Hacking Activity of SectorA Group in 2019
SectorA Group Overview
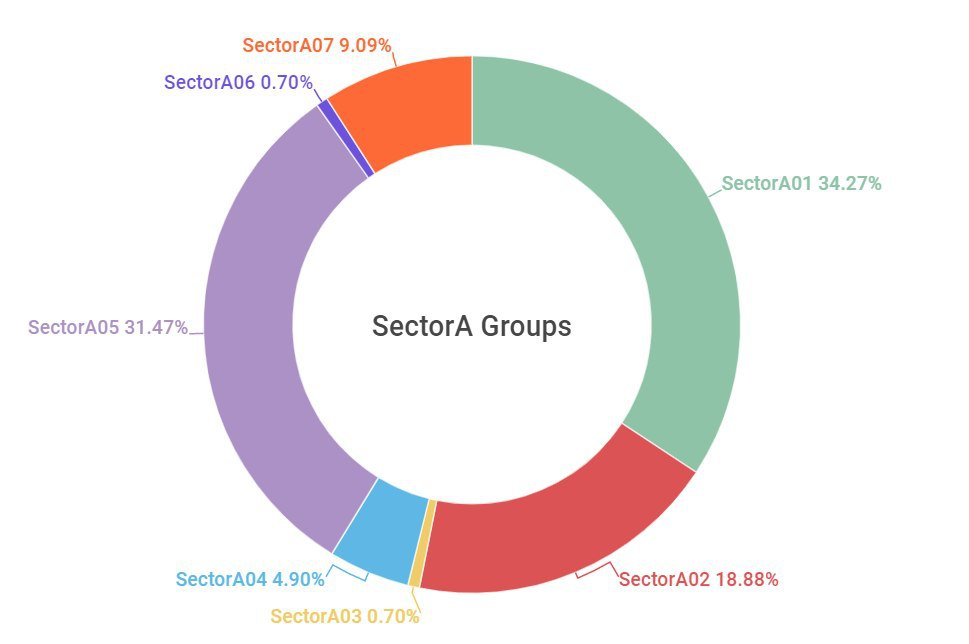
A total of 7 subgroups of SectorA have been found to date. In 2019, the activities of the SectorA01 group were most prominent, followed by the activities of the SectorA05 and SectorA02 groups. SectorA groups conduct hacking activities to collect political and diplomatic information related to specific country or to earn foreign currency. They often attach document files created using malicious MS Office documents or Hangul Word Processor vulnerabilities to spear phishing emails.
[Figure 1 : SectorA subgroup activity in 2019]
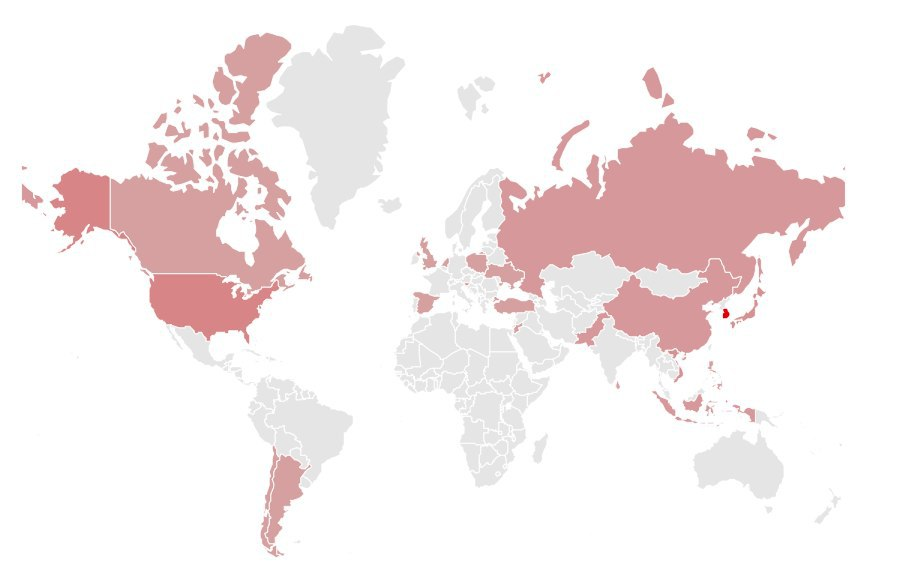
Their main targets identified until now were government ministries, Public enterprises, or organizations and individuals involved in activities related to defection of a particular country, and financial sectors such as virtual currency exchanges, banks and ATMs. Shown in red are the countries that the SectorA groups mainly targeted in 2019. The higher the frequency of hacking activity, the darker the color.
[Figure 2 : The main target countries for SectorA Groups in 2019]
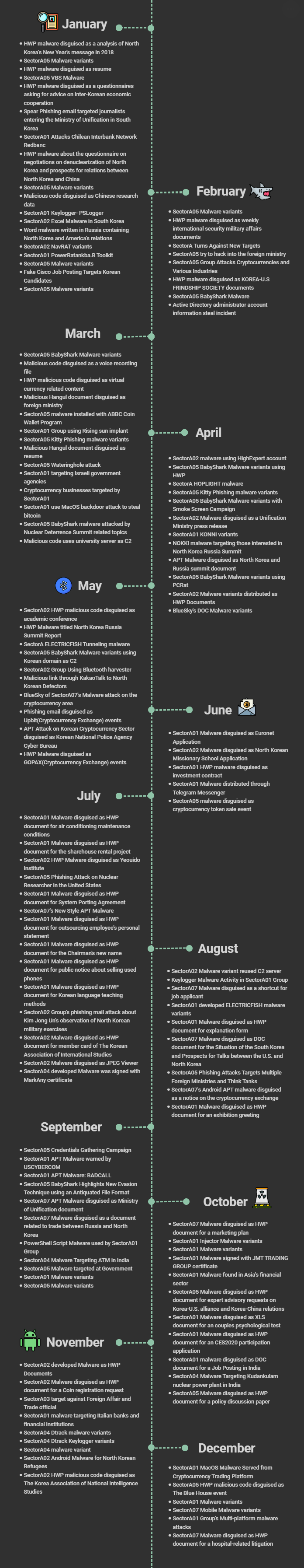
Below is the hacking activity timeline for the SectorA groups discovered in 2019.
[Figure 3: Timeline for SectorA group hacking activities in 2019]
Hacking Activity of SectorA Groups in 2019
The following is a description of the SectorA group’s monthly hacking activities.
JANUARY
A total of three hacking groups were found to be active in SectorA. While their modus operandi had been constant for the past few months, some of it has changed this time.
SectorA01 is still concentrating on financial crime using malware in countries such as Africa, Southeast Asia, and South America for financial gain.
SectorA02 and SectorA05 groups are concentrating on hacking activities aimed at stealing information related to foreign policy of South Korea, and their malware continues to be found in government agencies within South Korea.
But little by little, these hacking groups supported by SectorA have been changing their malware and hacking techniques since 2018. For example, besides their using their usual spear phishing with Hangul Word Processor (HWP) files, they have also started to use phishing with malicious scripts instead as well.
From the hacking activities by SectorA to date, we believe they will continue their activities related to financial crime and espionage aimed at South Korean government agencies.
FEBRUARY
A total of three hacking groups, SectorA01, SectorA02 and SectorA05 groups were discovered among SectorA groups this February. The range of activities of these hacking groups has not changed compared to January.
The SectorA01 group has been expanding its targets from South East Asia and South America to Central Asia to steal financial information that can be transformed into assets in the real world.
As before, the SectorA02 group conducted hacking activities aimed at collecting high-level information on government agencies and political activities in South Korea.
The SectorA05 group conducted hacking activities targeting countries that use the Russian language.
In the past, the SectorA02 and SectorA05 groups used spear phishing using malware in the form of a HWP file. Currently, both groups used malware in forms of Word and Excel (Microsoft Office) files.
Hacking activities of the SectorA01 group are highly likely to take place anywhere in the country in order to steal financial information. And the hacking activities of the SectorA02 and SectorA05 groups are likely to take place with the purpose of collecting high-level political information of the target country.
However, since the hacking activity of the SectorA05 group was found in other regions outside of East Asia, it is necessary to pay attention to the purpose and scope of the group’s activities in the future.
MARCH
A total of three hacking groups, SectorA01, SectorA02 and SectorA05 groups were discovered among SectorA groups this March. In March, there were many changes in the hacking activities of hacking groups supported by SectorA.
The SectorA01 group has attempted to steal financial information as a strategic goal in the past. However, they targeted general companies in South Korea in November 2018.
The SectorA05 group conducts the most hacking activity compared to other SectorA groups. The hacking purpose of SectorA05 is to collect information related to activities of the South Korean government and collect financial information assets as was previously conducted in SectorA01. They expanded their targets from East Asia including South Korea to North America and Europe.
All the SectorA groups used spear phishing with malware. Especially, the SectorA05 group used malware in the form of Microsoft Word, HWP files and voice record files depending on the targets and region.
As the hacking groups supported by SectorA attempt to make various changes, it is necessary to pay attention to the hacking activities of the groups.
APRIL
A total of four hacking groups, SectorA01, SectorA02, SectorA05 and SectorA06 were found among SectorA hacking groups this April.
The scope of activity for SectorA groups found in April is much larger than in the past. Previously, their targets were mainly in East Asia and North America, but now includes many more targets around the world. Traces of hacking activities have been found in the Middle East, including Israel, Turkey and Palestine, East Asia including China and South Korea, Eastern Europe including Ukraine and Slovenia, Southeast Asia including Sri Lanka and Vietnam, and North America including the United States.
The techniques used in their hacking activities found were basically using spear phishing techniques with a Hangul Word Process (HWP) file or Microsoft Word file depending on the target person or organization. We also observed them using the recently discovered WinRAR vulnerability. In addition, a case of Watering Hole attack was found.
For targets in East Asia, including South Korea, their aim was stealing information related to politics and diplomacy, as well as at stealing financial information represented by virtual currencies. Elsewhere, they were concerned with military information related to military weapons and stealing diplomatic information from countries engaged in diplomatic activities related to SectorA.
The scope of the hacking activities is expected to continue to expand in the future, as the hacking activities of SectorA hacking groups are being carried out for stealing military, diplomatic, political and financial information purposes.
MAY
A total of four hacking groups, SectorA01, SectorA02, SectorA05 and SectorA07 were found among SectorA hacking groups this May. Analysis of the hacking campaigns of SectorA groups over a long period of time reveals that SectorA02, SectorA05 and the newly defined SectorA07 are the most active. The increase in activity of these three groups means that the strategy, hacking purpose and direction of the entire SectorA groups are clarified. In addition, it means that the goals of each group in SectorA is now clear.
In the past, SectorA02 and Sector05 groups conducted hacking campaigns to collect advanced information related to Korea. However, these groups are currently conducting hacking campaigns to gather information on political activities in Europe, North America, and Southeast Asia, where countries that can influence the political and diplomatic activities of the SectorA government are located.
In May, the newly defined SectorA07 group was a small subgroup of the larger existing SectorA05 group. As a result of analyzing their hacking campaigns, we found that the SectorA07 group is active only for the purpose of collecting financial information from companies located in countries such as South Korea and Southeast Asia.
The SectorA02 group uses the most diverse hacking strategies and techniques in SectorA. They develop and utilize a variety of hacking strategies and techniques such as simple phishing attacks, spear phishing attacks with malware, and sophisticated social engineering techniques using KakaoTalk (a popular messenger in South Korea). On the other hand, SectorA05 and SectorA07 focused on utilizing spear phishing, which was used frequently in the past, for initial access. They use Microsoft Word or HWP file format malware selectively depending on their target victim.
We observe that SectorA is targeting specific countries less and now gathering political and economic activity information of various countries related to the SectorA government and capturing financial information in a variety of non-specific countries and regions.
JUNE
A total of three hacking groups, SectorA01, SectorA02, SectorA05 were found among SectorA hacking groups this June. The SectorA group was mainly active in the Middle East, Southeast Asia, and East Asia in June, targeting countries such as Jordan, Philippines, South Korea, and Japan.
The SectorA01 group mainly sent spear phishing emails to the Middle East and Southeast Asia which had Microsoft Office document files attached to them. However, in June, another case was discovered where they attached executable type malware that was disguised as a job application form.
The SectorA02 and SectorA05 groups are active mainly for monetary profit but based on their hacking techniques and malware features, each groups are aimed at different targets. The SectorA02 group mainly targets financial companies or companies related to cryptocurrency trading, but the SectorA05 group targets individuals who hold cryptocurrency. In the past, the two groups used spear phishing emails which attached malicious HWP or executable files. Recently, they have also used spear phishing emails impersonating cryptocurrency exchanges or government agencies.
Recently, the SectorA groups have been acting in parallel to target both diplomatic information related to their government and gain monetary benefits. In the past, they mainly targeted financial companies and cryptocurrency exchanges in order to earn monetary benefits. but nowadays they extended their range of hacking targets to include individual holders of cryptocurrency. Attention is needed as their range of activities expand.
JULY
A total of four hacking groups were found this July, including SectorA01, SectorA02, SectorA05 and Sector07.
The purpose of the SectorA hacking groups, which have continued to date, is to collect high-level information related to government activities, including political and diplomatic activities related to South Korea, as well as to secure money from around the world. The purpose of these hacking attacks has been similar over the long-term, and it is believed that these strategic hacking objectives will continue without change for the time being.
The hacking activities of the SectorA01, SectorA05 and SectorA07 groups discovered in July were found to be for securing financial goods, and the activities are targeted at cryptocurrency exchanges or towards individuals who can trade cryptocurrency currencies in South Korea.
The SectorA02 group’s hacking activities are being carried out with the aim of collecting high-level information related to the activities of government agencies in South Korea or organizations related to political activities.
The activities of the four SectorA-related hacking groups found in July were performed using spear phishing, which uses HWP (Korean) files which are only used by Koreans as attachments, as a basic hacking technique. However, only the SectorA07 group has been found to show characteristics of using Microsoft Word files with macro functionality as attachments of spear phishing emails.
In addition, SectorA05 used hacking techniques that utilize phishing emails for the purpose of obtaining email access information of specific targets located in the U.S., while SectorA07 group produced and used mobile malware designed to operate on Android smartphones.
As mentioned earlier, the hacking group’s activities related to SectorA are aimed at stealing high-level information related to South Korea’s political, diplomatic and SectorA’s relief group, in addition to hacking activities that are aimed at resolving SectorA’s economic activities that have been limited by sanctions. The hacking activities are expected to continue for some time in the foreseeable future.
AUGUST
A total of four hacking groups, SectorA01, SectorA02, SectorA04 and SectorA07 were found among SectorA hacking groups this August. Two parallel requirements of SectorA hacking groups are collecting high-quality information related to South Korean political and diplomatic activities and to obtain illegal monetary benefit by targeting anywhere in the world.
SectorA01 group activity was found in South Korea, the Philippines, Argentina, Pakistan, United States and Nepal. SectorA02 group activity has been found in South Korea and the United States. SectorA4 group, which had not been found for a while, was found in South Korea, and malware was discovered using a digital signature issued by a Korean security company. Sector07 group activity was found in South Korea, Indonesia, United States, Russian Federation and Germany.
The activities of the four SectorA-related hacking groups discovered in August common use spear phishing as an attack vector. However, SectorA01 uses Hangul files (HWP) as attachments in South Korea, and only other SectorA02, SectorA04, and SectorA07 groups use Microsoft Word files containing macro function as an attachment to its spear phishing emails.
The SectorA02 group produces mobile malware designed to run on Android smartphones and uses it for hacking activities.
The SectorA groups aim to seize high-level information related to South Korea’s political, diplomatic and SectorA’s relief organizations. Due to large-scale economic sanctions surrounding SectorA, their hacking groups carry out hacking activities to steal financial information in other countries, including South Korea. These operations take place in parallel. and SectorA groups are expected to continue hacking with the purpose.
SEPTEMBER
A total of three hacking groups, SectorA01, SectorA02, and SectorA07, were found among SectorA hacking groups this September.
The parallel requirements of the hacking activities of SectorA hacking groups, which continues to date, is to both collect high-quality information related to government activities such as political and diplomatic activities related to South Korea or related to SectorA relief organizations, and to illegally profit from crimes around the world. The purpose of this hacking has been continued for a long time, and for this strategic hacking purpose, it is expected to continue without change for the time being.
The hacking activities of the SectorA01, SectorA05 and SectorA07 groups discovered in September were related to collecting high-level information such as political and diplomatic activities related to South Korea.
SectorA01 group activity was found in South Korea, Germany, the United States, China, and Austria, and used malware in the form of files of Hangul software files, which is widely used by South Korean government agencies.
SectorA05 group activity was found in United States, South Korea, Peru, Belgium, France, China, Japan, the United Kingdom, Slovakia, Russia and Poland. The hacking technique used by the group was spear phishing emails to deliver malware in the form of Microsoft Word files to the target of attack. The lure document had a topic related to SectorA’s economic sanctions, nuclear development, and submarines.
SectorA07 group activity was found in South Korea, Italy, Vietnam, Japan, and Brazil. During that time, the attacker used a Windows executable file with a file name associated with a MOU contract with the Department of Defense. The file was disguised using the icon of Microsoft Word.
OCTOBER
A total of four hacking groups, SectorA01, SectorA04, SectorA05 and Sector07 groups were discovered among SectorA groups this October. SectorA01 group’s hacking activity was found in areas including the United States, Philippines, the United Kingdom, Germany, Nigeria, South Korea and India. SectorA04 group were found in areas including South Korea, United States, Japan and India. Hacking activity of the SectorA05 group was found in South Korea and Ukraine. Hacking activity of the SectorA07 group was found in South Korea.
The SectorA01 group has hacked into cryptocurrency traders by distributing fake cryptocurrency trading programs to both macOS and Windows operating systems.
The SectorA04 group hacked into an ATM Machine operated by an Indian financial firm. The attack is similar to an incident in South Korea in the past, and is a hacking activity aimed at stealing card information input through the hacked ATM device and stealing real money.
The SectorA05 group used a Hangul file (HWP) that disguised it as an expert advisory request document containing the vulnerability. This activity was conducted to collect information related to the SectorA government from academia, universities, and research institutes.
Similar to SectorA05 group, SectorA07 group used malware in the form of a Hangul file. The Hangul file used cryptocurrency mining as a theme. It seems that the hacking activity was performed targeting individuals and organizations related to cryptocurrency trading and mining.
The purpose of the hacking activities of the SectorA hacking groups to date is to collect high-quality information about political and diplomatic activities of South Korea and to steal money from financial organization all around the world. This purpose has remained the same for a long time, and is expected to continue without change for the time being.
NOVEMBER
A total of five hacking groups, SectorA01, SectorA02, SectorA03, SectorA04 and SectorA05 groups were discovered among SectorA groups this November. SectorA01 group’s hacking activity was found in areas including the United Kingdom, South Korea, India, Ukraine, Singapore, Italy and Netherlands. SectorA02 group’s hacking activity was found in areas including the United States, South Korea, India and Japan. SectorA03 group’s hacking activity was found in areas including the United Kingdom, Hong Kong, United States, China and Singapore. SectorA04 group’s hacking activity was found in areas including Finland, Israel, India, South Korea, Thailand, United States, Russia, Japan and Philippines. Hacking activity of the SectorA05 group was found in Ukraine and South Korea.
The SectorA01 group used a spear phishing email with a malicious Microsoft Word document attached. The malicious document contains a macro script that generates a DLL using Base64 encoded data at the end of the document.
The SectorA02 group used malware in the Hangul (HWP) file format written with various themes such as presidential election announcements, resumes, and cryptocurrency in spear phishing emails. Hangul malware used for hacking is the same as those found previously, and the embedded EPS (Encapsulated Postscript) object performs malicious functions when executed.
The SectorA03 group created decoy files with the theme of New Year’s greetings, holidays related to South Korea, news articles or images related to South Korea and North Korea. They used spear phishing emails with malware disguised as images, documents, and screensaver files. When the malware is executed, the normal images or documents are displayed, and the payload stored in the resource section of the file gets executed.
The SectorA04 group targeting the Kudankulam Nuclear Power Plant (KKNPP) located in India used the DTrack malware for the purpose of collecting information. The plant-related IP and account information was hard coded in the malware.
The SectorA05 group consistently used spear phishing emails with malware in the form of Korean files for attacks. The malware found in this activity was disguised as discussion document.
The purpose of the hacking activities of the SectorA hacking groups to date is to collect high-quality information about political and diplomatic activities of South Korea and to steal money from financial organization all around the world. This purpose has remained the same for a long time and is expected to continue without change for the time being.
DECEMBER
A total of three hacking groups, SectorA01, SectorA05 and SectorA07 groups were discovered among SectorA groups this December. SectorA01 group’s hacking activity was found in Italy, Indonesia, Ukraine, United Kingdom, United States, South Korea and China. SectorA05 and SectorA07 group’s hacking activity was found in South Korea.
The SectorA01 group used files disguised as macOS installers (DMG) distributed by cryptocurrency exchange.
The SectorA05 group used an executable (EXE) file disguised using the Hangul file icon. The file was disguised as a document of a government agency.
The SectorA07 group used malware in the form of Hangul document files (HWP) for attacks which included PostScript code.
The purpose of the hacking activities of the SectorA hacking groups to date is to collect high-quality information about political and diplomatic activities of South Korea and to steal money from financial organization all around the world. This purpose has remained the same for a long time and is expected to continue without change for the time being.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.