Monthly Threat Actor Group Intelligence Report, August 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 July 2024 to 20 August 2024.
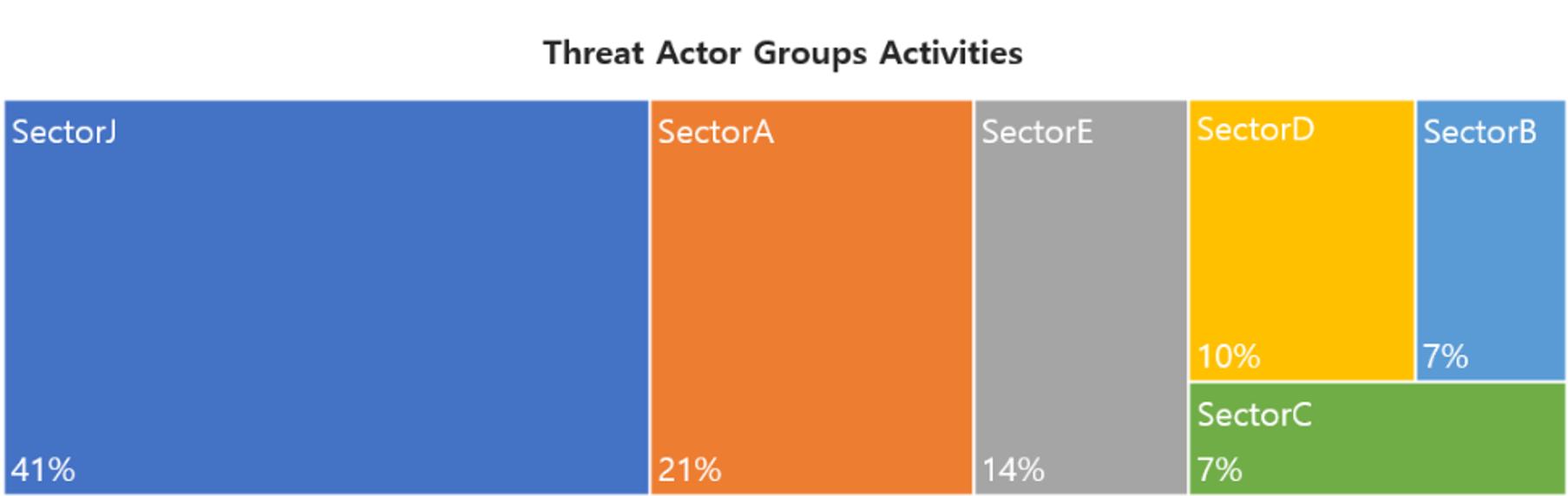
In August, activities by a total of 29 Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 41%, followed by SectorA and SectorE groups.
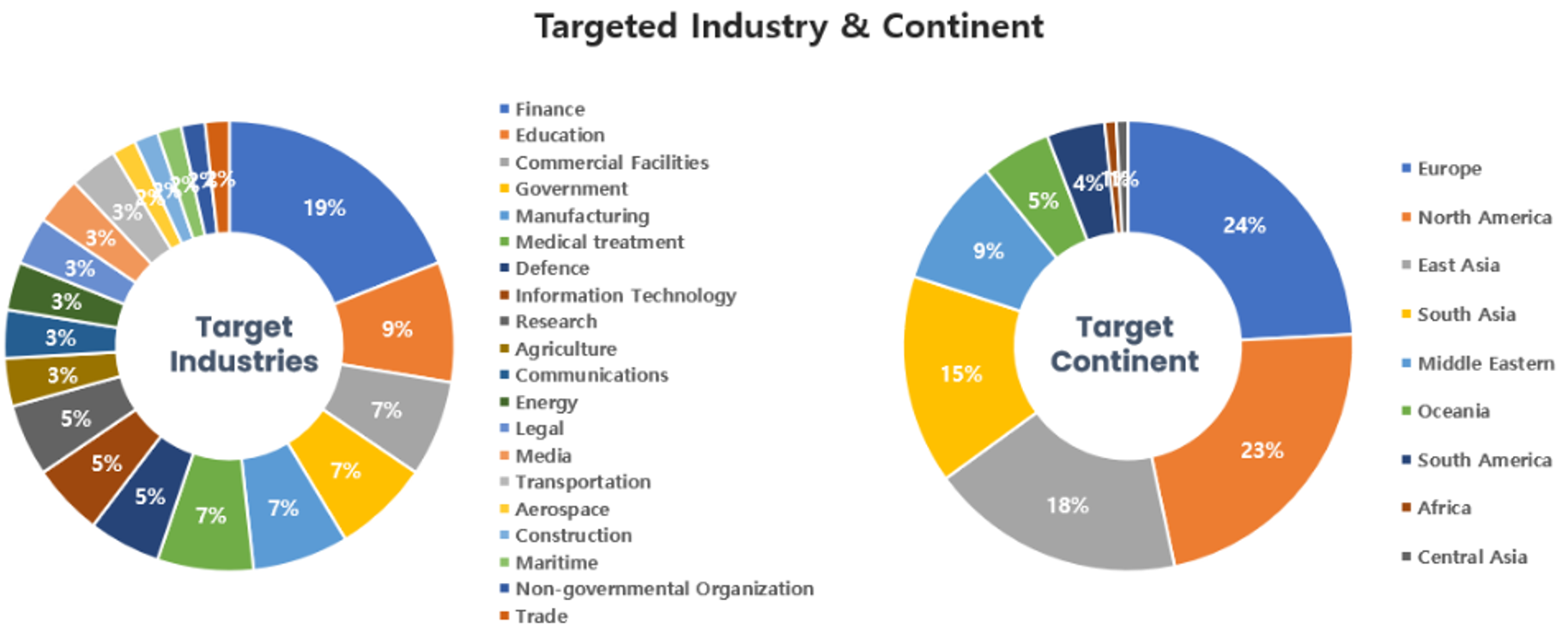
Threat Actors identified in August carried out the highest number of attacks on workers and systems in the finance and educational industries. Regionally, Europe and North America were seen as the regions with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In August 2024, activities by a total of 6 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA04, SectorA05, SectorA06 and SectorA07 groups.
SectorA01 group was found to be active in Serbia, India, Belgium, Pakistan, Jamaica, Turkey, Singapore, Romania, Malaysia, Finland, Israel, Russia, Canada, United States, Argentina, Australia, China, France, Colombia, Slovenia, United Kingdom, Estonia, Bangladesh, Vietnam, Norway, Indonesia, Japan, United Arab Emirates, Hong Kong, Spain, Croatia, Ukraine, Tunisia, Brazil, Mexico, Kazakhstan, Italy, Germany, and the Philippines. The group disguised themselves as hiring managers to use compressed files disguised under filenames such as hiring tests and source code review tests, leading the targets to execute the malicious script within the compressed file.
SectorA02 group was found to be active in South Korea. The group disseminated a Script malware that exploited an unknown vulnerability in the Microsoft Windows Scripting Engine.
SectorA04 group was found to be active in Japan, the United States, Russia, and South Korea. The group distributed malware that exploited unknown vulnerabilities in vaccine software management systems to collect system and network access information.
SectorA05 group was found to be active in South Korea, the United States, China, Australia, Mongolia, and Italy. The group used malware in the form of a CHM (Microsoft Compiled HTML Help) file disguised as a National Assembly schedule notice, and ultimately executed DLL malware that used DLL side-loading technique to carry out command and control functions using a legitimate software.
SectorA06 group was found to be active in France, Armenia, the United States, and the United Kingdom. The group targeted users of macOS involved in cryptocurrency to use Mach-O malware disguised as documents related to Bitcoin prices. Mach-O malware carried out the function of downloading and executing additional malware from attack servers.
SectorA07 group was found to be active in South Korea and Canada. The group used Windows shortcut (LNK) malware disguised as documents requesting updates on cryptocurrency related projects. When the target executed the malware, ultimately, a Visual Basic Script and Batch Script format malware are executed to collect information and download and execute additional malware.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In August, activities by a total of 2 hacking groups were identified, and the groups were SectorB01 and SectorB22 groups.
SectorB01 group was found to be active in Germany, United Arab Emirates, Qatar, Georgia, Italy, Taiwan, Romania, and Thailand. The group distributed an open-source web shell known as Godzilla to the targeted systems and installed a backdoor through the web shell. The group then carried out malicious activities such as downloading and uploading files, screen capturing, and registry manipulation according to commands received from the command and control (C2) server through the backdoor installed on the targeted systems.
SectorB22 group was found to be active in in the United States and Hungary. The group distributed malicious Windows installer (MSI) files disguised as meeting invitation documents to carry out their attacks. Using a malware known as PlugX, the group was able to remotely control the targeted systems and perform malicious actions such as collecting system information, key logging, and screen capture, based on commands received from the command and control (C2) server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In August, activities by a total of 2 hacking groups were identified, and the group were SectorC01 and SectorC08 groups.
SectorC01 group was found to be active in Armenia. The group used Microsoft Word format malware disguised under contents related to policies of the Ministry of Defense to lead the targets into directly executing the malware. Ultimately, the group used a VBS script that downloaded additional VBS script from the attacker server and executed it.
SectorC08 group was found to be active in Ukraine. The group used HTML (Hypertext Markup Language) format malware that intentionally caused image loading errors, and used the onerror function that is executed during errors to execute an obfuscated code with malicious purposes.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In August 2024, activities by a total of 3 hacking groups were identified, and the group were SectorD02, SectorD05, and SectorD30 groups.
SectorD02 group was found to be active in Sweden, the United States, Ukraine, Poland, India, and Israel. The group used MSI (Windows Installer) malware disguised as web seminar materials in their attacks, and ultimately used a commercial remote access tool known as Atera to attempt remote control of the targeted system.
SectorD05 group was found to be active in Lebanon. The group used malware written in Golang that was disguised as a program related to Microsoft SQL server, which carried out file system manipulation and internal propagation through network by receiving commands from the attack server.
SectorD30 group was found to be active in the United States, Iran, Australia, Israel, and the United Kingdom. The group used Microsoft Word malware containing macro, which enabled the VBA script to download and execute Batch script format malware. The group ultimately used PE malware with target system information collection and credential stealing capabilities.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In August 2024, activities by a total of 4 hacking groups were identified, and the group were SectorE01, SectorE02, SectorE04, and SectorE05 groups.
SectorE01 group was found to be active in Germany and the United Kingdom. The group distributed a downloader malware disguised as a Microsoft Word document icon to carry out their attacks. Through the downloader malware installed on the targeted systems, the group downloaded and executed a screen capture malware and a file collection malware, which collected system information and sent it to a command and control (C2) server.
SectorE02 group was found to be active in in Japan, China, Canada, and Sri Lanka. The group distributed ZIP compressed files containing malicious Windows shortcut (LNK) files disguised as technology innovation forum documents to carry out their attacks. In addition, the group used the malicious Windows shortcut (LNK) file installed in the targeted system to download malware with downloader properties, in order to download additional malware to set the foundation for future attacks.
SectorE04 group was found to be active in the United States, Egypt, Pakistan, Netherlands, Sri Lanka, Bangladesh, Myanmar, Nepal, and Maldives. The group targeted maritime organizations to carry out spear phishing email attacks. The group utilized a Microsoft Word document attachment containing personal information of high-ranking military officials to exploit vulnerabilities in the targeted systems and execute a shellcode to collect system information and download additional malware for future attacks.
SectorE05 group was found to be active in Belgium, Bangladesh, Singapore, Pakistan, China, USA, Hong Kong, and Israel. The group distributed Adobe PDF documents on requests to reviewing policy changes to carry out their attacks. The group led the targets into clicking on the malicious link included within the Adobe PDF document, and used the malicious Windows Help (CHM) file downloaded through the link to collect computer name and username of the targeted system and sent it to the C2 server. In addition, additional malware was downloaded and executed to set the foundation for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorT Group Activities
In August 2024, activities by a total of 1 hacking groups were identified, and the group was SectorT01 group.
SectorT01 group was found to be active in Ukraine. The group used Microsoft Excel file format malware disguised as tax declaration forms to lead the targets into executing the malware by themselves.
SectorT hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
7. Characteristics of Cyber Crime Group Activities
In August 2024, activities by a total of 11 hacking groups were identified, and the groups were SectorJ01, SectorJ09, SectorJ22, SectorJ57, SectorJ61, SectorJ64, SectorJ94, SectorJ113, SectorJ177, SectorJ185, and SectorJ188.
Unlike other government-supported hacking groups, these groups steal online information with tangible value that can secure monetary gains in the real world, or they hack specific companies and organizations directly, spreading ransomware within internal networks, or demanding monetary compensation after stealing important industrial secrets.
SectorJ01 group was found to be active in Russia and the United States. The group distributed malware in the form of Microsoft App Package Files (MicrosoftIX) through phishing pages disguised as commercial program homepages. The group is believed to have ultimately executed a remote control malware known as NetSupport on the targeted systems, in order to control them remotely and carry out malicious commands.
SectorJ09 group carried out a formjacking attack by using obfuscated skimming JavaScript to steal financial information entered by the target on payment pages.
SectorJ22 group was found to be active in Russia. The group spread malicious links through phishing emails, inducing the targets to download the compressed file being distributed within the malicious link. The compressed file contained a Windows shortcut (LNK) file that downloads and executes a JavaScript loader malware upon execution. It is believed that the group intended to download and execute JavaScript malware on the targeted systems through the JavaScript loader from the command and control (C2) server.
SectorJ57 group was found to be active in the Netherlands, Germany, the United States, Estonia, and Canada. Through phishing emails, the group disseminated HTML files disguised as the error page of Microsoft OneDrive, leading the targets into clicking the button for downloading JavaScript. JavaScript carried out the functions of downloading and executing Autoit program and the Autoit script files on the targeted system.
SectorJ61 group was found to be active in Germany, Russia, Romania, Vietnam, Belarus, Bulgaria, Albania, Ukraine, Italy, Georgia, Turkey, and South Korea. The group sent out phishing emails on payment invoices, and attached a malicious document file within the email. When the target executed the document file, the macro embedded within the document was activated, and carries out communication with the image file path of an external server. The image file contained malware hidden through the Steganography technique, and the remote access malware known as Remcos was executed, attempting to carry out various malicious activities depending on the command received from the Command and Control (C2) server.
SectorJ64 group was found to be active in Mexico, the United States, Turkey, and Hong Kong. The group distributed malware through PowerShell scripts for cryptocurrency mining. When the PowerShell script is executed, the data encoded in Base64 that was defined as a variable within the PowerShell script is decoded. The decoded data is a EXE file that downloads DLL malware from the command and control (C2) server. The DLL malware loads the XMRig payload in the “AddInProcess.exe” process, then carries out cryptocurrency mining.
SectorJ94 group was found to be active in Germany, Russia, the United States, and Italy. The group disseminated JavaScript malware that downloaded and executed DLL malware known as DanaBot on the targeted system. The group was seen to have attempted to collect system information from the targeted system for sending them to the command and control (C2) server.
SectorJ113 group was found to be active in Brazil, Poland, and Hong Kong. The group used the RA World ransomware to secure financial profit, and used a ransom note to deliver the means of communication for discussing the financial issue.
SectorJ177 group was found to be active in Denmark, Germany, the United States, Singapore, Italy, Poland, and South Korea. The group used the Black Basta ransomware to secure financial profit.
SectorJ185 group was found to be active in Russia, the United States, and China. The group distributed compressed files containing Windows shortcut (LNK) files for their attack. When the target executed the shortcut file, a DLL format malware was dropped in the targeted system, and was executed through the DLL side-loading technique. The DLL malware opened a decoy PDF document to prevent the target from noticing the execution of the malware, and loaded the Pupy RAT, a remote access malware, in order to perform various functions such as system information collection and keylogging depending on the command received from the command and control (C2) server.
SectorJ188 group was found to be active in Italy and Kuwait. The group used phishing emails to disseminate remote access malware (RAT) to the targeted systems, in an attempt to carry out various malicious remote control activities on the targeted system.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
