Monthly Threat Actor Group Intelligence Report, February 2023 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 January 2023 to 20 February 2023. In February, activities by a total of 23 Threat Actor Groups were identified, in which activities by SectorA was the most prominent by 28%, followed by SectorE and SectorJ groups.
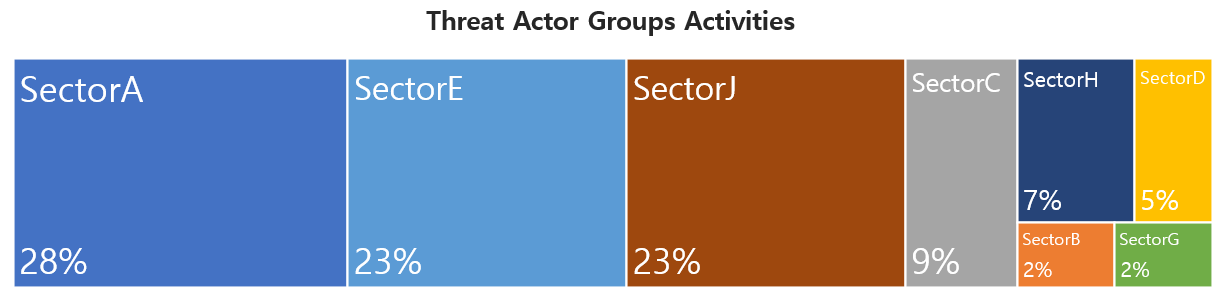
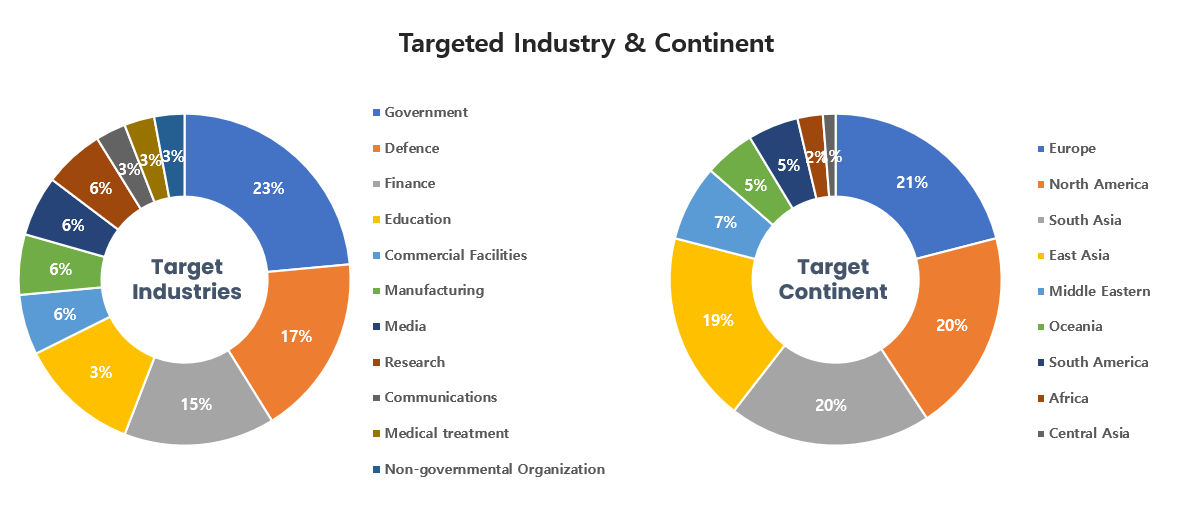
Threat Actors identified in February carried out the highest number of attacks on workers and systems in government agencies and national defense sectors. Regionally, Europe and North America were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In February 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, SectorA07.
SectorA01 group was found to be active in Belgium, the United States, Canada, and Slovenia. The group disseminated compressed files disguised as organization evaluation files and attempted to steal system information through the malware incorporated within the file.
SectorA02 group was found to be active in South Korea. The group disseminated HTML (Hypertext Markup Language) format malware disguised as a security email of an administrative agency. The malware registered itself under the scheduler to maintain persistency and carried out the function of downloading additional script files from the C2 server through MSHTA(Microsoft HTML Application) and executing it.
SectorA05 group was found to be active in South Korea. The group targeted workers of media communication and research institutions to distribute MS Word malwares, and attempted to steal information from the infected system.
SectorA06 group was found to be active in the United States, Canada, and Norway. The group distributed compressed files disguised as presentation resources and attempted to steal system information through the additionally downloaded malware.
SectorA07 group was found to be active in the United States, South Korea, and Australia. The group distributed LNK format malware disguised as request for supporting documents and downloaded additional malware in order to attempt information theft.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In February 2023, activities by a total of 1 hacking groups were identified, and the groups were SectorB22.
SectorB22 group was found to be active in Taiwan, Germany, Czech Republic, and Estonia. The group incorporated a LNK file and a PE(Portable Executable) malware in a compressed file disguised as an administrative document and monitored and collected information from the infected system.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In February 2023, activities by a total of 2 group was identified, and the group was SectorC04, SectorC08.
SectorC04 group was found to be active in Chile and Poland. The group used malware disguised as documents of car sales data, and utilized the DLL side-loading technique to execute malware that exploits the Notion API (Application Programming Interface).
SectorC08 group was found to be active in Ukraine. The group targeted on the Ministry of Defense to send out spear phishing emails disguised as criminal proceedings documents regarding illegal activities of military men, and attempted additional downloads of malicious files through MSHTA, a Microsoft HTML application program.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In February 2023, activities by a total of 2 hacking groups were identified, and the groups were SectorD11, SectorD14.
SectorD11 group was found to be active in France, Czech Republic, Turkey, Germany, Egypt, the United States, Vietnam, Russia, and Iraq. The group used malware disguised as commercial invoices and attempted to steal information through malware with remote access functions.
SectorD14 group used malware disguised as news articles on combat drones and attempted to steal information through malware with remote access and control functions.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In February 2023, activities by a total of 3 hacking groups were identified, and the groups were SectorE02, SectorE04, SectorE05.
SectorE02 group was found to be active in Bangladesh, India, Vietnam, the Netherlands, Sri Lanka, Pakistan, the United States, and Germany. The group distributed MS Word and Excel document malware disguised as conference events and administrative documents. Afterwards, additional malware was used to collect information from the infected system such as file details, process information, and screenshots, and send them to the C2 server.
SectorE04 group was found to be active in Pakistan and Malaysia. The group targeted on workers of government sectors to disseminate numerous MS Word documents, which were disguised as documents related to Sri Lanka. When executed, template files were downloaded from the C2 server, acting as the steppingstone for additional malicious activities.
SectorE05 group was found to be active in Pakistan, Australia, Japan, Hong Kong, China, and the United States. The group disseminated Windows CHM (Compiled HTML Help) format malware which was registered in the scheduler and stole system information.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorG Group Activities
In February 2023, activities by a total of 1 groups were identified, and the groups were SectorG01.
SectorG01 group was found to be active in India, South Korea, Israel, Venezuela, England, the United States, Dominican Republic, and Canada. The group disseminated Adobe PDF documents disguised as fund transfer confirmation documents to install malwares and carry out information theft activities.
SectorG hacking groups primarily target countries that are politically rivals with the supporting government. Their recent purpose is to collect high-quality information about the politics, diplomacy, and government activities of people or countries who are opposed to the supporting government.
7. Characteristics of SectorH Group Activities
In February 2023, activities by a total of 1 groups were identified, and the groups were SectorH03.
SectorH03 group was found to be active in Pakistan, India, the United States, and Singapore. The group targeted on government and education institutions to disseminate MS Word and PowerPoint documents disguised as cyber advisory, global executive Master of Business Administration program, and Indian administrative service documents, which were used to install malware for information theft activities.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, India, so it is analyzed that they will continue activities to collect advanced information regarding Indian government agencies’ military and politics to their need.
8. Characteristics of cybercrime group activities
In February 2023, activities by a total of 8 hacking groups were identified, and the groups were SectorJ04, SectorJ05, SectorJ09, SectorJ68, SectorJ76, SectorJ90, SectorJ92, and SectorJ94.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ04 group was found to be active in Columbia, the United States, Mexico, and Lebanon. The group used the Clop ransomware with the aim of securing financial resources.
SectorJ05 group was found to be active in Malaysia, Sweden, Turkey, and the United States. The group used malware disguised as a video call conference service software and used malware with downloader functions to set the base for executing additional malware.
SectorJ09 group continued to use their hacking strategy of inserting obfuscated skimming scripts in websites to collect username, address, email, phone number and credit card details from the payment page. In this activity, a JavaScript malware of a similar format to those found in the past was identified.
SectorJ68 group was found to be active in Algeria, Ukraine, the Netherlands, Germany, Uzbekistan, Russia, and India. The group used malware disguised as bills and used malware that collects information such as credential information and screenshots from the system.
SectorJ76 group was found to be active in Canada, Japan, Czech Republic, Germany, Romania, England, India, France, Sweden, the United States, Poland, South Korea, Australia, and Italy. The group exploited Google Ads, which displayed advertisements at the top of the search results, to lead the targets to access a phishing website impersonating a popular software, and used the Royal ransomware in the final stage.
SectorJ90 group was found to be active in the United States, India, Germany and Georgia. The group used phishing emails disguised as proposals, and attempted to steal information from the target’s system through infostealer malware.
SectorJ92 group was found to be active in Israel. The group used the DarkBit ransomware to encrypt the files, and generated a ransom note containing the contacts for discussing financial matters and indicating that that attack was geopolitically driven.
SectorJ94 group was found to be active in Hong Kong, Austria, Germany, the United States, Argentina, Bangladesh, Australia, England, India, Algeria, Iran, South Korea, Canada, and the Philippines. The group attached a OneNote document in the phishing email related to invoice, and attempted to steal system authorizations, carry out information collection and leak them through a backdoor malware.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
