Monthly Threat Actor Group Intelligence Report, October 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC Threat Research Lab based on data and information collected from 21 September 2024 to 20 October 2024.
In October, activities by a total of 31 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 37%, followed by SectorJ and SectorE groups.
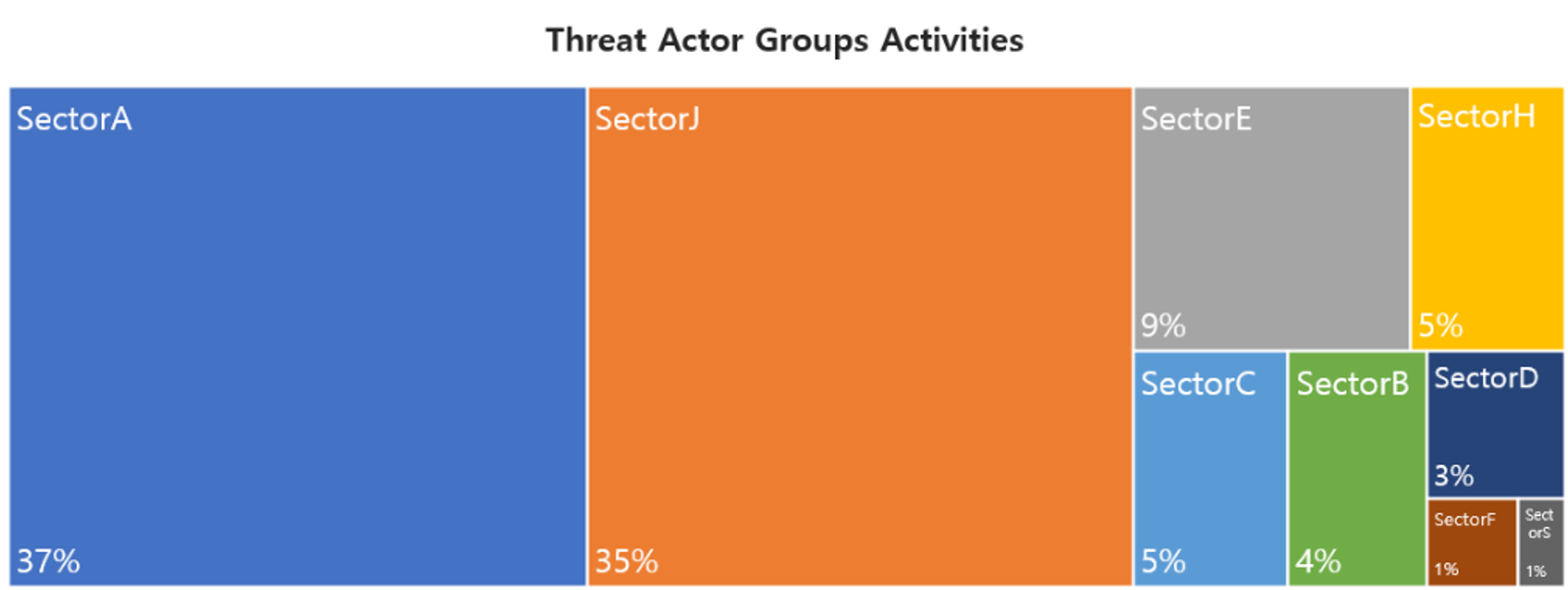
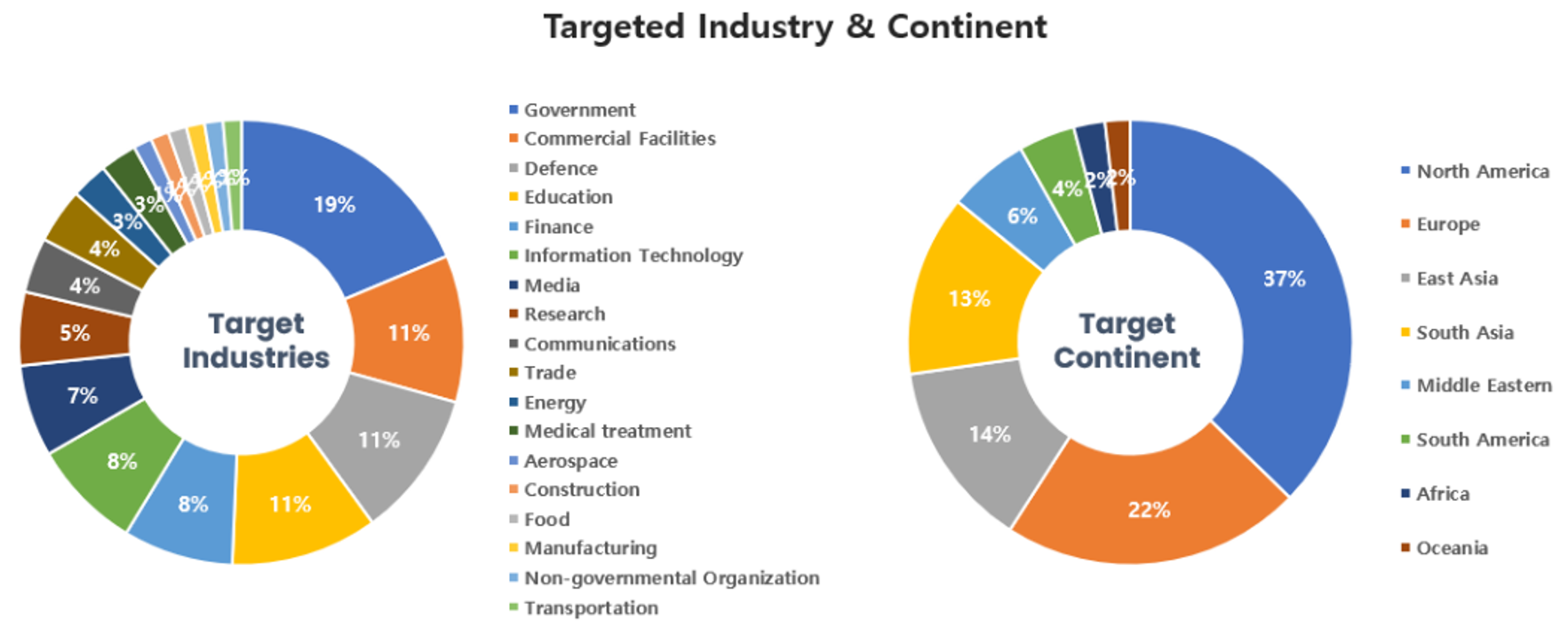
Threat Actors identified in October carried out the highest number of attacks on workers and systems in government institutions and the commercial sector.
Regionally, North America and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In October 2024, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05 and SectorA07 groups.
SectorA01 group was found to be active in the United States, Algeria, South Korea, Taiwan, China, Netherlands, Egypt, and Brazil. The group uploaded a malicious project named ‘nft_marketplace-main’ on GitHub, disguising it as a legitimate NFT marketplace project to induce software developers into downloading the project without suspicion. The final backdoor installed on the targeted system provided a foundation for long-term data collection, and had the function to communicate with the attacker’s server to execute additional commands, and send the collected data to the server.
SectorA02 group was found to be active in Cambodia, Israel, South Korea, and Japan. The group used a phishing email attacked with a compressed file named “NGO Income_edit.zip” for their attacks. The final malware used is a PowerShell based malware that carried out various activities such as file infiltration, registry modification, and creating scheduled tasks according to the attacker’s commands.
SectorA05 group was found to be active in South Korea and Japan. The group used a Windows shortcut (LNK) format file disguised as a book related to cryptocurrency, which used the Dropbox API to download additional malware and execute it through the fileless method.
SectorA07 group was found to be active in South Korea and Canada. The group used Windows shortcut (LNK) file format malware disguised as a project information confirmation request. When the target executed the malware, a Visual Basic script and Batch script format malware was executed ultimately, collecting information and downloading and executing additional malware.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In October, activities by a total of 3 hacking groups were identified, and the groups were SectorB22, SectorB60, and SectorB104.
SectorB22 group was found to be active in Thailand, Egypt, Pakistan, Korea, USA, Sri Lanka, and Vietnam. The group distributed Windows shortcut (LNK) files disguised as Vietnam Public Security Reports to carry out their attacks. Through these Windows shortcut files, the group used a penetration testing tool called Cobalt Strike to perform malicious actions according to various commands received from their command and control (C2) server.
SectorB60 group used phishing domains similar to Google’s domain to carry out their activities.
SectorB104 group was found to be active in India, Brazil, Singapore, Vietnam, and Mauritius. The group targeted government agencies, academic institutions, and political organizations in Asian countries and used SQL injection techniques to inject malicious SQL code into vulnerable public web servers in order to install web shells or malware for the purpose of stealing credentials.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In October, activities by a total of 1 hacking groups were identified, and the group was SectorC08.
SectorC08 group was found to be active in Ukraine, Bulgaria, Latvia, Lithuania, Poland, and Russia. The group used malware in the form of PE (Portable Executable) disguised as military-related documents.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In October 2024, activities by a total of 4 hacking groups were identified, and the group were SectorD01, SectorD02, SectorD05, and SectorD30.
SectorD01 group was found to be active in the United Arab Emirates and Iran. The group exploited vulnerabilities in public applications such as Microsoft Exchange server, installed web shells on targeted servers to establish a remote command execution environment, and executed .NET-based malware on the targeted systems to collect data and transmit it externally in encrypted form.
SectorD02 group was found to be active in Azerbaijan, Israel, Ireland, the United States, Pakistan, and Germany. The group used Windows installer (MSI) malware disguised as conference materials, and ultimately attempted to remotely control targeted systems through the use of the remote access tool known as PDQ Connect.
SectorD05 group was found to be active in the United States and Israel. The group targeted government agencies, military organizations, and research institutions as their main targets, and delivered malicious PDF documents through phishing emails.
SectorD30 group approached their targets through email, messaging platforms, or social media, and impersonated trusted organizations or individuals to induce them into entering their credentials.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In October 2024, activities by a total of 7 hacking groups were identified, and the group were SectorE01, SectorE02, SectorE03, SectorE04, SectorE05, SectorE08, and SectorE09.
SectorE01 group was found to be active in Bhutan and China. The group targeted on institutions in the field of aerospace, technology research, as well as government agencies to distribute Windows shortcut (LNK) files for their attacks. The group used the additional malware installed on the targeted system using the Windows shortcut file to modify security monitoring API and avoid detection. They collected system information and carried out malicious actions according to commands received from their command and control (C2) server.
SectorE02 group was found to be active in India and Tunisia. The group distributed Microsoft Word documents disguised as SOP (Standard Operating Procedure) documents for their attacks, and through the macro within the Word document, additional malware was installed to steal system information and download other additional malware to prepare the foundation for subsequent attacks.
SectorE03 group was found to be active in the Netherlands. The group distributed a RAR compressed file containing a Windows shortcut (LNK) file that was disguised as a notification document related to the increase in budget for Hajj, a Muslim pilgrimage. The group used the shortcut file to install malware on the targeted system, which was used to steal files of a specific extension and system information such as computer name and username.
SectorE04 group was found to be active in Cambodia, China, Pakistan, India, Taiwan, United States, Iran, Marshall Islands, Netherlands, Bangladesh, Djibouti, Jordan, Malaysia, Maldives, Myanmar, Nepal, Saudi Arabia, Sri Lanka, Turkey, United Arab Emirates, Afghanistan, France, Indonesia, and Morocco. The group distributed Microsoft Word document disguised as the official documents of the Cambodia government for their attacks. Through the Word document, a remote template document file was downloaded onto the targeted system, laying the groundwork for subsequent attacks.
SectorE05 group was found to be active in in Belarus, UK, Pakistan, Bangladesh, Latvia, USA, and Turkey. The group distributed a Windows installer (MSI) file disguised as a Laos Ministry of Defense meeting program document to carry out their attacks. Through this Windows installer file, the group installed a remote access malware known as PlugX on the targeted systems, which carried out various malicious activities according to commands received from the command and control (C2) server.
SectorE08 group was found to be active in the United Kingdom, Pakistan, Bangladesh, Germany, Netherlands, China, Thailand, Sri Lanka, and Singapore. The group distributed Windows Help (CHM) files disguised as government related documents to carry out their attack. The group installed a backdoor malware on the targeted systems through this CHM file, which allowed them to perform various malicious actions such as remote command execution, file uploads and downloads on the targeted system, according to commands from their command and control (C2) server.
SectorE09 group was found to be active in Pakistan, Bangladesh, Sri Lanka, Nepal, and China. The group distributed RAR compressed files that contained a malware disguised as invitations to the Japanese embassy. The group exploited a vulnerability (CVE-2023-38831) that occurs during decompression of RAR files to install malicious DLL files through directory traversal, and utilized Cloudflare’s serverless platform, Workers, to carry out command and control (C2) activities.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorF Group Activities
In October 2024, activities by a total of 1 hacking groups were identified, and the group was SectorF01.
SectorF01 group was found to be active in Malaysia. The group distributed a loader malware with backdoor functionalities for their attack and used the malware to install a backdoor on the targeted systems to collect computer names and disk details. The group also set up the foundation for future attacks by loading a DLL file that contained an encrypted payload.
Hacking activities of SectorF carry the aim of collecting advanced information on governmental activities of countries neighboring supported government, such as political, diplomatic, and military activities, and to steal information related to cutting-edge technology for economic development of their country.
7. Characteristics of SectorH Group Activities
In October 2024, activities by a total of 1 hacking groups were identified, and the group was SectorH03 group.
SectorH03 group was found to be active in the Netherlands and India. The group distributed Linux desktop entry (.desktop) files disguised as Adobe PDF documents for their activities. The group used Mythic, a Red Teaming Framework installed through the Linux Desktop entry file on the targeted desktop, to control the targeted system according to the commands received from the command and control (C2) server.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
8. Characteristics of Cyber Crime Group Activities
In October 2024, activities by a total of 10 hacking groups were identified, and the groups were SectorJ02, SectorJ09, SectorJ39, SectorJ40, SectorJ57, SectorJ64, SectorJ72, SectorJ149, SectorJ175, and SectorJ190.
Unlike other government-supported hacking groups, these groups steal online information with tangible value that can secure monetary gains in the real world, or they hack specific companies and organizations directly, spreading ransomware within internal networks, or demanding monetary compensation after stealing important industrial secrets.
SectorJ02 group disseminated backdoor malware through a phishing email attached with a ZIP compressed file that contained a fake resume. The compressed file contained a Windows shortcut (LNK) file with an obfuscated command string within it, and when executed, the a backdoor was installed on the targeted system. Through this backdoor, the attackers obtained remote access authorizations and executed additional malicious payloads, in order to steal information and gain financial profit.
SectorJ09 group carried out a formjacking attack to steal financial information such as credit card information entered by the target by inserting a skimming script into an online payment page.
SectorJ39 group was found to be active in Ukraine and France. The group distributed the SnipBot malware through phishing emails attached with PDF files. When the target executed the attached PDF document, they were prompted to click on a hyperlink through an alert instructing them to download a font package for proper display of the document. Clicking on the hyperlink leads the target to a phishing site disguised as an Adobe site which induced the target to click on the download button. The group ultimately distributed the SnipBot malware to the target system, which executed malicious commands on the targeted system and stole system information.
SectorJ40 group was found to be active in Germany, the United States, Belgium, Switzerland, the United Kingdom, India, and Hungary. The group distributed Dridex malware through phishing sites disguised as legitimate websites. The malware is analyzed to have the capability of stealing financial data such as web browser login information and account numbers from targeted systems.
SectorJ57 group distributed malware through a phishing site disguised as a fake Google Meet website. When the target accessed the phishing site, a pop-up window claiming there was an issue with their microphone or headset would appear, prompting them to click a button to download the malware. Upon clicking the button, the StealC and Rhadamanthys malware with information stealing capabilities were installed onto the target’s system.
SectorJ64 group was found to be active in Mexico and the United States. The group exploited a vulnerability to disseminate malware on targeted systems.
SectorJ72 group distributed malware in the form of Windows shortcut (LNK) file. When the target executed the Windows shortcut file, a command embedded within the file was executed. The command served the function of sending information from the target system to the attacker’s command and control (C2) server.
SectorJ149 group was found to be active in Germany, Russia, Armenia, UK, Ukraine, Colombia, Czech Republic, Panama, Poland, and Australia. The group distributed malware through spear phishing emails disguised as payment orders from insurance companies. The phishing email was attached with a compressed file, which contained another password-protected compressed file, a text file and a PDF document with instructions on the password for decompression. When the target decompressed all files, they were prompted to execute a Visual Basic Script (VBS) file with a name related to the payment order. Once executed, the script would run a PowerShell command to download malware onto the target system through Bitbucket. The downloaded malware is analyzed to have the capability to remotely control the target system, steal sensitive information, and download additional malicious payloads.
SectorJ175 group was found to be active in South Africa, New Zealand, Malaysia, United States, Belgium, Sweden, Spain, Singapore, United Arab Emirates, Argentina, Ireland, United Kingdom, Italy, India, China, Canada, Colombia, Curacao, Czech Republic, Palau, France, and Australia. The group distributed the DragonForce malware, and used the double extortion strategy of encrypting data of the targeted system through the malware and demanding a ransom while threatening to leak the stolen data, in order to gain financial profit. The group left a ransom note on the targeted system to deliver the contact point for discussing about the financial issues with the target.
SectorJ190 group carried out a combined attack using the Wiper malware and ransomware. The group used the ransomware to encrypt data and demand for ransom, and disseminated the Wiper malware along with the ransomware to carry out a double destruction attack, making it difficult for the target to recover the targeted systems.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
