2022 Activities Summary of SectorC groups (ENG)
Summary
In 2022, hacking activities by a total of 11 SectorC subgroups were identified. The groups carry the aim of collecting advanced information such as political and diplomatic activities of governments of countries bordering the government that supports the groups, as well as around the world.
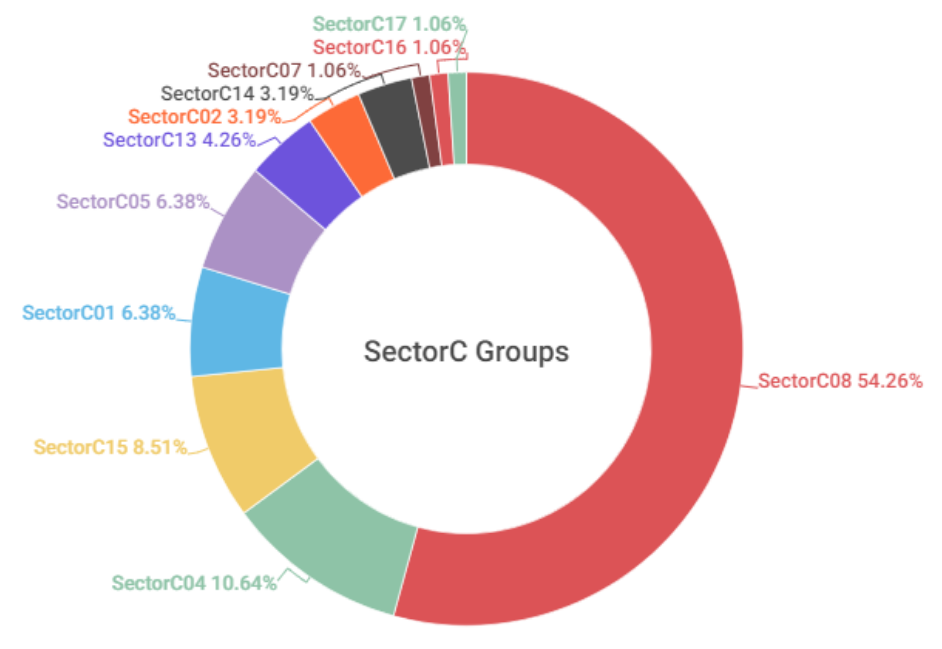
An analysis of hacking activities by SectorC groups in 2022 showed that there was a total of 11 active subgroups in the year, with activities by SectorC08 group being the most prominent out of all the subgroups.
[Figure 1: Activity level of SectorC subgroups in 2022]
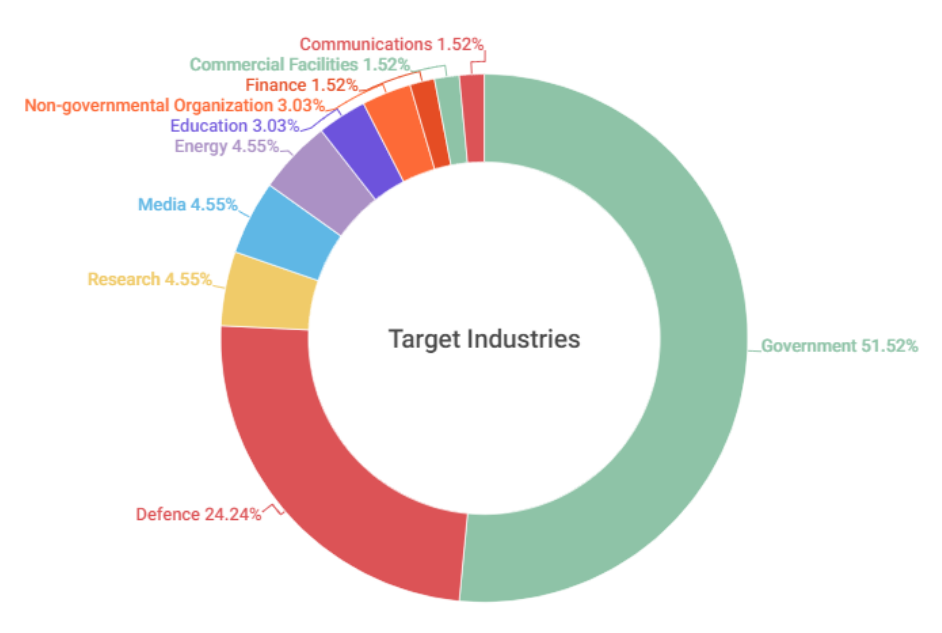
The main targets of SectorC groups were identified to be workers and systems in government institutions and national security related fields.
[Figure 2: Distribution of targeted industries in 2022]
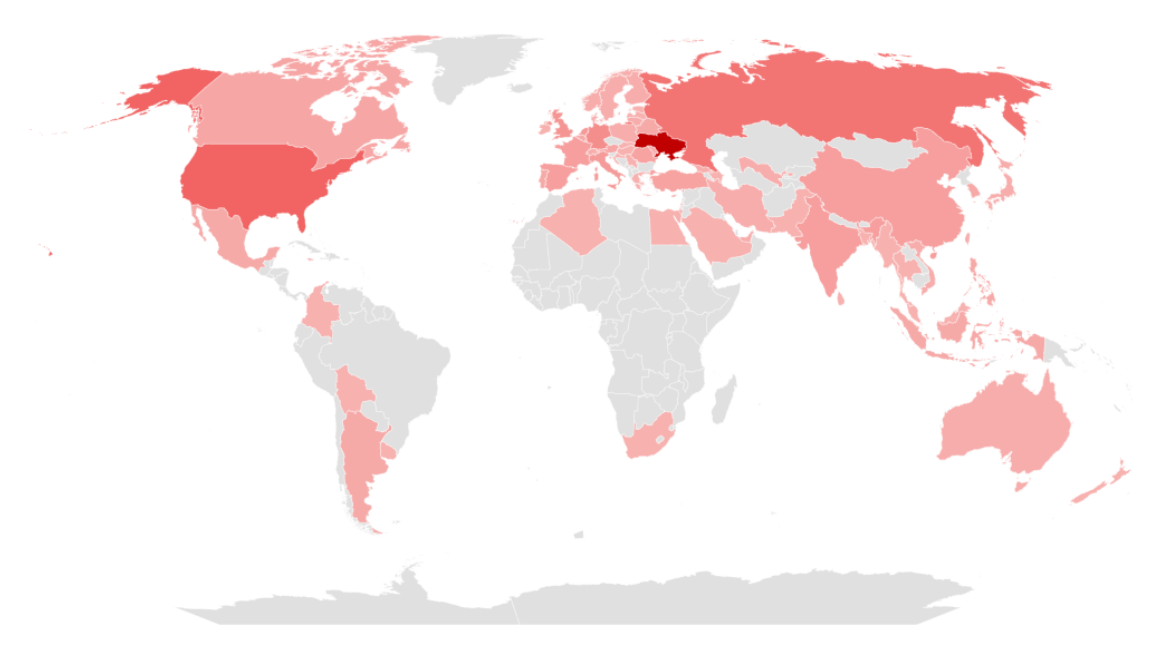
The following figure is a map showing the countries that were targeted by SectorC Groups in 2022, with a darker shade of red indicating a higher frequency of attacks. From the figure, it could be deduced that the group carried out the greatest number of hacking activities on Ukraine, a country bordering Russia, and the United States, located in the North American continent.
In the case of Ukraine, the country has been set as the main target of the groups following the invasion of the country by Russian government, the supporting entity of the groups. The groups are believed to be carrying out extensive hacking activities with the aim of disabling key systems of Ukraine or stealing critical information such as military technology information.
[Figure 3: Mainly targeted countries of SectorC in 2022]
2022 Activities of SectorC Groups
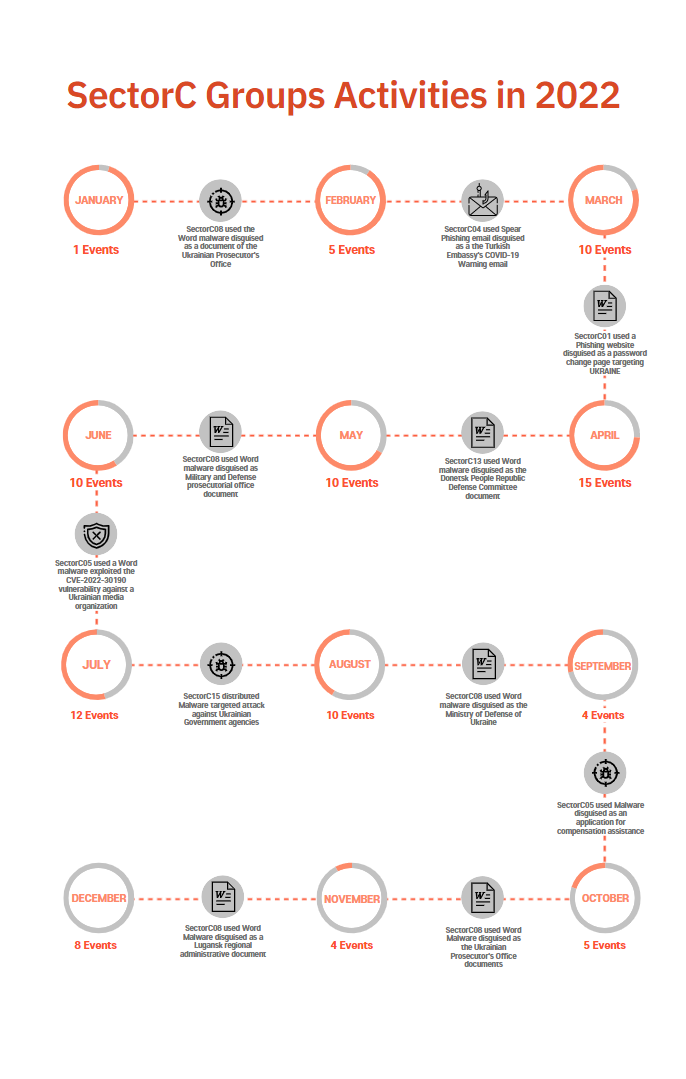
The following is a timeline of the hacking activities carried out by SectorC groups as identified in 2022 and the detailed information of monthly activities of the group.
[Figure 4: Main activities and events by SectorC groups in 2022]
JANUARY
In January 2022, activities by a total of 1 hacking groups were identified, and the groups were SectorC08.
SectorC08 group was found to be active in Ukraine. The group used MS Word file format malwares utilizing the template injection technique to install PE (Portable Executable) format malware in the target’s system and take over system controls.
FEBRUARY
In February 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorC04, SectorC08.
SectorC04 group was found to be active in China, the United States, and Portugal. The group used LNK files in ISO image files to load malicious DLL files, and install pen testing tools such as Sliver or Cobalt Strike to take over system authorizations.
SectorC08 group was found to be active in Ukraine, the United States, Germany, Netherlands, Switzerland, Israel, Russia, Iran, England, and Algeria. The group used MS Word documents utilizing the template injection technique to install PE (Portable Executable) format malware in the target’s system and steal system controls.
MARCH
In March 2022, activities by a total of 6 hacking groups were identified, and the groups were SectorC01, SectorC04, SectorC05, SectorC08, SectorC15 and SectorC16.
SectorC01 group was found to be active in Ukraine. With the aim of reading emails saved in internal mail systems and leaking them to external surroundings, the group sent out a delicately written phishing email accompanied with a phishing website. In this activity, the group launched a large-scale credential phishing campaign against users of a Ukrainian media related company.
SectorC04 group was found to be active in Taiwan and India. The group used LNK files included in ISO image files to load malicious DLL files for installation of pentesting tools such as Sliver and Cobalt Strike, with the aim of taking over system controls. In this activity, malicious PDF documents disguised with contents related to COVID-19 and a meeting with the president of India was used.
SectorC05 group was found to be active in the United States. The group developed a botnet targeting IoT (Internet of Things) devices, routers, and storage devices, and mainly uses ELF format malwares as the default OS of IoT devices is Linux. In this activity, the group used a botnet that targeted on the router device of a specific corporation.
SectorC08 group was found to be active in Ukraine, England, Vietnam, the United States, and Switzerland. The group used MS Word document malwares utilizing the template injection method to install PE (Portable Executable) format malwares in the target’s system and take over system controls. In this activity, MS Word documents disguised as list of Ukraine-related news and Ukrainian social media monitoring.
SectorC15 group was found to be active in Ukraine, France, England, China, Netherlands, Cyprus, Singapore, Jamaica, Germany, Canada, Denmark, Spain, the Philippines, Serbia, Moldova, Turkey, Saudi Arabia, Russia, the United States, and Italy. The group attached malware developed in the Go programming language to phishing emails related to Ukrainian cybersecurity and delivered them to the targets.
SectorC16 group was found to be active in Ukraine. The group attached a compressed file containing LNK malware to a phishing email for dissemination purposes, and the executed LNK file downloads and executes a HTA file in the victim’s computer. The final payload is a malware with backdoor functionalities.
APRIL
In April 2022, activities by a total of 6 hacking groups were identified, and the groups were SectorC02, SectorC04, SectorC05, SectorC08, SectorC13 and SecotorC15.
SectorC02 group was found to be active in Uzbekistan, Indonesia, Mexico, India, and Japan. The group used malware disguised as a process manager of Android OS to attempt information theft. Similar to other Android malwares, the aforementioned Android malware had various functionalities for stealing information from Android based smartphones.
SectorC04 group was found to be active in India, England, the United States, Spain, the Philippines, Austria, Bangladesh, Switzerland, Russia, Italy, France, Greece, China, Australia, Argentina, and Germany. The group used the tactics of loading a malicious DLL file through LNK files included within ISO image files, to install penetration test tools such as Sliver or Cobalt Strike and take over system controls. In this activity, an ISO format malware disguised as an information update document was used.
SectorC05 group was found to be active in Belgium, Japan, Ukraine, and the United States. The group targeted on an energy providing company in Ukraine to carry out their attacks. In the attack, a wiper with disk destruction functionalities was used against multiple operating systems such as Windows, Linux, and Solaris.
SectorC08 group was found to be active in Hungary, Romania, Ukraine, Russia, India, Latvia, Netherlands, Italy, New Zealand, Iran, and Turkey. The group used MS Word document format malwares utilizing the template injection technique to install PE (Portable Executable) format malware in the target’s system, in order to steal system controls. In this activity, a document in Ukrainian was found, and MS Word malwares disguised as documents related to Ukrainian government and Russian military were identified.
SectorC13 group was found to be active in Moldova and the United States. The group used MS Word documents utilizing the template injection technique, and a Word document disguised under contents related to the National Defense Committee and an excel document disguised as Securities and Exchange Commission Form was identified.
SectorC15 group was found to be active in Romania, Ukraine, Austria, Netherlands, Russia, and Hong Kong. The group used malwares developed using the Go programming language to collect general information from computers, then carried out commands received from the C2 server and undergo various activities such as file upload and download. In this activity, an MS Excel document containing macros was attached to a phishing email to be delivered to natural gas companies, banks, and media broadcasting stations.
MAY
In May 2022, activities by a total of 6 hacking groups were identified, and the groups were SectorC01, SectorC04, SectorC05, SectorC07, SectorC08 and SectorC15.
SectorC01 group was found to be active in Russia, Ireland, Columbia, Netherlands, Arab Emirates, Ukraine, Indonesia, Spain, Portugal, and Germany. The group targeted on Ukraine to send out spear phishing emails for dissemination of malwares with information collecting functionalities.
SectorC04 group was found to be active in Belgium, Turkey, Indonesia, Russia, Sweden, Canada, Austria, and Taiwan. The group impersonated the Embassy of Turkey to send out spear phishing emails targeted on the ministry of foreign affairs.
SectorC05 group was found to be active in Ukraine. The group used a variant of the malware loader used in their previous attack against the Ukrainian energy provision company.
SectorC07 group was found to be active in Germany, Thailand, South Korea, the United States, Russia, England, Netherlands, France, Italy, Portugal, Spain, Bolivia, Croatia, Turkey, Argentina, Romania, South Africa, and Mexico. The group used protected documents that prompted targets to disable protection settings, and used the malware to collect information saved in the system such as financial data and password details.
SectorC08 group was found to be active in Ukraine and Israel. The group sent out spear phishing emails on explosives installation to disseminate backdoor malware with various functionalities including a monitoring function within the system.
SectorC15 group was found to be active in Ukraine, South Korea, China, Israel, the United States, Singapore, Arab Emirates, Uzbekistan, Myanmar, and Vietnam. The group sent out spear phishing related to COVID-19 in order to disseminate malware that collects general system information, carry out commands received from the C2 server, or upload and download files.
JUNE
In June 2022, activities by a total of 4 hacking groups were identified, and the groups were SectorC02, SectorC04, SectorC05 and SectorC08.
SectorC02 group was found to be active in Luxembourg. The group used a URL disguised as a homepage related to NATO and EU, and a MS Word malware disguised as a document containing news scraps related to the war was identified.
SectorC04 group was found to be active in the United States and Romania. The malware used by the group was named in Catalan, a language used in certain regions of Spain, and was disguised as a file related to statute. In the final stage, a malicious DLL with downloader functions is executed.
SectorC05 group was found to be active in Singapore, Italy, Canada, Ukraine. The group targeted on an organization related on Ukrainian media to use malicious documents that exploited a vulnerability. The malware installed in the system at the final stage has a backdoor function that allows it to steal important information from the system or download additional malwares.
SectorC08 group was found to be active in Ukraine, the Netherlands, China, Russia, Poland, and Finland. The group used malware disguised as a Ukrainian prosecute and administrative related document, and a MS word malware disguised as a document from the Russian ministry of defense. In the final stage, remote controlling was attempted through the usage of open-source remote access tools.
JULY
In July 2022, activities by a total of 7 hacking groups were identified, and the groups were SectorC01, SectorC02, SectorC04, SectorC05, SectorC08, SectorC014 and SectorC15.
SectorC01 group was found to be active in Ukraine. The group used a DOT Net based malware with information collecting purposes, and a Word malware exploiting the Follina vulnerability (CVE-2022-30190), which was disguised as a news article related to the Ukrainian war.
SectorC02 group was found to be active in Georgia and Argentina. The group disseminated an Android malware disguised as a DDoS tool from a website impersonating a military unit.
SectorC04 group was found to be active in Egypt, Ukraine, India, Hong Kong, Canada, the United States, Norway, Italy, the Russian Federation, Belgium, Netherlands, Estonia, Malaysia, Finland, and Austria. The group impersonated the government to deliver a spear phishing email attached with a COVID-19 related PDF document, which prompted targets to click on a phishing link within it.
SectorC05 group was found to be active in Uruguay and Ukraine. The group targeted on the telecommunications industry to deliver spear phishing emails on legislation support and military units, and used a backdoor malware in the final stage.
SectorC08 group was found to be active in Ukraine, Russia, India, and Germany. The group used a malware disguised as a document related to payment of arms, together with a MS Word malware disguised as a document from the ministry of defense. In the final stage, UltraVNC, a remote access tool was used.
SectorC14 group was found to be active in Ukraine and England. The group used a phishing website disguised as the log in page of the ministry of defense.
SectorC15 group was found to be active in France, Ukraine, the United States, England, Australia, and Germany. The group targeted on workers of government institutions to send out spear phishing emails on national defense, and used Cobalt Strike, a pentesting tool in the final stage.
AUGUST
In August 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorC08, SectorC14.
SectorC08 group was found to be active in Ukraine, the United States, Russia, the Philippines, Germany, Sweden, Spain, India, and France. The groups used a MS Word format malware, and a remote access tool UltraVNC in the final stage.
SectorC14 group was found to be active in the United States and England. The group targeted on national defense, non-governmental organizations, intergovernmental organizations to utilize social engineering techniques through social media. Afterwards, the targets were led to access a phishing website, where their email account credentials were stolen.
SEPTEMBER
In september 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorC05, SectorC08.
SectorC05 group was found to be active in Ukraine. The group used a malware disguised as the military administration documents of Odessa, a port city in South Ukraine. In the final stage, a remote access tool was used.
SectorC08 group was found to be active in Ukraine and China. The group used malware disguised as documents from Ukrainian government institutions such as Ministry of Home Affairs and National Security Bureau. In the final stage, the malware was used to attempt system file collection and seizure files.
OCTOBER
In October 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorC01, SectorC08.
SectorC01 group was found to be active in Germany, Turkey, the United States, Italy, and Slovakia. The group used MS PowerPoint malware disguised as the translation guidelines for the OECD(Organization for Economic Co-operation and Development) meeting. In the final stage, an open-source remote access tool Empire was used to attempt system control.
SectorC08 group was found to be active in Ukraine, Germany, Belarus, and Russia. The group used malware disguised as government institution documents of Russia and Ukraine, and attempted to steal information through UltraVNC, a remote access tool, in the final stage.
NOVEMBER
In November 2022, activities by a total of 2 hacking groups were identified, and the groups were SectorC08, SectorC13.
SectorC08 group was found to be active in Ukraine, Lithuania, and Russia. The group used malwares disguised as administrative and security guideline documents of a government institution, and attempted to steal information using UltraVNC, a remote access tool.
SectorC13 group was found to be active in Russia and Belarus. The group targeted on the Ministry of Foreign Affairs to send out phishing emails disguised as a diplomacy journal, and prompted the targets to execute a MS Word malware utilizing the template injection technique.
DECEMBER
In December 2022, activities by a total of 5 hacking groups were identified, and the groups were SectorC08, SectorC13, SectorC14, and SectorC17.
SectorC08 group was found to be active in the United States, Ukraine, Lithuania, Belarus, Romania, France, Georgia, Mexico, Russia and South Korea. The group used a malware disguised as a administrative document of a government institution, and used UltraVNC, a remote access tool, to steal information in the final stage.
SectorC13 group was found to be active in Poland. The group used MS Word malware disguised as border crossing enquiries, and when the target executed the document, the target was connected to a malicious URL within the document that downloaded and executed a DLL file.
SectorC14 group was found to be active in the United States. The group used a phishing website disguised as a log in page of a National Research Center in the United States to steal email credentials.
SectorC17 group was found to be active in Ukraine. The group used Torrent to distribute a modified version of Windows installation software.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.