2022 Activities Summary of SectorA groups (ENG)
Summary
In 2022, hacking activities by a total of 7 SectorA subgroups were identified. The groups carry the aim of collecting advanced information such as political and diplomatic activities of the South Korean government, and simultaneously conduct hacking activities around the globe to secure financial resources.
While SectorA groups generally utilize malware in the form of files such as Microsoft Word and Excel, we also confirmed the increasing use of phishing web pages disguised as high-traffic internet services such as Naver and Google for their attacks.
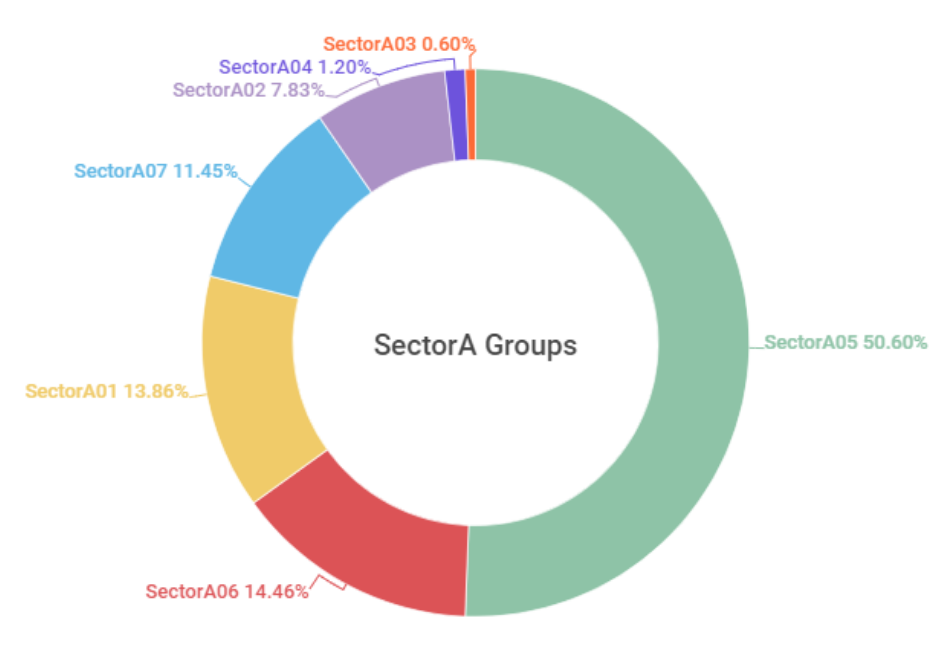
An analysis of the activity of the SectorA groups during the year 2022 showed that the activity of SectorA05 group was the most prominent, followed by the activities of SectorA06 and SectorA01 groups.
[Figure 1: Activity levels of SectorA subgroups in 2022]
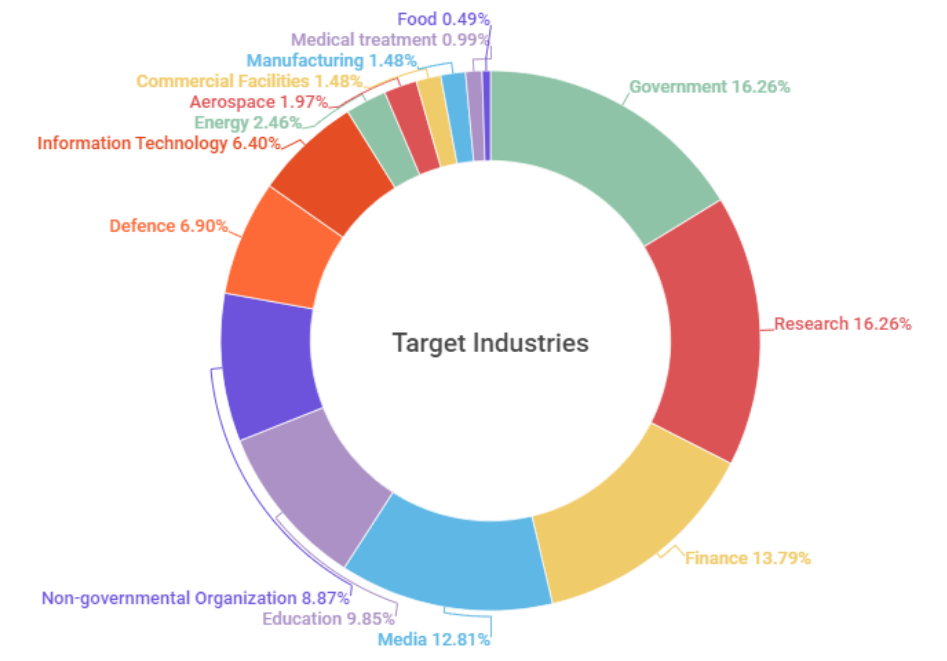
Looking at the industries that have been major targets of the SectorA groups attacks, the largest number of attacks were aimed at individuals or systems working in government agencies and research fields, followed by the financial, broadcasting, and education industries.
The targeted organizations include those in the government and research fields that conduct research on social, political, economic, and technological subjects or express opinions on such subjects, and are mainly identified as those related to North Korea or employed in related fields.
[Figure 2: Distribution of targeted industries in 2022]
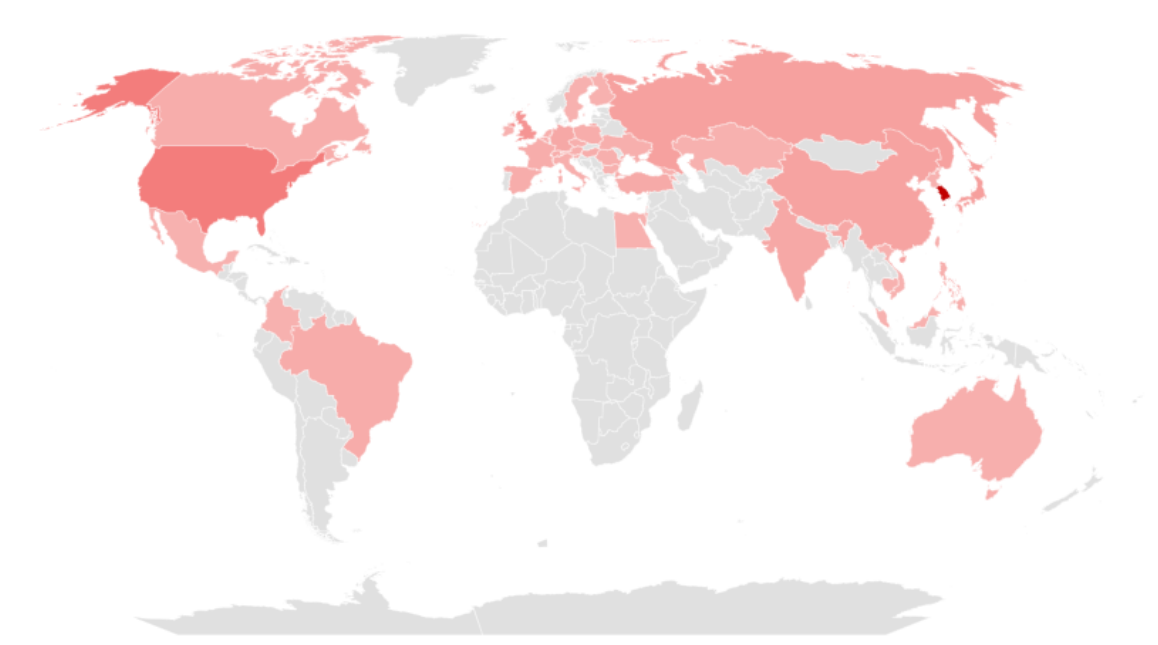
The following figure is a map showing the countries that were targeted by SectorA Groups in 2022, with a darker shade of red indicating a higher frequency of attacks. From the figure, it could be deduced that the group carried out the greatest number of hacking activities on South Korea, followed by the United States, the United Kingdom, and Russia.
[Figure 3 : Mainly targeted countries by SectorA groups in 2022]
2022 Activities of SectorA Groups
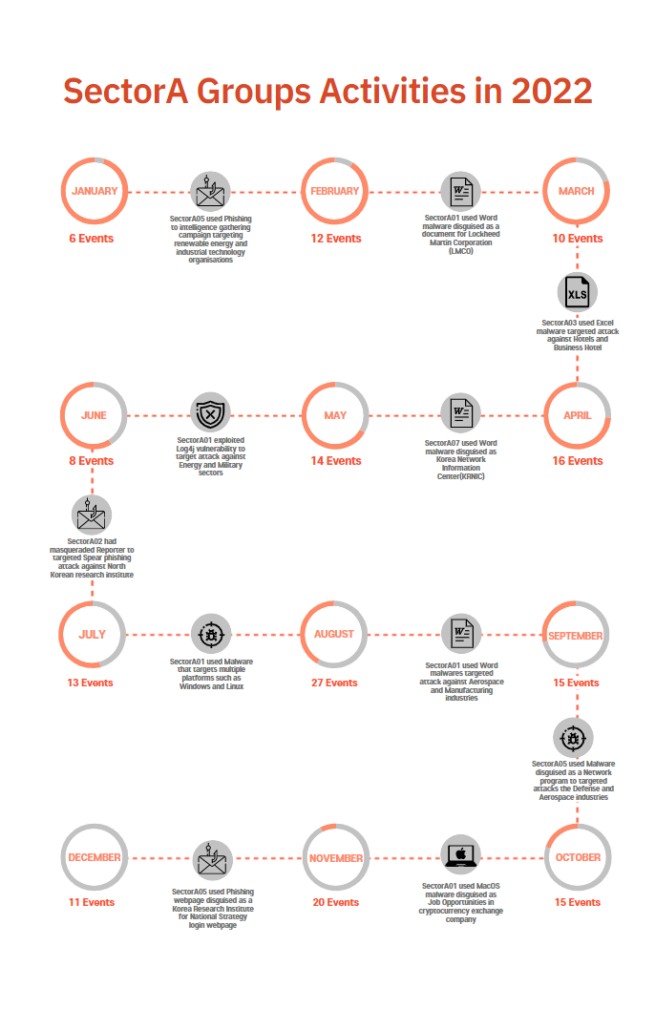
The following is a timeline of the hacking activities carried out by SectorA groups as identified in 2022 and the detailed information of monthly activities of the group.
[Figure 4: Main activities and events by SectorA Group in 2022]
JANUARY
In January 2022, activities by a total of 3 hacking groups were identified, and the groups were SectorA02, SectorA05, and SectorA07.
SectorA02 group was found to be active in South Korea. Their operation targeted North Korea-related professionals, using phishing emails disguised as credit card statements.
SectorA05 group was found to be active in South Korea and Bulgaria. The group distributed malicious code in the form of a Korean file (HWP) disguised with a title related to North Korea activities in this operation.
SectorA07 group was found to be active in Russia. The group targeted government agencies and foreign affairs officials of a specific country by sending spear-phishing emails.
FEBRUARY
In February 2022, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, and SectorA06.
SectorA01 group was found to be active in Spain, Mexico, India, Slovenia, and Russia. In these activities, the group disguised itself as companies belonging to the financial, insurance, and defense industries, and spread malware.
SectorA02 group was found to be active in South Korea. In this operation, the group disseminated HWP format malwares disguised under themes on social issues related to the South Korean presidential election.
SectorA05 group was found to be active in South Korea. In this operation, the group targeted public institutions and media industry personnel by sending Spear Phishing emails.
SectorA06 group was found to be active in Ukraine, Germany, Israel, Australia, Georgia, the United States, Italy, the United Kingdom, Finland, and Colombia. In this operation, the group used shortcut (LNK) files disguised as subjects related to “profit and loss statements”, “job postings”, and “payroll”.
MARCH
In March 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorA02, SectorA03, SectorA05, SectorA06 and SectorA07.
SectorA02 group was found to be active in South Korea. In this operation, the group disguised themselves as officials of a central government agency in South Korea and carried out the attack. They set up a phishing website to collect information and used a decoy document in the form of a HWP file to attract the interest of the target.
SectorA03 group was found to be active in Macau. In this operation, the group targeted officials of 20 businesses, including hotels, lodging, and restaurants in Macau, using spear phishing emails.
SectorA05 group was found to be active in South Korea and Hong Kong. The group used multiple phishing emails disguised as electronic documents sent from government agencies to carry out attacks.
SectorA06 group was found to be active in South Korea, Japan, France, Singapore, the United States, and the United Kingdom. The group utilized a help file format called CHM (Compiled HTML File) in their attack during this operation.
SectorA07 group was found to be active in South Korea. In this activity, the group used MS Word documents disguised as product brochures for the attack.
APRIL
In April 2022, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA05, SectorA06, and SectorA07
SectorA01 group was found to be active in Brazil, Germany, and the United States. In this activity, the group disguised themselves as corporate recruiters and sent spear-phishing emails to individuals working in finance, news, and IT fields.
SectorA05 group was found to be active in South Korea, Japan, the United States, China, and Austria. The group disguised themselves as broadcasting company officials and sent spear-phishing emails targeting North Korean human rights organizations and activists in this operation.
SectorA06 group was found to be active in the United Kingdom, China, South Korea, the United States, and Japan. The group utilized Compiled HTML File (CHM) format help files in their attack during this activity.
SectorA07 group was found to be active in South Korea, Japan, Canada, and Germany. In this activity, the group disguised themselves as a specific company and sent spear-phishing emails. The email body contains various topics that the targets might be interested in, such as ‘customer information’, ‘loans’, ‘tax evasion reports’, ‘complaints’, ‘contracts’ and prompts the target to execute the attached MS Word document.
MAY
In May 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, and SectorA07.
SectorA01 group was found to be active in Romania, Japan, Netherlands, and Spain. In this operation, the group targeted engineering companies in the energy and military sectors and damaged their systems by exploiting the Log4Shell vulnerability with an initial infiltration method.
SectorA02 group was found to be active in South Korea and Turkey. In this operation, the group targeted journalists from media companies and individuals involved in North Korean affairs by sending spear-phishing emails.
SectorA05 group was found to be active in South Korea, the United States, and Japan. In this activity, the group distributed various types of malware in different file formats targeting individuals working in the political and diplomatic fields.
SectorA06 group was found to be active in South Korea and the United States. The group once again utilized the compiled HTML file format, CHM, for its attacks following its April attacks.
SectorA07 group was found to be active in South Korea. The group used a form of attack that involved sending spear-phishing emails disguised as incident reports or virtual currency investment information with attached malware.
JUNE
In June 2022, activities by a total of 3 hacking groups were identified, and the groups were SectorA02, SectorA05, and SectorA06.
SectorA02 group was found to be active in South Korea. In this operation, the group targeted on personnel related to North Korea by sending Spear Phishing emails to them. The sent email, impersonating a writer of a broadcasting station, included a malicious HWP document attachment containing content about conducting interviews.
SectorA05 group was found to be active in South Korea, the Philippines, India, Hong Kong, and China. In this activity, the group sent spear-phishing emails to broadcasting company officials.
SectorA06 group was found to be active in Canada and Cambodia. In this activity, the group used a malicious code in Windows shortcut (LNK) file format disguised as content related to democracy.
JULY
In July 2022, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA04, SectorA05, and SectorA07.
SectorA01 group was found to be active in Japan, the United Kingdom, the United States, South Korea, and Austria. In this operation, the group targeted companies in the medical and health fields, spreading ransomware and using it to encrypt internal medical information. The group then demanded a ransom in exchange for decrypting the information, indicating their intent to engage in extortion.
SectorA04 group was found to be active in Germany and Hungary. In this operation, the group distributed ransomware to small businesses in Europe and used the encrypted internal information as leverage to demand a ransom. This activity was believed to be carried out for the purpose of extortion.
SectorA05 group was found to be active in South Korea. The group targeted university professors in defense, diplomacy, security, and unification fields, as well as journalists and researchers, with spear-phishing emails.
SectorA07 group was found to be active in Russia, Malaysia, Poland, Czech Republic, and Israel. In this operation, the group used spear-phishing emails with compressed files attached as an attack vector.
AUGUST
In August 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06 and SectorA07.
SectorA01 group was found to be active in China, the United Kingdom, Brazil, Turkey, the United States, India, and Singapore. In this operation, the group distributed malware disguised as an engineer recruitment document from a specific cryptocurrency exchange to individuals working in various industries such as finance, IT, aerospace, and manufacturing.
SectorA02 group was found to be active in South Korea. The group distributed malware disguised as document files with titles such as “business contact” or “transaction history”. They also seized control of a Korean outsourcing service company’s web server and used it as a C2 server.
SectorA05 group was found to be active in South Korea and the United States. In this operation, the group sent spear-phishing emails disguised as NFT (Non-Fungible Token) reward token announcements.
SectorA06 group was found to be active in Hong Kong, the United Kingdom, the United States, India, China, Italy, and Russia. In this operation, the group distributed malicious code in the form of Windows shortcut (LNK) files targeting individuals working in the financial industry. The malware was disguised with filenames related to employment, salary negotiations, revenue distribution that the target may find interesting.
SectorA07 group was found to be active in Russia and South Korea. In this operation, the group distributed a malicious code in MS Word format using the Template Injection technique. The Word malware was disguised as a document verified by a specific security solution in South Korea as a safe document written by a Korean language education center at a specific university in South Korea.
SEPTEMBER
In September 2022, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA05, SectorA06, and SectorA07.
SectorA01 group was found to be active in South Korea, India, Hungary, the United States, Canada, Japan, Turkey, Spain, and Ireland. In this operation, the group targeted individuals working in the news and media industries with spear phishing attacks. Using social engineering techniques, the group delivered malicious code through messaging apps that allowed for communication with C2 servers and performed functions such as collecting system information, establishing remote desktop protocol (RDP) connections, and uploading and downloading files.
SectorA05 group was found to be active in South Korea, Vietnam, the Philippines, Hong Kong, and the United States. In this operation, the group targeted government agencies, defense, media, and major think tank officials. To deliver malware to their targets, the group used a large file attachment service on a portal site to send malicious code in document formats such as HWP and Word, and finally attempted to download and execute additional malware using OLE (Object Linking and Embedding) objects embedded within the document, with an aim to obtain system privileges and steal information.
SectorA06 group was found to be active in Hong Kong, the United Kingdom, the United States, India, China, Italy, and Russia. In this activity, the group targeted individuals working in the investment and finance industries using spear phishing emails. The email contained malicious code download links and induced the execution of malicious code by including content related to performance distribution that the target may be interested in. Ultimately, the group performed functions to collect the system information of the target and send it to the C2 server.
SectorA07 group was found to be active in Russia, South Korea, France, and Sweden. In this activity, the group utilized spear phishing emails to attack Russian embassy officials. The email sent to the target was disguised to be sent by an embassy employee and contained a PowerPoint malware with a malicious macro script attached. The code eventually registered itself to the scheduler and performed the function of continuously sending system information to the C2 server.
OCTOBER
In october 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06 and SectorA07.
SectorA01 group was found to be active in Taiwan, the United Kingdom, India, Czech Republic, Hungary, Russia, the United States, South Korea, the Netherlands, and Belgium. The group targeted individuals in various industries such as defense, finance, media, pharmaceuticals, and aviation. They used an ISO image compressed file disguised as a resume for the initial access method, which included a Portable Executable (PE) format malware and a text file. Ultimately, they used the tactic of creating and operating a DLL file protected by Themida Protector to take control of the system.
SectorA02 group distributed malicious code in the form of PE (Portable Executable) in their recent activity. When the malicious code is executed successfully, it performed the function of downloading and executing additional malicious code from the C2 server, and ultimately, it performed the function of capturing system information, user input values, encoding them, and transmitting them to the C2 server.
SectorA05 group was found to be active in South Korea. The group targeted individuals in various industries, including government agencies, research institutes, media outlets, political parties, and schools. They exploited the disruption of a mobile messenger service in Korea and sent spear-phishing emails to take advantage of the situation. Ultimately, they used a tactic to gain control of the system by using Themida Protector-protected malware code.
SectorA06 group was found to be active in Russia, the United States, the United Kingdom, Switzerland, Hong Kong, and Australia. The group distributed a malicious code in the form of a shortcut (LNK) disguised as a decoy document and password file in a compressed archive. Ultimately, the group created a malicious code in the startup program folder to maintain persistence on the infected system and performed functions to collect system information using WMI (Windows Management Instrumentation) commands.
The SectorA07 group was found to be active in South Korea. The group distributed a MS Word malware disguised as an encryption currency company issue, using a template injection technique that downloads and executes a template file containing malicious VBA scripts. Ultimately, the VBA script collected OS version, computer name, and network information using WMI (Windows Management Instrumentation) commanded and sent it to the C2 server.
NOVEMBER
In Novemer 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06 and SectorA07.
SectorA01 group was found to be active in South Korea, the United Kingdom, Romania, the United States, Armenia, Turkey, and Egypt. The group exploited vulnerabilities in electronic signature and data encryption/decryption solutions to disable security programs and infiltrate internal systems. They then used tactics to execute additional malware within the internal system to take control of the system.
SectorA02 group was found to be active in South Korea. The group distributed MS Word malicious code targeting media outlets and individuals involved in North Korean affairs. The documents used in the attack were disguised as topics of interest to the targets, such as the Itaewon murder case, issue reports from the Korea Institute for Economics and Security, and the Northern Limit Line (NLL).
SectorA05 group was found to be active in South Korea and France. The group distributed MS Word documents disguised as news questionnaires, resumes, and other forms, targeting government agencies, research institutes, energy companies, and the media industry. The documents were analyzed to be maliciously modified and redistributed versions of documents provided by the Ministry of Justice.
SectorA06 group was found to be active in Japan. The group distributed a malicious code in the form of a Windows shortcut (LNK) disguised as a password file. Ultimately, they used msiexec (Windows installer utility) to download and execute MSI (Microsoft Installer) files from the C2 server to collect information and employed tactics to take control of the system.
SectorA07 group was found to be active in the United States and Singapore. The group used CHM (Compiled HTML Help) files for their attacks, disguised as topics related to the Chinese premier. Ultimately, the attacks used PowerShell commands to collect computer and user’s name information from infected systems and transmit it to a C2 server.
DECEMBER
In December 2022, activities by a total of 4 hacking groups were identified, and the groups were SectorA02, SectorA05, SectorA06, and SectorA07.
SectorA02 group was found to be active in South Korea and Switzerland. The group distributed MS Word malware using template injection technique targeting media and NGO personnel. When executed, the malware downloaded and ran a Rich Text Format (RTF) file, and ultimately performed the function of downloading an OLE (Object Linking and Embedding) object containing macros from the C2 server.
SectorA05 group was found to be active in South Korea and France. The group targeted individuals working in broadcasting, telecommunications, and universities, and conducted phishing attacks to steal account information. It was confirmed that they created phishing pages for the purpose of inducing the target to access them.
SectorA06 group was found to be active in Poland, the United States, and Switzerland. The group used CHM (Compiled HTML Help) files disguised as virtual currency exchange projects and recruitment-related content for their attacks. The CHM malware used in the attack downloads and executes MSI (Microsoft Installer) files from the C2 server using msiexec (Windows Installer utility). The group employed tactics to collect information from infected systems and take control of them.
SectorA07 group was found to be active in South Korea. They distributed a Microsoft Word (Word) malware using the Template Injection technique, disguised as personal information. If the target executes the document, it performs a function of downloading and executing a CAB (Windows Cabinet File) file from the C2 server.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.