Monthly Threat Actor Group Intelligence Report, December 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC Threat Research Lab based on data and information collected from 21 November 2024 to 20 December 2024.
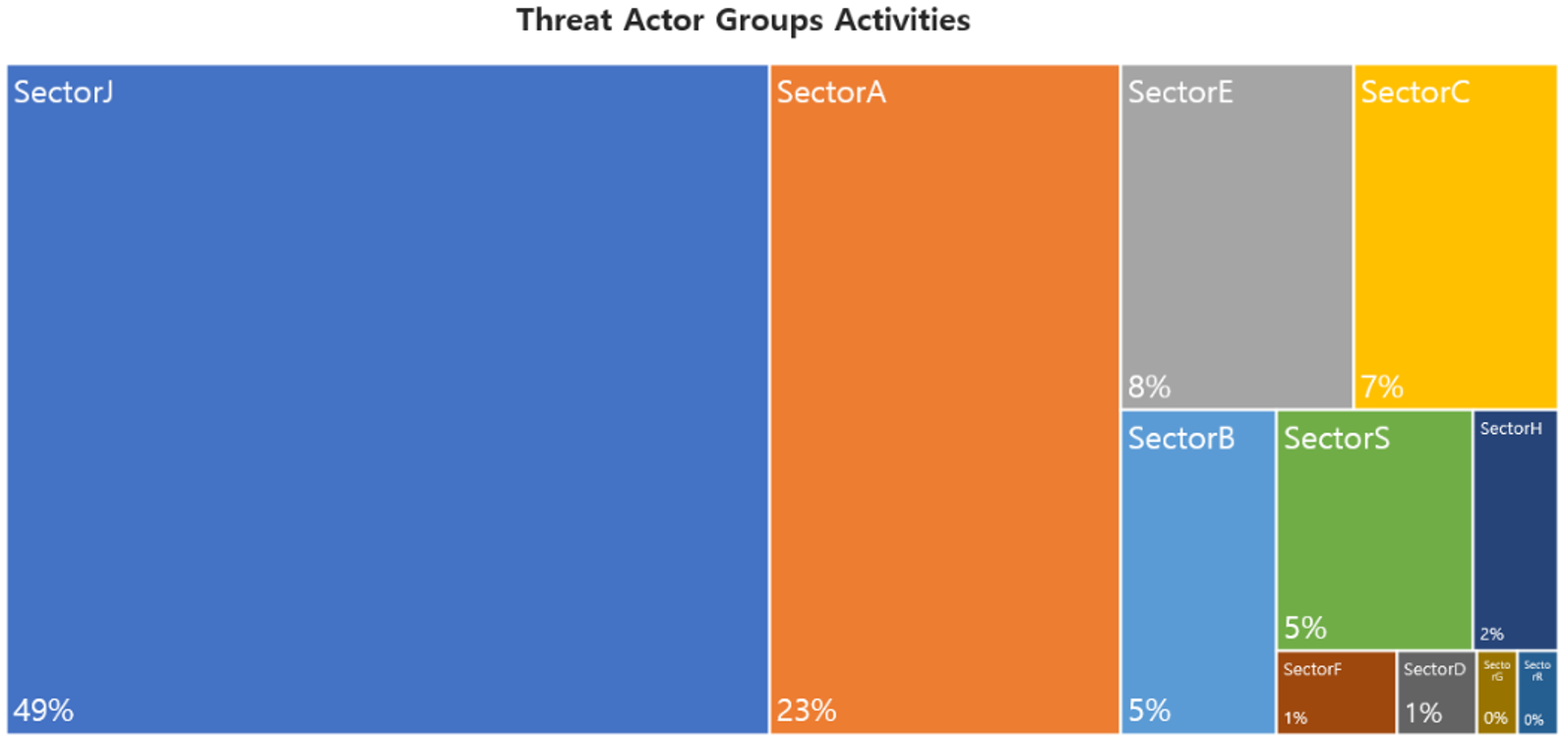
In December, activities by a total of 65 Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 49%, followed by SectorA and SectorE groups.
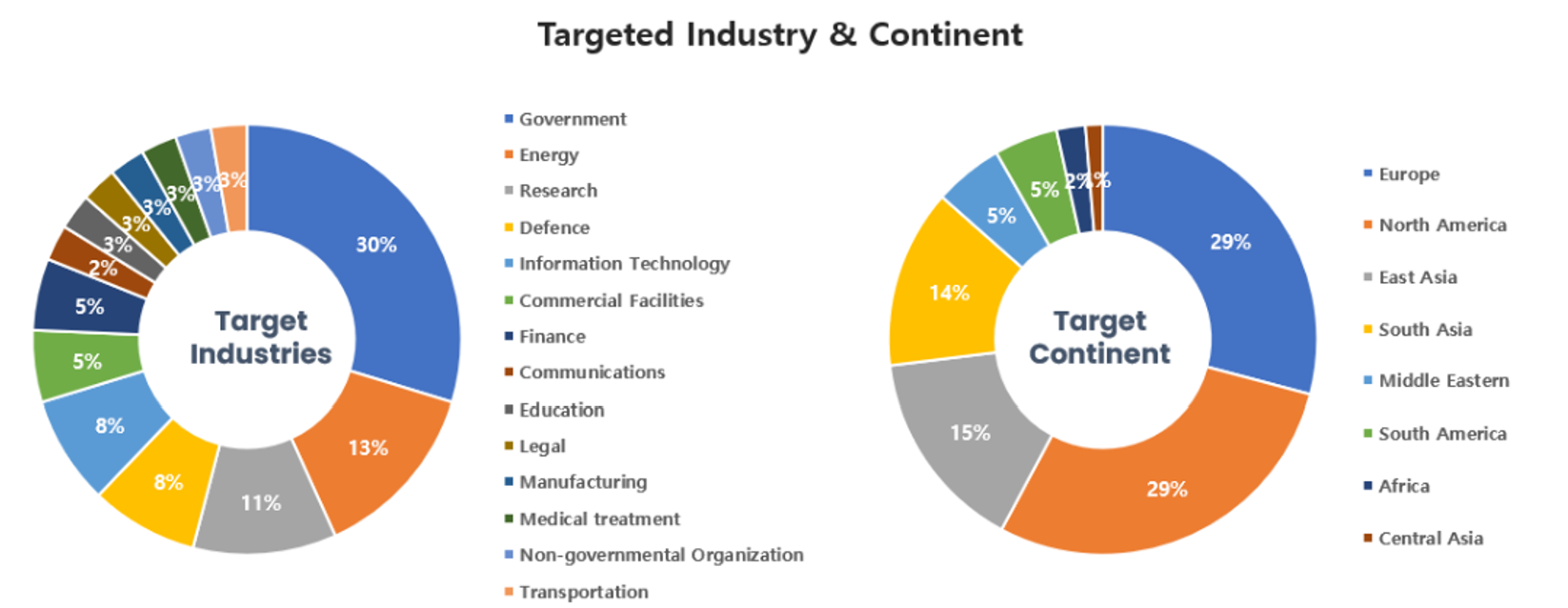
Threat Actors identified in December carried out the highest number of attacks on workers and systems in government institutions and the energy industry. Regionally, Europe and North America were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In December 2024, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, and SectorA07.
SectorA01 group was found to be active in South Korea. The group impersonated hiring managers on platforms such as LinkedIn to approach potential victims by providing fake employment opportunities. The final malware used by the group communicated with the command and control (C2) to download additional payload or leak sensitive data.
SectorA02 group was found to be active in South Korea. The group used a malware in the form of a Windows shortcut (LNK) file named “Kim kuk-sung Lecture Materials”. They ultimately attempted to use backdoor malware to steal files according to the attacker’s command, and use cloud services such as pCloud and Yandex to transmit the data to the attacker’s cloud server.
SectorA05 group was found to be active in South Korea. The group attempted to steal the email accounts and password of Naver, a South Korean portal website, by luring users to a phishing website disguised as the login page of Naver.
SectorA07 group was found to be active in Russia and South Korea. The group used malware disguised as a financial transaction confirmation document in the form of a CHM (Compiled HTML Help) file, and ultimately downloaded additional batch script malware from the attacker and executed it through a PowerShell command.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In December 2024, activities by a total of 4 hacking groups were identified, and the groups were SectorB01, SectorB22, SectorB91, and SectorB107.
SectorB01 group was found to be active in Greece, Germany, the Philippines, Taiwan, Malaysia, South Africa, the United States, Afghanistan, Brazil, Eswatini, India, Indonesia, Pakistan, Thailand, and Vietnam. The group targeted on government institutions, NGO (non-governmental organization), communication, technology, and consulting industries for their attack. They exploited N-Day vulnerabilities in various publicly available servers of the targeted systems to gain initial access. Then, the group distributed additional malware and carried out long-term spy activities.
SectorB22 group was found to be active in France, Taiwan, the United Kingdom, Singapore, the Philippines, Chile, and South Korea. The group exploited unknown vulnerabilities in the targeted systems to gain initial access and installed various web shells, ultimately installing a Linux backdoor to steal sensitive information.
SectorB91 group was found to be active in Japan. The group targeted on individuals and organizations in Japan to distribute spear phishing emails. They ultimately used malware installed on the systems to collect information of the infected systems. In addition, the group installed additional malware on the targeted system that carried out malicious activities according to the command received from the Command and Control (C2) server.
SectorB107 group was found to be active in the United States and China. The group utilized an exploit kit, which automatically exploits vulnerabilities to distribute malware, to target Android and Windows platforms. Ultimately, they were able to remotely control the targeted systems and collect sensitive information through the installed backdoor.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In December 2024, activities by a total of 7 hacking groups were identified, and the group were SectorC01, SectorC02, SectorC04, SectorC05, SectorC08, SectorC13, and SectorC24 groups.
SectorC01 group was found to be active in Armenia, China, Greece, Hungary, India, Kazakhstan, Kyrgyzstan, Tajikistan, Turkmenistan, Ukraine, and Uzbekistan. The group attempted initial access through phishing emails and social engineering techniques, and after successful penetration, they installed backdoors using customized malware and maintained long-term access to collect sensitive data continuously.
SectorC02 group was found to be active in Ukraine, Netherlands, Pakistan, the United States, Sweden, and Afghanistan. The group carried out hacking activities by compromising the command and control (C2) infrastructure of other hacking groups and distributing their own malware. They also used tools and infrastructure of other hacking groups to conceal their activities and evade detection.
SectorC04 group was found to be active in Czech Republic. The group primarily targeted the Czech government and military organizations, distributing malicious RDP (Remote Desktop Protocol) configuration files to their victims through phishing emails. The targets who executed the malicious RDP configuration file were connected to an RDP relay server controlled by the attackers, providing a platform for leaking sensitive data or installing additional malware.
SectorC05 group was found to be active in Ukraine, Germany, the United States, and Slovakia. The group used a bait PDF document about the agenda of an international military helicopter conference, and induced the targets to execute a malware in the form of a Windows shortcut (LNK) file that was disguised as a registration form. The Visual Basic Script (VBS) malware used in the final step was used as a backdoor malware that executed additional commands received through PowerShell commands.
SectorC08 group was found to be active in Hong Kong, Netherlands, Tajikistan, Uzbekistan, Syria, Kazakhstan, the United Kingdom, Germany, the United States, Kyrgyzstan, Poland, United Arab Emirates, Turkey, Ukraine, and Slovakia. The group sent out phishing emails containing details on court notice, attached with a RAR compressed file. When the target executed the HTA (HTML Application) format malware included in the compressed file, a Visual Basic Script (VBS) that was designed to download and execute addition HTA malware was executed.
SectorC13 group was found to be active in Russia and Belarus. The group sent out phishing emails impersonating government agencies, and attached a malicious Word document to the email, which used the template injection technique.
SectorC24 group was found to be active in Pakistan and Russia. The group created a phishing website imitating the official website of the “Армія+” application. They used an installation program containing a malicious PowerShell script to install an OpenSSH server, secured remote access permissions, and set up SSH services through the Tor network, providing a means to remotely access targeted systems.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In December 2024, activities by a total of 1 hacking groups were identified, and the group was SectorD37.
SectorD37 group was found to be active in the United States and Israel. After the group successfully infiltrated targeted systems using supply chain attacks and phishing emails, they used malware specialized in IoT (Internet of Things) and OT (Operational Technology) environments. The malware used by the group used the MQTT (Message queuing Telemetry Transport) protocol to communicate with the attacker server, and some of the main functions of the malware included fuel service disruption, data stealing, and inducing malfunctioning of equipment.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In December 2024, activities by a total of 5 hacking groups were identified, and the group were SectorE01, SectorE02, SectorE04, SectorE05, and SectorE08.
SectorE01 group was found to be active in Pakistan, China, Hong Kong, India, the United States, Kazakhstan, the United Kingdom, Turkey, Sweden, Poland, Vietnam, Czech Republic, Ukraine, Chile, Germany, Finland, Russia, Bulgaria, Belgium, Brazil, Indonesia, France, Switzerland, Thailand, Georgia, Singapore, and Egypt. The group distributed Windows shortcut (LNK) files disguised as project guideline proposals to carry out their attacks, and ultimately set up the foundation for future attacks by downloading additional malware through commands registered in the task scheduler of the targeted system.
SectorE02 group was found to be active in Pakistan. The group distributed an Android app disguised as a file named “New Delegation Details” to carry out their attacks, and ultimately used the installed Android app to carry out the malicious act of collecting SMS messages, contacts, and phone call history.
SectorE04 group was found to be active in Sri Lanka and Nepal. The group distributed Microsoft Word documents disguised as medical aid application forms to carry out their attacks. They ultimately downloaded and executed remote template document files through the distributed Word documents, laying the groundwork for subsequent attacks.
SectorE05 group was found to be active in Malaysia, China, Sweden, South Korea, the United Kingdom, Finland, Pakistan, and India. The group distributed MSC (Microsoft Management Console Snap-in Control) file disguised under the filename of “Education department” to carry out their attacks. The group ultimately used a system command included in the distributed MSC file to register a task scheduler, which sent the computer name and username of the targeted system to a command and control (C2) server, then set the foundation for future attacks by downloading and executing additional malware.
SectorE08 group was found to be active in Pakistan, Canada, Bangladesh, and Iran. The group distributed compressed files exploiting the WinRAR code execution vulnerability (CVE-2023-38831) from RARLAB. The group ultimately used the installed malware to execute commands received from the command and control (C2) server to carry out malicious activities.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In December 2024, activities by a total of 1 hacking groups were identified, and the group was SectorH03 group.
SectorH03 group was found to be active in India and Spain. The group distributed an Adobe PDF document under the filename of “Ministry of Defense Minister’s Meeting”, which contained a link that prompted the targets to log in with their email accounts, then led them to download a PDF document from the link. When the target clicked on the provided link, they were redirected to a phishing website disguised as an Indian government website created by the hacking group. The email account information was collected to set the foundation for future attacks.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of SectorR Group Activities
In December 2024, activities by a total of 1 hacking groups were identified, and the group was SectorR01.
SectorR01 group was found to be active in China. The group created a phishing page imitating the official website of a Chinese civil aviation company for their attacks. They inserted a malicious script into the website which was designed to automatically download a malicious file when the target accessed the website. The malicious file served the function of loading Sliver RAT and executing it.
SectorR hacking groups are aimed at collecting high-level information on government activities, including political, diplomatic and military activities involving the China, which is in rivalry with countries that support SectorR.
8. Characteristics of SectorS Group Activities
In December 2024, activities by a total of 1 hacking groups were identified, and the group was SectorS01 group.
SectorS01 group was found to be active in Columbia. The group distributed RARLAB’s WinRAR decompression library with malware inserted for their attacks, but the file was determined to be a test file for which normal operation is not possible due to an incorrect code patch. If the group had distributed the WinRAR decompression library with the code patch with a correct address to ensure normal operation, malicious activities would have been carried out according to the commands received from the command and control (C2) server.
SectorS hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
9. Characteristics of Cyber Crime Group Activities
In December 2024, activities by a total of 10 hacking groups were identified, and the groups were SectorJ09, SectorJ14, SectorJ25, SectorJ39, SectorJ47, SectorJ93, SectorJ115, SectorJ135, SectorJ149, and SectorJ194.
Unlike other government-supported hacking groups, these groups steal online information with tangible value that can secure monetary gains in the real world, or they hack specific companies and organizations directly, spreading ransomware within internal networks, or demanding monetary compensation after stealing important industrial secrets.
SectorJ09 group carried out a formjacking attack by inserting a skimming script on an online payment page to steal financial information. The group injected obfuscated malicious JavaScript code into the payment page of an e-commerce website, and was deduced to have stolen sensitive financial data such as card numbers, expiration dates, and CVC codes entered by the victims.
SectorJ14 group sent text messages containing shortened Twitter URLs to their targets, attempting to lead them into clicking the links. When the target clicked the shortened URL, they were redirected to a phishing page disguised as an Apple login page. The attack was analyzed as an attempt to steal the Apple credentials entered by the target.
SectorJ25 group was found to be active in South Korea and Croatia. The group disseminated an obfuscated Shell script format malware onto the targeted systems, and the script file served the function of downloading additional malware onto the targeted system. The malware installed by the hacking group were Diamorphine Rootkit, which has its source code publicly available on GitHub, and XMRig, which is used in cryptomining. The group used the rootkit to evade detection and ultimately performed cryptocurrency mining through XMRig in order to gain financial profit.
SectorJ39 group was found to be active in Germany, the United States, and Ukraine. The group built a phishing website that redirected targets who accessed the website to an Exploit hosting server where a specific vulnerability could be executed. The group took exploited the vulnerability hosted on the server to execute a Shellcode that downloads and executes a backdoor malware known as RomCom.
SectorJ47 group was found to be active in Hungary. The group distributed Windows shortcut files to targets, leading them into executing it. When the target executed the file, an embedded Windows command was executed, downloading an image file and additional malware from an external server. The downloaded image file was used to prevent the target from noticing the execution of the malware, and the malware downloaded together with the image was a DLL format malware that used web sockets to communicate with the command and control (C2) server. The malware not only serves the function of communicating with the C2 server, but also carried out malicious activities such as stealing browser credentials saved in the targeted system, or capturing screenshots.
SectorJ93 group was found to be active in Russia, the United Kingdom, and Italy. The group delivered compressed files to their targets through phishing emails and induced them to execute the HTA script files within the compressed file. When the target executed the HTA script file, an image file and a Batch Script file were downloaded from the external server onto the targeted system. The image file was disguised to resemble a document viewer, and was used to prevent the target from noticing the execution of the malware. The batch script file downloaded with the image file contained a remote control malware known as NetSupport, which was used by the group in an attempt to remotely control targeted systems and execute malicious commands.
SectorJ115 group was found to be active in the Netherlands and Brazil. The group targeted Linux servers using OpenSSL, an open-source encryption protocol, to distribute malware. The distributed malware were an ELF format malware with reverse shell functionality, a cyrptominer with cryptocurrency mining functionality, and a shell script file that downloaded additional malware.
SectorJ135 group distributed phishing page disguised as resume to the targets, leading them to download the compressed file uploaded on the website. When the target executed the Windows shortcut file within the compressed file, an embedded Windows command was executed. The command executed “ie4uinit.exe”, a utility related to the Windows Internet Explorer settings, and loaded a malicious INF file. The group ultimately disseminated backdoor malware on the targeted system, and took advantage of the task scheduler such that the backdoor would run continuously in the targeted system.
SectorJ149 group was found to be active in Ukraine. The group used a Windows shortcut file that contained a PowerShell command which downloaded an EXE format executable file from the command and control (c2) server. The final malware downloaded onto the targeted system was a remote control malware known as Remcos, and the group was analyzed to have attempted to remotely control and execute malicious commands on the targeted system.
SectorJ194 group sent phishing emails containing links to phishing sites, prompting targets to click the attached link by claiming that a microcode update was required. When the target accessed the link, Linux commands were provided to them along with instructions to execute the commands. When the target executed the provided command on their system, a shell script file hosted on GitHub would be downloaded onto the target’s system. Although the specific shell script file used in this attack has since been deleted, similar attack techniques have previously involved GitHub-hosted files containing backdoor malware. This suggests that the downloaded shell script file was also likely a backdoor malware.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
