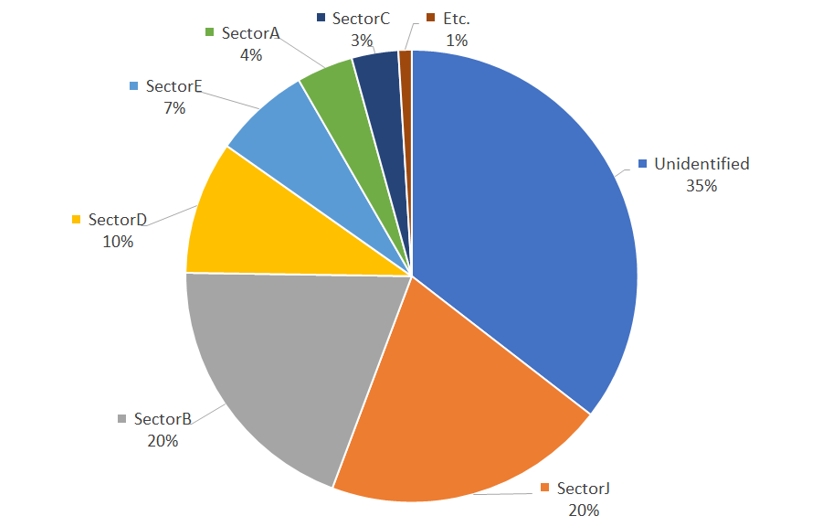
The distribution related to the percentage of vulnerability-exploiting hacking group activities among all threat actor activities can be identified in [Figure 3]. Excluding unidentified threat actors, vulnerabilities were most often exploited by SectorJ and SectorB followed by SectorD and SectorE groups.
As unidentified threat actors which consist of a large number of cybercrime hacking groups and SectorJ, carry out hacking activities with the aim of securing financial resources, these groups stole high-value information that could offset the resources used to exploit the vulnerability, or distributed ransomwares and crypto mining software.
Cybercrime hacking groups often utilized vulnerabilities through self-research, but those lacking in technical skills could purchase vulnerability-attacking codes in the Deep and Dark web, which was seen to be the reason to high exploitation rate of vulnerabilities. In addition, most cybercrime hacking groups do not limit their target to specific organizations or people, but generally carry out extensive attacks on mass audience with specific vulnerabilities, thus showing a higher rate of exploitation.
On the other hand, SectorB shows a trait of targeting on specific individuals or organizations holding onto important information of the nation such as political, defense and diplomacy. When targeting specific groups, there needs to be prior knowledge on the system used by the target, and human resources as well as a long period of time is needed to carry out the attacks, thus resource investment is necessary.
As such, SectorB groups show a high exploitation rate of vulnerabilities as they have enough human resource for operation of cyberattacks, and they have access to a large resource to sustain the hacking groups over a long period of time.
[Figure 3: The distribution of threat actor group that utilized vulnerabilities among cyberattacks in 2022]
2) SOFTWARE WITH IDENTIFIED VULERABILITIES
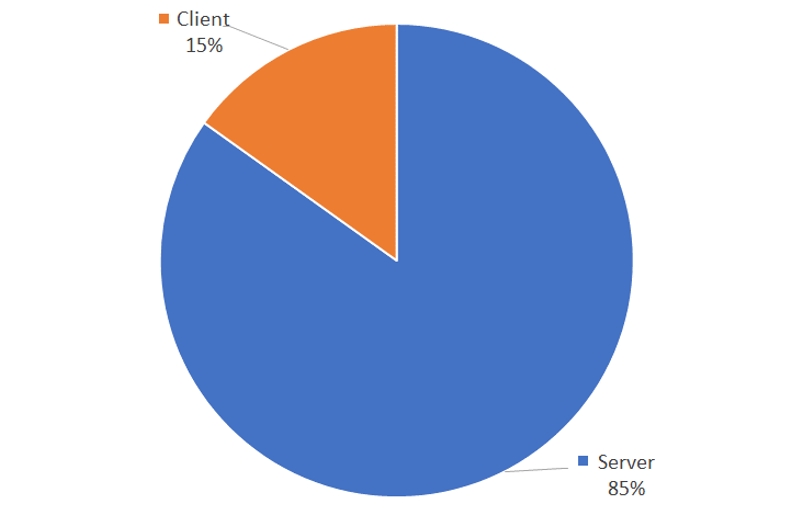
Software with identified vulnerabilities could be classified into two main portions, the server and the client. The server-type vulnerabilities consisted of operating systems, OS components such as kernel and protocol, software installed in hardware such as firmware, mail and web servers. Client-type vulnerabilities include web browser and document editing programs.
The distribution of software types with found vulnerabilities can be identified in [Figure 4], and the most commonly identified software type were the server types.
When a server type vulnerability is exploited, the vulnerable system connected to the internet acts as the base for approaching other internal systems with high-value sensitive data. As such, a single system could affect all other systems in the internal network, thus server type vulnerabilities are most commonly exploited as it affects a larger range of systems compared to client type vulnerabilities.
[Figure 4: Ratio of identified software type vulnerabilities in 2022]
3) VULNERBLE AREAS OF SOFTWARES WITH HIGH EXPLOITATION RATE
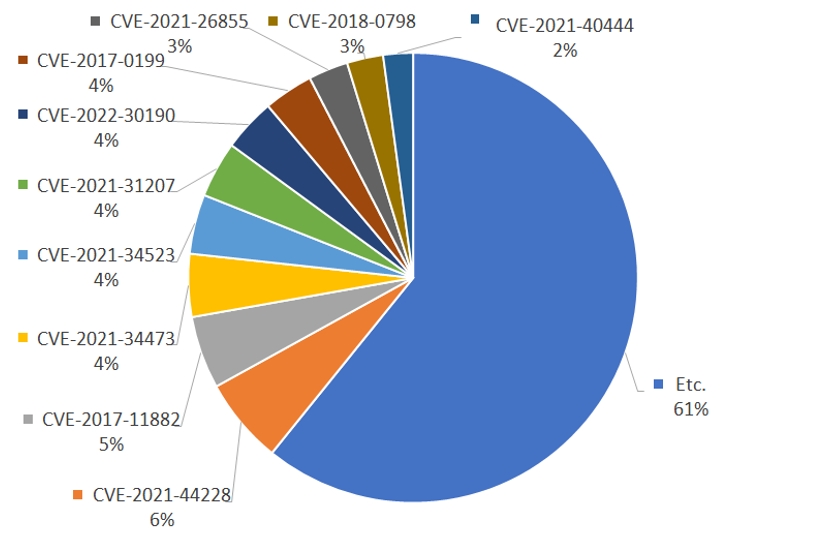
The distribution of vulnerabilities that were most commonly exploited by threat actors can be identified in [Figure 5], and the top 10 vulnerabilities took up 39% of all vulnerabilities found.
Among all vulnerabilities, CVE-2021-44228 vulnerability was seen to have been most exploited, followed by CVE-2017-11882, CVE-2021-34473, CVE-2021-34523 in sequence.
Among the top 10 vulnerabilities, 9 of them were patched more than a year ago, and one of them was even patched in 2017. This shows that even if the information regarding the vulnerability is released, there will be individuals or organizations that do not carry out measures immediately, and if they are using licenses with expired software support, usage of additional financial resources to resolve the vulnerability becomes obligatory, and preparation of old vulnerabilities become difficult.
The CVE-2021-44228 vulnerability of Apache Log4j library, which is used to leave logs, targeted on numerous vulnerable serves through scans, leading to the highest exploitation rate, and all following client type vulnerabilities were all related to Microsoft Office, the document editing software.
This was seen to be because the software is used worldwide, leading to a large scope for attack, and tools to exploit the vulnerabilities are easier for purchasing or building based on the information released regarding the vulnerability.
[Figure 5: Top 10 most exploited vulnerability in 2022]
Software vulnerability |
Details |
|
| 1 | CVE-2021-44228 | Vulnerability that occurs in Log4j 1.2 version. A remote code execution is possible during the process of JNDI (Java Naming and Directory Interface) receiving log messages containing a specific format. |
| 2 | CVE-2017-11882 | Vulnerability that occurs when Equation Editor in Microsoft Office does not validate the length of the value used, and remote code execution is possible through this vulnerability |
| 3 | CVE-2021-34473 | Vulnerability that occurs in Microsoft Exchange Server, allows remote code execution |
| 4 | CVE-2021-34523 | Vulnerability that occurs in Microsoft Exchange Server, allows authorization escalation |
| 5 | CVE-2021-31207 | Vulnerability that occurs in Microsoft Exchange Server, allows antivirus evasion |
| 6 | CVE-2022-30190 | Vulnerability that occurs when MSDT is called through connecting using URL written in External tag of Microsoft Office Word documents, allows remote code execution |
| 7 | CVE-2017-0199 | Vulnerability that occurs through OLE(Object Linking and Embedding) in Microsoft Office/WordPad, allows remote code execution |
| 8 | CVE-2021-26855 | Vulnerability that occurs in Microsoft Exchange Server, allows remote code execution |
| 9 | CVE-2018-0798 | Vulnerability that occurs due to input validation fails in Microsoft MSHTML engine, allows remote code execution |
| 10 | CVE-2021-40444 | Vulnerability that occurs due to input validation fails in Microsoft MSHTML engine, allows remote code execution |
[Table 1: Top 10 vulnerabilities]
4) THREAT ACTOR EXPLOITING ZERO DAY VULERABILITIES
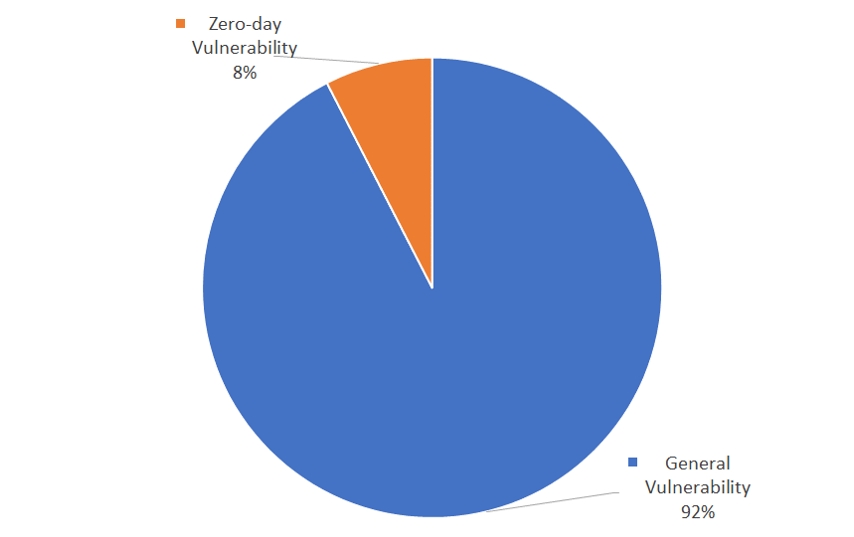
Among cyberattacks carried out through exploiting vulnerabilities, the distribution regarding zero-day exploiting attacks can be identified in [Figure 6]. Cyberattacks exploiting zero-day vulnerabilities were seen to take up 8% of all vulnerability exploiting attacks.
Finding zero-day vulnerabilities requires a long period of time and a large resource thus they are seen to be utilized lesser. Despite this, threat actors invest time and resources into finding zero-day vulnerabilities as they are able to evade security solutions in the initial access stage, making detection difficult and acts as the crucial element that increases the success rate of the attacks.
[Figure 6: Percentage of zero-day vulnerability exploitation among all vulnerability exploiting cyberattacks in 2022]
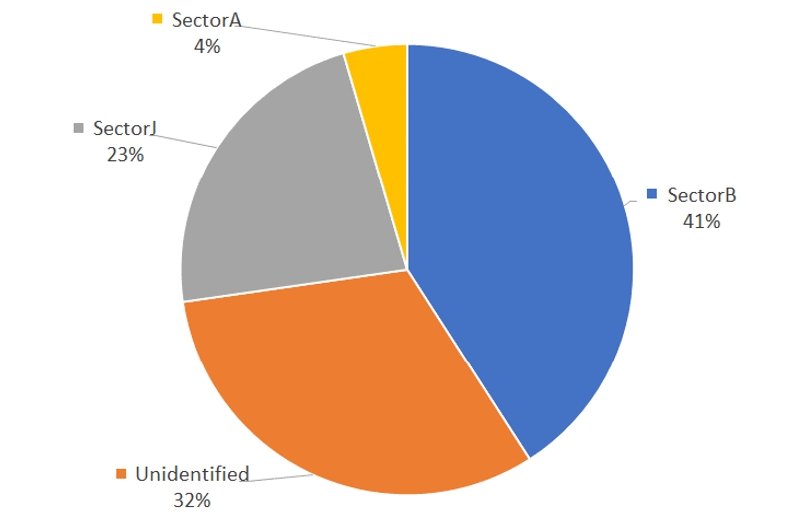
The distribution of hacking groups that exploited zero-day vulnerabilities can be identified in [Figure 7]. SectorB, was seen to have exploited zero-day vulnerabilities the most, followed by unidentified groups, SectorJ and SectorA.
As exploiting zero-day vulnerabilities require more time and resources compared to known vulnerabilities, attacks by SectorB groups which can be supported with plenty of resources by the government were seen to have carried out the greatest number of activities with zero-day vulnerabilities.
In addition, platforms where zero-day vulnerabilities can be traded, such as Dark and Deep web, allowed for cybercrime hacking groups to exploit more zero-day vulnerabilities, and there is a possibility that cybercrime groups with higher-level technology would have invested time and resources to research on zero-day vulnerabilities by themselves.
[Figure 7: Distribution of hacking group activities exploiting zero-day vulnerabilities]
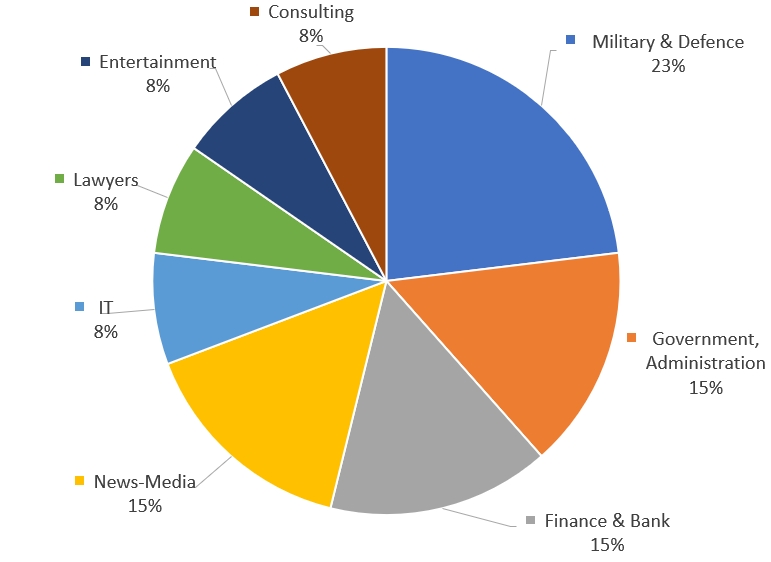
The distribution of industries targeted using zero-day vulnerability exploitation can be identified in [Figure 8]. National defense and related sectors were seen to have been targeted the most, with 23% of all attacks targeted on the industry. They were followed by government entities that have government activity related data such as politics and diplomatic information, public institutions, financial sector which holds on to financial information and data, and news-media that deals with various broadcast data over multiple industries.
National defense sectors contain advanced technique and high-value information that could affect national defense in order to ensure safety of civilians from external factors, which was seen to be the reason of being targeted the most. In addition, it is believed that many attacks were carried out on government and public institutions with the purpose of stealing information related to national policies that shows the direction of national operation. Financial industries have the highest possibility of gaining financial profit immediately upon succeeding the attack, which was seen to be the reason of being the most popular target of hacking groups aiming to secure financial assets.
In the case of news-media workers, they were seen to have been targeted as they show possibilities of being links to other industries dealing with important national and corporation related data, and other industries such as IT, entertainment, law, consulting services that could be affected directly in terms of customer service operation were the targets of zero-day vulnerabilities.
[Figure 8: Distribution of industries targeted for Zero Day attacks]
CLASSIFICATION OF SOFTWARE VULERABILITY
1) MANUFACTURERS WITH VULNERABILITIES IDENTIFIED
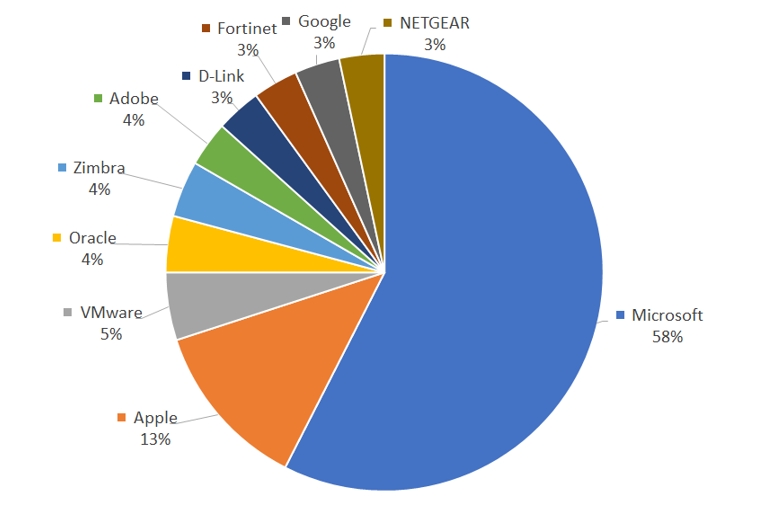
The statistics of products that have been most affected by vulnerabilities can be identified from [Figure 9]. Microsoft products showed the highest number of vulnerabilities exploited by threat actors, followed by Apple, VMware, and Oracle.
As Microsoft products are used widely over the world, various vulnerabilities are exploited, leading vulnerabilities related to Microsoft products taking up more than half of all cyberattacks worldwide. Next in line are Apple products, numbered at an unexpectedly high value, which was seen to be an effect of increased usage of Apple products in personal and organizational environments, leading to more cyberattacks targeted on Apple products.
[Figure 9: Distribution of top 10 manufacturers affected by vulnerabilities]
제조사 |
제품 |
|
| 1 | Microsoft | Active Directory, Excel, Exchange Server, Internet Information Services(IIS), .NET Framework, Edge, Internet Explorer, Enhanced Cryptographic Provider, MSHTML, MSCOMCTL.OCX, Netlogon Remote Protocol (MS-NRPC), PowerPoint, Remote Desktop Services, SMBv1, SMBv3, Win32k, Windows, Windows Server, WinVerifyTrust function, Word |
| 2 | Apple | iOS, macOS, iPadOS |
| 3 | VMware | Cloud foundation, Identity manager, Vrealize automation, Vrealize suite lifecycle manager, Spring Framework, vCenter Server, Workspace ONE |
| 4 | Oracle | WebLogic Server |
| 5 | Zimbra | Collaboration, Webmail |
| 6 | Adobe | Acrobat Reader, Flash Player |
| 7 | D-Link | DCS-930L Devices, DIR-610 Devices, DIR-645 Router, DSL-2760U |
| 8 | Fortinet | FortiOS, FortiADC |
| 9 | Chrome, Chromium | |
| 10 | NETGEAR | DGN2200 Devices, Wireless Access Point Devices, Wireless Router DGN2200 |
[Table 2: List of software affected by vulnerabilities]
2) TYPES OF SOFTWARE VULNERABILITIES
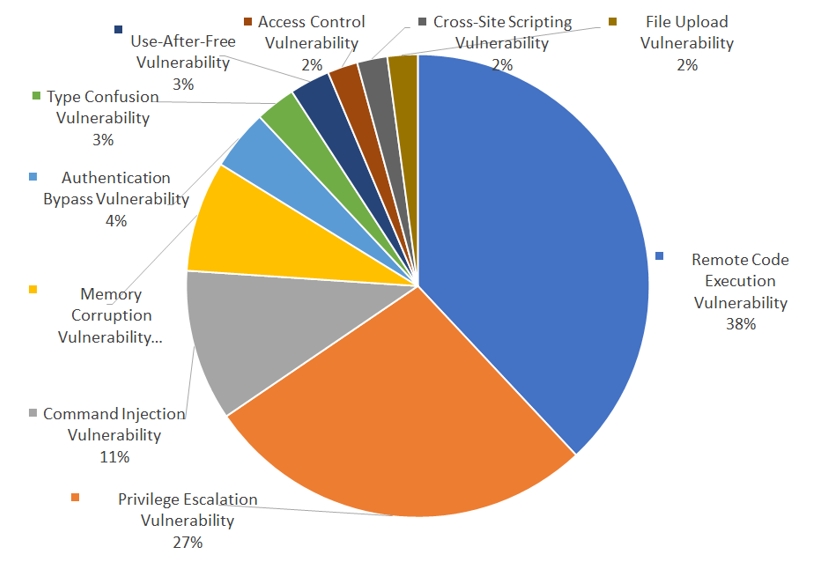
The distribution regarding types of software vulnerabilities exploited in cyberattacks could be identified in [Figure 10]. Threat actors were most often seen to be exploiting the remote code execution vulnerability, followed by privilege escalation, command injection and authentication bypass. Cyber threat actors install malware or software in the targeted system to accomplish their aim, and remote code execution vulnerability is seen to have been exploited most in the process. In addition, vulnerabilities regarding authorization escalation were also often exploited to gain access to higher authorization such as Administration authorization, such that maximum activities could be achieved in the infected system.
[Figure 10: Ratio of top 10 types of vulnerabilities that occurred in year 2022]
3) STAGES OF ATTACKS EXPLOITING SOFTWARE VULNERABILITIES
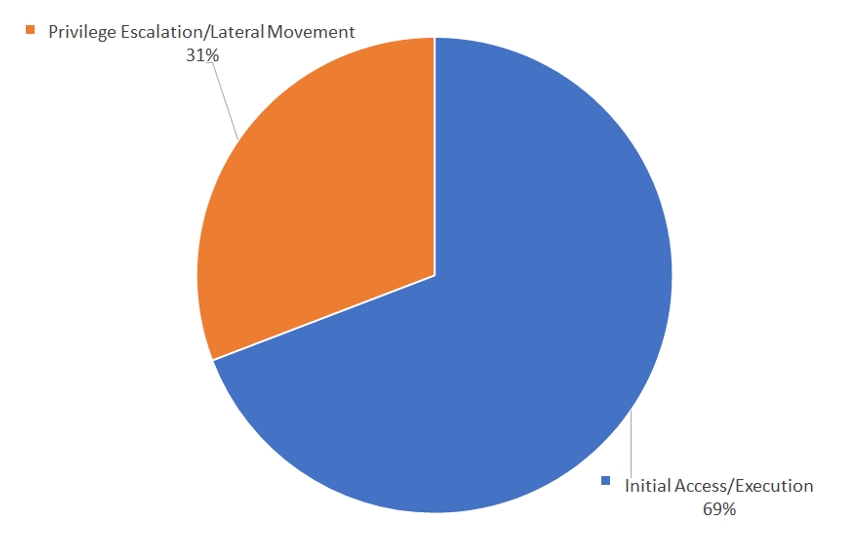
The distribution of software vulnerabilities per attack stage is shown in [Figure 11].
The stages of attacks of threat actors that exploits vulnerabilities were divided based on Tactic of MITRE ATT&CK Matrix that descripted the hacking stages and detailed hacking techniques per stages, into two stages. The first stage is the Initial Access/Execution stage that attempts penetration into the system and execution of malwares, and the second stage is the Privilege Escalation/Lateral Movement stage where the attacker obtains higher authorizations and attempts to carry out lateral movement within the organization’s network.
Threat actors often search the Attack Surface to utilize vulnerability for penetration purposes, so vulnerabilities are mostly used in the Initial Access/Execution stage, and the rate of vulnerability exploitation was comparatively low in the Privilege Escalation/Lateral Movement stages as various open-source tools such as Cobalt Strike and Mimikatz could be used for authorization escalation and network lateral movement within the organization.
[Figure 11: Percentage of vulnerability-exploiting attacks used per each stage, year 2022]
CONCLUSION
We have taken a look at software vulnerability exploiting cyberattacks carried out by government-subsidized threat actors and financially driven cybercrime threat actors in 2022.
Cyberattacks that exploits software vulnerabilities were seen to have been most actively carried out by SectorB and SectorJ. In addition, cyberattack activities exploiting Zero Day vulnerabilities were often used by major threat actors with enough financial resources to purchase or research on Zero Day vulnerabilities, and they most commonly targeted on high-value industries with valuable information and assets that could compensate for the loss occurred by utilizing the zero-day vulnerabilities.
Threat actors set the base of penetrating into the internal system by exploiting vulnerabilities, and mainly targeted on server-based systems to obtain high added value information. The highest number of exploited vulnerabilities belonged to Microsoft’s products, due to their high usage rate throughout the world. In addition, among all vulnerabilities exploited by threat actors, a total of 69% of the vulnerabilities were used in the stage of initial access into the organization networks and executing malwares, to evade security solution detection and penetrate the intranet.
Software vulnerabilities occur constantly every year, so companies carry out inspections and security measures to solve the issues. However, they face problems such as having vulnerabilities that continuously appear despite repetitive inspections and managements, and the resources that goes into the management of such issues are not something to overlook as well.
From the point of view of someone who takes charge of an organization’s security, acquiring cyber threat intelligence related to vulnerabilities exploited by cyber threat actors and the stages of attack that utilizes the vulnerability will benefit an organization in deciding the priorities in vulnerability management with regards to the company’s situation. From this, a quicker response to vulnerabilities that should be managed with priority would be possible, and this could be used in inspecting security patches and security policies that adheres to the company’s situation.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.