Monthly Threat Actor Group Intelligence Report, February 2025 (ENG)
This is a summary of the activities of hacking groups (Threat Actor Groups) analyzed based on data and information collected by the NSHC Threat Research Lab from January 21, 2025, to February 20, 2025.
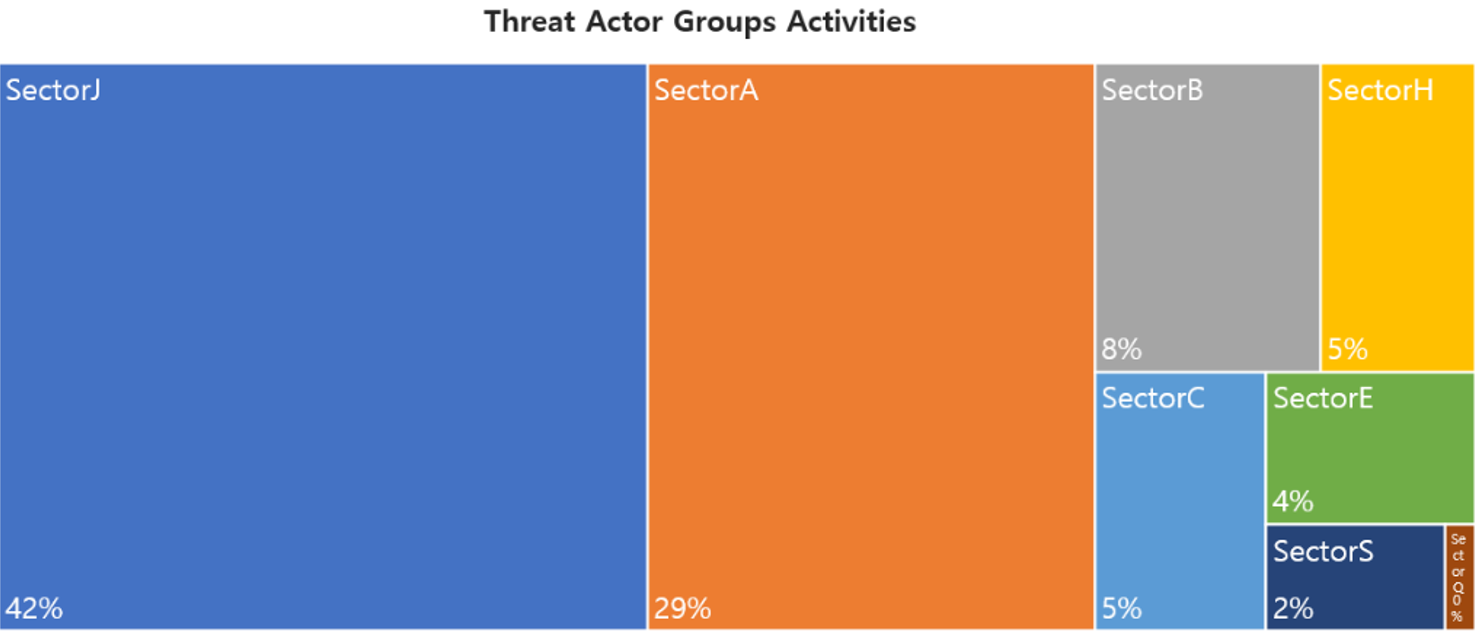
In February, activities of a total of 62 hacking groups were identified, with SectorJ group being the most active at 42%, followed by the activities of SectorA and SectorB groups.
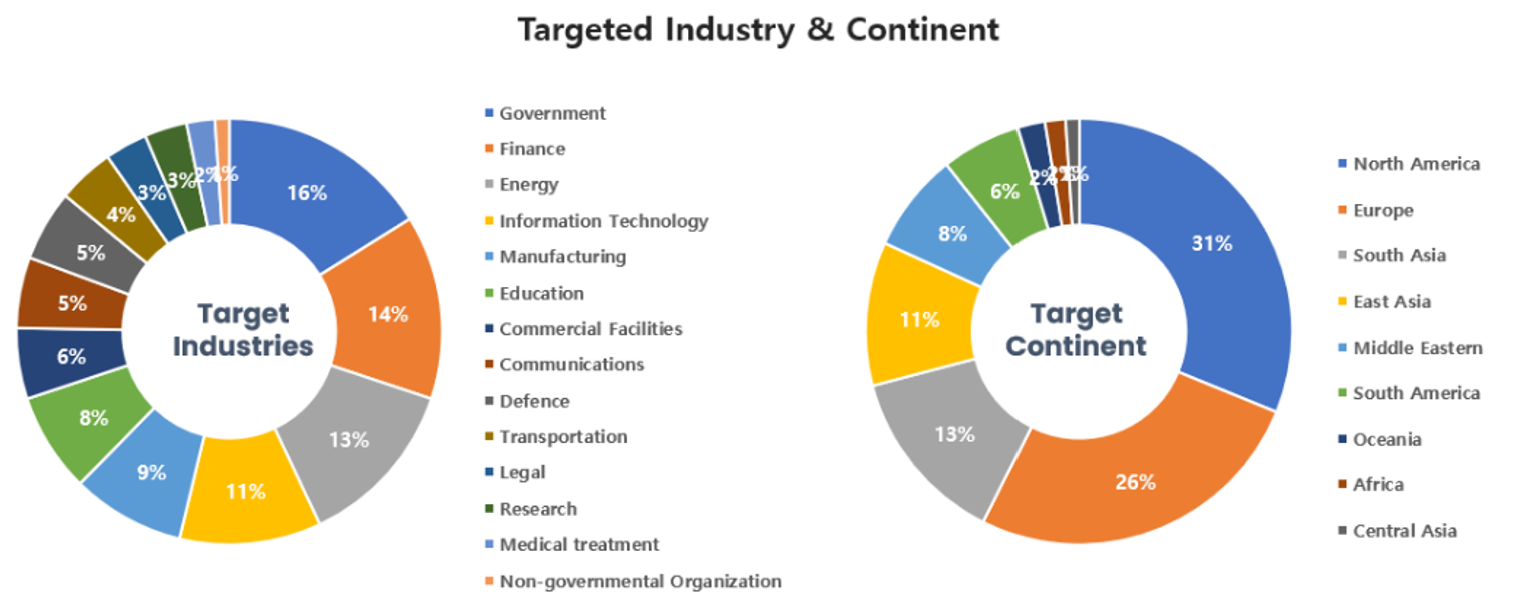
Threat Actors identified in February carried out the highest number of attacks on workers and systems in finance and government institutions. Regionally, North America and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In February 2025, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, and SectorA07 groups.
SectorA01 group activities were discovered in in Brazil, the United States, Russia, Poland, the Netherlands, and France. This group disguised themselves as recruiters using platforms such as LinkedIn, Telegram, and Discord, and pretended to conduct video interviews to trick targets into copying and executing specific commands. The group ultimately used malware with backdoor capabilities.
SectorA02 group activities were discovered in in South Korea and Japan. This group used malicious Hangul (HWP) file format documents containing North Korea-related content, and ultimately used backdoor malware to steal files according to the attacker’s commands. They then transferred the files to the attacker’s cloud server using cloud services such as pCloud and Yandex.
SectorA05 group activities were discovered in Austria, the United States, South Korea, Mexico, India, and Italy. This group attempted phishing attacks using topics related to VAT (value-added tax) filings, impersonating tax authorities, portal sites, and verification emails to send emails to users. Clicking the link included in the email redirects the user to a phishing page disguised as a portal site login screen, designed to transmit the user’s login information to the attacker upon entering the credential details.
SectorA07 group activities were discovered in Japan, South Korea, and Vietnam. This group used malware in the form of Windows shortcut (LNK) files disguised as requests for supporting documents regarding National Tax Collection. When the target executes the malware, it ultimately triggers malware in the form of Visual Basic Script and Batch Script, which collects information and downloads and executes additional Malware.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In February 2025, activities by a total of 6 hacking groups were identified, and the groups were SectorB01, SectorB22, SectorB71, SectorB108, SectorB109, and SectorB110.
SectorB01 group activities were discovered in Taiwan, Saudi Arabia, Yemen, Japan, South Korea, Spain, Belgium, Russia, the United Kingdom, the Philippines, Greece, Germany, Ecuador, Panama, and the United States. This group has targeted the manufacturing, education, energy, and entertainment industries by distributing malware with remote control capabilities known as ShadowPad, as well as ransomware, to conduct attacks aimed at intellectual property theft.
SectorB22 group activities were discovered in Thailand, Singapore, the United States, China, Vietnam, and the Philippines. This group conducted attacks by distributing MSC (Microsoft Management Console Snap-in Control) files disguised as invitation documents. Ultimately, they performed malicious activities by executing commands received from a Command and Control (C2) server through malware with remote control functions, which was additionally downloaded via a malicious batch file installed on the target system.
SectorB71 group activities were discovered in South Korea. This group conducted attacks by targeting Linux-based systems to distribute malware that is inserted into SSH Daemon. The group ultimately carried out malicious activities by executing commands received from the Command and Control (C2) server through the malicious SSL library loaded using the SSH Daemon.
SectorB108 group activities were discovered in Argentina, Bangladesh, Indonesia, Malaysia, Mexico, the Netherlands, Thailand, the United States, and Vietnam. This group conducted attacks targeting unpatched Cisco network equipment of telecommunications companies worldwide. The group ultimately configured a GRE (Generic Routing Encapsulation) tunnel to facilitate sensitive data exfiltration during communication between targeted Cisco equipment and the company’s infrastructure, as well as to bypass network monitoring.
SectorB109 group activities were discovered in South Korea, Japan, and China. This group conducted a supply chain attack targeting a South Korean VPN software vendor, through which it distributed a backdoor malware. The backdoor was used to collect sensitive information from compromised systems, execute stored Python modules, and modify the system registry to establish persistence.
SectorB110 group activities were discovered in Hong Kong, Thailand, the United States, Brazil, and South Korea. This group conducted attack activities by distributing malware targeting the South American Ministry of Foreign Affairs. Ultimately, through the malicious files installed on the targeted systems, they performed malicious actions by executing commands received from the Command and Control (C2) server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In February 2025, activities by a total of 6 hacking groups were identified, and the groups were SectorC01, SectorC04, SectorC05, SectorC26, SectorC28, and SectorC29.
SectorC01 group activities were discovered in the United Arab Emirates. This group distributed malicious documents through phishing emails and exploited vulnerabilities to infiltrate internal systems. The attackers executed malware through compressed files containing the WinRAR vulnerability (CVE-2023-38831), and subsequently chained PowerShell, Visual Basic Script (VBS), and Batch (BAT) scripts to load multi-stage payload and install a backdoor.
SectorC04 group recently conducted a phishing attack exploiting the Device Code Authentication method to hijack Microsoft 365 accounts. They impersonated government agencies such as the U.S. Department of State, the European Union Parliament, and the Ukrainian Ministry of Defense to send phishing emails. The group aimed to induce targets into trusting them by using workplace relevant scenarios such as Microsoft Teams meeting invitations, chat room participation requests, and external application approval requests.
SectorC05 group activities have been discovered in Ukraine, Spain, France, Poland, the United Kingdom, the United States, Canada, and Australia. The group conducted attacks by distributing Remote Desktop Protocol (RDP) malware disguised as a Windows update. The malware was disguised as an executable designed to appear like a regular system update to targets, but upon execution, it forcibly changes the RDP settings on the system to allow external access.
SectorC26 group conducted a sophisticated phishing campaign that exploited the Microsoft Device Code Authentication process to hijack Microsoft 365 accounts. They used messages disguised as Microsoft Teams invitations or external application authentication requests.
SectorC28 group conducted a phishing attack by spoofing the group invitation page of the Signal messenger to deceive users and connect the attacker’s device to the target’s account. This attack was meticulously crafted to insert a device connection URL into the webpage that appeared to be a legitimate group invitation link, allowing the attackers to monitor the messages with a mere click, without account hijacking.
SectorC29 group exploited the device linking feature of the Signal messenger to carry out a phishing attack based on malicious QR codes. When the target scans the QR code, the attacker’s device gets linked to the Signal account, allowing them to intercept messages in real-time.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorE Group Activities
In February 2025, activities by a total of 3 hacking groups were identified, and the groups were SectorE01, SectorE02, and SectorE04.
SectorE01 group activities were discovered in China and Taiwan. This group conducted attack activities by distributing Windows shortcut (LNK) files disguised as military special recruitment guide documents. The group ultimately registered the malware on the task scheduler to download malicious files and execute them every minute, setting a foothold for subsequent attacks.
SectorE02 group activities were discovered in the Netherlands and Bangladesh. This group conducted attack activities by distributing Android apps disguised as chat applications. The group ultimately performed malicious activities to steal sensitive information such as SMS messages, contacts, and call logs through the Android apps executed on the targeted devices.
SectorE04 group activities were discovered in Sri Lanka, the United States, China, and Hong Kong. The group conducted attacks by distributing Microsoft Word documents disguised as official documents issued by the Sri Lankan Presidential Secretariat. Ultimately, through the Word documents executed on the target systems, they facilitated the download and execution of a remote template document file, setting the foothold for subsequent attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
5. Characteristics of SectorH Group Activities
In February 2025, activities by a total of 2 hacking groups were identified, and the group were SectorH01 and SectorH03.
SectorH01 group activities were discovered in the United Kingdom, United States, Switzerland, and Australia. This group conducted attack activities by distributing malware through phishing emails impersonating tax software solution organizations. Ultimately, they performed malicious activities by executing commands received from a Command and Control (C2) server through a remote control malware installed on the targeted systems.
SectorH03 group activities were discovered in India and Afghanistan. This group conducted attack activities by distributing Windows shortcut (LNK) files disguised as cybersecurity guideline documents. Ultimately, they set the foothold for subsequent attacks by downloading and executing additional malware through a malicious DLL file installed on the target system.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
6. Characteristics of SectorQ Group Activities
In February 2025, activities by a total of 1 hacking groups were identified, and the group was SectorQ02.
The SectorQ02 group executed sophisticated cyber operations targeting aerospace and science and technology-related institutions, including Chinese universities. They inserted customized malware, such as the NOPEN backdoor, into the targeted systems to enable long-term remote control.
The ongoing hacking activities of the SectorQ hacking groups are analyzed to be conducted with the purpose of collecting high-level information related to government activities, such as political and diplomatic activities of government agencies worldwide. The collection of such high-level information is believed to be driven by the aim of maximizing their own country’s political and economic interests.
7. Characteristics of SectorR Group Activities
In February 2025, activities by a total of 1 hacking groups were identified, and the group was SectorR02.
SectorR02 group activities were discovered in China. This group targeted users of 163.com, a free email service by the Chinese IT company NetEase, to conduct phishing campaigns. They tricked users into entering their login credentials, and stole these login credentials to access the victims’ email accounts and collected sensitive information.
SectorR hacking groups are aimed at collecting high-level information on government activities, including political, diplomatic and military activities involving the China, which is in rivalry with countries that support SectorR.
8. Characteristics of SectorS Group Activities
In February 2025, activities by a total of 1 hacking groups were identified, and the group was SectorS01 group.
SectorS01 group activities were discovered in Italy. The group conducted attack activities by distributing Windows shortcut (LNK) files disguised as documents related to a summit meeting. The group ultimately executed a remote control malware in the memory of the targeted system, which received commands from the Command and Control (C2) server to perform malicious activities.
SectorS hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
9. Characteristics of SectorU Group Activities
In February 2025, activities by a total of 1 hacking groups were identified, and the group was SectorU01 group.
SectorU01 group activities were discovered in Russia, Spain, Uzbekistan, India, the United States, Hong Kong, the Czech Republic, Kyrgyzstan, and Turkmenistan. This group attempted initial infiltration of systems under government agencies in Central Asia by sending phishing emails containing malicious ISO files. Ultimately, they posed a serious cyber espionage threat to the Central Asian region by executing malware on the targeted systems to collect sensitive information and modifying the system registry to ensure persistence.
The ongoing hacking activities of the SectorU hacking groups are analyzed for the purpose of gathering advanced intelligence on government activities, including the political and diplomatic activities of government agencies in countries around the world, including the governments that support them and their neighbors.
10. Characteristics of Cyber Crime Group Activities
In February 2025, activities by a total of 13 hacking groups were identified, and the groups were SectorJ09, SectorJ14, SectorJ21, SectorJ25, SectorJ85, SectorJ102, SectorJ110, SectorJ177, SectorJ195, SectorJ196, SectorJ197, SectorJ201, and SectorJ202.
Unlike other government-supported hacking groups, these groups steal online information with tangible value that can secure monetary gains in the real world, or they hack specific companies and organizations directly, spreading ransomware within internal networks, or demanding monetary compensation after stealing important industrial secrets.
SectorJ09 group conducted formjacking attacks by inserting skimming scripts into online payment pages to steal financial information. This group injected obfuscated malicious JavaScript code into the payment pages of e-commerce websites, and was analyzed to have stolen sensitive financial data such as card numbers, expiration dates, and CVC codes entered by the target.
SectorJ14 group activities were discovered in South Korea, Germany, the United States, India, Japan, and France. This group used a smishing technique of disguising themselves as a delivery service notification to send Twitter shortened URLs to their targets. When the target accessed the shortened URL, they were redirected to a malicious URL, prompting them to download Android Malware disguised as the Chrome browser app. The downloaded malware encouraged the target to grant permissions for text and notification display and, under the pretext of spam prevention, set the malware as the default SMS app. Once the initial permission setup was complete, a notification channel was created on the target device to display phishing messages. When the group sent phishing messages, they were displayed through this notification channel to entice the target to click on them. Additionally, it is analyzed that the group utilized data registered on a profile on Pinterest, a social media platform, to compose and send phishing messages.
SectorJ21 group activities were discovered in the United States and Canada. This group delivered phishing emails attached with PDF documents containing links to download ZIP archive files. The ZIP archive file contained an IMG file that automatically mounted to an external drive and was opened through the file explorer upon execution. When the SCR file disguised under the Adobe icon was executed on the mounted drive, a malicious DLL file was loaded through the DLL side-loading technique. The loaded malware carried out the function of collecting system information, then encrypting it to upload it to Tab Digital, a cloud storage service.
SectorJ25 group activities were discovered in India. The group was analyzed to have disseminated a malicious compressed file by renaming it to “NetworkAnalyzer.tar.gz”, disguising it as a network analysis program. The compressed file contained an ELF format malware, which is analyzed to be the CHAOS remote control tool with source code available on GitHub. This malware is analyzed to have the capability to execute commands remotely and exfiltrate data from the target system.
SectorJ85 group published a phishing site that mimicked the login page of Okta, an enterprise cloud-based Identity-as-a-Service (IDaaS) solution. They employed the typosquatting technique by registering domains with similar spelling or structure to the legitimate Okta login page domain, tricking targets into mistaking it for the legitimate login page and prompting them to enter their credentials.
SectorJ102 group activities were discovered in the United States and India. The group exploited SQL injection and file upload vulnerabilities of Vera Core to distribute a web shell to targeted systems. The web shell is analyzed to be capable of executing SQL commands and exploring the internal database server.
SectorJ110 group activities were discovered in Germany, Lithuania, Belgium, and Ukraine. This group distributed phishing documents in PDF format, enticing targets to click on the “Download Document (Завантажити Документ)” hyperlink text within the document. When the target clicked on the hyperlink text, a compressed file was downloaded onto the target’s system. The compressed file contained a JavaScript malware using a double extension (.pdf.js) to appear as a PDF document, and upon executing the document, a malware with loader properties was downloaded from the Command and Control (C2) server, then executed. At the same time, a regular document acting as a decoy was downloaded and shown on the target’s screen, to prevent the target from being suspicious.
SectorJ177 group activities were discovered in Mexico, the United States, and Hungary. This group impersonated technical support by sending messages to their targets via Microsoft Teams, then prompted them to install Microsoft Quick Assist to resolve spam issues. Once the target installed Quick Assist and granted remote control access to the hacking group, they downloaded a malicious payload in ZIP file format through the web browser. The compressed file contained a Microsoft-signed OneDrive update executable file and several DLL files. The group then utilized the DLL Search Order Hijacking technique to execute Malware in DLL format. This DLL-format Malware is analyzed to perform functions such as collecting system and operating system information, user accounts, and credentials, and transmitting them to a Command and Control (C2) server.
SectorJ195 group activities were discovered in the United States and Bulgaria. This group sent a large volume of spam messages to their targets and then attempted to initiate a Microsoft Teams call to persuade the target to allow remote screen sharing. Once sharing was permitted, they executed a malicious JAR (Java Archive) file through the command shell. This file was analyzed to perform tasks that involved calling the WMI Command-line Utility (Windows Management Instrumentation Command-line, WMIC.exe) via a Java-based proxy module to identify the PID of the Java process. Subsequently, they bypassed the PowerShell ExecutionPolicy to download a ZIP archive and the 7-Zip utility from an external source and extracted the contents. The archive contained a ProtonVPN executable and a malicious DLL, and they exploited the DLL side-loading technique to load the malicious DLL through the ProtonVPN program. This created a session in the targeted system that connected to virtual private servers (VPN) hosted in Russia, the Netherlands, and the United States. Additionally, the JAR file opened a new CMD (Command Prompt) session and used javaw.exe (Java SE Launcher) to execute another JAR file that dropped another compressed file. This file contained an obfuscated Python script, which was analyzed to be a reverse proxy tool known as RPivot. The group appears to have used this tool to leverage tunneling and proxy functions within the internal network to attempt persistent connections with the Command and Control (C2) server.
SectorJ196 group published a phishing site disguised as a Solana blockchain communication tool deployment site that targeted Web3 users. Through this phishing website, the group distributed an Infostealer malware, a type of malware that steals information. The phishing website directed users to different download URLs depending on the OS environment of the targets, using Dropbox for Windows environments, and a separate external server for MacOS environments.
SectorJ197 group activities were discovered in Guatemala and the United States. This group distributed phishing sites disguised as Chrome browser update sites. When the target clicked the “Update Chrome” button, a compressed file named “Release.zip” was downloaded, and it was confirmed that the compressed file contained a DLL format malware. This malware is analyzed to be a stealer malware that performs the function of stealing data from the target system.
SectorJ201 group was analyzed to have operated a Traffic Distribution System (TDS) service, providing malicious traffic inflow services to other hacking groups to secure financial gains. This TDS infrastructure performs functions such as filtering and redirecting traffic conditionally based on the visitor’s system environment and is believed to have played a role in delivering payloads, including malware, to appropriate targets.
SectorJ202 group activities were discovered in the United States, India, France, and Poland. This group distributes phishing pages disguised as Chrome browser updates to trick targets into downloading a malicious MSI (Microsoft Installer) file. The MSI file is structured to include a malicious DLL alongside a legitimate program, and the malicious DLL is loaded using the DLL side-loading technique. Ultimately, a stealer malware is executed on the target system, which was analyzed to be used in an attempt to steal data from the target system.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
