Monthly Threat Actor Group Intelligence Report, June 2023 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 May 2023 to 20 June 2023.
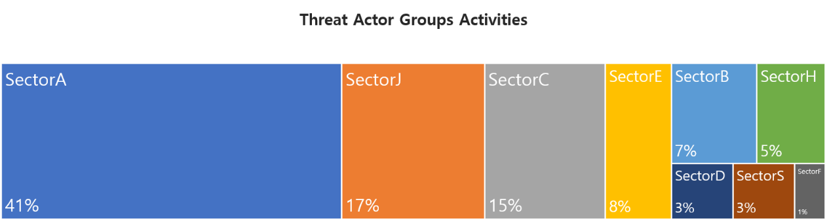
In June, activities by a total of 32 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 41%, followed by SectorJ groups.
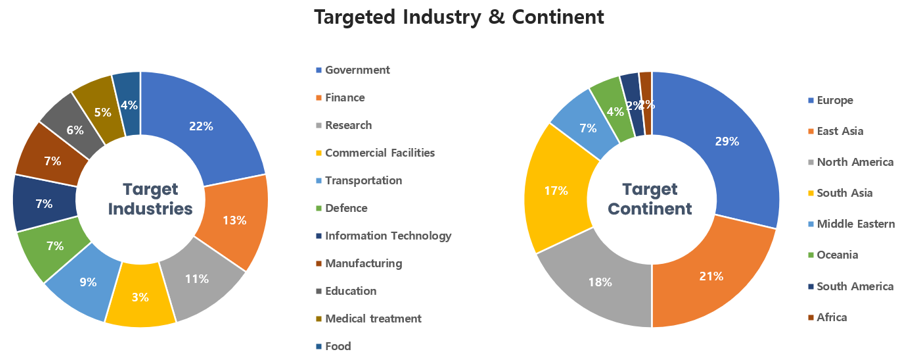
Threat Actors identified in June carried out the highest number of attacks on workers and systems in government agencies and commercial sectors. Regionally, Europe and East Asia were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In June 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06 and SectorA07 groups.
SectorA01 group was found to be active in South Korea. The group utilized remote code execution vulnerabilities in web security programs and corporate asset management software used in South Korea to download and execute malicious code on the targeted systems.
SectorA02 group was found to be active in South Korea, Australia, Cambodia, the United States, and the United Kingdom. The group employed malicious code in the form of Windows Shortcut (LNK) files, disguising them as documents requesting cooperation for a North Korean human rights film screening event.
SectorA05 group was found to be active in South Korea, Belgium, the United States, China, Japan, Ukraine, and the United Kingdom. The group sent phishing emails disguised as topics related to North Korean human rights organizations, attaching compressed files containing malicious code in Windows Help (CHM, Compiled HTML Help) file format. Ultimately, they utilized malicious code to leak various information from the targeted systems.
SectorA06 group was found to be active in United Arab Emirates, Australia, Israel, Swiss, Indonesia, India, the United States, Romania, China, Japan, Singapore, the United States and Italy. The group targeted macOS users by disguising malicious code as a PDF viewer. To deceive the victims, they used bait documents disguised as protected documents from Microsoft Azure.
SectorA07 group was found to be active in South Korea and Israel. The group distributed malicious code disguised as Windows shortcut (LNK) files in the form of a ZIP archive, masquerading as an emotional assessment cooperation guide. Ultimately, they employed Visual Basic Script and Batch script files to collect system information.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In June 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorB22, SectorB38, SectorB50, SectorB73 and SectorB75 groups.
SectorB22 group was found to be active in Latvia, Taiwan, Myanmar, Japan, turkey, Estonia, Greece, the United Kingdom, the United States, Finland, Germany, and Norway. The group targeted various organizations including governments, institutions, and the telecommunications industry, distributing spear phishing emails as part of their attack activities. Ultimately, they engaged in malicious actions such as system information gathering, command execution, and file deletion on the targeted systems.
SectorB38 group was found to be active in the United States, Italy, Canada, India, Australia, Singapore, France, Germany, and the United Kingdom. The group targeted various organizations including governments, institutions, foreign affairs departments, and financial entities, distributing spear phishing emails as part of their attack activities. On the targeted systems, they installed malicious code with downloader functionality, laying the groundwork for future attacks.
SectorB50 group was found to be active in the United Arab Emirates, the United States and Germany. The group distributed compressed files disguised as survey documents to carry out their attack activities. Ultimately, on the targeted systems, they engage in malicious activities according to the attacker’s commands.
SectorB73 group was found to be active in the United States. The group targeted critical infrastructure providers for their attack activities. They utilized various open-source tools and system commands to carry out information exfiltration.
SectorB75 group was found to be active in Latvia, Pakistan, China, Germany, Hong Kong and the United States. The group exploited a vulnerability (CVE-2023-2868) in the Barracuda Email Security Gateway Appliance to carry out their attack activities. They engaged in information exfiltration on the targeted systems.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In June 2023, activities by a total of 6 hacking groups were identified, and the groups were SectorC01, SectorC04, SectorC05, SectorC08, SectorC13 and SectorC14 groups.
SectorC01 group was found to be active in Ukraine. The group exploited vulnerabilities in webmail software to steal information from webmail servers. They manipulated sender and recipient email addresses, as well as pilfered user address books, in order to lay the groundwork for secondary attacks.
SectorC04 group utilized the DLL side-loading technique using a legitimately signed EXE file with a Microsoft certificate to execute malicious code. Ultimately, they employed a downloader malware with the capability to download and execute additional malicious code.
SectorC05 group was found to be active in Ukraine. The group exploited VPN accounts without multi-factor authentication (MFA) and used a batch script-formatted malicious code with the intention of system destruction to delete files within the system.
SectorC08 group was found to be active in the United States, Russia, the United Arab Emirates, Ukraine, Poland and South Korea. The group attempted lateral movement using removable media to reach systems isolated by an air gap. They generated malicious code in Windows shortcut (LNK) format to induce the target to execute, aiming at the systems of the targeted organization.
SectorC13 group was found to be active in the United States and Russia. The group utilized malicious code disguised as MS Word (Word) documents with instructions for evasive actions against shelling. If the target executes the MS Word (Word) malicious code, it triggers a template injection technique, downloading and executing an MS Word (Word) template containing malicious code.
SectorC14 group was found to be active in Ukraine. The group employed emails containing attached PDF files with links to phishing sites disguised as portal sites. The emails were designed to appear as portal site security alerts, enticing the target to execute the PDF file.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In June 2023, activities by a total of 2 hacking groups were identified, and the groups were SectorD01 and SectorD15 groups.
SectorD01 group was found to be active in Israel and Australia. The group targeted servers exposed to VPN vulnerabilities, utilizing web shells to access them. Ultimately, they distributed the Moneybird Ransomware to these compromised servers.
SectorD15 group was found to be active in Saudi Arabia, Israel and the United Kingdom. The group attempted watering hole attacks targeting transportation and logistics-related websites. The malicious code, inserted in the web pages in the form of JavaScript, collected information such as visitors’ operating system language, IP addresses, and screen resolutions.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In June 2023, activities by a total of 4 hacking groups were identified, and the groups were SectorE01, SectorE02, SectorE04, SectorE05 groups.
SectorE01 group was found to be active in the United Kingdom and Nepal. The group distributed malicious code disguised as VPN software to carry out their attack activities. Ultimately, they installed a downloader functionality as part of the malicious code to establish a foundation for future attacks.
SectorE02 group was found to be active in the United States and Pakistan. The group distributed malicious Android code disguised as chat and VPN apps to carry out their attack activities. Ultimately, they managed to steal sensitive information such as contacts and location data from the targeted devices.
SectorE04 group was found to be active in Pakistan and Denmark. The group distributed malicious activities disguised as MS Excel documents with titles like “Salary Increase List” and “Compromised Systems List”. Through this approach, they conducted their attack activities. Eventually, they managed to install malware to establish a foothold for future attacks.
SectorE05 group was found to be active in Pakistan. The group engaged in malicious activities by distributing a Windows Help file disguised as a development project evaluation. They used this deceptive tactic to carry out their attack operations. Ultimately, they succeeded in installing malware to establish a foundation for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorF Group Activities
In June 2023, activities by a total of 1 hacking groups were identified, and the groups were SectorF01 groups.
SectorF01 group was found to be active in Vietnam and Czechia. The group targeted the financial sector by distributing malicious code to carry out their attack activities. Ultimately, they executed various malicious actions on the targeted systems, including stealing system information, downloading and uploading files, and performing process injection.
Hacking activities of SectorF carry the aim of collecting advanced information on governmental activities of countries neighboring supported government, such as political, diplomatic, and military activities, and to steal information related to cutting-edge technology for economic development of their country.
7. Characteristics of SectorH Group Activities
In June 2023, activities by a total of 1 hacking groups were identified, and the groups were SectorH03 groups.
SectorH03 group was found to be active in Pakistan, India, China and Hong Kong. The group disguised their attack activities by distributing documents camouflaged as defense product export papers and security measure documents. Ultimately, they deployed the CrimsonRAT malware to infiltrate systems and carry out information theft operations.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
8. Characteristics of SectorS Group Activities
In June 2023, activities by a total of 1 hacking groups were identified, and the groups were SectorS01 groups.
SectorS01 group was found to be active in Canada, Columbia, Brazil, South Korea, France, Hong Kong and Spain. The group conducted their attack operations by distributing Adobe PDF documents disguised as “Embargo” requests. These documents were used as camouflage to carry out information theft activities.
Hacking activities of SectorS group activities to date is to collect advanced information on governmental activities of South American countries such as political, diplomatic, and military activities.
9. Characteristics of Cyber Crime Group Activities
In June 2023, activities by a total of 7 hacking groups were identified, and the groups were SectorJ04, SectorJ09, SectorJ20, SectorJ27, SectorJ39, SectorJ110 and SectorJ118.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ04 group was found to be active in the group’s activities were identified in the United States, United Kingdom, India, Italy, Canada, Ireland, and Singapore. This group distributed Cl0p Ransomware by targeting systems exposed to MOVEit Transfer vulnerabilities (CVE-2023-35708, CVE-2023-34362).
SectorJ09 group continues to maintain its traditional hacking approach by embedding obfuscated skimming scripts into websites. These scripts are designed to collect various user details such as usernames, addresses, emails, phone numbers, and credit card payment information from payment pages.
SectorJ20 group was found to be active in the United States. The group continues to employ traditional hacking methods by inserting obfuscated skimming scripts into websites. These scripts collect user information such as usernames, addresses, emails, phone numbers, and credit card payment details from payment pages.
SectorJ27 group was found to be active in Russia, China, Austria, Poland, Singapore, Moldova, Germany, Argentina, Bulgaria, Turkey, the United States, South Africa, Italy, Belarus, Taiwan, Malaysia, Algeria, Canada, Georgia, Ukraine and Switzerland. The group attached malicious MS Word (Word) documents to phishing emails impersonating an international transportation company. Ultimately, they aimed to install malicious code with remote control capabilities onto the targeted systems, enabling them to gather system information and attempt command and control actions.
SectorJ39 group was found to be active in Russia, Czechia, the United States, Ukraine and Australia. The group exploited Google Ads to display phishing sites at the top of search results, luring users to access them. Ultimately, they utilized malicious code capable of stealing system permissions and enabling command control.
SectorJ110 group was found to be active in Ukraine and Spain. The group distributed phishing emails disguised as invoices, attaching compressed files containing malicious JavaScript code. Ultimately, they used malicious code with the capability to download and execute additional malicious code.
SectorJ118 group was found to be active in the United States, Canada and Lithuania. The group exploited websites hosting illegal content for the distribution of malicious code. Ultimately, their malicious Chrome browser extension code collected sensitive information like browser search data and inserted arbitrary ads into the browser.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
