2023 Activities Summary of SectorA groups (ENG)
Activity of SectorA Group
Threat Research Lab classifies SectorA groups into 7 subgroups. These groups aim to collect advanced information related to the government activities such as politics and diplomatic activities from the South Korean government, and at the same time, carry out hacking activities worldwide to secure financial resources.
Analysis of activities by SectorA groups in 2023 shows that activities by SectorA05 group was the most prominent, followed by SectorA02 group and SectorA01 group.
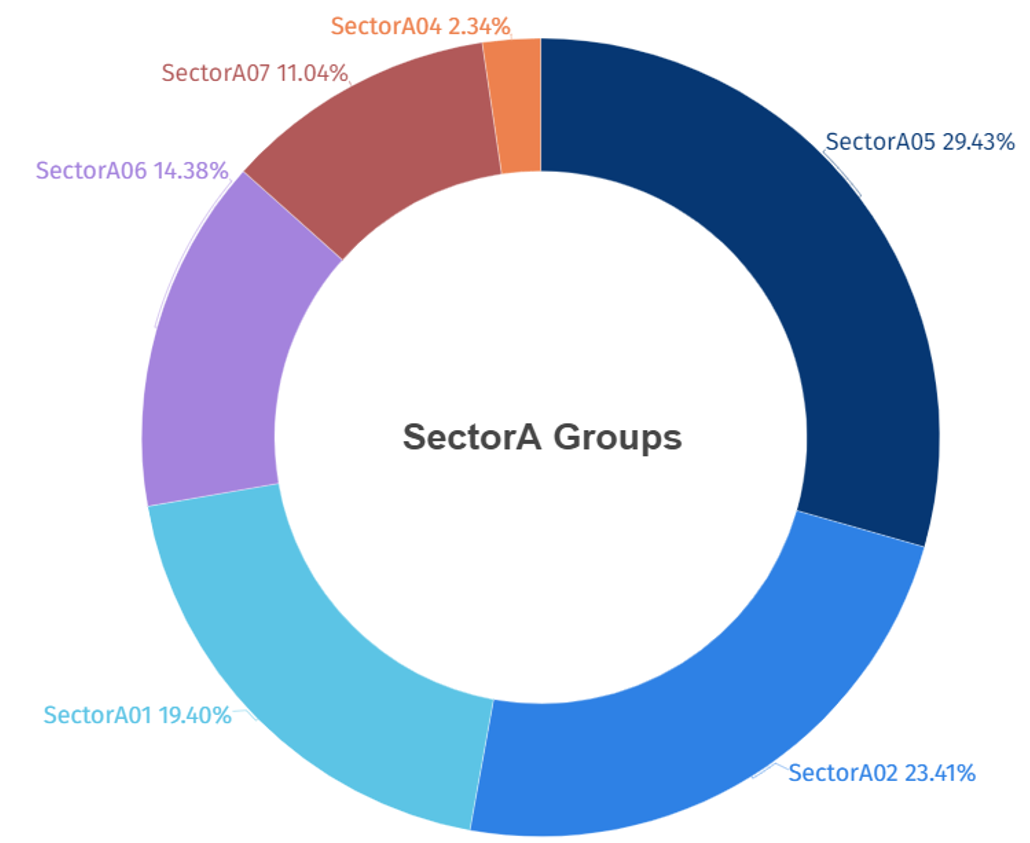
[Figure 1: Statistics of activities of SectorA groups identified in 2023]
SectorA hacking groups identified in 2023 carried out the highest number of attacks on workers and systems in financial industries, followed by research and government institutions.
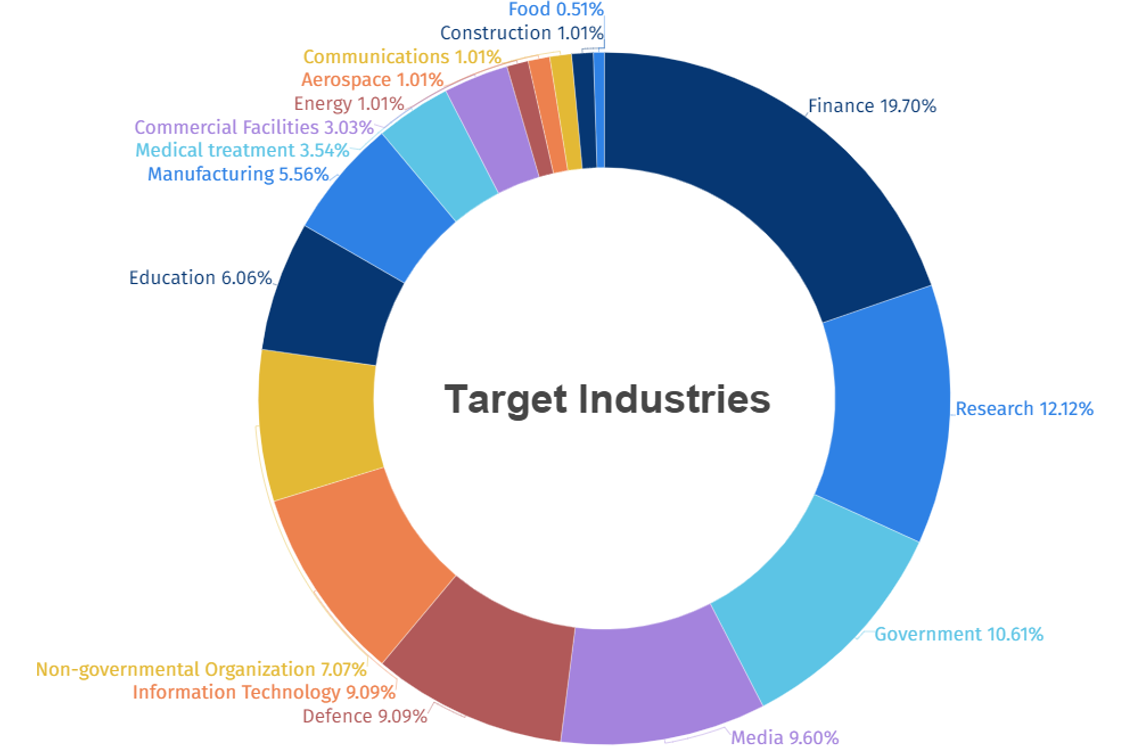
[Figure 2: Statistics of Industries Targeted in 2023]
The following map illustrates the countries targeted by SectorA groups in 2023, with darker shades of red indicating higher frequencies of attacks. This shows that SectorA Group conducted the most hacking activities against South Korea, followed by the United States, India, Japan, and the United Kingdom.
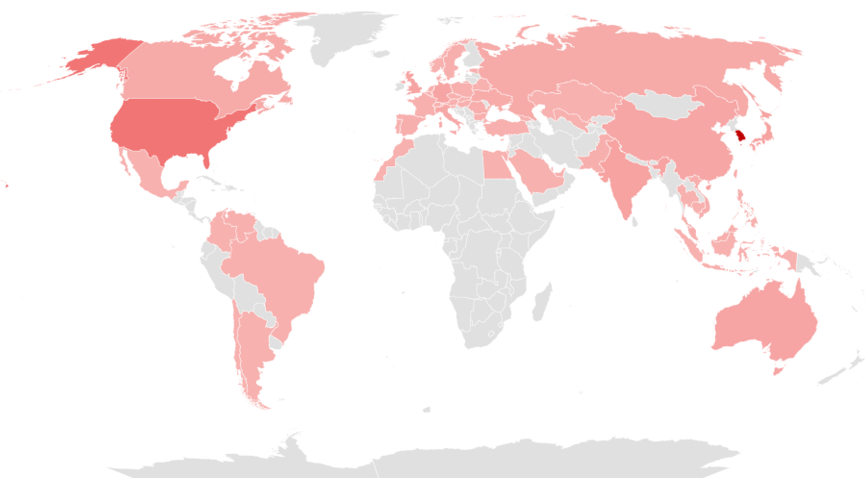
[Figure 3: Countries Targeted by SectorA Groups in 2023]
INITIAL ACCESS ROUTE of SectorA Group
Among the initial access routes used by SectorA groups, distributing spear phishing links was found to be the primary access route used in 2023. Spear phishing attacks are social engineering attacks targeting specific individuals or organizations. Through malicious links, attackers induce targets to input their credentials or execute malware.
The groups disguise themselves as trusted contacts or credible individuals to induce the target to execute malicious links or attachments, making spear phishing the most commonly utilized method with its high likelihood of successful initial access.
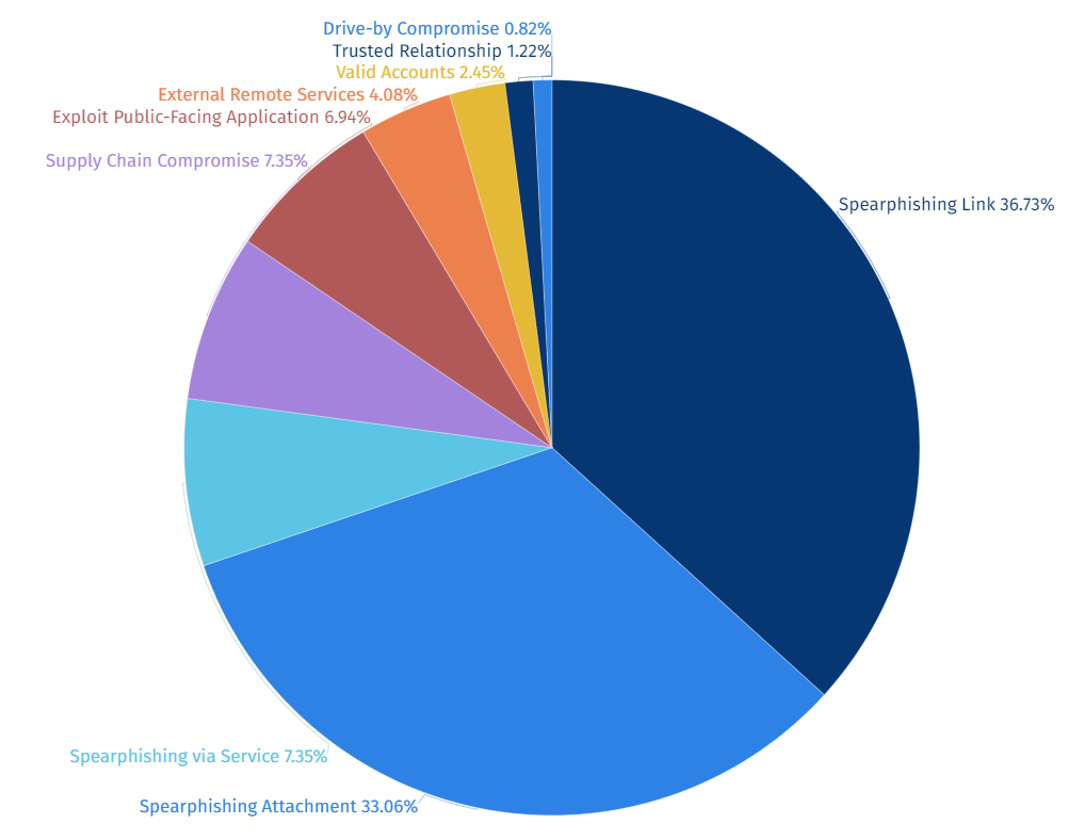
[Figure 4: Statistics of Initial Access Routes used by SectorA Groups]
Vulnerabilities Exploited by SectorA Group
Among the top 5 vulnerabilities exploited by SectorA groups, CVE-2023-29059 (Malware vulnerability embedded in 3CX Desktop App) was most prominently exploited in 2023. SectorA group was seen to have exploited the CVE-2023-29059 vulnerability to distribute and execute malware on the targeted system.
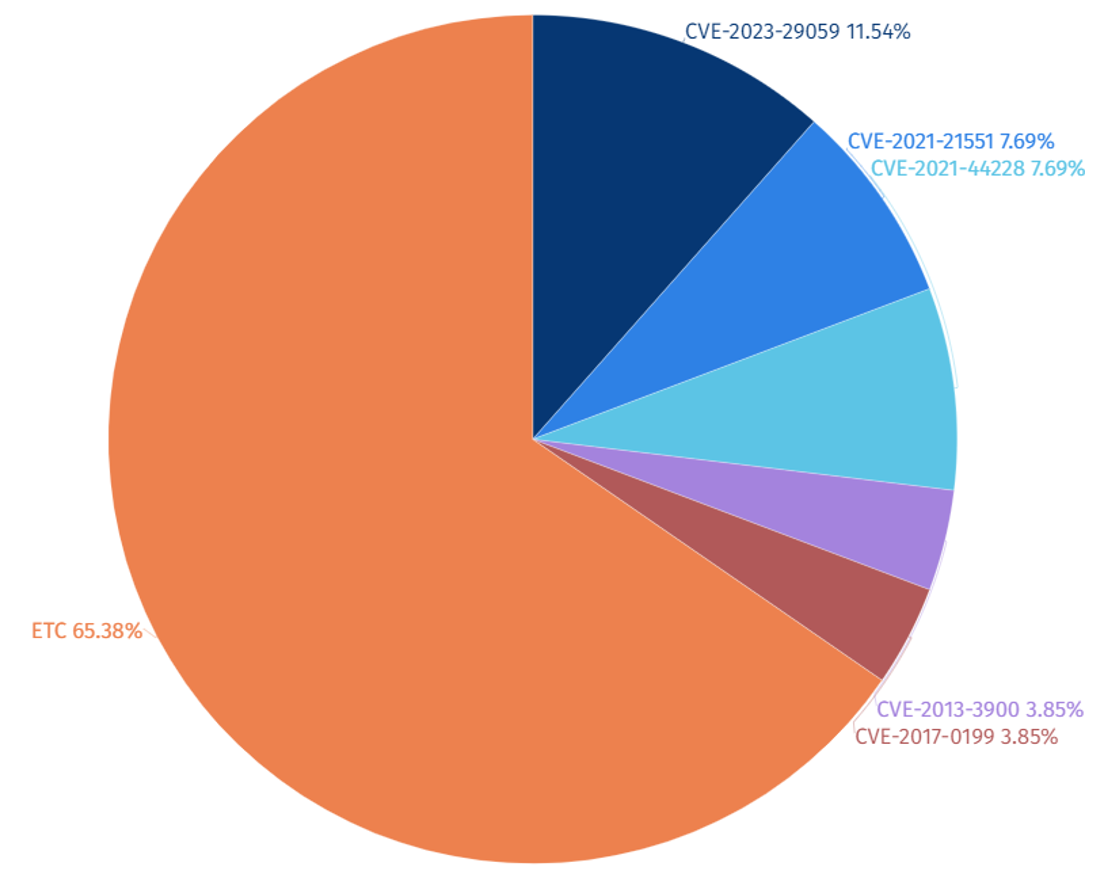
[Figure 5: Statistics of Top 5 Vulnerabilities Exploited by SectorA Group in 2023]
|
Vulnerability |
Classification |
Target System |
|
CVE-2023-29059 |
Embedded Malicious Code |
3CX DesktopApp |
|
CVE-2021-21551 |
Insufficient Access Control Vulnerability |
Dell dbutil Driver |
|
CVE-2021-44228 |
Remote Code Execution Vulnerability |
Apache Log4j2 |
|
CVE-2013-3900 |
Remote Code Execution |
Microsoft WinVerifyTrust function |
|
CVE-2017-0199 |
Remote Code Execution Vulnerability |
Microsoft Office and WordPad |
[Table 1: Top 5 Vulnerabilities Exploited by SectorA Group in 2023]
SectorA Attack Target Systems Statistics
Software vulnerabilities are typically categorized into server and client types. Hacking groups, strategically positioned at the heart of networks, exploit vulnerabilities within server systems to facilitate further attacks on internal networks.
Among the top 5 attack target systems by SectorA groups, the greatest number of attacks were carried out on 3CX Desktop App, video conference software.
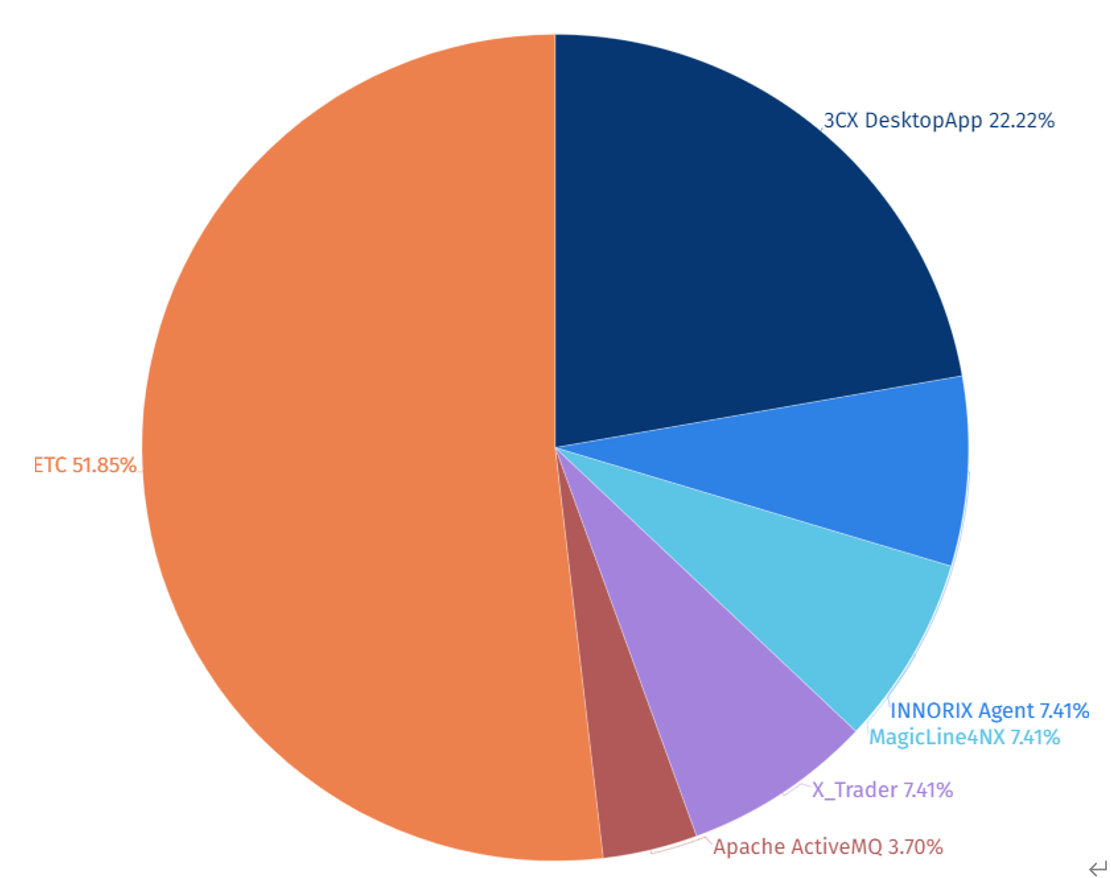
[Figure 6: Statistics of Top 5 Attack Target Systems by SectorA Group in 2023]
Open Source and Freeware Tools Utilized by SectorA Group
Among the top 5 open source and freeware tools utilized by SectorA groups, the Microsoft cloud storage service “OneDrive” was identified as the most frequently used tool in 2023.
SectorA group exploited OneDrive as a C2 server to download and execute additional malware on the targeted system. Cloud storage services often used in business purposes, such as OneDrive, can avoid detection by security solutions as they are passed as regular traffic. It is analyzed that SectorA group utilized OneDrive as the C2 server due to this characteristic.
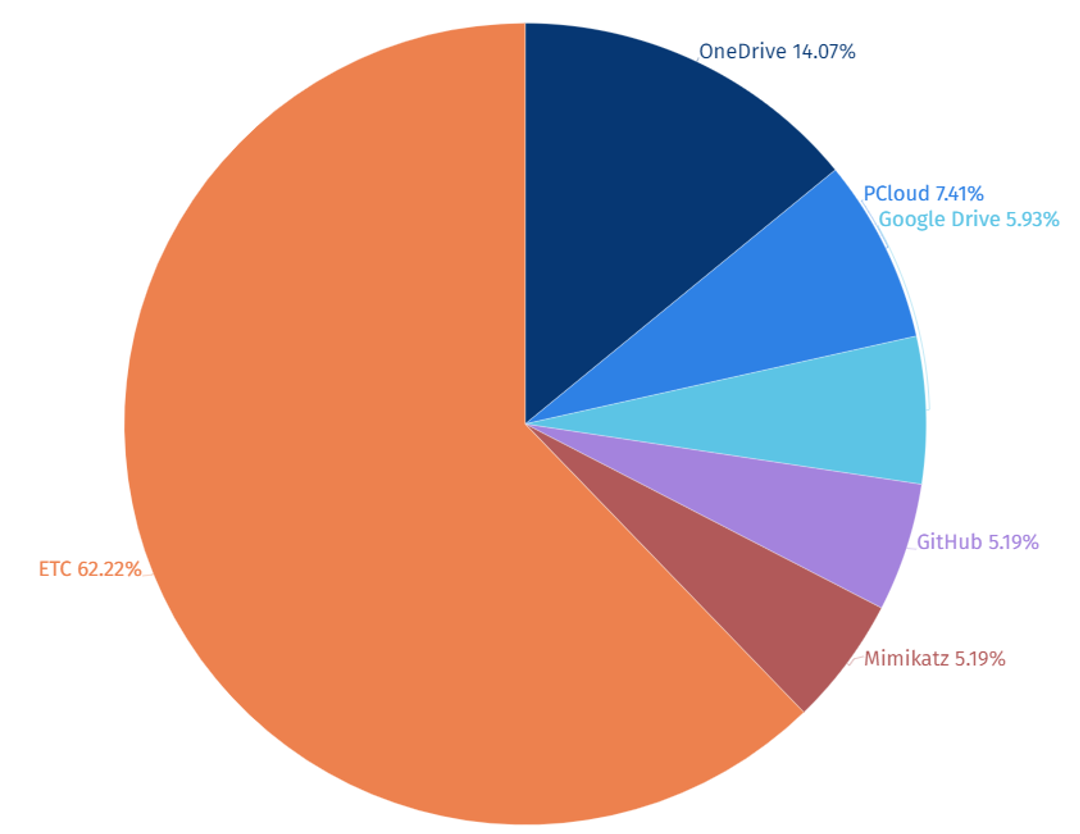
[Figure 7: Statistics of Top 5 Open Source and Freeware Tool used by SectorA Group in 2023]
|
Tool Name |
Function |
|
OneDrive |
Cloud Storage |
|
PCloud |
Cloud Storage |
|
Google Drive |
Cloud Storage |
|
GitHub |
Software management platform |
|
Mimikatz |
Windows Credential Information Collection Tool |
[Table 2: Top 5 Open Source and Freeware Tool used by SectorA Group in 2023]
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
