Monthly Threat Actor Group Intelligence Report, February 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 January 2024 to 20 February 2024.
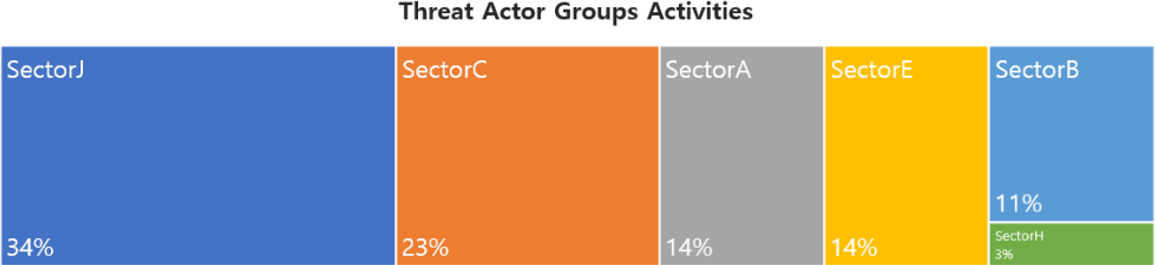
In February, activities by a total of 26 Threat Actor Groups were identified, in which activities by SectoJ groups were the most prominent by 34%, followed by SectorC and SectorA groups.
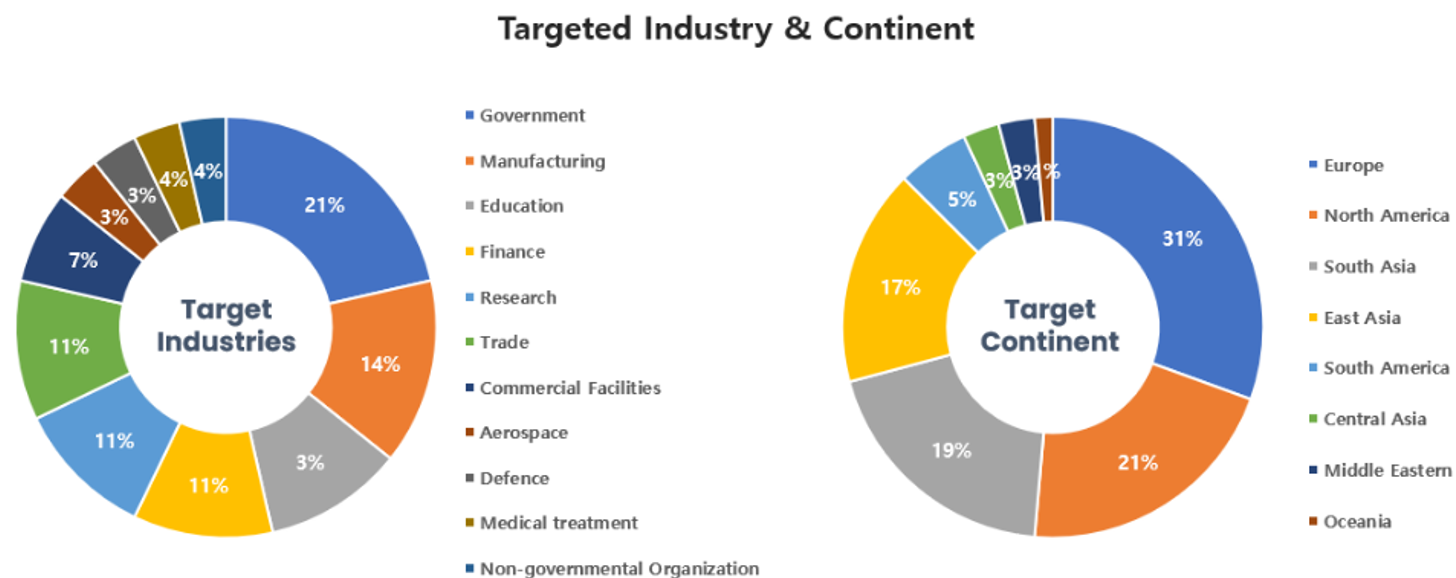
Threat Actors identified in February carried out the highest number of attacks on workers and systems in government agencies and manufacturing sectors. Regionally, Europe and North America were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In February 2024, activities by a total of 2 hacking groups were identified, and the groups were SectorA01 and SectorA05.
SectorA01 group was found to be active in Vietnam, Germany, and the United States. The group used malware in PE (Portable Executable) format disguised as open-source remote management and desktop software UltraVNC.
SectorA05 group was found to be active in Hungary, South Korea, Singapore, Pakistan, and Germany. The group used malware in the form of Windows shortcut (LNK) disguised as trading lecture materials and utilized Dropbox API. Ultimately, malware in Portable Executable (PE) format with capabilities such as Distributed Denial of Service (DDoS) attacks, keylogging, and remote control, and can perform various functions according to the commands from the attacker’s server was downloaded.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In February 2024, activities by a total of 4 hacking groups were identified, and the groups were SectorB22, SectorB86, SectorB87, and SectorB91.
SectorB22 group was found to be active in Mongolia, Czech Republic, Japan, Netherlands, Vietnam, Singapore, India, Malaysia, Taiwan, Russia, United States, China, France, and Hong Kong. The group distributed Windows shortcut (LNK) files disguised as flood alert documents in Mongolia and carried out attacks. The group downloaded and executed malware with remote control capabilities known as PlugX on the targeted systems and performed various malicious activities according to commands received from the C2 server.
SectorB86 group was found to be active in the United States, South Korea, and Germany. The group exploited vulnerabilities in Ivanti Connect Secure software and distributed malware based written in Rust to carry out their attacks. They also downloaded and executed a command-and-control framework known as Sliver through the Rust-based malware on the targeted systems, allowing them to carry out various attacks.
SectorB87 group was found to be active in the United Kingdom, China, and Japan. The group distributed malware through an Adversary-in-the-middle (AitM) attack that intercepted legitimate software update requests from individuals in the United Kingdom, China, and Japan. The group also carried out attacks through a backdoor malware on the targeted systems according to commands from the C2 server and acquired information on Tencent QQ messenger credentials, chat logs, and contact lists, as well as intercepting audio conversations.
SectorB91 group was found to be active in Japan, Taiwan, India, Iran, and the United States. The group targeted technology organizations and government agencies in East Asia, distributing malware. They exploited vulnerabilities in various products of the targeted systems and installed malware to collect system information, active directory information, and credentials according to commands received from the C2 server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In February 2024, activities by a total of 4 hacking groups were identified, and the groups were SectorC01, SectorC02, SectorC08, and SectorC13.
SectorC01 group was found to be active in Ukraine and Kazakhstan. The group used phishing site disguised as web portal and when the target entered account information to log in, they inadvertently leaked authentication data.
SectorC02 group was found to be active in Poland. The group targeted a non-governmental organization (NGO) supporting Ukraine and used malware to perform various functions according to the attacker’s server commands.
SectorC08 group was found to be active in Ukraine, Poland, Indonesia, and the United States. The group used malware disguised as MS Word documents related to budget support for the Ministry of National Defense.
SectorC13 group was found to be active in Belarus. The group used malware disguised as an engineering note in MS Word format to trick the target into directly executing the malware.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorE Group Activities
In February 2024, activities by a total of 5 hacking groups were identified, and the groups were SectorE01, SectorE02, SectorE04, SectorE05, and SectorE08.
SectorE01 group was found to be active in United States, Netherlands, India, and Pakistan. The group distributed Android malware disguised as news or messaging apps to carry out their attacks. They collected contact lists, SMS messages, call logs, device location, installed app lists, and files with specific extensions from the targeted devices and sent them to a C2 server.
SectorE02 group was found to be active in India. The group distributed Android malware disguised as a chat app and carried out attack activities. The group collected contact lists, SMS messages, camera recordings, location information, and system information from targeted devices and sent them to a C2 server.
SectorE04 group was found to be active in Nepal. The group distributed MS Word documents disguised as Ministry of Foreign Affairs Nepal documents and carried out attack activities. Additional malware was downloaded on the target system to lay the groundwork for future attacks.
SectorE05 group was found to be active in Pakistan and Taiwan. The group distributed Windows Help (CHM) files to carry out their attacks. Usernames and computer names from the targeted systems was sent to a C2 server, and subsequently downloaded and executed additional malware to lay the groundwork for future attacks.
SectorE08 group was found to be active in Pakistan. The group distributed and executed various malware for their attacks, including malwares with the function of collecting host names and usernames from targeted systems, or stealing Chrome browser passwords.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
5. Characteristics of SectorH Group Activities
In February 2024, activities by a total of 1 hacking groups were identified, and the groups was SectorH03.
SectorH03 group was found to be active in the United States. The group distributed malware disguised as a chat app for Android and carried out attack activities. The group collected SMS messages, call logs, voice recordings, device location, and system information from the targeted devices, saved them as JSON files, and then sent them to a C2 server.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
6. Characteristics of Cyber Crime Group Activities
In February 2024, activities by a total of 10 hacking groups were identified, and the groups were SectorJ20, SectorJ21, SectorJ72, SectorJ94, SectorJ111, SectorJ113, SectorJ132, SectorJ145, SectorJ146, and SectorJ149.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ20 group distributed malware disguised as illegal replication programs to unspecified multiple users who were using illegal file sharing sites and induced the users to directly execute installation programs containing malware.
SectorJ21 group was found to be active in the United States, Hong Kong, Germany, New Zealand, Russia, Australia, Singapore, and Canada. The group disguised a SVG (Scalable Vector Graphics) format file as a corporate proposal and attached it to a phishing mail, inducing the target’s execution. They also distributed malware in PE (Portable Executable) format through a phishing site URL using Google’s AMP (Accelerated Mobile Pages) service.
SectorJ72 group was found to be active in Poland, Vietnam, and Germany. The group used the URL of Discord, a voice and chat channel service, to distribute malware and induced the attack target to download and install the compressed file containing the malware by uploading it to the Discord channel and sharing the link.
SectorJ94 group was found to be active in Germany, Switzerland, Italy, India, Belgium, South Korea, and the United States. The group delivered compressed MS Excel files containing malicious links to their targets, and ultimately used a backdoor malware with the ability to download and execute additional malware according to the attacker’s commands.
SectorJ111 group was found to be active in France, Portugal, Russia, Hong Kong, Brazil, Ukraine, the United States, and Reunion. The group used the Amadey Botnet to collect system information and sent it to attacker’s servers and performed various functions according to the attacker’s commands.
SectorJ113 group was found to be active in Poland and Japan. The group used Babuk Ransomware to secure financial resources and employed a double extortion attack, threatening to release leaked data in order to increase the likelihood of the attack targets paying the file decryption cost.
SectorJ132 group was found to be active in Poland, the United States, Brazil, Germany, India, Spain, the Philippines, Israel, the United Kingdom, and Russia. The group accessed their targets through foreign exchange forums or Telegram channels, and ultimately downloaded and executed malware in PE (Portable Executable) format with remote control capabilities by exploiting malicious links based on WebDAV (Web Distributed Authoring and Versioning) and a bypass vulnerability (CVE-2024-21412) in Windows Defender SmartScreen.
SectorJ145 group was found to be active in the United States. The group targeted remotely accessible Microsoft SQL servers and carried out attacks using various open-source tools.
SectorJ146 group was found to be active in Finland, Uzbekistan, Germany, Russia, Brazil, and the United States. The group attached compressed files containing malware disguised as prosecution investigation materials to phishing emails, inducing the target to execute them and ultimately collected authentication information stored in encrypted wallets and system for financial gain.
SectorJ149 group was found to be active in Ukraine. The group utilized phishing emails containing information on civilian evacuation plans, and ultimately utilized a commercial remote access program, RemoteUtilities to carry out their attacks.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
