Monthly Threat Actor Group Intelligence Report, November 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC Threat Research Lab based on data and information collected from 21 October 2024 to 20 November 2024.
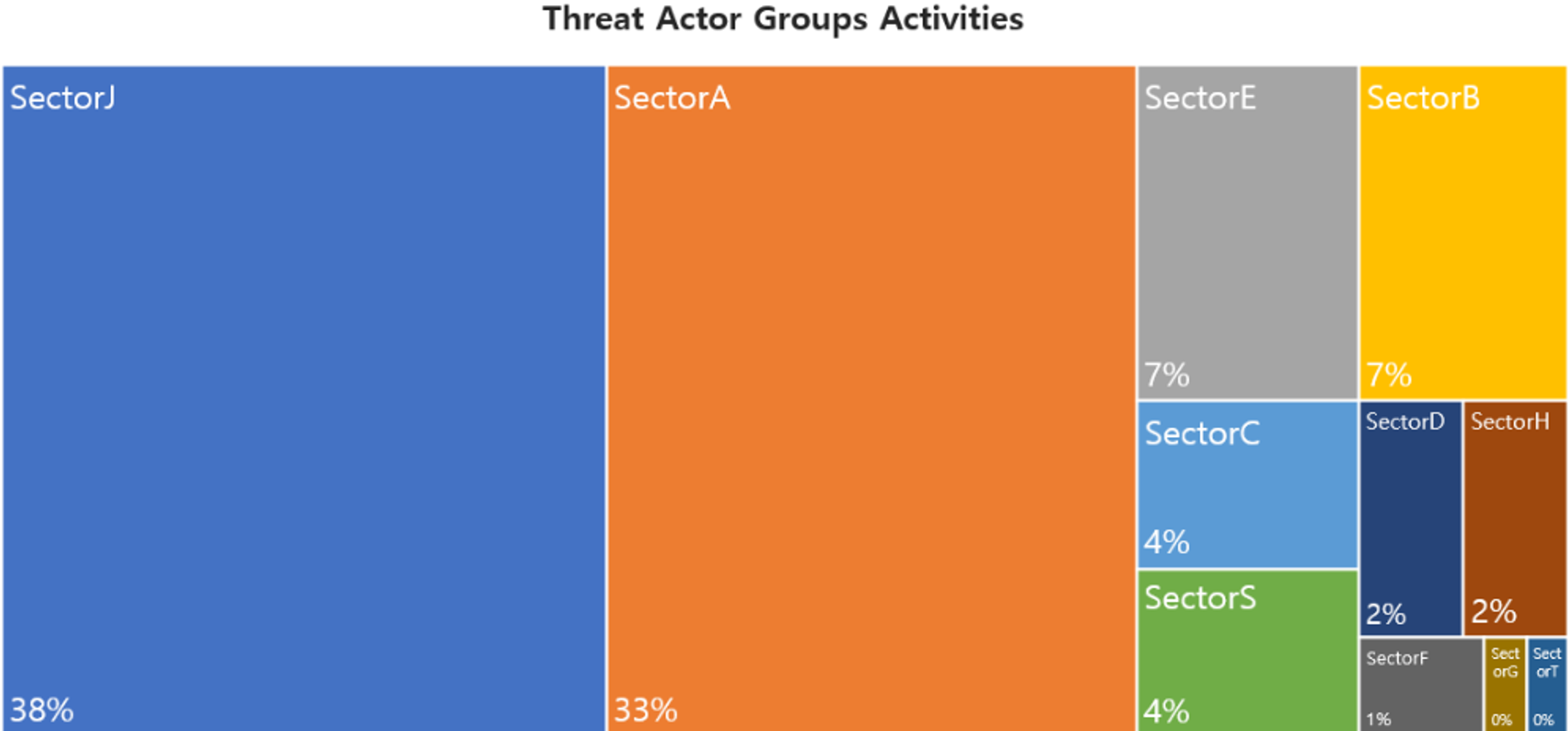
In November, activities by a total of 34 Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 38%, followed by SectorA and SectorE groups.
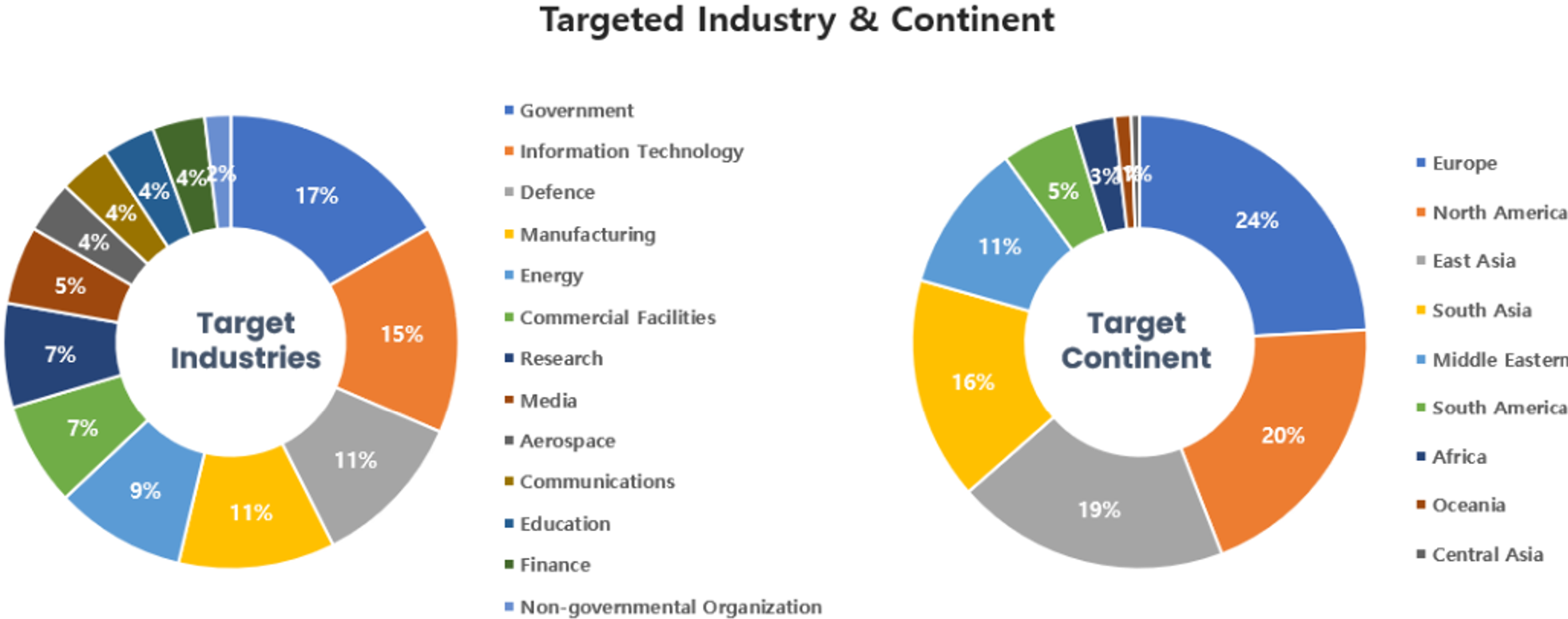
Threat Actors identified in November carried out the highest number of attacks on workers and systems in government institutions and the IT sector. Regionally, North America and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In November 2024, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA03, SectorA04 and SectorA06 groups.
SectorA01 group was found to be active in the Russia, China, Turkey, Pakistan, Indonesia, Brazil, France, Germany, the United States, India, Croatia, Vietnam, Singapore, Spain, Iran, Malaysia, Israel, Italy, Hong Kong, Switzerland, Japan, Ukraine, South Korea, Canada, and the United Kingdom. The group exploited remote position hiring processes of companies, by using fake identities to be hired and stealing sensitive data. The final backdoor used was installed on the targeted systems to set the foundation for a prolonged collection of data, and served the functions of communicating with attackers’ server to carry out additional commands and send the collected data.
SectorA02 group was found to be active in South Korea and the United Kingdom. The group used a Windows shortcut (LNK) file format malware under the filename of “Changes in China’s North Korean policies following North Korea’s close ties with Russia” to carry out their attack. Ultimately, a backdoor malware was used to steal files according to the attacker’s commands, and took advantage of cloud services such as pCloud and Yandex to transfer the files to the attacker’s cloud server.
SectorA03 group was found to be active in Iran, Germany, Japan, and Russia. The group used a virtual disc image (VHDX) disguised as an invitation file from the Chinese embassy, and the final malware used by the group had the functions of stealing files, screenshotting, downloading and executing additional malware according to the attacker’s commands.
SectorA04 group was found to be active in Russia. The group performed network takeover and privilege escalation through stolen credentials and Windows access token manipulation, and evidences of the group collaborating with a threat actor that uses Play ransomware in order to carry out ransomware attacks were identified.
SectorA06 group was found to be active in the United Kingdom and the United States. The group aimed to steal cryptocurrency assets and collect sensitive information, and they modified the Zsh environment file (~/.zshenv) for MacOS to ensure that the malware would continue to run even after system reboot.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In November 2024, activities by a total of 6 hacking groups were identified, and the groups were SectorB01, SectorB22, SectorB31, SectorB65, SectorB71, and SectorB106.
SectorB01 group was found to be active in Indonesia and Taiwan. The group stole sensitive data from political activists, politicians, and journalists in Southeast Asia. They installed a modular Windows-based monitoring framework on the targeted systems to collect sensitive data such as messaging app data, email client, and browser credentials, which was then encrypted and sent to a command and control (C2) server.
SectorB22 group was found to be active in India. The group distributed compressed files containing malware disguised as a promotion notification report for their attack, and the malicious DLL file installed on the targeted system was used to receive commands for malicious activities.
SectorB31 group was found to be active in Canada, India and China. The group exploited vulnerabilities in the Sophos Firewall to steal sensitive data and establish Operational Relay Boxes (ORB) for network control.
SectorB65 group distributed a modular malware framework targeting the telecommunications industry in South Asia to steal sensitive data. The malware installed on the targeted system was used to establish communication with command and control (C2) servers, to where the stolen data was encrypted and transmitted.
SectorB71 group was found to be active in China, Saudi Arabia, and Taiwan. The group distributed malware targeting government agencies and religious organizations in Taiwan, and used the installed malware on the targeted systems to steal web session cookies and collect cloud service data.
SectorB106 group targeted on telecommunication companies to distribute ransomware for their attacks. They directly hacked the external DNS server of the GPRS (General Packet Radio Service) network used to transmit data and messages between different telecommunication companies in order to gain access to the target network. In addition, the group used customized malware on the target network to collect subscriber information and call-related metadata, which was then sent to a command and control (C2) server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In November 2024, activities by a total of 1 hacking groups were identified, and the group were SectorC01 and SectorC04.
SectorC01 group was found to be active in Ukraine and Italy. The group used a phishing page disguised as a reCAPTCHA provided by Google, inducing users to copy PowerShell commands to the clipboard and execute them, performing browser authentication information theft and remote control when the commands were executed.
SectorC04 group was found to be active in Ukraine, Estonia, Turkey, Belgium, Sweden, the United Kingdom, Australia, and Japan. The group used phishing emails with topics such as “Amazon and Microsoft service integration” and when the target executed the RDP configuration file attached to the email, RDP connection with the attacker’s server was automatically set up. The group set the foundation for executing additional malware through the RDP connection.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In November 2024, activities by a total of 4 hacking groups were identified, and the group were SectorD02, SectorD05, and SectorD31.
SectorD02 group was found to be active in Rwanda, Morocco, Israel, Canada, Brazil, Afghanistan, the United Kingdom, the United States, Kazakhstan, India, Peru, Armenia, Egypt, Spain, Japan, Iraq, Argentina, Jordan, Germany, and Luxembourg. The group used phishing emails with attached PDF documents containing information about unpaid invoices, and ultimately attempted remote control of the targeted systems through a remote control tool called ‘Level’.
SectorD05 group was found to be active in Israel, India, Albania, Turkey, and the United Arab Emirates. The group created fake recruitment profiles on platforms such as LinkedIn and delivered phishing links disguised as job websites to their targets, inducing them to download the malware through the phishing link and executing it. The group ultimately used a backdoor malware with remote control capabilities, and used DLL side-loading techniques to avoid detection and collect system data.
SectorD31 group was found to be active in the United States, Russia, Israel, Germany, Mexico, and Spain. The group distributed modular malware through phishing emails impersonating the Israel National Cyber Directorate (INCD), which was capable of performing functions such as remote command execution, data theft, and screenshot captures.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In November 2024, activities by a total of 7 hacking groups were identified, and the group were SectorE02, SectorE04, SectorE05, and SectorE08.
SectorE02 group was found to be active in Bangladesh. The group distributed Windows shortcut (LNK) files disguised as RTF documents summarizing project-related delivery progress and key information, and carried out attack activities. They collected system information through the installed malware on the targeted systems and established a foundation for subsequent attacks by downloading additional malware.
SectorE04 group was found to be active in India, United Arab Emirates, Germany, Singapore, Netherlands, Pakistan, Maldives, Sri Lanka, and France. The group distributed Microsoft Word documents disguised as bidding notices to carry out their attack activities. Through the Word documents executed on the targeted systems, external remote template was downloaded to set the foundation for subsequent attacks.
SectorE05 group was found to be active in Korea, the United Kingdom, Japan, Iran, Romania, China, Pakistan, and Singapore. The group distributed a Windows Help (CHM) file disguised as a policy document for one of the Muslim pilgrimages, Hajj, and used the malware installed on the targeted system to download additional malware to lay the foundation for subsequent attacks.
SectorE08 group was found to be active in Hong Kong, China, Singapore, Japan, Taiwan, India, the United Kingdom, the United States, and Pakistan. The group targeted on the Pakistan defense industry and researchers in Hong Kong to distribute malicious RAR compressed files, and used Cobalt Strike, a penetration testing tool, installed on the targeted system to execute additional commands received from the command and control (C2) server.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorF Group Activities
In November 2024, activities by a total of 1 hacking groups were identified, and the group was SectorF01.
SectorF01 group was found to be active in Japan, South Korea, and China. The group distributed MSC (Microsoft Management Console Snap-in Control) files disguised as legal research documents related to the South China Sea, and used Cobalt Strike, a penetration testing tool, installed on the targeted system to execute additional commands received from the command and control (C2) server.
Hacking activities of SectorF carry the aim of collecting advanced information on governmental activities of countries neighboring supported government, such as political, diplomatic, and military activities, and to steal information related to cutting-edge technology for economic development of their country.
7. Characteristics of SectorH Group Activities
In November 2024, activities by a total of 1 hacking groups were identified, and the group was SectorH03 group.
SectorH03 group was found to be active in India, Germany, the United Kingdom, United Arab Emirates, Switzerland, Canada, Japan, and the United States. The group distributed Linux Desktop Entry (.desktop) files disguised as official military correspondence PDF documents to carry out threat activities. They also used Poseidon, a tool that supports a red teaming framework known as Mythic, that was installed on the targeted system to receive commands from the command and control (C2) server and control the targeted system.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
8. Characteristics of SectorS Group Activities
In November 2024, activities by a total of 1 hacking groups were identified, and the group was SectorS01 group.
SectorS01 group was found to be active in Brazil and Columbia. The group distributed self-extracting archive (SFX) files disguised as judicial documents using phishing emails, and through the DcRat remote control malware installed on the targeted system, additional commands received through the command and control (C2) server were carried out.
SectorS hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
9. Characteristics of Cyber Crime Group Activities
In November 2024, activities by a total of 10 hacking groups were identified, and the groups were SectorJ09, SectorJ25, SectorJ39, SectorJ72, SectorJ85, SectorJ90, SectorJ109, SectorJ149, SectorJ165, SectorJ175, and SectorJ191.
Unlike other government-supported hacking groups, these groups steal online information with tangible value that can secure monetary gains in the real world, or they hack specific companies and organizations directly, spreading ransomware within internal networks, or demanding monetary compensation after stealing important industrial secrets.
SectorJ09 group carried out a formjacking attack by inserting obfuscated skimming JavaScript into payment pages, in order to steal financial information such as credit card details entered by the targets.
SectorJ25 group was found to be active in Russia, Singapore, Israel, France, and Hong Kong. The group executed shell script malware on Docker containers for malware dissemination purposes. The shell script malware downloaded and executed network scanning tools known as Zrab and Masscan, as well as a backdoor malware on the targeted system. The group ultimately disseminated the CryptoMiner malware and executed it on the targeted systems, attempting to secure financial profit by utilizing the resources of targeted systems to mine cryptocurrency.
SectorJ39 group installed the kernel driver file of Avast, a security software, on the targeted system, then registered it as a service using the Window service control tool command. It was analyzed that they attempted to control the targeted system by terminating processes related to security software using the installed driver file.
SectorJ72 group was found to be active in Peru. The group used DLL format malware which used Onion domains as a C2 server in the process of carrying out malicious activities such as remotely controlling targeted systems.
SectorJ82 group built phishing websites that were similar to corporate domains, and attempted typosquatting attacks to redirect users who make mistakes in URL input when trying to access the company’s page. It is analyzed that the group attempted typosquatting attacks targeting specific corporate domains in order to collect credentials of users related to the company.
SectorJ90 group sent out phishing emails attached with a document file which contained a cloud file. They led the targets into executing the file by adding instructions telling the targets to click on the “Open” button if they wished to download the file from the cloud, and upon clicking the button, a JavaScript malware was downloaded from the command and control (C2) server and executed. The JavaScript malware downloaded additional malware in Windows Installer (MSI) format and executed it. The group ultimately executed JavaScript and Python malware that was analyzed to have the capability to send screenshots of the target system to the command and control server.
SectorJ109 group was found to be active in South Korea and China. The group used phishing sites disguised as commercial software download sites to lead the targets into downloading a malware, and displayed a screen similar to the execution screen of the actual commercial software to prevent the targets from noticing that they have downloaded a malware. The malware disseminated by the group is a Trojan that collected targeted system information or remotely controlled targeted systems.
SectorJ149 group was found to be active in South Korea, Denmark, Russia, Malaysia, the United States of America, Belarus, Ukraine, Canada, Colombia, Panama, Pakistan, and France. The group sent phishing emails disguised as quotation requests and induced the targets to download and execute the attached file. The attached file is a Windows Cabinet (CAB) compressed file, which contains a malware in Visual Basic Script (VBS) format. When the target executed the malware, it downloaded additional malware uploaded to Bitbucket or GitHub using PowerShell commands. The downloaded malware is an image file with Base64-encoded binary inserted using steganography technique, and was decoded through PowerShell commands and executed using the process hollowing technique. The group was analyzed to have attempted to disseminate stealer and remote access malware on the targeted system to carry out malicious activities such as remote control or information theft.
SectorJ165 group used a JavaScript malware with downloader functions to download Bot malware and ransomware on the targeted system and executed them.
SectorJ175 group was found to be active in Italy, Canada and Turkey. The group used the Dragonforce ransomware to secure financial profit and delivered an Onion domain address for discussing financial issues through the ransom note.
SectorJ191 group was found to be active in India. The group targeted on Microsoft SQL server to disseminate CoinMiner malware and the Proxyware malware, which uses the network resources of the targeted system as a third-party proxy and shares it.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
