Monthly Threat Actor Group Intelligence Report, April 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 March 2024 to 20 April 2024.
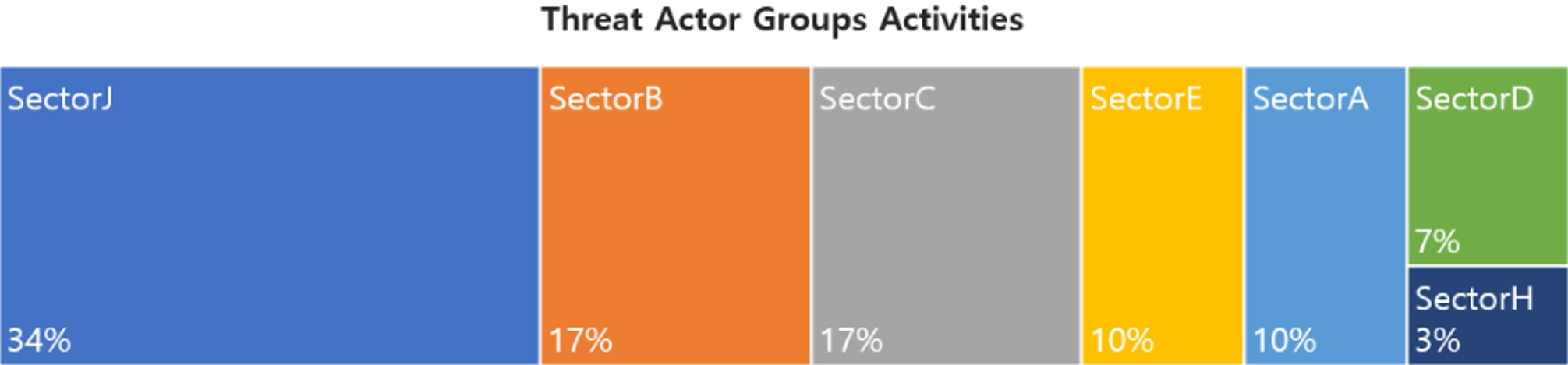
In April, activities by a total of 29 Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 34%, followed by SectorB and SectorC groups.
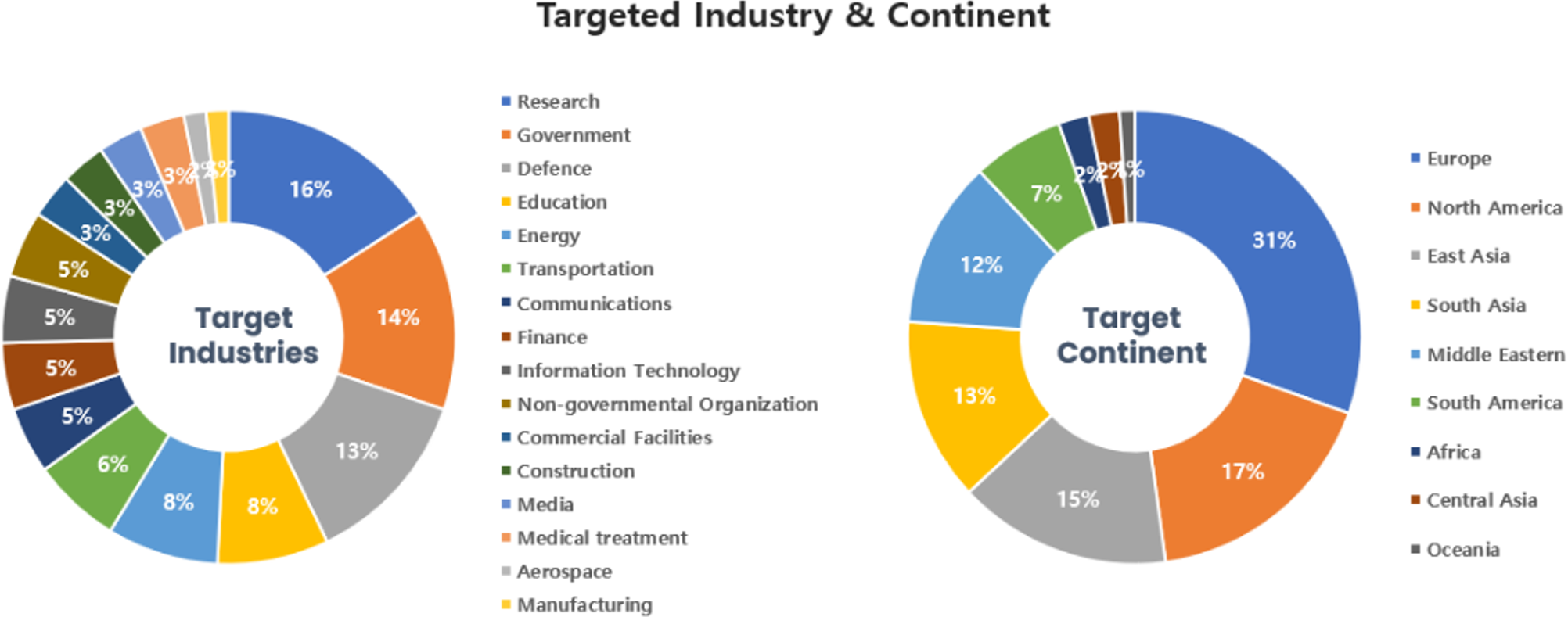
Threat Actors identified in April carried out the highest number of attacks on workers and systems in government agencies and research institutions. Regionally, Europe and North America were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In April 2024, activities by a total of 3 hacking groups were identified, and the groups were SectorA01, SectorA05 and SectorA07 groups.
SectorA01 group was found to be active in India, Bangladesh, Singapore, and Hungary. This group used malicious Windows shortcut (LNK) files disguised as job descriptions to entice individuals interested in job opportunities to execute the malware. The primary functions of the final executed malware are to transmit system information, ensure persistence through registry entries, and execute malicious code delivered by the attacker on the target system.
SectorA05 group was found to be active in South Korea. The group used malware disguised as a meeting agenda in the form of a Windows shortcut (LNK) file, and downloaded additional malware through the Dropbox API.
SectorA07 group was found to be active in South Korea. The group used malware in the form of Windows shortcut (LNK) files disguised as internal trends related documents in North Korea. If the target executed the malware, it would download and execute additional malware created with AutoIt script to carry out malicious activities.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In April, activities by a total of 5 hacking groups were identified, and the groups were SectorB09, SectorB22, SectorB94, SectorB96 and SectorB97 groups.
SectorB09 group was found to be active in Taiwan. The group distributed malware with loader functions targeting organizations in government, technology, and research sectors. Once the malware was executed on the target system, it performed various malicious activities according to commands received from the C2 server through the remote control functionality of the malware.
SectorB22 group was found to be active in Mongolia, the United States, and Germany. The group conducted attack activities by distributing compressed files containing remote control malware known as PlugX. When executed on the target system, the remote control malware carried out various malicious activities according to commands received from the C2 server. Additionally, the group exploited vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure solutions to gain initial access rights, after which they distributed malware to carry out attack activities. The malware executed on the target system performed various malicious activities based on commands received from the C2 server.
SectorB94 group was found to be active in Canada, Taiwan, Russia, Malaysia, Hong Kong, the United States, China, and the United Kingdom. The group targeted government agencies, research and educational institutions, and nongovernmental organizations (NGOs), exploiting various vulnerabilities to gain initial access rights. After gaining access, they distributed malware to carry out their attack activities. The reverse shell backdoor executed on the target system performed various malicious activities according to commands received from the C2 server.
SectorB96 group was found to be active in Canada, the United States, and Germany. The group exploited vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure solutions to distribute malware for their attack activities. The malware, including Sliver, a penetration testing tool developed in Go language, and backdoor functionalities, executed on the target system, carried out various malicious activities based on commands received from the C2 server.
SectorB97 group was found to be active in Italy. The group exploited vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure solutions to distribute malware for their attack activities. The backdoor malware executed on the target system set up a Secure Shell (SSH) server and performed various malicious activities based on commands received from the C2 server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In April, activities by a total of 5 hacking groups were identified, and the groups were SectorC01, SectorC04, SectorC05, SectorC08, and SectorC13 groups.
SectorC01 group used iOS malware to collect data and perform remote control on iOS devices.
SectorC04 group was found to be active in Ukraine, Germany, the Czech Republic, India, Italy, Latvia, Peru, and Denmark. This group used Adobe PDF documents disguised as dinner invitations from Germany’s major political party, the Christian Democratic Union (Christlich Demokratische Union, CDU), and ultimately used malware that performed information collection and remote control functions.
SectorC05 group was found to be active in Ukraine, France, South Korea, the United Kingdom, and the United States. This group used ELF malware with the purpose of causing disruption to national infrastructure systems.
SectorC08 group was found to be active in Poland and Ukraine. This group used MS Word documents disguised as documents related to the police department to entice the target to execute the malware directly.
SectorC13 group was found to be active in Ukraine, Russia, and Belarus. This group used MS Word documents disguised as government-related documents to entice the target to execute the malware directly.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In April 2024, activities by a total of 2 hacking groups were identified, and the groups were SectorD02 and SectorD12 groups.
SectorD02 group was found to be active in Israel, Romania, Turkey, and Canada. This group used phishing emails containing links disguised as webinar invitation documents and ultimately attempted to remotely control the target system through the remote control tool Atera.
SectorD12 group was found to be active in the United States. This group conducted phishing attacks targeting job seekers in the aerospace and defense industries and enticed the target to execute malware disguised as human resources management software.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In April 2024, activities by a total of 3 hacking groups were identified, and the groups were SectorE01, SectorE02, and SectorE04 groups.
SectorE01 group was found to be active in the United States. This group distributed RAR compressed files containing Windows shortcut (LNK) files disguised as the Koran, the holy book of Islam, to conduct their attack activities. The malware, written in Go language and executed on the target system, performed various malicious activities such as system information theft and screen capture based on commands received from the C2 server.
SectorE02 group was found to be active in Turkey and Pakistan. This group distributed MS Word documents disguised as special regulations to conduct their attack activities. The malicious DLL file executed on the target system downloaded and executed additional malware, laying the groundwork for future attacks.
SectorE04 group was found to be active in Sri Lanka, the United Kingdom, Pakistan, the United States, Iran, and the United Arab Emirates. This group sent spear-phishing emails to the Sri Lankan Ministry of Defense, guiding the recipients to download and execute MS Word documents disguised as a decentralized budget program form. The malicious Word document executed on the target system downloaded and executed a remote template document file, laying the groundwork for future attacks. Additionally, the group distributed Windows disk image (ISO) files containing malware disguised as the Intel Wireless Display program. The malicious DLL file executed on the target system collected the computer name, user’s personal folder path, and C drive volume serial number, transmitted this information to the C2 server, and performed various malicious activities based on commands received from the C2 server.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In April 2024, activities by a total of 1 hacking groups were identified, and the groups was SectorH03 group.
SectorH03 group was found to be active in the United Arab Emirates and India. This group distributed RAR executable compressed files containing documents disguised as resumes to conduct their attack activities. The malicious EXE file executed on the target system downloaded and executed additional malware from the C2 server, laying the groundwork for future attacks. Additionally, this group distributed RAR compressed files disguised as analysis-based cards to conduct their attack activities. The CrimsonRAT remote control malware executed on the target system performed various malicious activities based on commands received from the C2 server.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of Cyber Crime Group Activities
In April 2024, activities by a total of 10 hacking groups were identified, and the groups were SectorJ09, SectorJ16, SectorJ61, SectorJ72, SectorJ94, SectorJ149, SectorJ160, SectorJ172, SectorJ174, and SectorJ175 groups.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ09 group inserted obfuscated skimming scripts into websites to collect information such as usernames and credit card details from payment pages.
SectorJ16 group was found to be active in Germany, the United States, Switzerland, and Austria. This group sent invoice-related phishing emails disguised as retail companies. When the target executed the Windows shortcut (LNK) file, a PowerShell command that downloads stealer malware was executed. They stole data from the target system through the stealer malware and transmitted it to the C2 server.
SectorJ61 group was found to be active in Guatemala, Greece, the Netherlands, Taiwan, the Dominican Republic, Germany, Lithuania, Latvia, Russia, Romania, Macedonia, Mexico, Morocco, the United States, Vietnam, Bulgaria, Brazil, Cyprus, Serbia, Sweden, Switzerland, Spain, Slovakia, Singapore, Argentina, Ireland, Ecuador, the United Kingdom, Jordan, Uruguay, Ukraine, Italy, India, Indonesia, China, the Czech Republic, Chile, Kazakhstan, Canada, Costa Rica, Colombia, Kyrgyzstan, Thailand, Turkey, Pakistan, Peru, Poland, France, and South Korea. This group distributed phishing emails with malicious RTF documents disguised as quotations. The documents contained malicious macros, and when the target opened the document, a remote access tool (RAT) was downloaded from an external server. The stolen data was transmitted to the C2 server via the FTP protocol.
SectorJ72 group was found to be active in the United States, Ecuador, and South Korea. This group executed Windows Installer (msiexec) through Windows shortcut (LNK) files. When the target executed the LNK file, the information from the target system was transmitted to the C2 server.
SectorJ94 group was found to be active in Germany, the United States, Austria, Italy, Canada, France, and Hong Kong. This group distributed MS Excel files via phishing emails, enticing targets to click on hyperlinks that download malicious JavaScript. This JavaScript subsequently downloaded and executed a stealer DLL file disguised as an image file, and transmitted the collected data from the target system to the C2 server.
SectorJ149 group was found to be active in Russia, Slovakia, and Ukraine. This group utilized Windows shortcut (LNK) files. When the target executed the LNK file, a PowerShell command was executed to download an executable file from a download server. The downloaded executable was an open-source-based Remote Access Tool (RAT), which the group intended to use for malicious activities such as keylogging, screen capturing, and clipboard data collection, based on commands received from the C2 server.
SectorJ160 group sold phishing kits based on Adversary-in-The-Middle (AiTM) techniques. These phishing kits operated by attaching URLs or QR codes in email bodies or attachments that redirected to phishing pages. To protect against bot traffic detection, the group used Cloudflare Captcha pages. Once the target passed the captcha authentication, they were redirected to a phishing page disguised as a Microsoft authentication page, where the email addresses, passwords, and two-factor authentication (2FA) codes entered by the targets were transmitted to the C2 server.
SectorJ172 group was found to be active in the Netherlands, the United States, Bangladesh, Vietnam, Spain, India, Indonesia, China, Pakistan, and South Korea. This group used Windows shortcut (LNK) files to steal social network account credentials. When the target executed the LNK file, a PowerShell command was executed to download a malicious HTML application (HTA) file from an external server. The downloaded malware further downloaded and executed a PE-formatted malware disguised as Windows Print Spooler (Spoolsv.exe). The executed malware transmitted the stolen data from the target system to Telegram.
SectorJ174 group used Ghost Locker Ransomware to secure monetary gains, transmitting the information from the infected systems to the C2 server.
SectorJ175 group was found to be active in Russia, the United States, Armenia, Ecuador, and South Korea. This group used Dragonforce Ransomware to secure monetary gains, leaving a ransom note on the infected systems with contact information via email and Tox.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
