Monthly Threat Actor Group Intelligence Report, July 2023 (ENG)
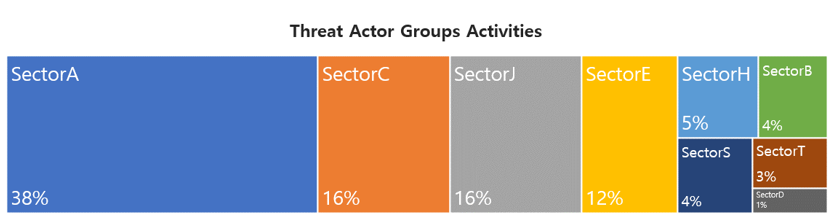
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 June 2023 to 20 July 2023. In July, activities by a total of 25 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 38%, followed by SectorC and SectorJ groups.
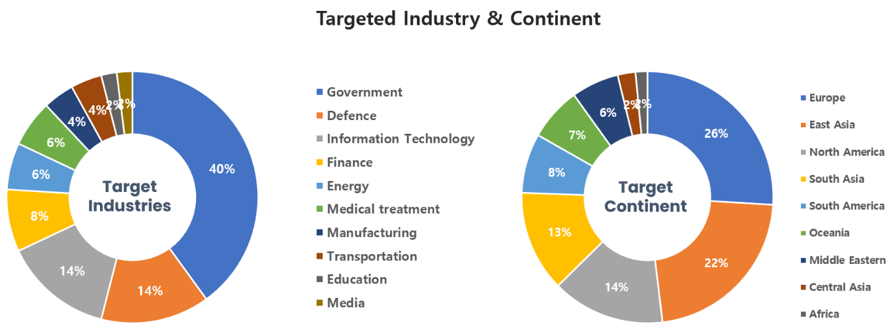
Threat Actors identified in July carried out the highest number of attacks on workers and systems in government agencies and the field of military defense. Regionally, Europe and North America were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In July 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06 and SectorA07 groups
SectorA01 group was found to be active in Czech Republic, China, Germany, and South Korea. The group used malware disguised as the VNC program, a remote access tool. In the final stage, a malware with downloader functions was utilized to download and execute additional malware.
SectorA02 group was found to be active in India, Australia, Germany, South Korea and Singapore. The group used CHM (Compiled HTML Help) format malware disguised as insurance fee transfer guidelines, and PowerShell command was used to download and execute additional malware.
SectorA05 group was found to be active in South Korea, the United States, Australia, and China. The group used MS Word format malware disguised as divorce agreement application forms, which downloaded and executed a VBS (Visual Basic Script) file format malware when the target executed the file.
SectorA06 group was found to be active in South Korea, Japan, Australia, Estonia, the United States, Bulgaria, Singapore, Vietnam, and India. The group targeted on Japanese cryptocurrency exchanges to disseminate Mach-O file format malware. In the final stage, a malware with various functionalities such as system information collection and sending, Python script execution, Shell command execution depending on the command received.
SectorA07 group was found to be active in South Korea. The group disseminated ZIP files containing Windows shortcut (LNK) format malware disguised as taxpayer invoices and used Visual Basic Script and Batch script format files that collected system information in the final stage.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In July 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorB22.
SectorB22 group was found to be active in Myanmar, South Korea, the United Kingdom, India, Russia, Hong Kong, France, Czech Republic, Slovakia, Hungary, Sweden, Ukraine, Chile, Netherlands, and Australia. The group disseminated malware exploiting components of various security solutions, which carried out malicious activities such as file deletion, file creation, process initialization, command execution in the victim’s system, depending on the command received from the C2 server. In addition, the group targeted on ministry of diplomacy and government institutions in Europe to disseminate a remote access malware known as PlugX, which carried out malicious activities such as file collection, keylogging, screen capturing in the targeted system depending on the command received from the C2 server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In July 2023, activities by a total of 4 hacking groups were identified, and the groups were SectorC01, SectorC02, SectorC04 and SectorC08.
SectorC01 group was found to be active in Albania and Ukraine. The group used phishing websites disguised as Ukrainian mail systems and portal sits to lead the targets into accessing the page, and leaked the credential data input from the user when they attempted to log in.
SectorC02 group was found to be active in Ukraine and Bulgaria. The group collected various information in targeted systems and attempted to leak the data using rclone, a cloud storage management tool.
SectorC04 group was found to be active in Ukraine, Uzbekistan, Turkmenistan, Sudan, Kyrgyzstan, Spain, Slovakia, Norway, Netherlands, Libya, Latvia, Kuwait, Ireland, Iraq, Greece, Estonia, Denmark, Cyprus, Canada, Argentina, Albania, Slovenia, the United States, Turkey, Japan, China, Germany, and the United Kingdom. The group sent out phishing emails disguised as official invitations from the Norway Embassy, and used a downloader malware which could download and execute additional malware through a SVG (Scalable Vector Graphics) file format malware.
SectorC08 group was found to be active in Ukraine, the United Kingdom, and Russia. The group used a malware disguised as documents relate to military reservist. In the final stage, the group used UltraVNC, a remote access tool, to attempt information seizure from the victims.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In July 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorD02.
SectorD02 group was found to be active in Israel. The group used a PowerShell script that could decode and encoded data and used a VBS (Visual Basic Script) file format malware with various functionalities such as downloading and executing additional malware or carrying out other PowerShell commands depending on the command received from the attackers.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In July 2023, activities by a total of 4 hacking groups were identified, and the groups were SectorE01, SectorE02, SectorE03 and SectorE05.
SectorE01 group was found to be active in Italy, Singapore, France, the United States, Ireland, Pakistan, Nepal, South Korea, India, the United Kingdom, Netherlands, and China. The group disseminated malware disguised as a VPN software to carry out malicious activities such as collecting system information and anti-virus product details, depending on the command received from the C2 server. In addition, the group targeted on military and political targets in South Asia to disseminate various remote access malwares, which carried out malicious activities such as file download, command execution, and screen capturing in the targeted systems, depending on the command received from the C2 server.
SectorE02 group was found to be active in the United States. The group disseminated MS Word documents disguised as modification and detail requests, which generated and executed a downloader malware to set the base for additional attacks.
SectorE03 group was found to be active in the United States, Israel, Jamaica, Canada, and Tajikistan. The group disseminated Windows shortcut files (LNK) disguised as the Red Book by International Atomic Energy Agency and Nuclear Energy Agency to carry out commands received from the C2 server through malware with reverse shell functionalities.
SectorE05 group was found to be active in India, China, the United States, and Australia. The group disseminated RAR files containing a MS Excel document and a Windows Help (CHM) file disguised as recommendations by Transnational Security Cooperation Workshop, which was used as the foundation for additional attacks by downloading and installing additional malware from external servers.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In July 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorH03.
SectorH03 group was found to be active in Pakistan, Germany, the United States, Australia, India, and the United Kingdom. The group targeted on government institutions and ministry of diplomacy to deliver compressed files (ZIP) containing a Windows shortcut file disguised as a presentation, which collected information such as system information (OS version, system username) and antivirus product details from the victim’s system depending on the command received from the C2 server.
In addition, the group disseminated MS Word documents disguised as school assignments to carry out malicious activities commanded by the C2 server, such as system information seizure, keylogging, and screen capturing, through a malware known as Crimson.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of SectorS Group Activities
In July 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorS01.
SectorS01 group was found to be active in Italy, South Korea, Ecuador, Columbia, Mexico, the United States, and Germany. The group targeted on a precision-machine manufacturing company to disseminate spear phishing emails containing a MS Word document that led the targets to download and install a downloader malware from external server, to set the foundation for additional attacks in the future.
In addition, the group disseminated spear phishing emails containing compressed files (RAR) disguised as payment refunds to lead the targets into downloading and installing a downloader malware from external server, to set the foundation for additional attacks in the future.
SectorS hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
8. Characteristics of SectorT Group Activities
In July 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorT01.
SectorT01 group was found to be active in South Korea, Ukraine, Canada, Poland, and Hong Kong. The group used MS Excel document format malware disguised as tax return forms and attempted to collect information from the targeted system and carry out remote access through njRAT, a remote access tool.
SectorT hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
9. Characteristics of Cyber Crime Group Activities
In July 2023, activities by a total of 7 hacking groups were identified, and the groups were SectorJ05, SectorJ06, SectorJ39, SectorJ45, SectorJ110, SectorJ113 and SectorJ119.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ05 group was found to be active in the United States, Canada, Chile, Germany, Mexico, Turkey, and Singapore. The group gained initial access through exploiting a remote code execution vulnerability (CVE-2022-31199) in Netwrix Auditor, an on-premises and cloud based software, and attempted lateral movement. In the final stage, malware with data leakage properties was used to gain financial profit.
SectorJ06 group was found to be active in Romania, Georgia, Israel, India, Germany, Hong Kong, the United States, Italy, Canada, Egypt, South Korea, Qatar, Poland, Spain, Singapore, France, China, Columbia, Denmark, Lithuania, the United Kingdom, Austria, Japan, and Slovakia. The group targeted on systems exposed to the Microsoft PrintNightmare vulnerability (CVE-2021-34527) and Microsoft MSDT Follina vulnerability (CVE-2022-30190) to disseminate ransomwares.
SectorJ39 group was found to be active in the United States, Ukraine, and Croatia. The group exploited a Zero-Day vulnerability (CVE-2023-36884) and used a MS Word format malware disguised as NATO (North Atlantic Treaty Organization) membership document of Ukraine. In the final stage, a remote access malware was used to collect information from the targeted system and attempt remote access as well as data leakage.
SectorJ45 group was found to be active in Japan, South Korea, China, the United States, and the United Kingdom. The group is known to target on vulnerable MS-SQL server systems to disseminate malwares through an arbitrary PowerShell command and collected system information and carried out crypto mining activities in the final stage.
SectorJ110 group was found to be active in Ukraine, Columbia, and Hungary. The group distributed phishing emails attached with a compressed file containing a VBS (Visual Basic Script) format malware disguised as an invoice. In the final stage, a malware that could download and execute additional malware was used.
SectorJ113 group used the BlackStore ransomware to gain financial profits.
SectorJ119 group was found to be active in Indonesia, Czech Republic, Kazakhstan, Spain, Bangladesh, Greece, Ukraine, Israel, Germany, Saudi Arabia, the United Kingdom, Columbia, Russia, Netherlands, Lithuania, Turkey, the United States, and India. The group used the Big Head Ransomware to gain financial profits.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
