Monthly Threat Actor Group Intelligence Report, June 2024 (ENG)
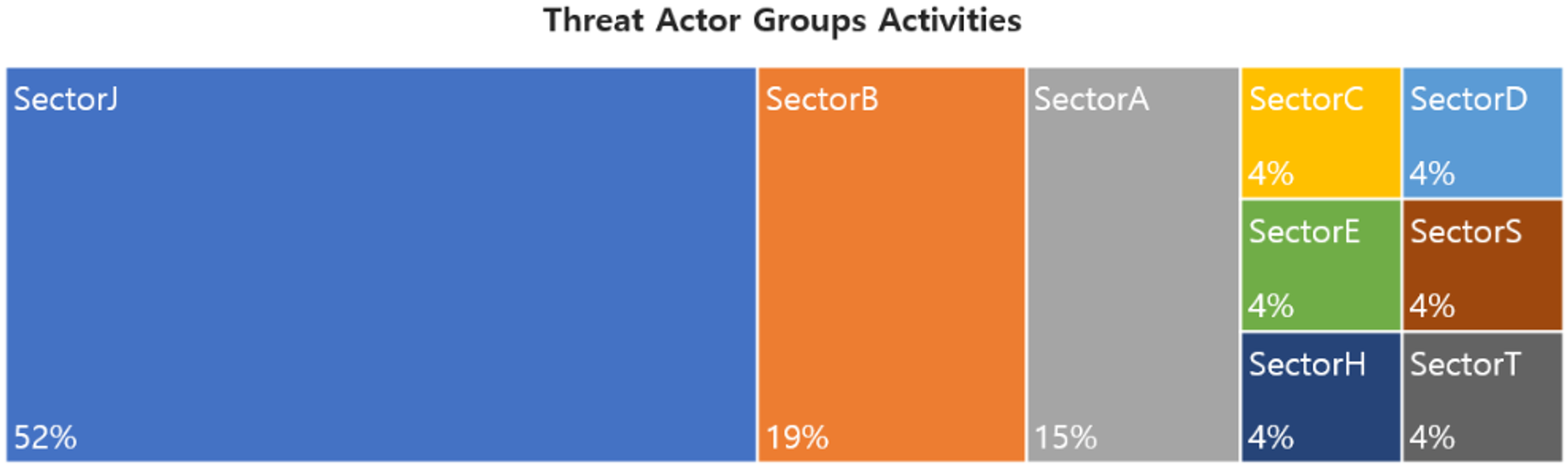
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 May 2024 to 20 June 2024. In June, activities by a total of 27 Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 52%, followed by SectorB and SectorA groups.
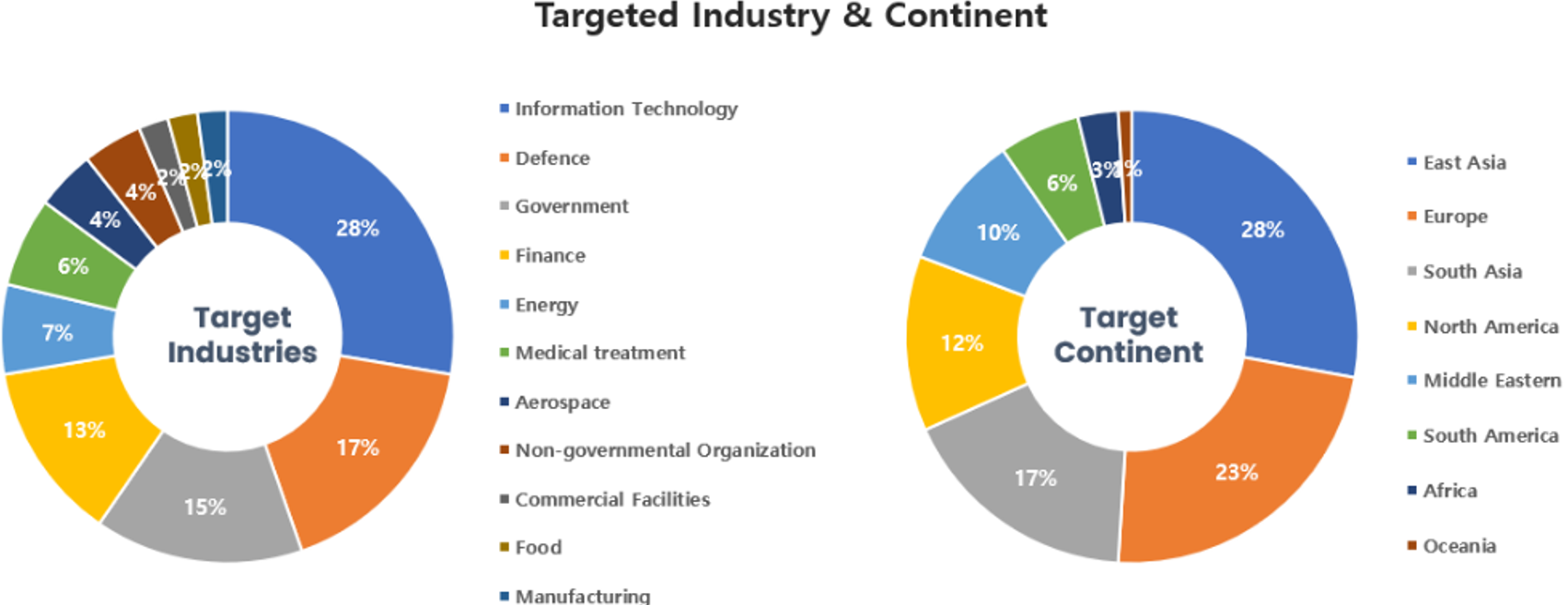
Threat Actors identified in June carried out the highest number of attacks on workers and systems in IT (Information Technology) and the Defense industries. Regionally, East Asia and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In June 2024, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05 and SectorA07 groups.
SectorA01 group was found to be active in Australia, Argentina, Turkey, Israel, Philippines, France, United Arab Emirates, Canada, Honduras, Ukraine, Egypt, China, United States, Pakistan, Romania, Nepal, Sweden, Cyprus, Georgia, Brazil, Russia, and Italy. The group disguised themselves as hiring managers and used compressed files disguised under filenames such as hiring tests and source code review tests, leading the targets to execute the malicious script within the compressed file.
SectorA02 group was found to be active in South Korea. The group used HWP format malware disguised as eligibility verification forms. When the target double clicked the document for editing purposes, OLE (Object Linking and Embedding) was activated and connection to the attacker’s server was attempted.
SectorA05 group was found to be active in South Korea, the United States, Germany, and China. The group attempted to carry out social engineering approaches to military personnels, by disguising themselves as university seniors and juniors to carry out direct conversations and gain trust. Afterwards, they delivered a download link for a compressed file disguised as surveys through messengers and emails. The malware executed in the final stage is a PE (Portable Executable) malware that carries out various malicious activities depending on the command received.
SectorA07 group was found to be active in Estonia, the United States, South Korea and Germany. The group used Windows shortcut (LNK) format malware disguised as scholarship application forms, and when the target executed the malware, additional malware developed using AutoIt was downloaded and executed for further malicious activities.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In June, activities by a total of 5 hacking groups were identified, and the groups were SectorB04, SectorB22, SectorB38, SectorB72, and SectorB99 groups.
SectorB04 group was found to be active in Mongolia and Japan. The group carried out malicious activities through spear phishing emails containing malware hosted on GeoCities Japan website. A PowerShell Module known as PowerSploit was executed to load a remote access malware known as Poison Ivy into memory, which carried out various malicious activities depending on the command received from the C2 server.
SectorB22 group was found to be active in South Korea and Vietnam. The group sent out spear phishing emails attached with a compressed file (RAR) which contained a Windows LNK file disguised as the tax compliance guide document. A malicious DLL was executed through DLL sideloading to download an encoded data file from the C2 server, which was decoded to execute Shellcode from the memory to encrypt the MAC address of the targeted system and send it to the C2 server.
SectorB38 group was found to be active in Malaysia, the Philippines, Singapore, the United States, and Taiwan. The group used government infrastructure that was previously compromised to send out RTF documents exploiting the Equation Editor vulnerability in Microsoft Office to other government institutions. They downloaded a penetration testing tool known as Cobalt Strike on the targeted system and executed it to carry out various malicious activities depending on the command received from the C2 server.
SectorB72 group was found to be active in Taiwan, Germany, Nigeria, Arab Emirates, and Hong Kong. The group targeted on government institutions and used various attack tools for their activities. The Microsoft Exchange Server vulnerability was exploited for initial access, and the group collected sensitive data from the target’s mail server by utilizing keywords related to the government, diplomacy, and military.
SectorB99 group was found to be active in the Philippines and Japan. The group targeted on government and military organizations to distribute variants of a remote access malware known as Gh0st RAT, and carried out activities such as keylogging browser data stealer, windows portable devices and USB monitoring to collect information and send it to the C2 server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In June, activities by a total of 1 hacking groups were identified, and the group was SectorC08 group.
SectorC08 group was found to be active in Russia and Armenia. The group used Windows PE (portable executable) format malware disguised as documents related to the military, and ultimately attempted to steal information using UltraVNC, a remote access tool.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In June 2024, activities by a total of 1 hacking groups were identified, and the group was SectorD02 group.
SectorD02 group was found to be active in Saudi Arabia, Kenya, Israel, Azerbaijan, Jordan, and Turkey. The group used a bait document on invitations to a web seminar, which contained a phishing link within it, and ultimately used a malware with data collection and remote access functionalities.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In June 2024, activities by a total of 1 hacking groups were identified, and the group was SectorE05.
SectorE05 group was found to be active in Pakistan and Hong Kong. The group distributed PUB (Microsoft Publisher) files disguised as board meetings to carry out their attacks, by using the file to collect computer name and username and sending them to the C2 server, then downloading and executing additional malware to lay the groundwork for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In June 2024, activities by a total of 1 hacking groups were identified, and the group was SectorH03 group.
SectorH03 group was found to be active in India, Pakistan, Japan, Brunei, Lithuania, Saudi Arabia, Bangladesh, the United States, Thailand, Singapore, and Canada. The group distributed Microsoft Excel document disguised as university courses to carry out their attacks, and used a remote access malware known as Crimson RAT to carry out various malicious activities depending on the command received from the C2 server. In addition, the group distributed Microsoft Excel documents disguised as design documents and claim summary documents using the same method, also using Crimson RAT to carry out various malicious activities depending on the command received from the C2 server.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of SectorS Group Activities
In June 2024, activities by a total of 1 hacking groups were identified, and the group was SectorS01 group.
SectorS01 group was found to be active in Columbia. The group targeted on government institutions to deliver spear phishing emails attached with ZIP files containing the IObit Anti-malware solution. Using the malware known as AsyncRAT, the group performed various malicious actions according to commands received from the C2 server on the targeted systems.
SectorS hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
8. Characteristics of SectorT Group Activities
In June 2024, activities by a total of 1 hacking groups were identified, and the group was the SectorT01 group.
SectorT01 group was found to be active in Germany. The group used Microsoft Excel document format malware disguised as a military supply request from the Ministry of Defense to lead the targets into executing the malware.
SectorT hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
9. Characteristics of Cyber Crime Group Activities
In June 2024, activities by a total of 12 hacking groups were identified, and the groups were SectorJ09, SectorJ25, SectorJ57, SectorJ93, SectorJ94, SectorJ110, SectorJ177, SectorJ178, SectorJ179, SectorJ180, SectorJ181, and SectorJ185.
Unlike other government-supported hacking groups, these groups steal online information with tangible value that can secure monetary gains in the real world, or they hack specific companies and organizations directly, spreading ransomware within internal networks, or demanding monetary compensation after stealing important industrial secrets.
SectorJ09 group carried out a form jacking attack on CMS (Content Management System), a type of attack that steals the credential information entered by users, specifically by inserting obfuscated scripts that capture payment information into some files of WooCommerce, one of the e-commerce plugins for WordPress.
SectorJ25 group used the Bash malware for cryptojacking, and the Bash malware used by the group was identified to have modified system settings to collect system information and carry out cryptomining attacks.
SectorJ57 group was found to be active in the United States, Spain, Italy, and Canada. The group used a phishing email containing a malicious URL to disseminate ransomwares. When the target clicked on the URL attached to the phishing email, a compressed file containing a VBS (Visual Basic Script) file was downloaded. When the target executed the Visual Basic Script, a DLL file that could download additional malware was downloaded onto the system, which was used by the group to disseminate ransomware.
SectorJ93 group used a phishing page disguised as a fake browser update website to lead the targets into downloading the malware being distributed in the phishing page. When the target clicked on the button to download malware, a JavaScript malware disguised under the name of a Chrome Update was downloaded, which then downloaded a Bot malware from the C2 server through PowerShell.
SectorJ94 group was found to have used Bot malware to steal data from targeted systems. The group encrypted the traffic using the RC4 algorithm, and used HTTP protocol to send the stolen data to the C2 server.
SectorJ110 group was found to be active in the Netherlands and Ukraine. The group sent out phishing emails attached with a compressed file containing malware by impersonating the finance department. When the target clicked on the ACCDB (Windows Access Database File) in the compressed file, a table attached with an image file that would prompt the target to click the “Enable Content” button was shown. Clicking on the button executed the Visual Basic Script attached to the document, and additional malware was downloaded.
SectorJ177 group was found to be active in Germany, Russia, and the United States. The group exploited the Privilege Management Vulnerability in Microsoft Windows Error Reporting Service (CVE-2024-26169) in their attacks using Exploit Tool, and the vulnerability was used to disseminate and execute the Black Basta Ransomware.
SectorJ178 gorup was found to be active in the United States, Spain, China, and Cambodia. The group used malware disguised as Tiworker.exe, the Windows Integrity check program, which executed a PowerShell to download additional malware from the C2 server. The downloaded malware disables Windows Defender and creates a task scheduler to continuously mine cryptocurrency on the targeted system.
SectorJ179 group used the leaked credentials of users of Snowflake, a data platform, to approach Snowflake instances and steal data.
SectorJ180 group sent out phishing emails disguised with contents related to recruitments, which contained a link that seemed like a legitimate webpage to induce the target to click on it. When the target accessed the attached URL, they were prompted to download a document disguised as CAPTCHA (CAPTCHA). Once downloaded, an obfuscated JavaScript file is downloaded to the target system. The JavaScript file also downloads a DLL file that communicates with the C2 server, and utilizes a task scheduler and Component Object Model (COM) object to continue operating.
SectorJ181 group was found to be active in Brazil and Chile. The group used a Cloud platform to disseminate Stealer malware, by distributing compressed files containing a Windows shortcut (LNK) file and a Base64 encoded file disguised as a JPG extension through the Cloud platform. The group was seen to have used this method to steal data from targeted systems using the disseminated stealer malware.
SectorJ185 group was found to be active in Nigeria, the United States, Ukraine, India, China, and Hong Kong. The group used compressed files disguised as resumes to distribute malware. The compressed file contained a Windows shortcut (LNK) file, which executed a bait PDF document while generating DLL data encoded within the LNK file in the TEMP path when executed. The decoded DLL format PE file loaded the Pupy RAT on memory, which carried out various activities such as system information collection and keylogging depending on the command received from the C2 server.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
