Phishing Attack Activities: Threat Actors in Sheep’s Clothing (ENG)
Introduction
The idiom “beware of wolves in sheep’s clothing” is often used as a metaphorical representation of something that appears to be trustworthy on the outside but is hiding the truth and disguised in another form to deceive others.
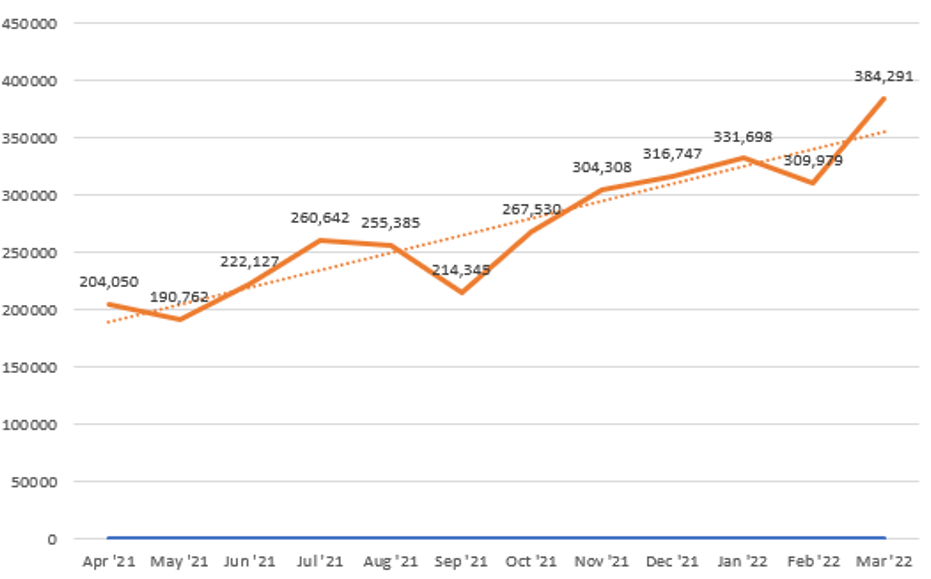
Phishing attacks are one of the attack techniques used by Threat Actors to steal information from individuals and organizations through tricking them. Just like a wolf in sheep’s clothing, specific channels such as emails or messengers are used to impersonate credible entities to steal sensitive information from the targets, such as account credentials. Reports by the Anti-Phishing Working Group, an international collaboration to mitigate and provide information on phishing attacks, claims that more than 1 million phishing attacks were carried out in the first quarter of 2022, an increase of over 67% in comparison to 2021.
[Figure 1: Phishing attacks from April 2021 to March 2022 (Source: APWG)]
The 2022 phishing attack database in the ThreatRecon Platform shows that SectorA groups, mainly targeted on South Korea to carry out phishing attacks. The frequency of phishing attack activities has increased to more than 2.5 times in comparison to 2021, and the main targets were identified to be South Korea’s research center and government sector workers. Under such circumstances, both individuals and organizations are implementing various cybersecurity measures against phishing attacks, but it could be observed that damage is still occurring due to the ongoing phishing activities of SectorA groups.
With this background in mind, this report aims to provide detailed information regarding phishing attack activities carried out by SectorA groups. Current status of phishing attacks by SectorA groups as analyzed by the ThreatRecon Platform, their main targets, characteristic analysis of phishing attacks, and real phishing cases will be discussed in the upcoming sections.
Current Status of Phishing Attacks
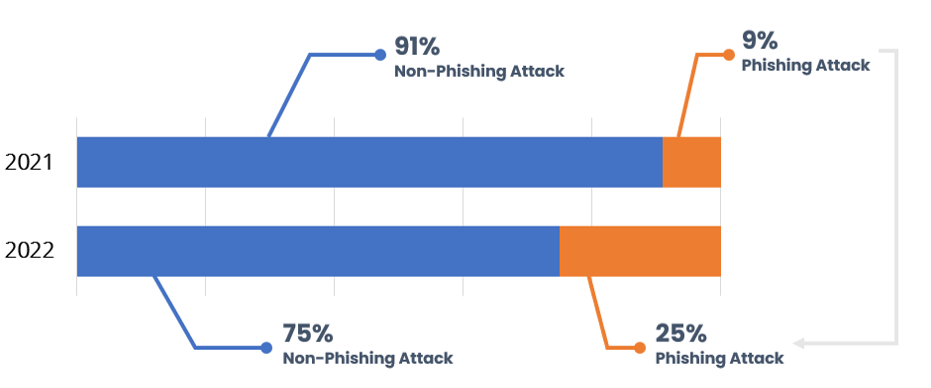
The ThreatRecon Team has observed that SectorA groups, have shown a rapid increase in phishing attacks from 2021 to 2022. The percentage of phishing attacks among all cyberattacks were limited to 9% in 2021, which increased by 2.5 times to become 25% of all cyberattacks by the group in 2022. The reasoning behind this phenomenon is because phishing attacks tend to have lower technical complexity in comparison to other cyberattack techniques and have a wider range of victims across diverse industries through utilizing daily tools such as emails, social media, and messengers.
[Figure 2: Past 2 years of statistics on phishing attacks by SectorA groups]
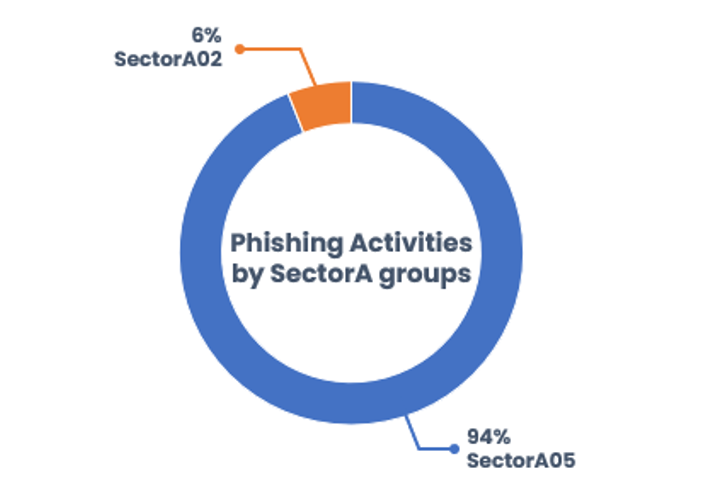
The ThreatRecon Team has classified SectorA into 7 subgroups, namely SectorA01 through SectorA07. Phishing attacks observed in 2022 were carried out by SectorA02 and SectorA05, and as shown in [Figure 3],SectorA05 accounted to be the attacker of 94% of total phishing attacks carried out by SectorA groups, followed by SectorA02.
[Figure 3: Distribution of phishing attacks by SectorA groups]
Main Targets of Phishing Attack Activities
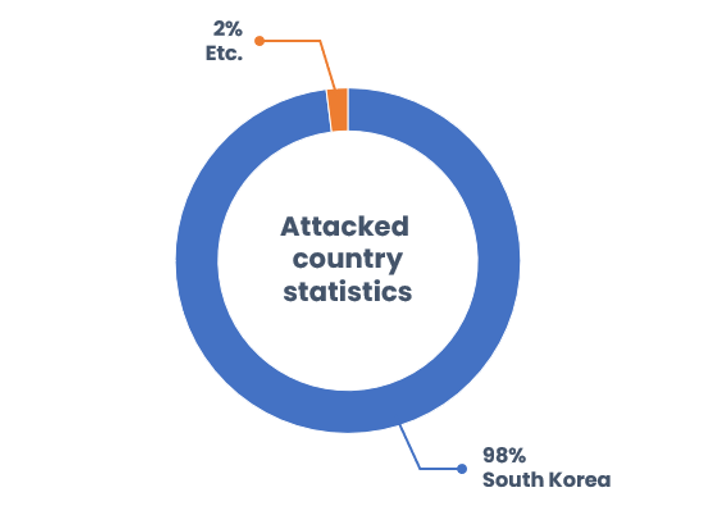
As previously mentioned, SectorA05 group most actively carries out phishing activities among SectorA groups, and analysis of the victims’ geographical location shows that South Korea was the most targeted country, accounting for 98% of all attacks, as seen in [Figure 4].
SectorA05 mainly carries out hacking activities with the aim of collecting critical information related to politics, diplomacy and military activities of South Korea, so the phishing attacks are seen as an extension to this aim of attacks.
[Figure 4: Distribution of countries targeted by SectorA groups]
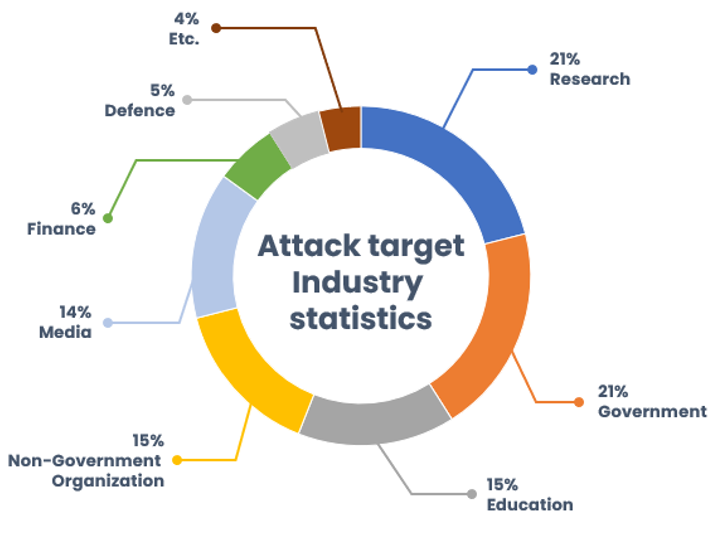
Analysis of industries affected by phishing activities caused by SectorA groups shows that research sector and government industries has been targeted the most frequently by 21% each, followed by education, NGO (Non-governmental organization), media communications and finance.
The research centers targeted by the group were organizations focused on studying or expressing opinions on topics such as social, political, economic, technology. The primary targets were identified to be researchers specializing in the field of North Korean policies.
SectorA groups attempted to steal account credentials of popular portal sites in South Korea through phishing attacks. This is because any additional internal information related to research and government institutions discovered in the stolen accounts could act as the steppingstone to infiltrating into the internal systems. In addition, the stole portal site accounts could be linked to the portal site for accessing information saved in email or cloud services that are related to other organizations, which could be used to expand the range of targets.
[Figure 5: Statistics of industries targeted by SectorA groups]
Other targets included individual investors of stocks, cryptocurrencies and real estate, who showed a common characteristic of being active in Naver Blogs, and often posted contents related to investments.
The government supporting SectorA groups is facing an economic crisis, recording the lowest economic growth rate currently. Analysis shows that individual investors exposed in online spaces such as communities, forums and social media are targeted for phishing attacks with the aim of securing foreign currency due to this economic crisis in government supporting SectorA groups.
[Figure 6: Blogs of individual investors targeted for phishing attacks]
Cases of Phishing Attacks
1) Phishing Attacks Targeted on Research Centers and North Korea Related Personnels
SectorA05 group has sent out phishing emails to researchers studying unification strategies in a research institute under the Ministry of Foreign Affairs and a North Korean defector who works in the field of North Korea related policies.
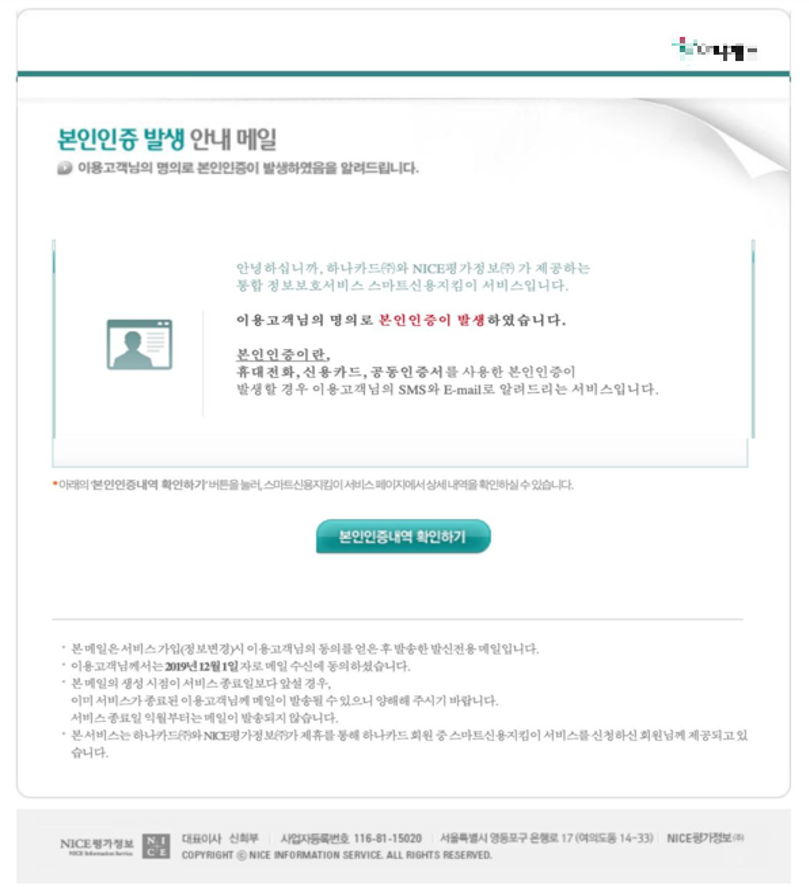
The email contained a body text mentioning that a problem occurred with personal identification of cards issued by a specific card company, together with a ‘Check my personal authentication history’ button. When the button is clicked, targets were redirected to a phishing site.
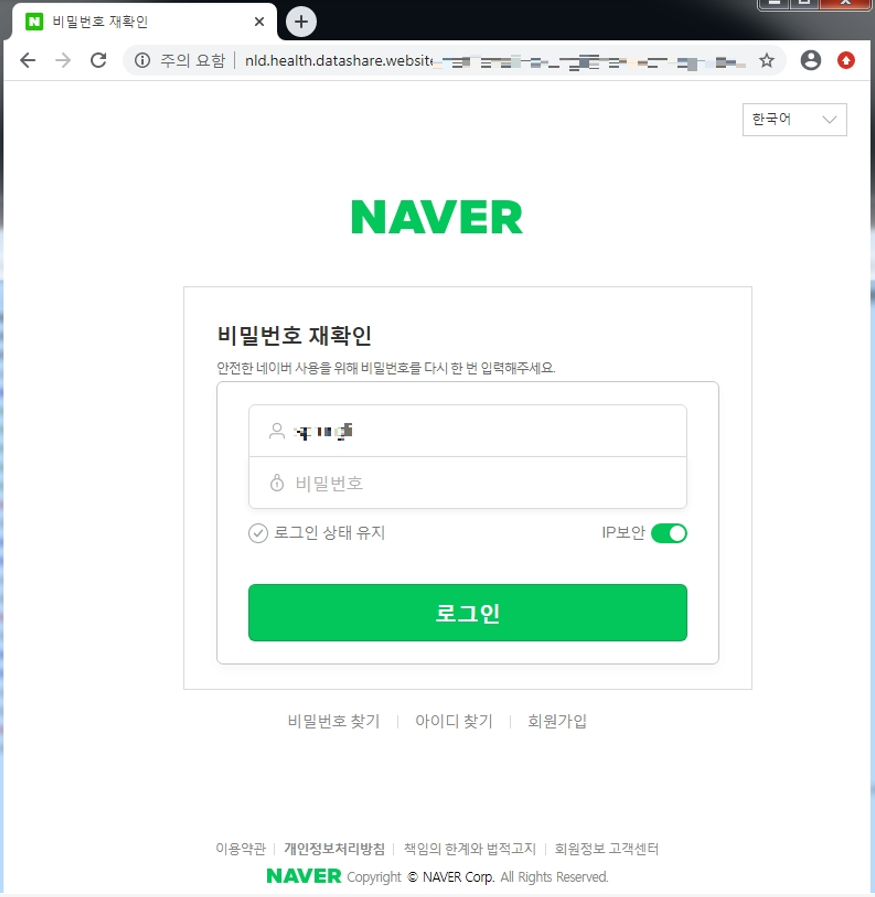
The phishing website developed by SectorA05 group was disguised as a login page for Naver, a popular portal site in South Korea. When account credentials were input, they were sent to the C2 server.
[Figure 7: Body of the phishing email impersonating a card company]
[Figure 8: Phishing webpage disguised as Naver login page]
2) Phishing Attacks Targeted on Media Communication Workers
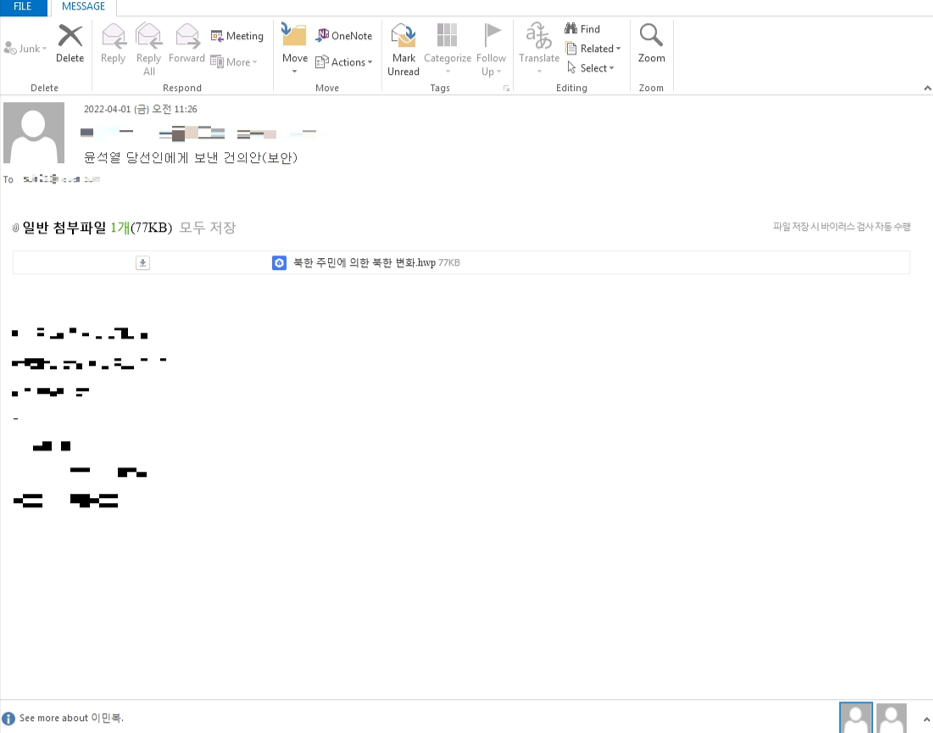
SectorA05 group sent out phishing emails to workers in North Korea related broadcast stations, and the mail was disguised to have been sent by North Korean defected human rights activist who was a close acquaintance of the target.
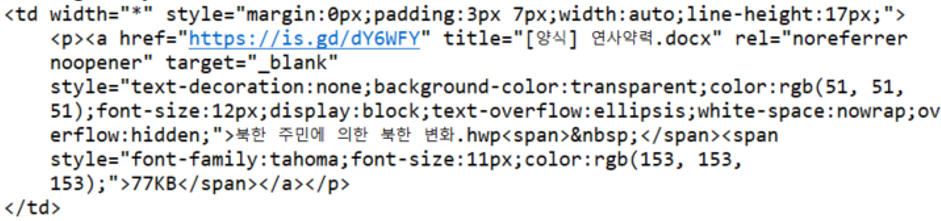
The email appears to contain an attached file named “Changes in North Korea by North Korean Residents.hwp”, which was not an attachment but a hyperlink that redirected the targets to a phishing website.
[Figure 9: Body of the phishing email sent by SectorA05]
[Figure 10: Phishing link address in the phishing email]
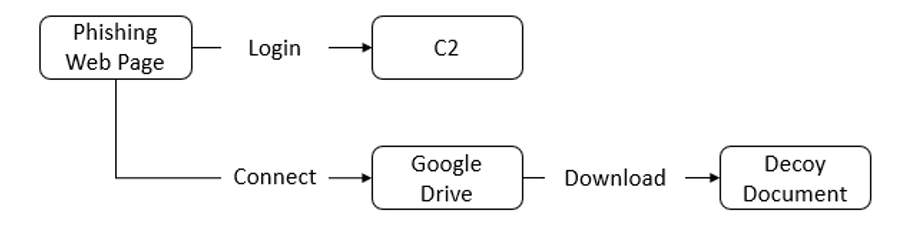
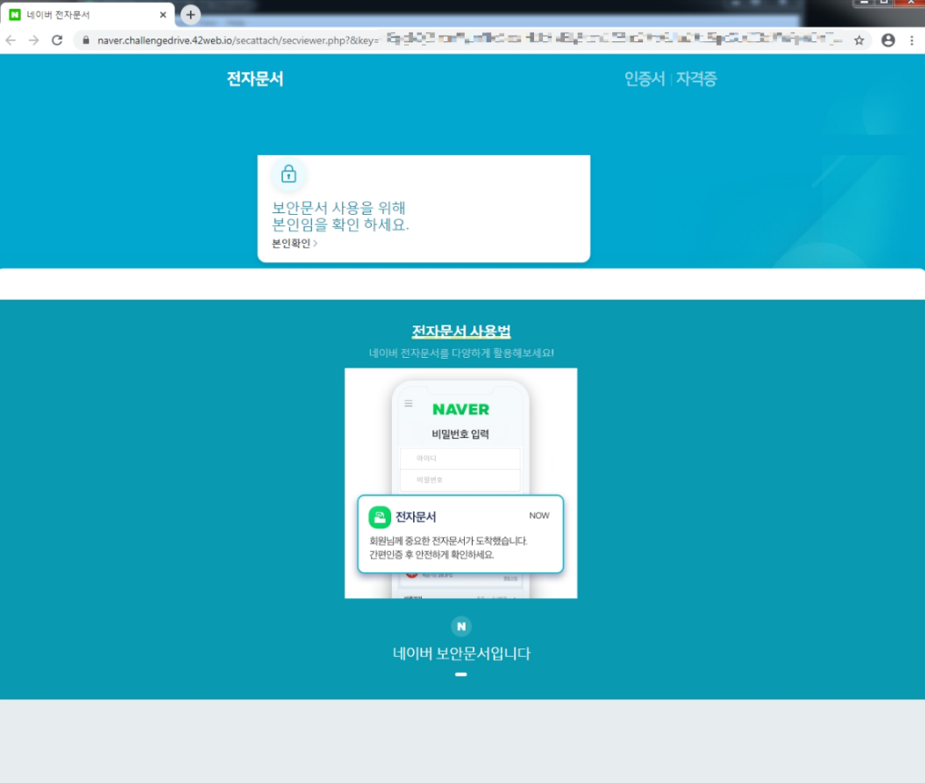
The phishing websites were disguised as the e-document page of Naver, where users could check notification documents sent by public, financial and private institutions. The phishing webpage led the targets to log into the page, and the input account credentials were transferred to the C2 server. Afterwards, a bait document under the same name as the supposedly attached file in the phishing email is downloaded from Google Drive.
[Figure 11: Phishing webpage activation process of SectorA05]
[Figure 12: Phishing webpage disguised as e-document page of Naver]
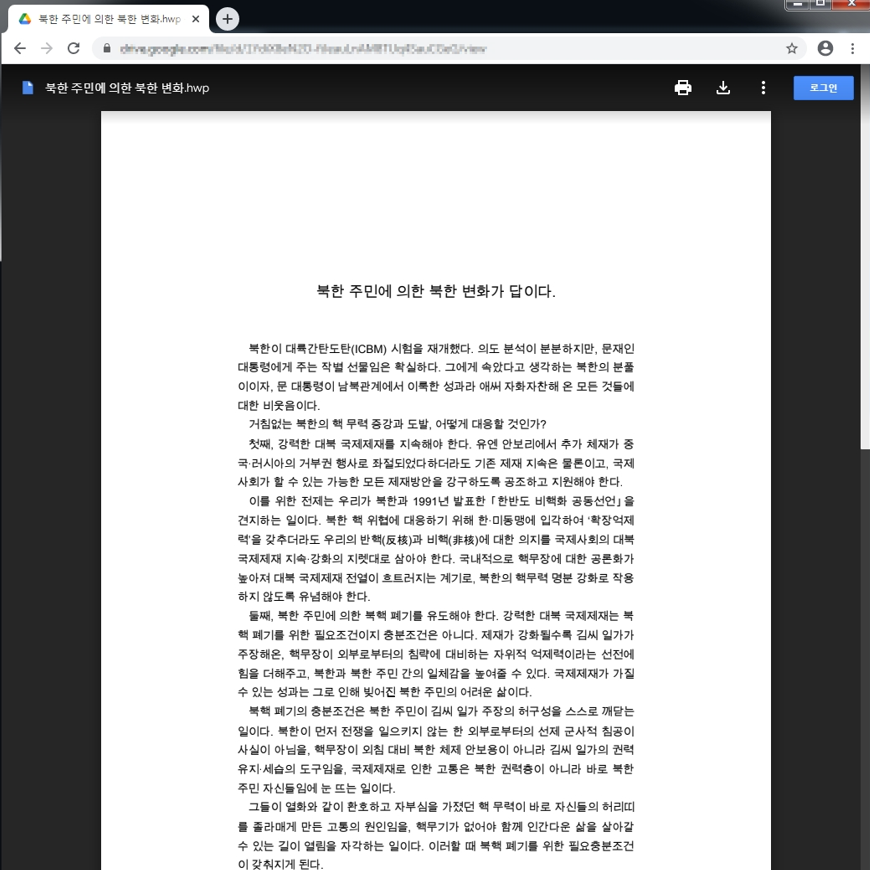
[Figure 13: Part of the bait document in Google Drive]
3) Phishing Attacks Targeted on University Employees
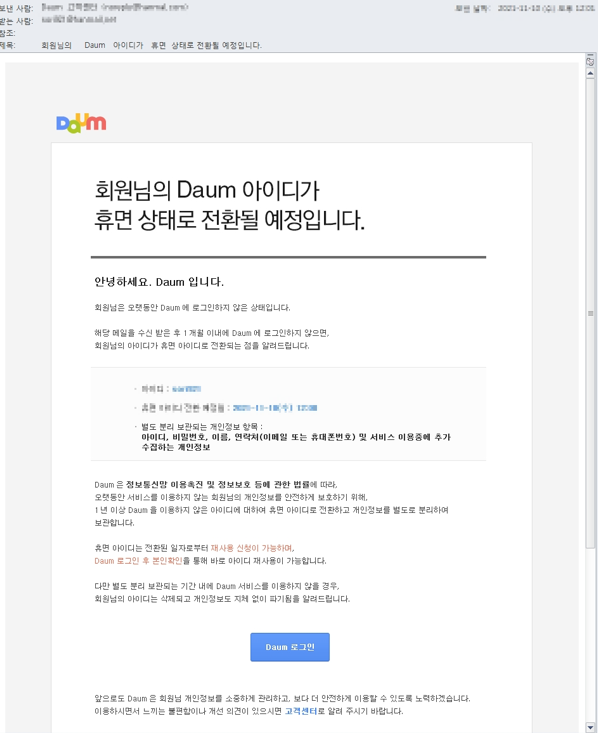
SectorA02 group targeted on a specific university professor and the university offices in South Korea to deliver phishing emails disguised to have been sent from customer support of Daum, a South Korean portal site.
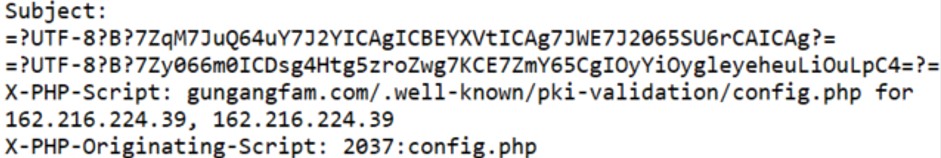
The email contained a message notifying the target that their account would be deactivated due to inactivity, and that they could find out more through logging in. The email contained a ‘Daum login’ button, which redirected the targets to a phishing website. The delivered email was identified to have been sent from a specific IP address (162.216.224.39), utilizing web hosting services by SupremeBytes, in the United States.
[Figure 14: Phishing email impersonating Daum Customer Support]
[Figure 15: Sender IP address in phishing email]
Characteristics of Phishing Attacks
1) Disguising as Internet Services Commonly Used by South Koreans
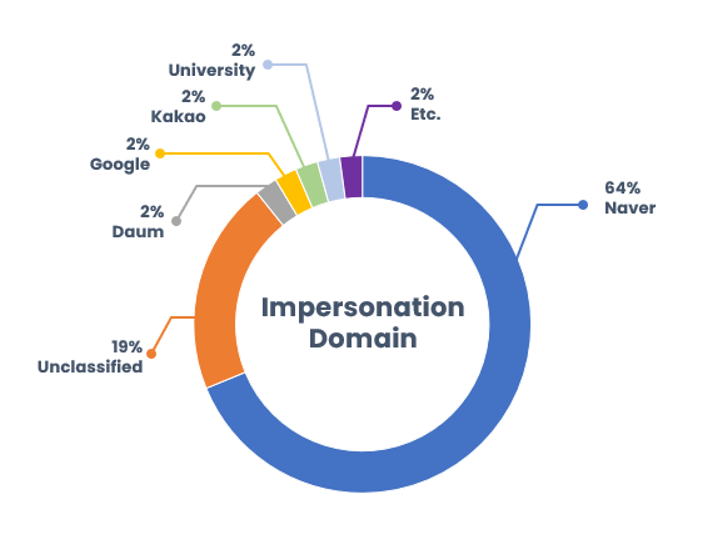
SectorA groups were identified to have been using domains disguised as various internet services. Excluding the unclassified websites, the most commonly impersonated internet service was the Naver portal site, accounting for 64% of all impersonations. Following this was portal websites like Daum, Google, and Kakao, and other exploited domain names included those from universities, financial institutions, and public agencies.
SectorA groups mainly impersonated popular portal sites with high usage rate by South Koreans, to carry out phishing attacks on South Korea. They have used the method of disguising as normal services such as e-document service provided by Naver to lead targets to checking phishing emails without suspicion.
[Figure 16: Domains of services impersonated by SectorA groups in phishing attacks]
The domains used in phishing attacks were disguised as follows.
Classification |
Disguised Domain |
|
| 1 | Naver | naver-sec[.]site
naver.cloudfiles[.]epizy.com navocorp[.]link |
| 2 | googlmeil[.]com
accounts.qocple[.]epizy.com |
|
| 3 | Daum | daum-privacy[.]com
daurn[.]in.net nid.daurn[.]in.net |
| 4 | Kakao | Kakaocop[.]com
kakao.cloudfiles[.]epizy.com |
| 5 | Public institutions | Kisa[.]42web.io |
| 6 | Universities | snu.cloudfiles[.]epizy.com
dankook.onedviver[.]epizy.com |
| 7 | Financial institutions | hanacard.navceo[.]website
cood.nonghyup[.]website |
[Table 1: Some domains disguised as specific organizations and institutions]
2) Utilizing Top-Level Domain (TLD)
The top-level domain refers to the unique identifier used to represent the classification of institution, country, or registered address by domains, such as ‘.com’ or ‘.org’.
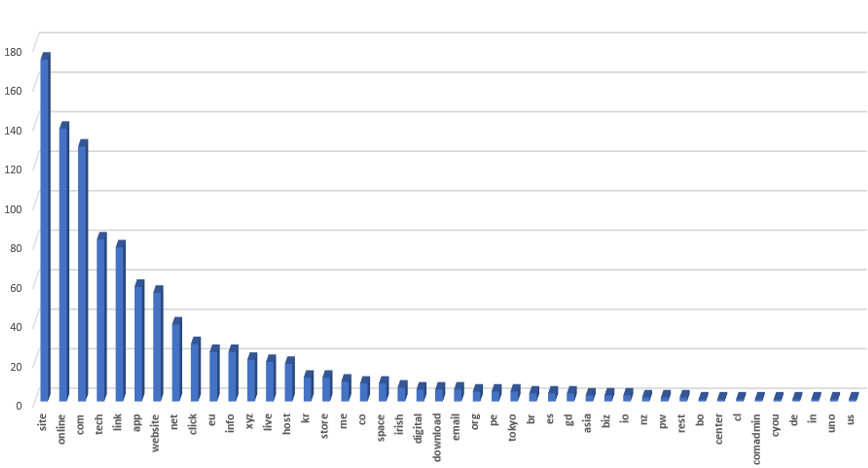
A total of 44 TLDs were identified in phishing attacks by SectorA groups, and 80% of all domains were found to belong to the top 10 TLDs.
As mentioned in the previous section, phishing domains used hostnames similar to the real domain name to disguise themselves as popular internet services with high usage rate such as Naver or Google, and utilizing TLDs such as ‘.site’, ‘.online’ and ‘.tech’.
Phishing domains analyzed in the previous context were created in a form similar to the actual domain name to disguise themselves as high-occupancy internet services such as Naver and Google. They also utilized top-level domains such as ‘.site’, ‘.online’, and ‘.tech’.
[Figure 17: Statistics of TLDs used in phishing attacks by SectorA groups]
3) Exploitation of Overseas Web Hosting Services
Domains used in phishing attacks were identified to have been registered through various internet web hosting services. A total of 20 web hosting services were identified from phishing attacks by SectorA groups, and they were mainly located in Europe and North America.
Domain Hosting Service |
Service Location |
|
| 1 | 1API GmbH | Germany |
| 2 | Atak Domain | Turkey |
| 3 | Danesco Trading Ltd. | Cyprus |
| 4 | Endurance Domains Technology LLP | India |
| 5 | Enom | United States |
| 6 | Gabia | South Korea |
| 7 | Gandi SAS | France |
| 8 | GMO | Japan |
| 9 | GoDaddy | United States |
| 10 | Hosting Concepts | Netherland |
| 11 | Hostinger | Lithuania |
| 12 | INAMES | South Korea |
| 13 | Key-Systems GmbH | Germany |
| 14 | MarkMonitor | United States |
| 15 | Name.com | United States |
| 16 | NameCheap | United States |
| 17 | NetEarth One | United States |
| 18 | PublicDomainRegistry | India |
| 19 | Tucows Domains | Canada |
| 20 | Whois Corp | South Korea |
[Table 2: Web hosting services related to the identified domains]
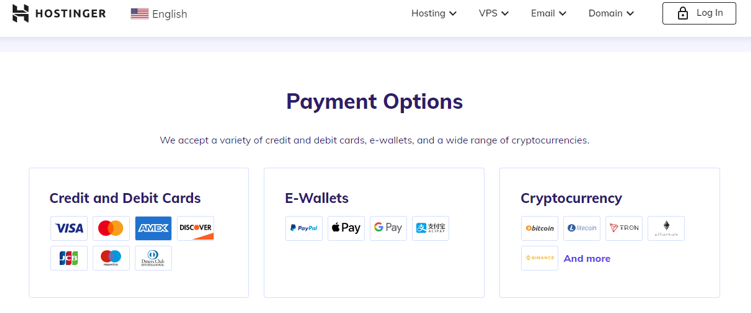
Such overseas web hosting services could be protected based on the legislation of the country where the services are located, and they take advantage of the fact that international collaboration and investigations are difficult, to hide their identity and avoid international investigations. In addition, some overseas web hosting services provide cryptocurrency payment methods such as BitCoin, allowing users to stay anonymous during payment as well.
[Figure 18: Payment method of overseas web hosting]
SectorA groups are exploiting various web hosting on top of what have been mentioned, and the overseas web hosting services used by the group provides sub-domains as shown in [Table 3] for user convenience, allowing for identification of web hosting services.
Web Hosting Service |
Second Level Domain |
|
| 1 | Fleek | *.fleek.co |
| 2 | FreeHostingEU | *.eu3.biz
*.eu3.org *.eu5.net *.me.pn |
| 3 | Glitch | *.glitch.me |
| 4 | Infinityfree | *.epizy.com
*.rf.gd *.42web.io *. infinityfreeapp.com |
| 5 | MYARTSONLINE | *.myartsonline.com |
| 6 | Netlify | *.netlify.app |
[Table 3: Domain characteristics of overseas web hosting services]
Conclusion
We have taken a look at the phishing attack activities carried out in 2022 by SectorA groups.
An increase in phishing attacks by SectorA groups are analyzed to be a result of the high efficiency of phishing attacks, characterized by their lower complexity and low resource consumption in comparison to other hacking techniques.
The groups were identified to be targeting research centers and government institutions through impersonating internet services with high usage rate in South Korea, such as Naver, Google and Kakao, with the aim of collecting critical information on economy, politics and national defense held by various organizations in South Korea.
On top of that, the government supporting SectorA groups are facing an economic crisis of recording the lowest economic growth rate, thus they are seen to have expanded their targets to individual investors in stocks, cryptocurrency and real estate who are active in Naver Blogs.
With such a situation in mind, security organizations should utilize cyber threat intelligence to carry out cybersecurity awareness workshops for employees, based on actual phishing attack cases. In addition, they should acquire cyber threat intelligences on domain and phishing webpages used in phishing attacks to quickly identify hacking techniques and strategies used by hacking groups depending on their aim of hacking, to implement response measures appropriate for the organization’s situation.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.