Monthly Threat Actor Group Intelligence Report, January 2025 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC Threat Research Lab based on data and information collected from 21 December 2024 to 20 January 2025.
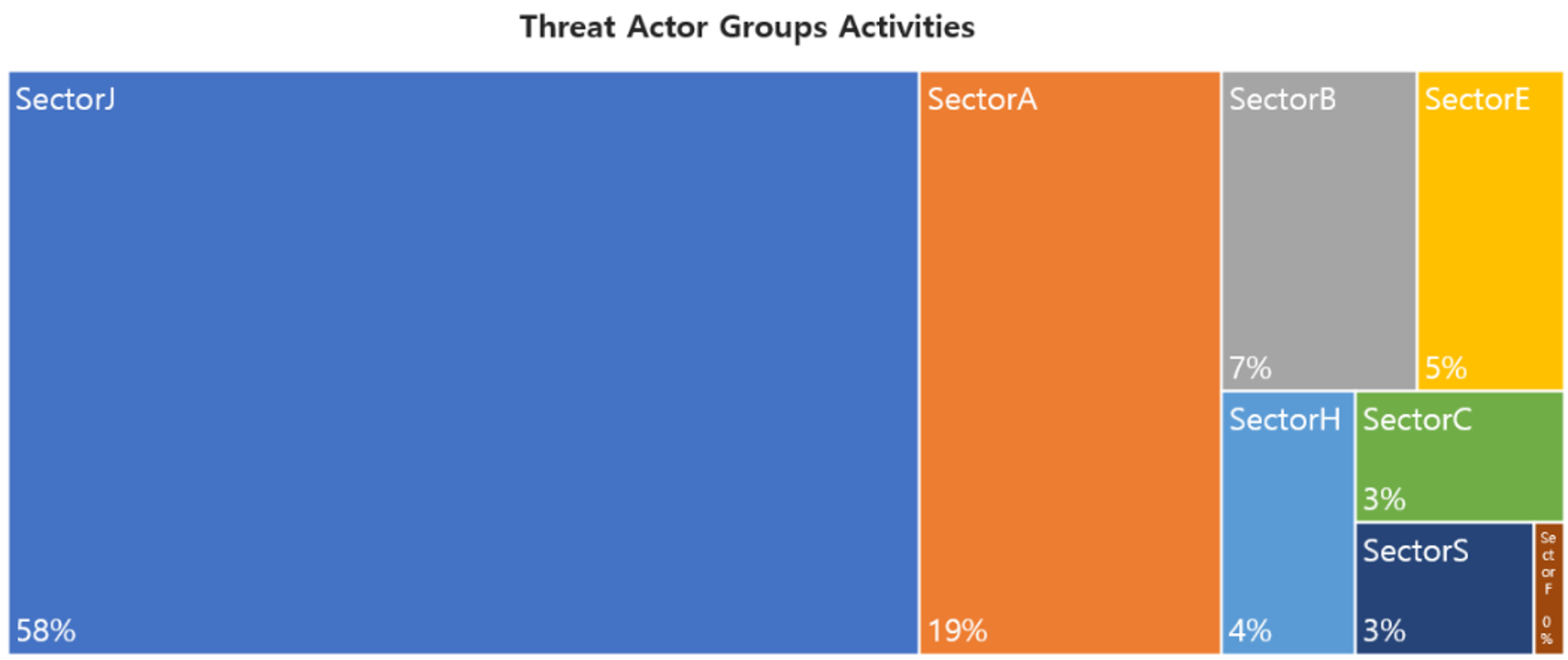
In January, a total of 51 activities by Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 58%, followed by SectorA and SectorB groups.
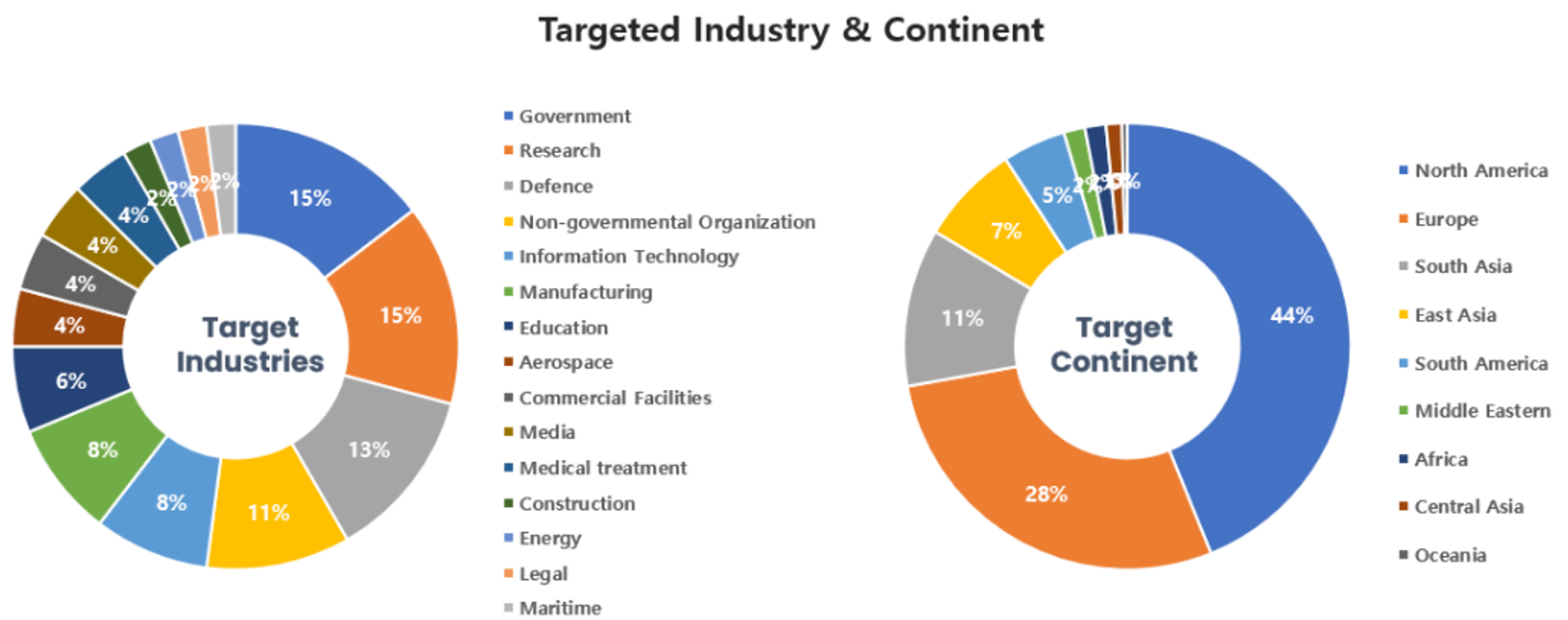
Threat Actors identified in January carried out the highest number of attacks on workers and systems in government institutions and the research sector. Regionally, North America and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In January 2025, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA04, SectorA05 and SectorA07 groups.
SectorA01 group was found to be active in Brazil, the United States, Russia, Poland, Netherlands, and France. The group disguised themselves as recruiters using platforms such as LinkedIn, Telegram, and Discord, and conducted video interviews to trick their targets into copying and executing specific commands, ultimately using malware to perform backdoor functions.
SectorA04 group was found to be active in Brazil and South Korea. The group targeted asset management solutions and data loss prevention (DLP) solutions in an attempt to seize control server permissions, and used malware with backdoor and keylogging purposes.
SectorA05 group was found to be active in South Korea. The group used spear phishing emails related to the defense industry, which were attached with a HWP format document file. They used HWP files exploiting OLE (Object Linking and Embedding) objects, and ultimately registered a scheduled task in the task scheduler to download and execute a batch file that could deliver and execute appropriate malware depending on the situation.
SectorA07 group was found to be active in the United Kingdom and Japan. The group used a Windows shortcut (LNK) format malware disguised as a request for explanatory documents related to national tax collection. When the target executed the malware, a visual basic script (VBS) malware and a batch script format malware were executed, collecting information from the targeted system and downloading additional malware for execution.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In January 2025, activities by a total of 4 hacking groups were identified, and the groups were SectorB04, SectorB22, SectorB73, and SectorB86.
SectorB04 group was found to be active in India and the Philippines. The group targeted organizations in the aerospace and defense sector, as well as pharmaceutical companies for their attacks, mainly focusing on cyber espionage activities such as intellectual property theft and information gathering using malware installed on the targeted systems.
SectorB22 group was found to be active in Germany, Hungary, Vietnam, India, the United States of America, Japan, China, Hong Kong, Malaysia, Italy, Mongolia, Taiwan, Myanmar, Cambodia, Ethiopia, Brazil, and Australia. The group targeted various countries in Asia to use a meticulously built infection chain and distribute customized backdoor malware. In particular, the group elevated their attack techniques by taking advantage of documents with clever topics such as the Taiwanese presidential candidate or important regional events and using various types of files.
SectorB73 group was found to be active in January through the activities of their botnet. Despite attempts by law enforcement agencies to shut down the botnet control server operated by the group, the botnet was confirmed to have communicated with a new control server.
SectorB86 group used an exploit kit, a tool that automatically exploits vulnerabilities to distribute malware, to exploit vulnerabilities in Ivanti Connect Secure VPN devices and distribute customized malware.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In January 2025, activities by a total of 2 hacking groups were identified, and the groups were SectorC01 and SectorC14.
SectorC01 group was found to be active in Kazakhstan, Ukraine, Israel, India, Kyrgyzstan, Tajikistan, and Mongolia. The group used malicious Microsoft Word documents on diplomacy matters with macros embedded. They ultimately used a HTA malware with backdoor capabilities to send system and account names to the command and control (C2) server, as well as the function to receive visual basic scripts (VBS) from the attacker depending on the situation and execute it.
SectorC14 group impersonated U.S. government officials to send out spear phishing emails claiming to offer targets the opportunity to join a WhatsApp group. They disguised a QR code for WhatsApp device linking and web login as a group invitation QR code. When the target scanned the QR code according to the instructions, the attacker gained access to their WhatsApp account and read their messages. In addition, the attackers could use a browser plugin for sending messages in the web version of WhatsApp to leak data.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorE Group Activities
In January 2025, activities by a total of 4 hacking groups were identified, and the groups were SectorE01, SectorE02, SectorE04, and SectorE05.
SectorE01 group was found to be active in China, Japan, and Taiwan. The group distributed Windows shortcut (LNK) files disguised as project execution plan documents to carry out their attacks, ultimately performing malicious activities according to the command received from the command and control (C2) server through an installed malware.
SectorE02 group was found to be active in India. The group distributed Android applications disguised as chat applications, ultimately stealing sensitive information such as SMS messages, contact list, and phone call history from the targeted devices.
SectorE04 group was found to be active in Bangladesh, Pakistan, and Germany. The group distributed Microsoft Word documents disguised as cyber security advisories to carry out their attacks, ultimately downloading and executing a remote template document file to set the foundation for future attacks.
SectorE05 group was found to be active in the United Kingdom. The group distributed Windows help (CHM) files disguised under the filename of “Nomination of Rep of Mod Committee” to carry out their attacks, ultimately using the visual basic script command registered in the task scheduler of the targeted system to download additional malware and set the foundation for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
5. Characteristics of SectorF Group Activities
In January 2025, activities by a total of 1 hacking groups were identified, and the group was SectorF01.
SectorF01 group was found to be active in China. The group distributed a malware-containing plugin for Cobalt Strike, a penetration testing tool, to cybersecurity experts through GitHub. The ultimately installed malware executed commands received from the command and control (C2) server to carry out malicious activities.
Hacking activities of SectorF carry the aim of collecting advanced information on governmental activities of countries neighboring supported government, such as political, diplomatic, and military activities, and to steal information related to cutting-edge technology for economic development of their country.
6. Characteristics of SectorH Group Activities
In January 2025, activities by a total of 4 hacking groups were identified, and the group was SectorH03.
SectorH03 group was found to be active in India. The group distributed Adobe PDF documents disguised as official document from the government to carry out their attacks. The PDF document contained a link that redirected users to a phishing website disguised as an Indian government website, which was used to collect email account credentials for future attacks.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of Cyber Crime Group Activities
In January 2025, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA04, SectorA05 and SectorA07 groups.
Unlike other government-supported hacking groups, these groups steal online information with tangible value that can secure monetary gains in the real world, or they hack specific companies and organizations directly, spreading ransomware within internal networks, or demanding monetary compensation after stealing important industrial secrets.
SectorJ09 group carried out a formjacking attack by inserting a skimming script on online payment pages to steal financial information. The group injected obfuscated malicious JavaScript code on the payment pages of e-commerce websites, stealing sensitive financial data such as card numbers, expiration dates, and CVC codes entered by the victims.
SectorJ110 group was found to be active in South Korea. The group sent out phishing emails on freight transportation, inducing the target to execute the attachment file by explaining that it was a document related to customs clearance procedures. The attached file was a data file written in HTML (Hypertext Markup Language), designed to automatically redirect the target to a phishing page upon clicking the document. The redirected phishing page prompted the target to enter their Adobe account credentials by showing a pop-up window stating that the document was protected, which was deduced to be an attempt to steal Adobe credentials of the targets.
SectorJ153 group disseminated the RansomHub ransomware to targets in an attempt to secure financial profit. The group not only encrypted the targeted systems using the ransomware, but also carried out a double extortion attack by leaking the system data to cloud storage such as Mega, and threatening to expose the data.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
