2022 Activities Summary of SectorB groups (ENG)
Summary
In 2022, hacking activiites by a total of 22 SectorB subgroups were identified. The groups carry the aim of collecting advanced information such as political and diplomatic activities of worldwide government institutions. These groups show a trend of sharing malwares or vulnerabilities with one another to carry out their hacking activities.
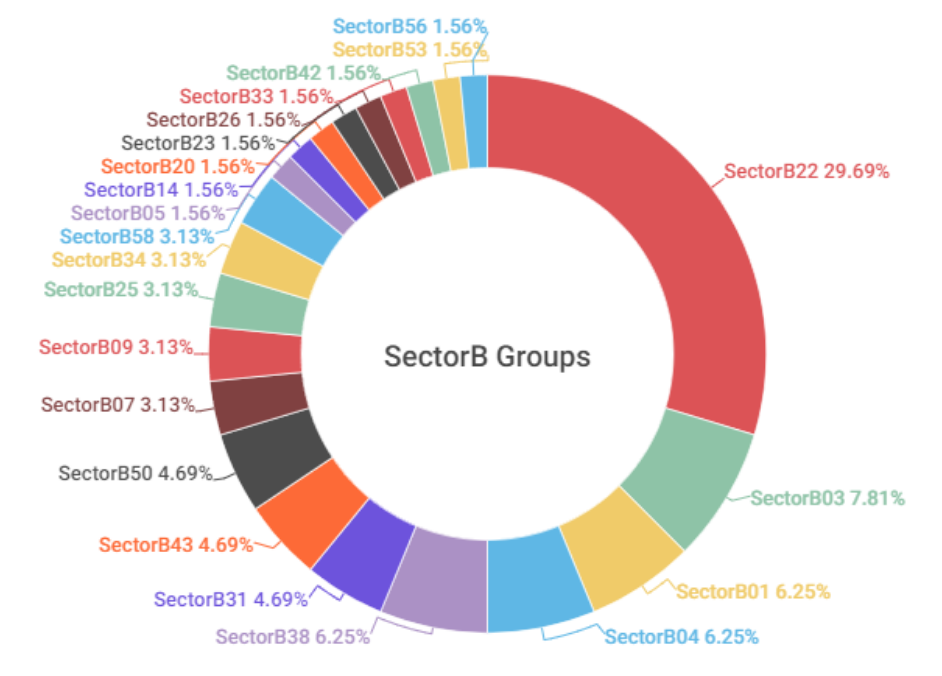
An analysis of hacking activities by SectorB groups in 2022 showed that there was a total of 22 active subgroups in the year, with activities by SectorB22 group being the most prominent out of all the subgroups.
[Figure 1. Activity level of SectorB subgroups in 2022]
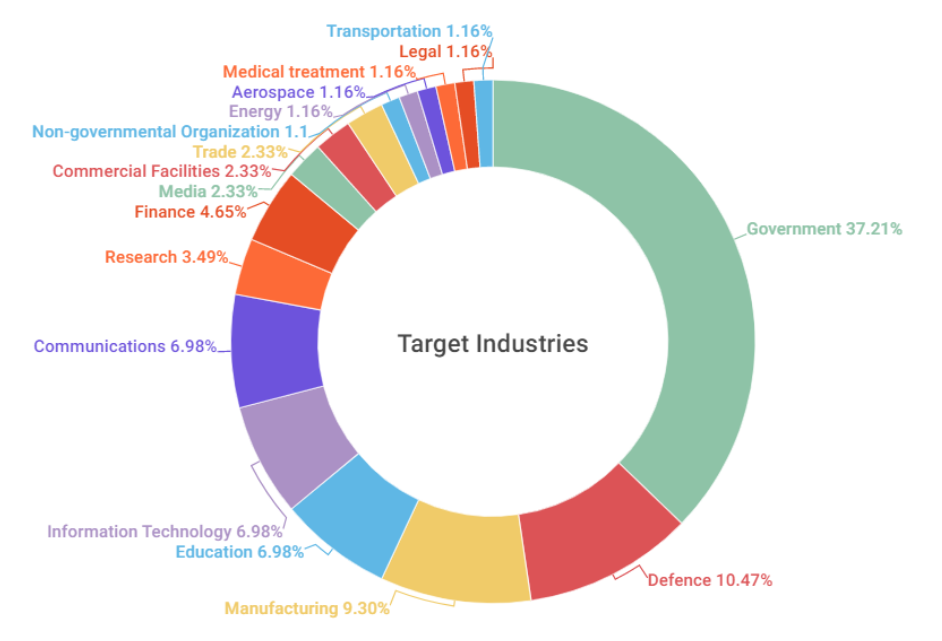
The main targets of SectorB groups were identified to be workers and systems in government institutions and national security related fields, followed by manufacturing, education, and IT industries.
[Figure 2: Distribution of targeted industries in 2022]
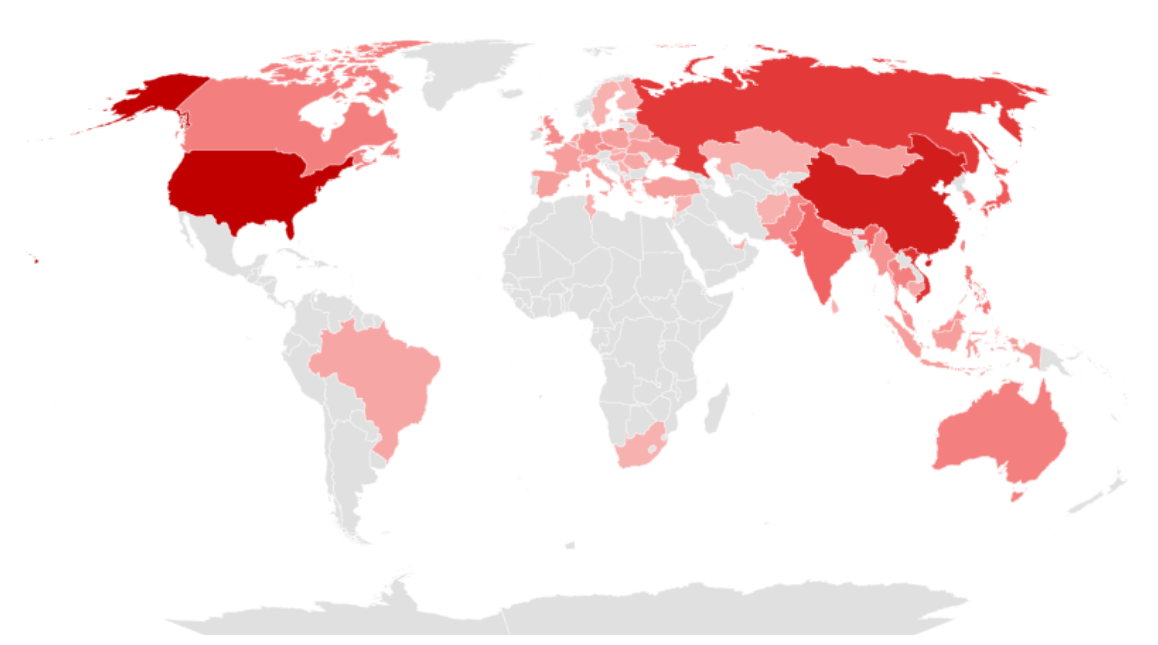
The following figure is a map showing the countries that were targeted by SectorB Groups in 2022, with a darker shade of red indicating a higher frequency of attacks. From the figure, it could be deduced that the group carried out the greatest number of hacking activities on the United States, located in the North American continent, as well as Hong Kong and Vietnam, which are neighboring countries of China.
In the case of Russia, where a war initiated by the invasion of Ukraine by Russia is ongoing, was also targeted despite the fact that the Chinese government is maintaining a positive relationship with the Russia government. SectorB groups were seen to have been carrying out attacks on the country to steal crucial information including Russian military technology.
[Figure 3: Mainly targeted countries of SectorB in 2022]
2022 Activities of SectorB Groups
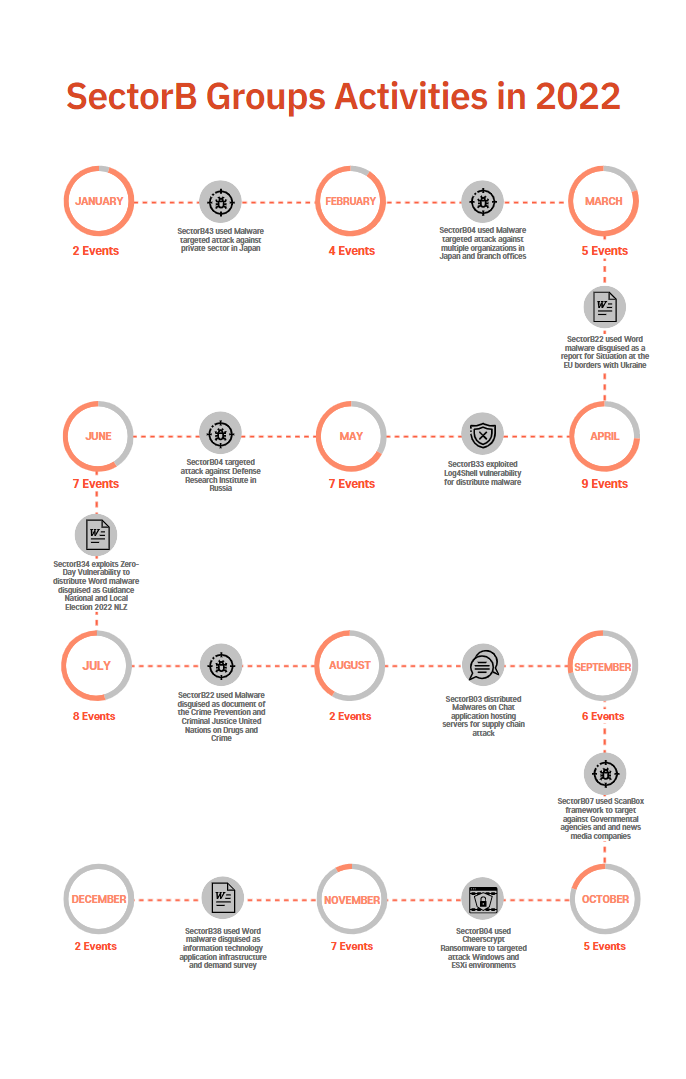
The following is a timeline of the hacking activities carried out by SectorB groups as identified in 2022 and the detailed information of monthly activities of the group.
[Figure 4: Main activities and events by SectorB groups in 2022]
JANUARY
In January 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorB03 and SectorB43.
SectorB03 group was found to be active in South Korea, the United States, China, England, Brazil, Hong Kong, Japan, and Serbia. The group made use of themes such as “software engineer”, “maintenance engineer” and “resume” which would be of interest to workers in the IT industry to deliver malwares for attempting command and control functions in the infected system.
SectorB43 group was found to be active in Pakistan, India, Vietnam, Russia and Japan. The group disseminated malwares targeted on a private company of a specific country, which registers itself in the Window services to maintain persistency.
FEBRUARY
In February 2022, activities by a total of 3 hacking groups were identified, and the groups were SectorB04, SectorB38, and SectorB43.
SectorB04 group was found to be active in India and the United States. The group utilized the DLL side-loading technique to load a malicious DLL in a regular program. The malware was disguised as a module of a virtual software and carries out functions such as command and control in the infected system once executed.
SectorB38 group was found to be active in Vietnam. The group used MS Word format malwares utilizing the template injection method in their attacks, and the MS Word document used was disguised under contents related to socialism in Vietnam.
SectorB43 group was found to be active in Russia, the United States and Canada. The group used PE (Portable Executable) format malwares, which collected information from the infected system and used OpenSSL to carry out encrypted communication functions.
MARCH
In March 2022, activities by a total of 3 hacking groups were identified, and the groups were SectorB01, SectorB09, and SectorB22.
SectorB01 group was found to be active in the United States, Hong Kong, England, China and Vietnam. The group exploited the Log4j and USAHerds vulnerabilities to penetrate into the targeted systems. Afterwards, open-source tools were used to install PE (Portable Executable) format malwares in the targeted systems and steal system controls.
SectorB09 group was found to be active in Taiwan and South Korea. The group used ELF (Executable and Linkable Format) file malwares to collect information from the infected system, and carry out commands received from the C2 server such as file transfer, remote shell command, and proxy mode to control the malware.
SectorB22 group was found to be active in Russia, Romania, Hong Kong, Czech Republic, Slovakia, the United States, Belgium, and Poland. The group targeted on workers of European diplomacy institutes to deliver spear phishing emails attached with compressed files.
APRIL
In April 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorB14, SectorB22, SectorB26, SectorB33, SectorB50.
SectorB14 group was found to be active in South Korea, China, and Singapore. The group used a Windows LNK file, which downloads a PowerShell script from the C2 server and executes it upon execution of the file.
SectorB22 group was found to be active in Spain, Thailand, Canada, China, Greece, Vietnam, Mongol, Hong Kong, Myanmar, Russia, Cyprus, and South Africa. The group targeted on workers of government agencies and research institutes located in Europe and Southeast Asia.
SectorB26 group was found to be active in South Korea. The group used a multiplatform malware to target on users of Windows and Mac OS in this attack.
SectorB33 group was found to be active in India, France, Tunisia, Pakistan, Singapore, Australia, Netherlands, Canada, Finland, Hong Kong, South Korea, the United States, Italy, and Spain. The group exploited the Log4Shell vulnerability to carry out attacks on systems of companies in finance, academia and travel industries.
SectorB50 group was found to be active in Ukraine, Turkey, India, Russia, the Philippines, China, and the United States. The group used MS Word documents disguised under topic such as “OSCE meeting” and “military”, which were related to national defense and diplomacy.
MAY
In May 2022, activities by a total of 7 hacking groups were identified, and the groups were SectorB04, SectorB20, SectorB22, SectorB23, SectorB31, SectorB34, and SectorB53.
SectorB04 group was found to be active in Netherlands, China, Belarus, Russia, Italy, Turkey, and Malaysia. The group targeted on workers of a specific research center to send out spear phishing emails.
SectorB20 group was found to be active in China, Vietnam, Thailand, Singapore, the Philippines, Malaysia, Indonesia, Cambodia, and Brunei. The group used spear phishing emails attached with MS Word documents in this activity.
SectorB22 group was found to be active in Vietnam. The group disseminated malwares disguised as security software products with the aim of stealing system controls.
SectorB23 group was found to be active in South Korea. The group used CHM files, which is a help file format, in this activity. The documents used were disguised as a technical support document for users of a specific system.
SectorB31 group was found to be active in Russia. The group used MS Word documents written in Russian for their attacks.
SectorB34 group was found to be active in India, Japan, and China. The group used a malware exploiting a RTF (Rich Text Format) vulnerability in this activity.
SectorB53 group was found to be active in Sweden, Taiwan, the United States, Macao, Hong Kong, China, India, and South Korea. The group disseminated ELF (Executable and Linkable Format) malware targeting Linux operating systems in this activity.
JUNE
In June 2022, activities by a total of 7 hacking groups were identified, and the groups were SectorB07, SectorB25, SectorB31, SectorB34, SectorB38, SectorB42, and SectorB56.
SectorB07 group was found to be active in Luxembourg, Pakistan, Japan and Australia. The group disseminated document malwares exploiting a vulnerability, and utilized a technique that disseminates additional malicious scripts encoded in BASE64 from the C2 server to steal system controls.
SectorB25 group was found to be active in the United States and Russia. The group used RTF (Rich Text Format) malware written in Russian for their attacks.
SectorB31 group was found to be active in Russia. The group used Word documents incorporated with a VBA macro script in this activity. The Word malware was disguised as a reference and session document written in Russian, and prompted the target to click on the macro activation button.
SectorB34 group was found to be active in the Philippines, India, Nepal, Russia, and Belarus. The group exploited a vulnerability that allows execution of arbitrary commands in MS documents.
SectorB38 group was found to be active in Thailand and China. The group sent out spear phishing emails to numerous government agency workers in this activity. The email was attached with a compressed file containing a Word malware and the password to the compressed file.
SectorB42 group was found to be active in Cambodia, Russia, Vietnam, and the United States. The group targeted on corporates across various industries such as finance and communication, as well as government institutions of numerous countries, to send out a specific malware and carry out their attacks.
SectorB56 group exploited the remote access code execution vulnerability of a firewall tool to carry out delicate attacks.
JULY
In July 2022, activities by a total of 3 hacking groups were identified, and the groups were SectorB22, SectorB25, and SectorB38.
SectorB22 group was found to be active in Czech Republic, the Philippines, Thailand, Vietnam, England, China, Belgium, Hungary, and Singapore. In this activity, the group used malicious code in the form of compressed files disguised as various topics that the target of the attack could be interested in, such as conference reports, embassy reports, guidelines, and Pandemic.
SectorB25 group was found to be active in Pakistan and England. The group sent out spear phishing emails attached with document format malwares to workers of telecommunication centers in Southeast Asian countries.
SectorB38 group was found to be active in Vietnam. The group used a RTF (Rich Text File) format malware disguised as e-newsletters written by military units.
AUGUST
In August 2022, activities by a total of 1 hacking groups were identified, and the group was SectorB03.
SectorB03 group was found to be active in Czech Republic, the Philippines, Thailand, Vietnam, England, China, Belgium, Hungary, and Singapore. The group compromised the server of a video chatting application, modifying installation programs downloaded through a legitimate path such that malwares are downloaded additionally.
SEPTEMBER
In September 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorB01, SectorB07, SectorB09, SectorB22, and SectorB58.
SectorB01 group was found to be active in Mongolia, Taiwan, Russia, Vietnam, Singapore, Netherlands, Germany, Hong Kong, the United States, China, and Cyprus. The group targeted on personnels of various industries such as government institutions, finance, telecommunications, and media to disseminate malwares. The group used the DLL sideloading technique, which is a technique to load malicious DLL files and executing them through regular legitimate programs, together with a known malware. The malware carried out functions such as keylogging, screen capturing, file upload and downloading.
SectorB07 group was found to be active in Taiwan, Thailand, Singapore, Germany, Australia, Malaysia, the United States, and Israel. The group attempted to carry out phishing attacks on government institutions and workers of energy and manufacturing sectors, disseminating malware to targets through inserting a malicious JavaScript to a phishing webpage. In the final stage, the malware collects browser information of the targets and communicates them to the C2 server, and carries out various malicious acts depending on the Plugin sent from the C2 server.
SectorB09 group was found to be active in Japan and the United States. The group used ARM based malwares to attack Linux Operating Systems, with the aim of penetrating into the internal networks. In the final stage when the malware establishes a successful communication with the C2 server, it collects information such as the computer name, process ID, login username from the infected system and sends them to the C2 server.
SectorB22 group was found to be active in Canada, the United States, Myanmar, and Vietnam. The group targeted on government institution personnels to disseminate malware-containing compressed files under titles that would be of interest to the targets, such as economic status of Ukraine, impersonating Suriname Ministry of Foreign Affairs, or EU drug related crimes. In the final stage, the group monitored the infected system for information collection purposes and compromised system controls.
SectorB58 group was found to be active in Xinjiang Uygur Autonomous Region of China. The group targeted on active users of a Chinese ethnic minority community website to collect information such as SMS, contacts, phone call history, and location data of infected devices through an Android malware.
OCTOBER
In October 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorB01, SectorB03, SectorB04, SectorB22, and SectorB58.
SectorB01 group was found to be active in the United States and Sri Lanka. The group targeted on workers of government institutions to disseminate ISO image format malwares through cloud storages such as Dropbox and Google Drive. They used the DLL side loading technique, which consists of loading malicious DLL files using regular programs and executing them, and the downloaded malwares carried out functions such as keylogging, screen capturing, file uploading and downloading.
SectorB03 group was found to be active in the United States, China, Vietnam, Hong Kong, Japan, Albania, and the Arab Emirates. The group targeted on systems of government institutions, electronics, and medical sectors to carry out their attacks. The Log4j vulnerability was exploited in the process of uploading a Web Shell with various functionalities such as file uploading and downloading, with the aim of acquiring initial access authorization. In the final stage, the infected system was consistently monitored for information collection purposes, and system controls were taken over.
SectorB04 group was found to have exploited the Log4j vulnerability to gain initial access authorizations. Afterwards, PowerShell commands was used to generate and execute additional malicious codes in the internal system, and tools such as Cobalt Strike and Impacket was used in the process. In the final stage, ransomware was used to encrypt critical files for system disruption purposes.
SectorB22 group was found to be active in Romania. The group distributed malicious code and shortcut (LNK) files together in a compressed file. The group showed a bait document on the screen to hide the infection, and used the tactics of consistently monitoring the infected system for information collection purposes and to take over system controls.
SectorB58 group was found to be active in Xinjiang Uygur Autonomous Region of China. The group targeted on active users of a Chinese ethnic minority community website by using Android malwares disguised under topics related to Al-Qaida military courses translated into Uyghur. In the final stage, the group attempted to collect information such as SMS, contacts, phone call history, and location data of infected devices.
NOVEMBER
In November 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorB04, SectorB05, SectorB22, SectorB31 and SectorB38.
SectorB04 group was found to be active in Japan. The group targeted on government and diplomatic institution personnels for their attacks. A MS Word malware disguised under titles related to US-Japan alliance was used for initial access. In the final stage, an additional malware was generated and executed through DLL side loading technique, and collected information from the infected system to set the base for penetrating into the internal systems.
SectorB05 group was found to be active in China, the United States, Russia, Syria, and Xinjiang Uygur Autonomous Region. The group targeted on active users of a Chinese ethnic minority community website to disseminate Android malwares. The Android malware was disguised as applications such as video sharing platforms, video call, voice chat, translators, dictionary, and religious apps with high usage rate and would be of interest to the targets. In the final stage, information such as SMS, contacts, phone call history, and location data were collected from the infected system.
SectorB22 group was found to be active in Poland, the Philippines, Myanmar, Thailand, the United States, Canada, Hong Kong, India, Australia, Taiwan, and Japan. The group targeted on workers in government institutions, academia, foundations and research sectors to send out spear phishing emails. The email, which was used as the initial access method, contained a link to the Google Drive that prompted the user to download the malware. The malware collected information such as process information, user and computer usernames, OS details and sent them to the C2 server.
SectorB31 group attached a malware to a compressed file that was disguised under filenames related to online shopping malls and informative websites for distribution purposes. The malware continuously monitored the infected system for stealing system information.
SectorB38 group was found to be active in Australia. The group disseminated MS Word format malwares which were disguised under subjects related to info-communication application technology and demand survey. When executed, the malware utilized the template injection technique to download template files incorporated with malicious macros. In the final stage, the group used the tactic of downloading a DLL file from the C2 server and executing it through rundll32.exe (Windows application program) to compromise system authorities.
DECEMBER
In December 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorB03, SectorB22.
SectorB03 group was found to be active in Hong Kong. The group exploited a digital signature information of a software development company to disguise malware as a legitimate file, which collected system and file information from the infected system when executed.
SectorB22 group was found to be active in Vietnam and Latvia. The group distributed a malware-containing RAR compressed file that was disguised under titles related to Hungary to carry out their attacks. The malware in the compressed file consistently monitors the infected system to carry out information collecting functions.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.