Monthly Threat Actor Group Intelligence Report, September 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC Threat Research Lab based on data and information collected from 21 August 2024 to 20 September 2024.
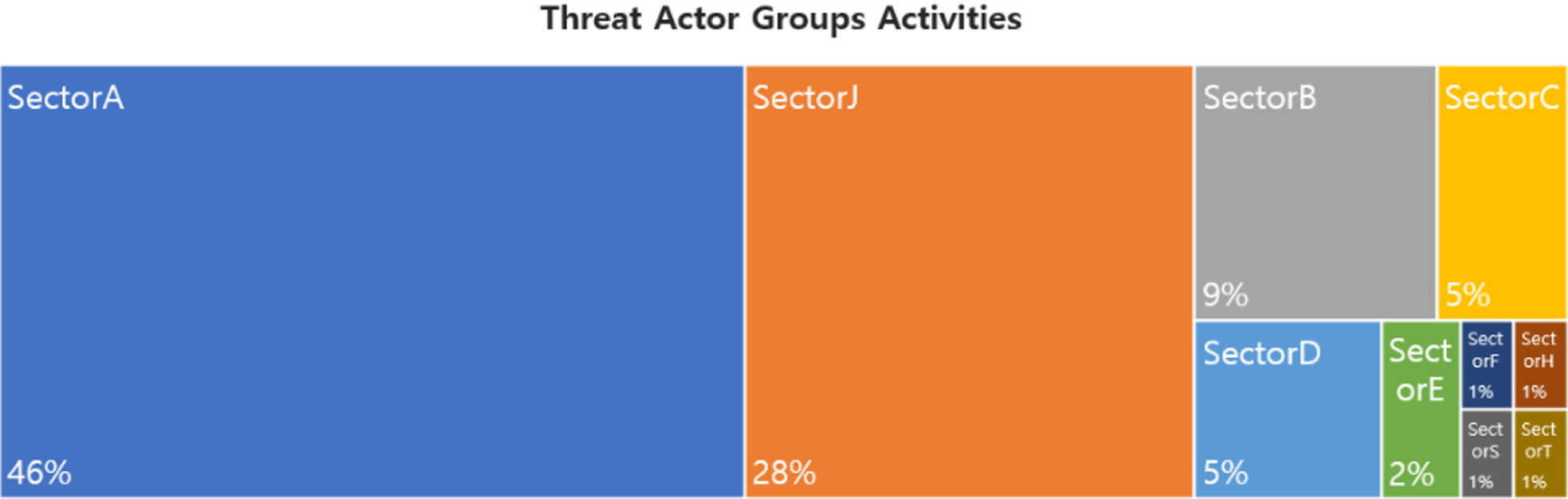
In September, activities by a total of 47 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 46%, followed by SectorJ and SectorB groups.
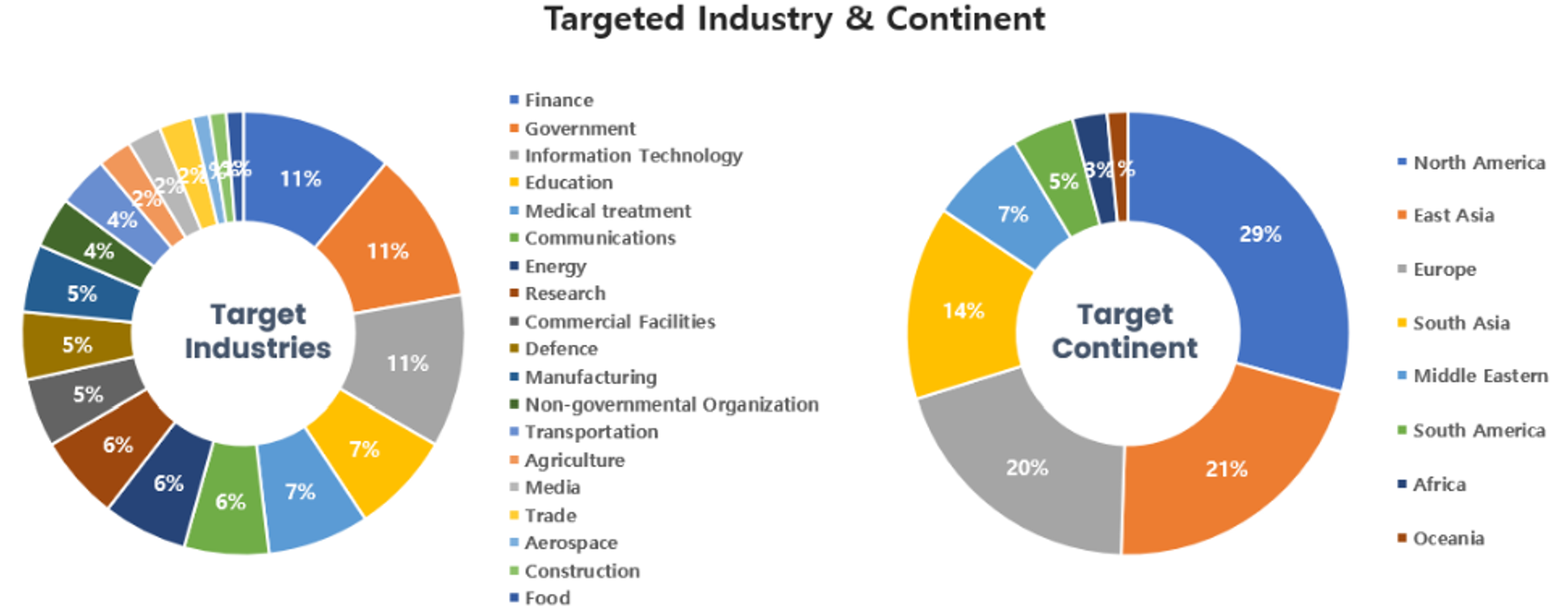
Threat Actors identified in September carried out the highest number of attacks on workers and systems in finance and government institutions. Regionally, North America and East Asia were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In September 2024, activities by a total of 6 hacking groups were identified, and the groups were SectorA01, SectorA03, SectorA04, SectorA05, SectorA06, and SectorA07 groups.
SectorA01 group was found to be active in Japan, Netherlands, Canada, Philippines, United States, Singapore, Russia, Australia, Poland, India, Vietnam, United Kingdom, France, Egypt, Brazil, Sweden, Turkey, Qatar, Colombia, Morocco, Belgium, United Arab Emirates, China, Iran, Hong Kong, Jordan, Lithuania, South Korea, and Germany. The group disguised themselves as recruiters to disseminate compressed files under the filename of hiring tests and source code review tests, prompting the targets to execute the malicious script within the compressed file.
SectorA03 group was found to be active in Hong Kong and Germany. The group used a DLL format malware that used the XOR algorithm and Base64 algorithm to encrypt the strings used in malware execution. The DLL malware took advantage of the ImageView_Fullscreen module of shimgvw.dll, a legitimate component of the Windows photo gallery viewer. The malware executed in the final stage had the function to collect system information or receive and execute additional malware from the attacker, depending on the situation.
SectorA04 group was found to be active in Italy and Columbia. The group disguised themselves as recruiters to deliver encrypted PDF files and malicious PDF readers designed to execute this file to the targets, and the malware executed in the final stage had the functions to remotely execute commands, download files, and steal data.
SectorA05 group was found to be active in the United States, South Korea, Singapore, India, Japan, Morocco, Canada, and the United Kingdom. The group used Windows shortcut (LNK) format malware disguised as a proposal for policy discussion on security issues. The group used the Dropbox API to download additional malware and execute it using a fileless method.
SectorA06 group was found to be active in Austria. The group targeted on macOS users to disseminate Mach-O malware disguised as Discord, a VoIP application software. This malware replaces the installed Discord program on infected systems, automatically runs every time the system boots, and ultimately creates and executes additional malware to perform remote control functions.
SectorA07 group was found to be active in in the United States, South Korea, and Canada. The group used spear-phishing emails disguised as messages from the customer service of a portal site, claiming that the email account would be deactivated.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In September, activities by a total of 8 hacking groups were identified, and the groups were SectorB01, SectorB08, SectorB22, SectorB62, SectorB72, SectorB79, SectorB100, and SectorB103 groups.
SectorB01 group was found to be active in the United States, Thailand, Canada, China, Singapore, Hong Kong, and Japan. The group carried out large-scale attack activities through a multiplatform backdoor malware that affects Windows and Linux systems. This backdoor malware performed malicious actions such as file manipulation, command execution, and remote port scanning according to commands received from the command and control (C2) server on the targeted system.
SectorB08 group was found to be active in Japan, the United Kingdom, and Vietnam. The group targeted government agencies in the Middle East and carried out attack activities by distributing web shells and backdoor malware. They also installed various open source tools and backdoor malware for lateral movement through the web shells installed on the targeted systems.
SectorB22 group was found to be active in the Philippines, China, and Taiwan. The group has carried out attacks targeting various government agencies in the Asia-Pacific (APAC) region, and used removable drives and spear-phishing emails for initial access to the targeted systems.
SectorB62 group was found to be active in Chile, Netherlands, Germany, Hong Kong, China, the Philippines, and the United States. The group targeted government agencies in Southeast Asia and carried out attack activities by distributing various open-source tools and off-the-shelf tools.
SectorB72 group was found to be active in Germany. The group targeted on government institutions and used various tools for their attack. They exploited vulnerabilities in the Microsoft Exchange Server to gain initial access, and used keywords related to government, diplomacy, and military in the email server to search for sensitive information.
SectorB79 group was found to be active in the United States, Taiwan, and China. The group targeted on government institutions, military, higher education, and telecommunications sectors in Southeast Asia using a multilayered Botnet malware, which carried out various malicious activities such as file uploading and downloading, and distributed denial of service attack (DDoS) on the targeted system.
SectorB100 group exploited the Cisco NX-OS device vulnerability to distribute malware and install it on the targeted systems. The malware had various functionalities such as arbitrary command execution, file download and upload, and tunnel setup for network traffic proxies for data infiltration and maintaining consistent access to the targeted system.
SectorB103 group was found to be active in China, South Korea, Taiwan, the Philippines, Vietnam, and Thailand. They exploited the OSGeo GeoServer vulnerability or used spear phishing email to carry out attacks on government institutions, telecommunication companies, and the energy industry.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In September, activities by a total of 4 hacking groups were identified, and the group were SectorC04, SectorC08, SectorC15, and SectorC22 groups.
SectorC04 group was found to be active in the United States. The group performed watering hole attacks targeting systems without patches by exploiting known vulnerabilities in iOS and Google Chrome. They also attempted to steal browser cookies and user session information.
SectorC08 group was found to be active in Ukraine. The group used malware in the form of HTML (Hypertext Markup Language), which intentionally causes image loading errors, and designed the malware such that an obfuscated code with malicious purposes was executed through the onerror function which is executed when an error occurs.
SectorC15 group was found to be active in the United States. The group targeted on major industries including energy, finance, defense, and government agencies, using malware with system destruction and information stealing properties as its main function.
SectorC22 group built phishing websites disguised as Protonmail, a secure email service in Switzerland, and domains related to Ukraine, in order to attempt collection of credentials and sensitive information.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In September 2024, activities by a total of 5 hacking groups were identified, and the group were SectorD01, SectorD02, SectorD12, SectorD16, and SectorD28 groups.
SectorD01 group was found to be active in Iraq, Pakistan, and Bahrain. The malware used by this group utilized government agency email accounts as command and control (C2) servers, and used DNS tunneling techniques to exfiltrate data through DNS requests.
SectorD02 group was found to be active in Israel. The group used spear phishing emails containing request to fill out a form related to security, and ultimately attempted to remotely control the targeted systems using Atera, a remote access tool.
SectorD12 group was found to be active in the United States and the United Arab Emirates. The group used malware disguised as Adobe PDF documents containing the policy guide and infrastructure security guide of a satellite communication company, and ultimately, used a malware that could collect information on system and network environments, maintain persistence, execute commands, and download additional malware depending on the situation.
SectorD16 group was found to be active in Israel, the United States, Azerbaijan, and the United Arab Emirates. The group exploited vulnerabilities in network devices to gain initial access, and used this as a foundation to obtain network access privileges and prepare for subsequent ransomware attacks. They provided the acquired network access and domain administrator privileges to ransomware affiliate organizations to support ransomware distribution, and in return received a portion of the ransom payment as commission to generate profits.
SectorD28 group was found to be active in in Israel, the United Kingdom, Jordan, Iran, Saudi Arabia, Turkey, Cyprus, Sweden, Iraq, India, Netherlands, the United States, Kuwait, and Qatar. The group secured initial access through web shells and then performed command and control within the network using remote control malware, thereby providing access to other threat groups or establishing a foundation for subsequent attacks.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In September 2024, activities by a total of 2 hacking groups were identified, and the group were SectorE01 and SectorE05.
SectorE01 group was found to be active in the Netherlands, the United States, and China. The group carried out attacks through spear phishing emails attached with compressed files. Which contained malicious Windows shortcut (LNK) files. The group used various remote access malware installed on the targeted system to control them, decrypt password saved in web browsers, and stole important data.
SectorE05 group was found to be active in China. The group distributed malicious Windows help (CHM) files disguised as bidding information, which registered a PowerShell command for downloading malware upon execution. This was done in order to set the foundation for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorF Group Activities
In September 2024, activities by a total of 1 hacking groups were identified, and the group was SectorF01.
SectorF01 group was found to be active in Vietnam and Japan. The group has been continuously carrying out attacks for the purpose of information theft against a non-profit organization supporting human rights in Vietnam.
Hacking activities of SectorF carry the aim of collecting advanced information on governmental activities of countries neighboring supported government, such as political, diplomatic, and military activities, and to steal information related to cutting-edge technology for economic development of their country.
7. Characteristics of SectorH Group Activities
In September 2024, activities by a total of 1 hacking groups were identified, and the group was SectorH03 group.
SectorH03 group was found to be active in Japan, India, and the United Arab Emirates. The group distributed malicious Linux desktop entry (.desktop) files disguised as external cyber security audit documents for their activities. The malware downloaded and executed by the group on the targeted system is a Poseidon tool that supports the Red Teaming Framework, Mythic. The tool was used to control the targeted system, depending on the command received from the command and control (C2) server.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
8. Characteristics of SectorS Group Activities
In September 2024, activities by a total of 1 hacking groups were identified, and the group was SectorS01 group.
SectorS01 group was found to be active in Columbia and Italy. The group targeted on the insurance sector in Columbia, using spear phishing emails containing ZIP compressed files. The group used the remote access malware within the downloaded ZIP files to carry out various malicious activities such as keylogging, monitoring of banking and payment services, and data theft from web browsers and FTP clients, according to the commands received from the command and control (C2) server.
SectorS hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
9. Characteristics of SectorT Group Activities
In September 2024, activities by a total of 1 hacking groups were identified, and the group was SectorT01 group.
SectorT01 group was found to be active in Germany. The group used an MS Excel file format malware disguised as the contact point of the Ministry of Defense, inducing the targets into executing the malware by themselves.
SectorT hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
10. Characteristics of Cyber Crime Group Activities
In September 2024, activities by a total of 18 hacking groups were identified, and the groups were SectorJ01, SectorJ04, SectorJ06, SectorJ09, SectorJ25, SectorJ39, SectorJ73, SectorJ74, SectorJ84, SectorJ85, SectorJ110, SectorJ113, SectorJ119, SectorJ149, SectorJ172, SectorJ176, SectorJ189, and SectorJ190.
Unlike other government-supported hacking groups, these groups steal online information with tangible value that can secure monetary gains in the real world, or they hack specific companies and organizations directly, spreading ransomware within internal networks, or demanding monetary compensation after stealing important industrial secrets.
SectorJ01 group distributed malware through phishing sites. When the target accessed the phishing site, a pop-up window appeared stating that a browser extension was needed, inducing the targets to click the download button. Upon clicking the download button, it was deduced that additional malware in the form of a Windows Silent installer was downloaded from a hyperlinked Dropbox.
SectorJ04 group was found to be active in Russia. The group used a Trojan horse malware disguised as an audio file. The malware was deduced to have functions such as information collection from targeted systems, key logging, screen capture, and clipboard data collection.
SectorJ06 group was found to be active in Germany, Russia, Spain, USA, Brazil, Switzerland, India, China, Turkey, Poland, and France. The group used Conti ransomware to encrypt targeted systems in order to secure financial profits, and it was deduced that the group delivered a ransom note containing the Onion domain for financial discussions.
SectorJ09 group was found to be active in Switzerland. The group targeted on online shopping malls to carry out formjacking attacks by inserting obfuscated skimming JavaScript in the payment page, stealing financial information such as credit card information entered by the victims.
SectorJ25 group infiltrated target systems through brute force attacks and uploaded malicious scripts on the target system. This script terminated processes related to crypto-mining malware, and installed a rootkit on the targeted system. It also generated a backdoor account such that they could continuously access the targeted system through SSH.
SectorJ39 group was found to be active in the United States and the United Kingdom. The group distributed the Underground ransomware in order to secure financial profits, and it was deduced that the group delivered a ransom note containing the Onion domain for financial discussions.
SectorJ73 group was found to be active in China. The group used the HelloKitty ransomware to secure financial profits, and the malware generated a ransom note containing the Onion domain for financial discussions after encrypting the files in the system.
SectorJ74 group was found to be active in the United States. The group used malware with loader functionality capable of loading additional payloads onto the targeted system. and the malware was found to decrypt the encrypted payload within the code and then execute it on the targeted system using process injection technique.
SectorJ84 group was found to be active in Canada. The group used a stealer malware known as Formbook in order to steal data from targeted systems.
SectorJ85 group was found to be active in Russia and Ireland. The group exploited cloud authentication tokens exposed on code repositories such as GitHub and credentials obtained through phishing websites to infiltrate targeted systems. After initial access, the group collected Active Directory information and executed a remote monitoring and management (RMM) program. The group ultimately disseminated the BlackCat malware on the targeted system with the aim of securing financial profit.
SectorJ110 group was found to be active in the United States and France. The group used loader malware to load additional payload on the targeted system.
SectorJ113 group was found to be active in the Netherlands, Germany, Russia, Brazil, India, and Poland. The group used the QRYPT ransomware to secure financial gains, and it was deduced that the group delivered a ransom note containing the Onion domain for financial discussions.
SectorJ119 group was found to be active in the Netherlands, Germany, Madagascar, USA, Yemen, Ukraine, Iraq, Egypt, Italy, India, Indonesia, Canada, Costa Rica, Croatia, Poland, France, and the Philippines. The group used the SLAM ransomware to secure financial gain, and the SLAM ransomware collected information such as information of the encrypted system, encryption key, and screenshots, and transmitted them to the command and control (C2) server.
SectorJ149 group was found to be active in Germany, the United States, and Canada. The group used an Antivirus Killer malware that disable or forcefully terminate antivirus software in order to avoid the detection of the newly generate malware on the targeted system.
SectorJ172 group was found to be active in Nigeria, the United States, Singapore, Ireland, India, Japan, Canada, Hungary, and Korea. The group used a stealer malware known as Formbook to steal data from targeted systems.
SectorJ176 group was found to be active in Canada. The group used the Pharming malware to steal financial information and personal data of their targets, and the malware transmitted the collected personal information to a command and control (C2) server.
SectorJ189 group was found to be active in the Netherlands, Bangkok, Belgium, Singapore, Iran, India, China, Thailand, Philippines, South Korea, and Hong Kong. The group exploited vulnerabilities in web applications to distribute web shells, and the web shell distributed by the group was analyzed to be ASPXspy, one of the open-source web shells. The group used the web shell to collect information from targeted systems and execute additional malware, such as PlugX, a remote access malware. The PlugX malware installed on the target system is believed to have carried out malicious activities such as system information gathering, keylogging, and screen capturing, based on commands received from the command and control (C2) server.
SectorJ190 group was found to be active in Germany, Russia, the United States, the United Kingdom, Ukraine, Japan, and Tunisia. The group executed the Lockbit ransomware on targeted systems to encrypt them, and also used a Wiper malware to damage the MBR (Master Boot Record) area of connected drives, making the system unable to boot properly.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
