Monthly Threat Actor Group Intelligence Report, July 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC Threat Research Lab based on data and information collected from 21 June 2024 to 20 July 2024.
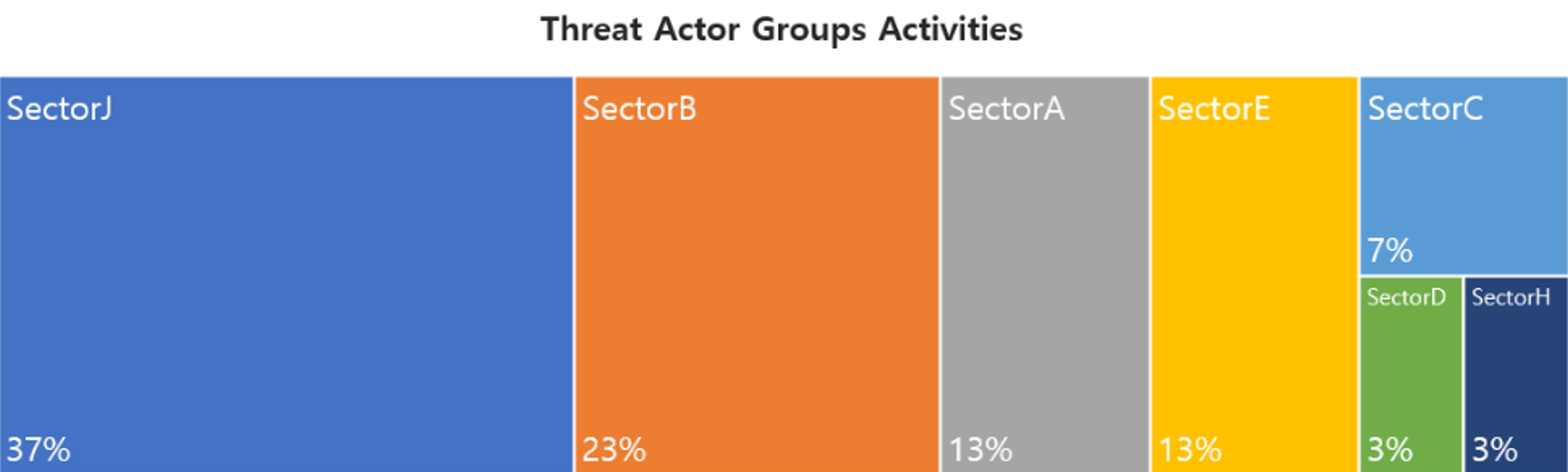
In July, activities by a total of 30 Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 37%, followed by SectorB and SectorA groups.
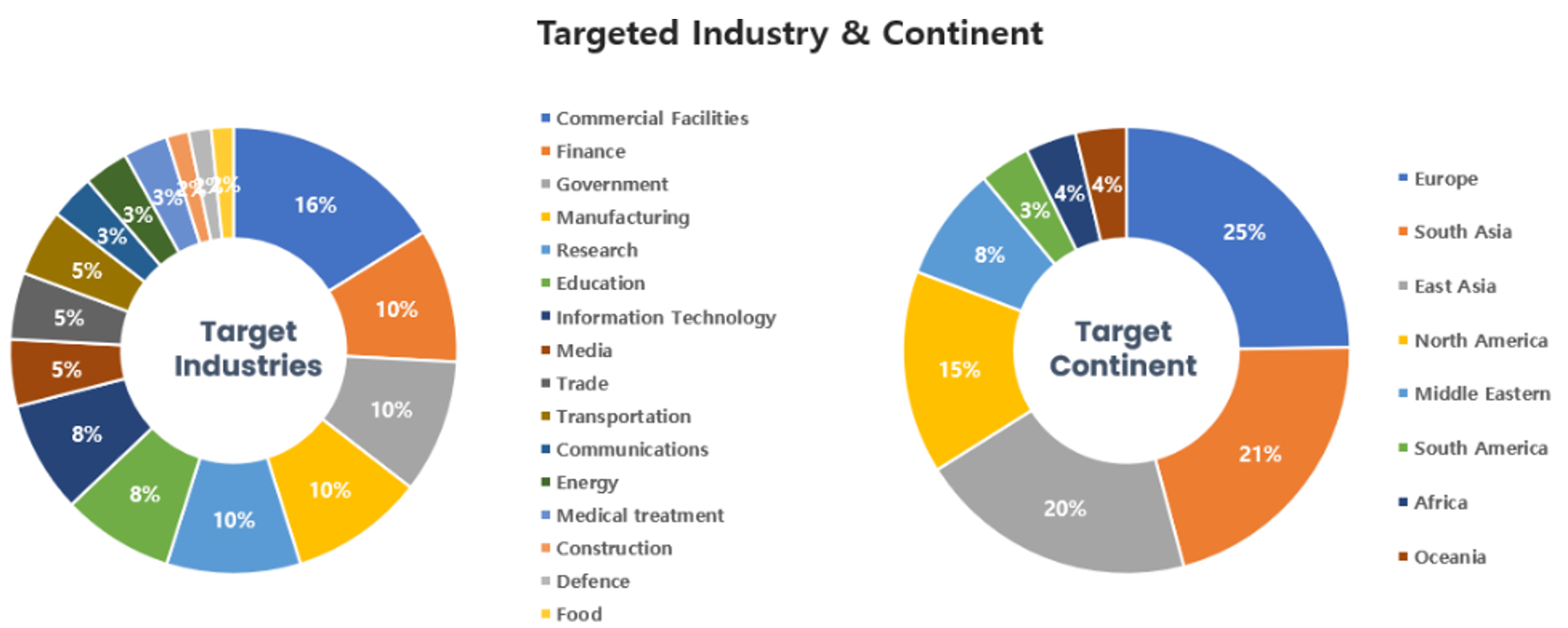
Threat Actors identified in July carried out the highest number of attacks on workers and systems in commercial facilities and financial industries. Regionally, Europe and South Asia were seen as the regions with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In July 2024, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA04, SectorA05 and SectorA07 groups.
SectorA01 group was found to be active in France, Pakistan, Malaysia, Taiwan, Spain, USA, India, Philippines, South Korea, Vietnam, Morocco, Brazil, Israel, and Bosnia and Herzegovina. The group disguised themselves as hiring managers to send compressed files with filenames such as hiring tests and source code review tests, leading the targets to execute the malicious script within the compressed files.
SectorA04 group was found to be active in South Korea. The group targeted on central management solutions of corporations with the aim of disseminating malware through the file distribution function, and exploited vulnerabilities to gain control of the solution.
SectorA05 group was found to be active in South Korea and Germany. The group used malware in Windows shortcut (LNK) format that was disguised as a request for lectures. They carried out their attack by downloading additional malware through the Dropbox API and executing it in a fileless manner.
SectorA07 group was found to be active in South Korea. The group used a malware in the form of a Windows shortcut (LNK) file that was disguised as a VAT revision notice, which executed a Visual Basic Script and a Batch script when executed, ultimately carrying out malicious activities such as information collection and additional malware download and execution.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In July, activities by a total of 7 hacking groups were identified, and the groups were SectorB01, SectorB07, SectorB10, SectorB17, SectorB28, SectorB38, SectorB101SectorA07 groups.
SectorB01 group was found to be active in the United States, Romania, Thailand, Italy, Spain, Turkey, the United Kingdom, and Taiwan. The group carried out attack activities by distributing a malware loader to the targeted systems and installing a backdoor that exploits Google Drive for command and control communication. The backdoor carried out various malicious activities such as collection of information such as computer name, username, and OS versions, as well as command line command execution, according to the command received through exploiting Google Drive.
SectorB07 group was found to be active in Australia. The group targeted on Australian government institutions and organizations to carry out attacks that exploited vulnerabilities in exposed infrastructure on the internet. After gaining initial access authorizations and obtaining legitimate credentials, the group used an open-source tool known as Secure Socker Funneling to access Web Shells and connect to malicious infrastructure.
SectorB10 group was found to be active in South Korea. The group distributed a Windows help (CHM) file disguised as statistics on employment rate of a Korean university to carry out their attacks. Ultimately, the group used the installed malware to execute malicious files through the cmd.exe command, in preparation for further future attacks.
SectorB17 group was found to be active in Italy. The group distributed a Microsoft Word document explaining how to participate in a meeting through the Skype Web App to carry out their attacks, leading targets to download a malicious Windows installer (MSI) file disguised as the Skype Web app. The remote access malware installed in the targeted system in the final stage carried out various malicious activities such as screen capturing, program execution, file exploration, and process management according to the command received from the command and control server.
SectorB28 group generated and distributed malware though ShadowPad Builder.
SectorB38 group was found to be active in Vietnam. The group distributed Microsoft Word documents disguised as official documents sent from the Central News Agency of the Communist Party of Vietnam, leading targets to download the remote template document file and execute it. The group downloaded and installed a backdoor known as RoyalCli in the targeted systems, downloading malware from external servers and executing them to set the base for future attacks.
SectorB101 group was found to be active in Angola, Russia, and the Netherlands. The group targeted on government institutions to deliver spear phishing emails attached with RAR compressed files. The malware installed carried out various malicious activities such as system information theft, file download, arbitrary command and binary execution functions according to the command received from the C2 server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In July, activities by a total of 2 hacking groups were identified, and the group were SectorC02 and SectorC08.
SectorC02 group was found to be active in the United States and Ireland. The group used malware in the form of Windows shortcut (LNK) files disguised as documents from national statistical agencies, ultimately using malware that could download and execute additional malware or carry out PowerShell commands according to the command received from the C2 server.
SectorC08 group was found to be active in in the United States, Germany, Netherlands, Russia, Norway, and Ukraine. The group attached a HTML (Hypertext Markup Language) format malware to a phishing mail disguised as urgent special notification documents and delivered it to the targets. The HTML malware attached to the phishing email uses the onmousemove event attribute to decode a JavaScript encoded in Base64 format and execute it when mouse movement is detected in the HTML screen.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In July 2024, activities by a total of 1 hacking groups were identified, and the group was SectorD02 group.
SectorD02 group was found to be active in Jordan, Israel, Turkey, Saudi Arabia, India, Portugal, Poland, Germany, Singapore, and the Netherlands The group used MSI (Windows Installer) malware disguised as web seminar materials in their attack, and ultimately attempted to remotely control targeted systems using Atera, a remote access tool.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In July 2024, activities by a total of 4 hacking groups were identified, and the group were SectorE01, SectorE04, SectorE05, and SectorE06.
SectorE01 group was found to be active in Bhutan and the United States. The group distributed Windows shortcut (LNK) files disguised as funding proposal documents to carry out their attacks. They ultimately installed Brute Ratel, a penetration testing tool, and a backdoor written in Golang on the targeted systems.
SectorE04 group was found to be active in Pakistan and the United Kingdom. The group distributed Microsoft Excel documents disguised as list of employees to carry out their attacks. When the target opened the document, a malware was downloaded from the external server onto the targeted system, preparing the base for future attacks.
SectorE05 group was found to be active in Pakistan, the United States, and China. The group distributed a Windows help (CHM) file under the name of CamScanner to carry out their attacks. When the target executed the CHM file, a malware was downloaded and executed to set the base for future attacks.
SectorE06 group was found to be active in Bangladesh and China. The group distributed Windows help files (CHM) under the name of Proposal to carry out their attack. When the Windows help file was executed in the targeted system, the computer name and username was delivered to the C2 server, then a PowerShell malware was downloaded and executed to set the base for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In July 2024, activities by a total of 1 hacking groups were identified, and the group was SectorH03 group.
SectorH03 group was found to be active in India and Russia. The group distributed Android apps disguised as TikTok to carry out their attacks, and performed malicious activities such as collecting SMS messages, contacts, call history according to the command received from the command and control server. In addition, the group distributed Microsoft Word documents disguised as financial accounting lectures to install a remote access malware known as Crimson RAT in the targeted system, which carried out various malicious activities such as system information theft, keylogging, and screen capture according to the commands received from the command and control server.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of Cyber Crime Group Activities
In July 2024, activities by a total of 11 hacking groups were identified, and the groups were SectorJ01, SectorJ09, SectorJ64, SectorJ74, SectorJ146, SectorJ149, SectorJ154, SectorJ164, SectorJ168, SectorJ184, and SectorJ187.
Unlike other government-supported hacking groups, these groups steal online information with tangible value that can secure monetary gains in the real world, or they hack specific companies and organizations directly, spreading ransomware within internal networks, or demanding monetary compensation after stealing important industrial secrets.
SectorJ01 group was found to be active in in the Netherlands, Taiwan, Germany, Russia, Romania, Malaysia, USA, Austria, Italy, India, Canada, Portugal, France, and Australia. The group distributed Microsoft App Package Files (MSIX) through phishing sites, which activates the PowerShell script within the MSIX file when the target executed the file. The PowerShell script downloads and executes the NetSupport RAT malware from an external server, allowing the attackers to remotely control the target system and carry out malicious attacks.
SectorJ09 group carried out a formjacking attack using obfuscated skimming JavaScript, stealing financial information entered by the target on payment pages.
SectorJ64 group was found to be active in Italy. The group exploited a RCE (Remote Code Execution Vulnerability) in Oracle WebLogic Server to execute ELF (Executable and Linkable Format) malware on the targeted systems. The executed ELF malware additionally downloaded a script that downloads DDoS botnet and a mining malware. The group ultimately used the DDoS Botnet and the mining malware to remotely control the targeted systems, carry out DDoS attacks, and mine cryptocurrency known as Monero.
SectorJ74 group was found to be active in Taiwan, Germany, the United States, Vietnam, Saudi Arabia, Spain, Israel, Japan, and Thailand. The group distributed internet shortcut files (URLs) disguised as phishing emails related to purchase orders. When the target opens the attached internet shortcut file, it connects to a URL controlled by the attacker through Microsoft Windows MSHTML platform’s spoofing vulnerability (CVE-2024-38112) via Internet Explorer. The target is then prompted to download additional malware in the form of an HTML application (HTA) file.
SectorJ146 group was found to be active in in South Africa, Germany, Romania, USA, Vietnam, United Arab Emirates, UK, Israel, India, Jamaica, Czech Republic, Canada, Kenya, and the Philippines. The group used phishing emails disguised as tax invoices to distribute a compressed file containing a Batch file format script. When the target executes the Batch script file, the obfuscated PowerShell command within the Batch script is executed, downloading and executing a stealer malware that collects system data of the targeted system and sends it to the C2 server.
SectorJ149 group was found to be active in the Netherlands, Germany, the United States, Venezuela, Brazil, Argentina, Ireland, Estonia, Ukraine, Japan, Poland, and Colombia. The group distributed compressed files containing Windows shortcut (LNK) files and prompted the target to execute the shortcut file. Executing the shortcut file executed the PowerShell command within it, downloading a compressed file and a bait document from an external server. The DLL file contained within the compressed file was loaded through the DLL side-loading technique, and carried out various malicious activities such as system data theft, DDoS attacks, and ransomware dissemination.
SectorJ154 group was found to be active in Russia, Czech Republic, and Thailand. The group delivered a password-protected compressed file through a phishing email impersonating the accounting team, leading the targets into executing the EXE format executive disguised as a PDF file. The remote control malware of the group carried out various malicious activities such as system information collection, screen capture, and keylogging according to the command received from the C2 server.
SectorJ164 group was found to be active in the Netherlands, Moldova, United States, Sweden, Italy, Canada, Cyprus, Turkey, and France. The group distributed Medusa Ransomware in order to secure financial profits, and the ransomware encrypted files on the system then generated a ransom note to provide a means of contact for discussing financial issues.
SectorJ168 group was found to be active in Ukraine and Chile. The group targeted on Veeam backup server to exploit a vulnerability and disseminate the Akira ransomware.
SectorJ184 group was found to be active in South Korea, Germany, the United States, Spain, Russia, India, China, the Czech Republic, Canada, and Turkey. In order to disseminate various malware simultaneously, the group used a loader malware disguised as “Wextract”, a Windows program used to execute Windows Cabinet files. The malware was used to download various malware such as Botnet and stealer malware from the C2 server to the targeted system, and to execute them.
SectorJ187 group was found to be active in the Netherlands, Germany, Romania, USA, UK, China, Canada, Thailand, and Australia. The group distributed malware disguised as Python scripts related to Artificial Intelligence (AI) through GitHub. When the target executes the Python script, the malware collects their data and sends it to a Discord webhook. In addition, the group distributed compressed files containing malware written in Lua through a community forum for the car simulation game “BeamNG”, and the Lua malware executed a PowerShell which downloaded a remote access malware. This malware was identified to have been used to disseminate the Lockbit ransomware.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
