Monthly Threat Actor Group Intelligence Report, May 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 April 2024 to 20 May 2024.
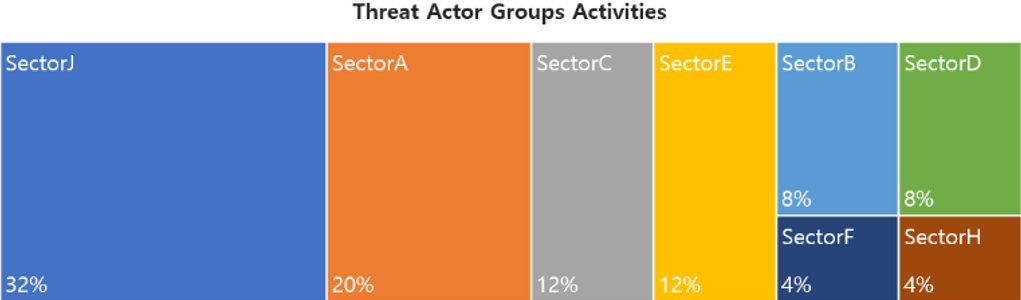
In May, activities by a total of 25 Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 32%, followed by SectorA and SectorC groups.
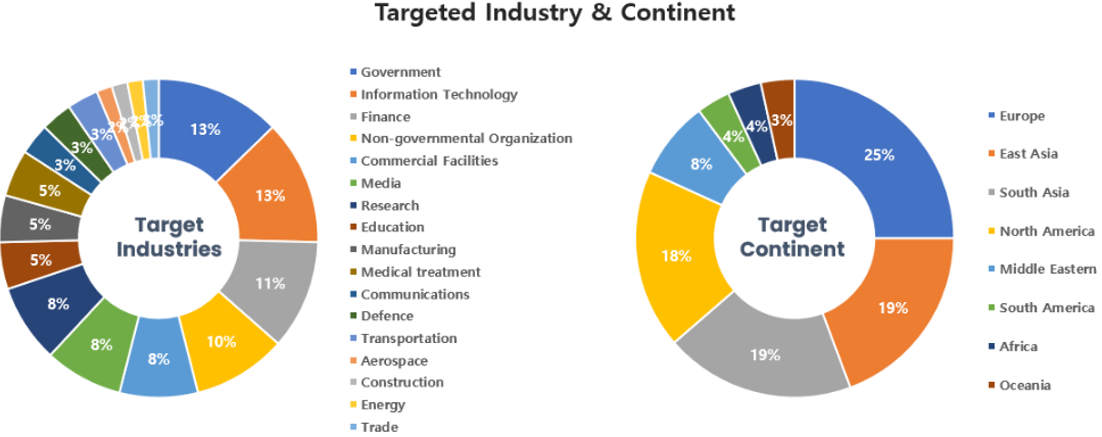
Threat Actors identified in May carried out the highest number of attacks on workers and systems in government agencies and the IT industry. Regionally, Europe and East Asia were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In May 2024, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA04, SectorA05 and SectorA07 groups.
SectorA01 group was found to be active in the United States, Poland, South Korea, the Philippines, Brazil, Russia, Germany, Ukraine, Turkey, Romania, Azerbaijan, Argentina, Armenia, the United Kingdom, Japan, France, Canada, Italy, Bangladesh, Pakistan, Morocco, and Singapore. The group disguised themselves as hiring managers on job posting platforms such as LinkedIn, to target on software developers and IT engineers and deliver malicious scripts. The compressed files disguised under filenames on recruitment test and source code review tests contained a malicious script that collected keyboard input data and system information.
SectorA02 group was found to be active in South Korea. The group used a Windows shortcut (LNK) file disguised as a visitor log to carry out their attacks. The malware installed in the target’s system carried out various malicious activities such as system information collection and CMD command execution, according to commands received from the C2 server.
SectorA04 group was found to be active in South Korea. The group targeted on manufacturing, construction and educational institutions to deliver compressed files containing malware disguised as the OpenVPN Client. Through the malware installed, various malicious activities were carried out according to the command received from the C2 server.
SectorA05 group was found to be active in South Korea, India, Switzerland, the United States, and Japan. The group sent out phishing emails through a web server. The phishing email led the targets to access a phishing website disguised as the login page on Naver, a South Korean portal website, in order to steal their Naver email account credentials. In addition, the group used the aforementioned web server to disseminate Xeno RAT, a remote access malware generated from an Open-source project. Through the malware installed, various malicious activities were carried out according to the command received from the C2 server.
SectorA07 group was found to be active in South Korea. The group distributed Windows shortcut (LNK) files disguised as supporting documents, and carried out malicious activities through the AutoItScript installed in the target’s system.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In May, activities by a total of 2 hacking groups were identified, and the groups were SectorB86 and SectorB98 groups.
SectorB86 group exploited the Remote Code Execution (RCE) vulnerability of the VMWare vCenter server (CVE-2021-21972) to obtain initial access authorizations and disseminate ransomware.
SectorB93 group exploited the Great Firewall (GFW) of China to return modified data containing incorrect MX record, in order to conceal their intentions and objectives behind their attack activities.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In May, activities by a total of 3 hacking groups were identified, and the groups were SectorC01, SectorC02, and SectorC08 groups.
SectorC01 group was found to be active in Germany, the United States, Belarus, Ukraine, China, Czech Republic, and Poland. The group disseminated compressed files containing malwares through phishing emails. When the target executed the executable within the compressed file, a DLL file that loaded a hidden Batch Script File (BAT) was executed through the DLL side-loading technique. This batch script file ultimately downloads and executes an additional batch script file that sends system information to the C2 server.
SectorC02 group was found to be active in Slovakia. The group targeted on the Ministry of Foreign Affairs to disseminate a backdoor malware through MS Word documents inserted with malicious macros, which was delivered through a phishing email. The backdoor downloaded through the VBA script in the Word document was found to communicate with the C2 server using the Outlook Messaging API (MAPI).
SectorC08 group was found to be active in Ukraine. The group distributed MS Word documents disguised as content related to the Ukrainian national regulatory service. When the target executed the Word document, it installed an additional malware through a downloaded external template file, laying the groundwork for future attacks.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In May 2024, activities by a total of 2 hacking groups were identified, and the groups were SectorD02 and SectorD30 groups.
SectorD02 group was found to be active in the United States, Singapore, Israel, Egypt, Italy, India, and Turkey. The group led their targets to download compressed files from Egnyte, a file sharing website, through a phishing email. The email, disguised as content related to the Golan Heights Council in the Middle East, was used to lead targets into downloading Atera, one of the remote monitoring and management tools.
SectorD30 group was found to be active in the United States, the United Kingdom, Ukraine, Israel, and Australia. The group disseminated a Visual Basic Script (VBS) that could download additional malware in the targeted systems. When the target executed the VBS file, a bait Adobe PDF file on gender equality and a Window PE format malware was downloaded.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In May 2024, activities by a total of 3 hacking groups were identified, and the groups were SectorE02, SectorE04, and SectorE05 groups.
SectorE02 group was found to be active in in Pakistan, India, Portugal, Germany, Nigeria, Netherlands, Canada, Turkey, Moldova, Poland, Philippines, Hong Kong, and Iran. The group distributed an Android malware disguised as a chat application to carry out their attacks. The malware installed in the victims’ devices collected sensitive data such as contacts, messages, phone call history, device location, list of installed apps, and files of a specific extension, sending them to the C2 server.
SectorE04 group was found to be active in Pakistan, China, United Arab Emirates, and India. The group distributed MS Excel documents containing lists or data related to the recently updated Battlefield Management and Analysis Center (BMAC). Through the installed malware, various malicious activities were carried out based on the command received from the C2 server.
SectorE05 group was found to be active in Netherlands, Pakistan, and Japan. The group distributed compressed files containing malware disguised as meeting minutes to carry out their attacks. Through the installed malware on the targeted systems, they sent computer names and usernames to a C2 server and downloaded and executed additional malware to prepare for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorF Group Activities
In May 2024, activities by a total of 1 hacking groups were identified, and the groups was SectorF01.
SectorF01 group was found to be active in China, the United States, Japan, and Singapore. The group distributed a file packaged as a NSIS (Nullsoft Scriptable Install System), which contained a remote access malware written in Rust language. Through the malware installed on the target system, they performed various malicious actions according to commands received from the C2 server.
Hacking activities of SectorF carry the aim of collecting advanced information on governmental activities of countries neighboring supported government, such as political, diplomatic, and military activities, and to steal information related to cutting-edge technology for economic development of their country.
7. Characteristics of SectorH Group Activities
In May 2024, activities by a total of 1 hacking groups were identified, and the groups was SectorH03 group.
SectorH03 group was found to be active in Australia, Germany, and India. The group targeted on the Indian government to distribute MS Excel documents with filename containing the term DGMS, an abbreviation for Director General of Mines Safety. Through the CrimsonRAT remote access malware installed in the targeted systems, various malicious activities were carried out depending on the command received from the C2 server.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
8. Characteristics of Cyber Crime Group Activities
In May 2024, activities by a total of 8 hacking groups were identified, and the groups were SectorJ01, SectorJ06, SectorJ61, SectorJ85, SectorJ146, SectorJ152, SectorJ172, and SectorJ177 groups.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ01 group was found to be active in the United States. The group used a phishing website impersonating the official webpage of a commercial program often used by the general audience to disseminate MSIX files. When the target executed the MSIX file, the PowerShell script within was executed, ultimately downloading and executing a NetSupport RAT. The group was seen to be intending to remotely control target systems through the NetSupport RAT.
SectorJ06 group was found to be active in Belgium, Switzerland, Spain, UK, Ukraine, Italy, Korea, Australia, and Hungary. The group distributed Black Basta Ransomware using spear phishing and vulnerabilities. They stole original data through Rclone, a cloud storage file transfer program.
SectorJ61 group distributed MS Word documents that downloads RTF files from external C2 server, using the template injection technique. The downloaded RTF downloaded another image file hidden with a Window PE format malware through the steganography technique from Paste.ee, a file sharing website. The group used the process hollowing technique to execute a malware known as Remcos in the targeted system, which carried out various malicious activities according to the command received.
SectorJ85 group carried out a typosquatting attack, a technique used to which is a method of taking advantage of user’s typos or cognitive errors by making it similar to the domains used by actual companies and institutions, to target a large number of general users. The group attempted to collect the account information of the target by directing them to a fake login page when they accessed a phishing site hosted by the group due to typos or cognitive errors.
SectorJ146 group was found to be active in Russia. The group sent out phishing emails impersonating federal agencies, leading the targets to download and execute the attached compressed file. The compressed file contained a Stealer malware, which was used to steal data from the attacked system and send it to a C2 server.
SectorJ152 group used the Qlik Sense vulnerability to distribute the Cactus Ransomware. They stole data from the targeted system using Rclone, a cloud storage file transfer program.
SectorJ172 group was found to be active in Nigeria, South Africa, Netherlands, Norway, Germany, Russia, Romania, Malaysia, Mexico, Morocco, United States, Vietnam, Belgium, Brazil, Saudi Arabia, Sweden, Syria, United Kingdom, Ecuador, Iran, Iraq, Egypt, Indonesia, Japan, China, Colombia, Turkey, Pakistan, Poland, France, Philippines, and South Korea. The group used Windows shortcut (LNK) files disguised as movie files. When the Windows shortcut file is executed, an embedded PowerShell command was executed, and the content delivery network (CDN) domain was used as a download server to download additional malware onto the targeted system.
SectorJ177 group was found to be active in the United States and Canada. The group used Microsoft Teams to send messages and make calls to their targets, leading the targets to allow remote access to their systems through Quick Assist. The group then executed a batch script file to download additional malware onto the remote system, and ultimately used PsExec to distribute the Black Basta ransomware to other networks connected to the targeted system.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
