2022 Activities Summary of SectorD groups (ENG)
Summary
In 2022, hacking activities by a total of 9 SectorD subgroups were identified. The groups primarily conducted hacking activities targeting countries under political dispute with the government that supports the groups. Recently, SectorD groups have been analyzed to be collecting advanced information such as political and diplomatic activities of individuals and governments against the government that supports the groups.
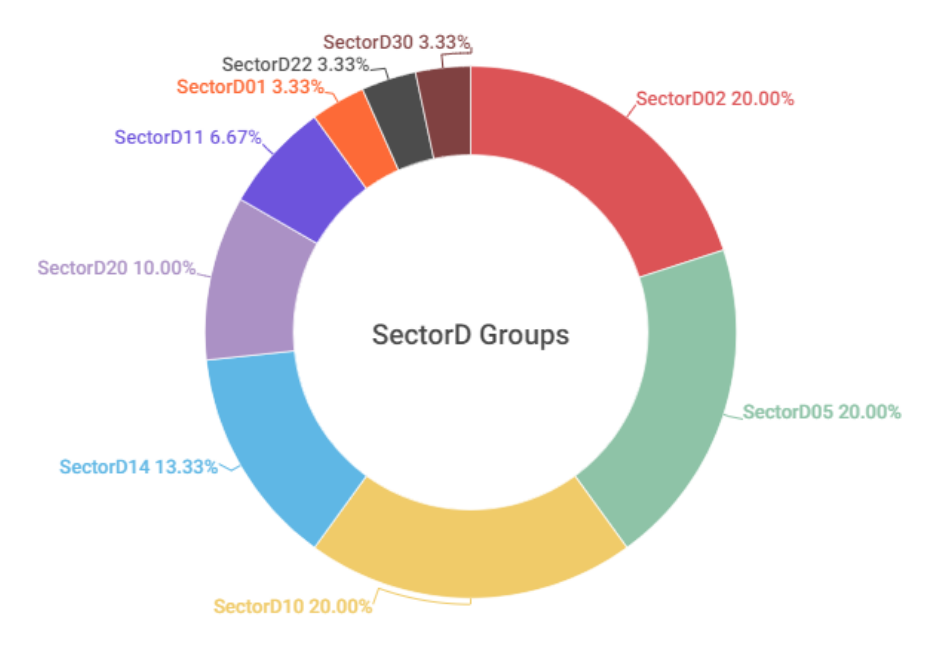
An analysis of hacking activities by SectorD groups in 2022 showed that there was a total of 9 active subgroups in the year, with activities by SectorD02, SectorD05, and SectorD10 being the most prominent out of all the subgroups, each accounting for 20% of the total activities.
[Figure 1: Activity levels of SectorD subgroups in 2022]
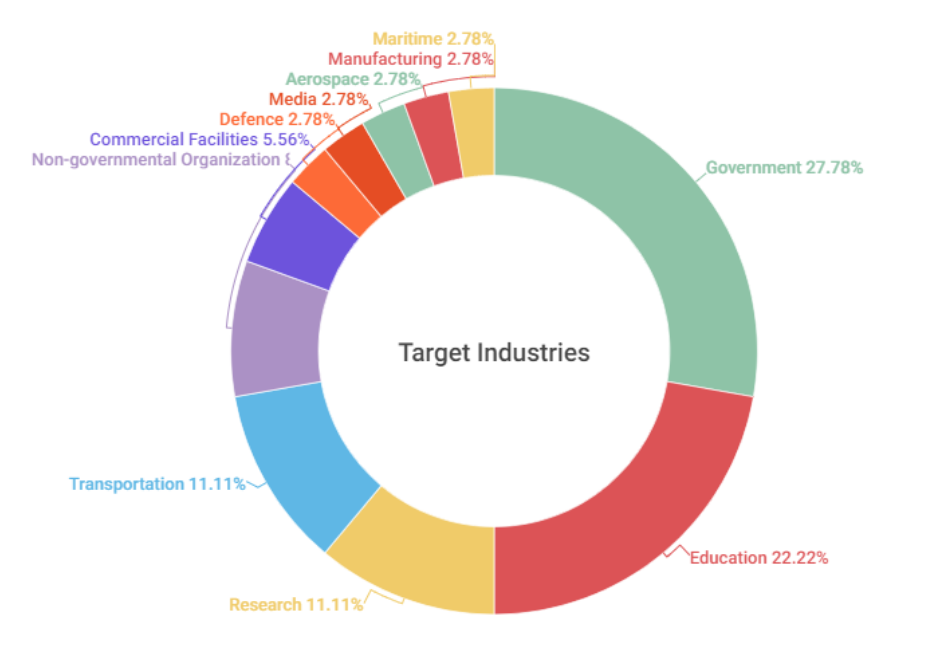
The main targets of SectorD groups were identified to be workers and systems in government institutions and education sectors.
[Figure 2: Distribution of targeted industries in 2022]
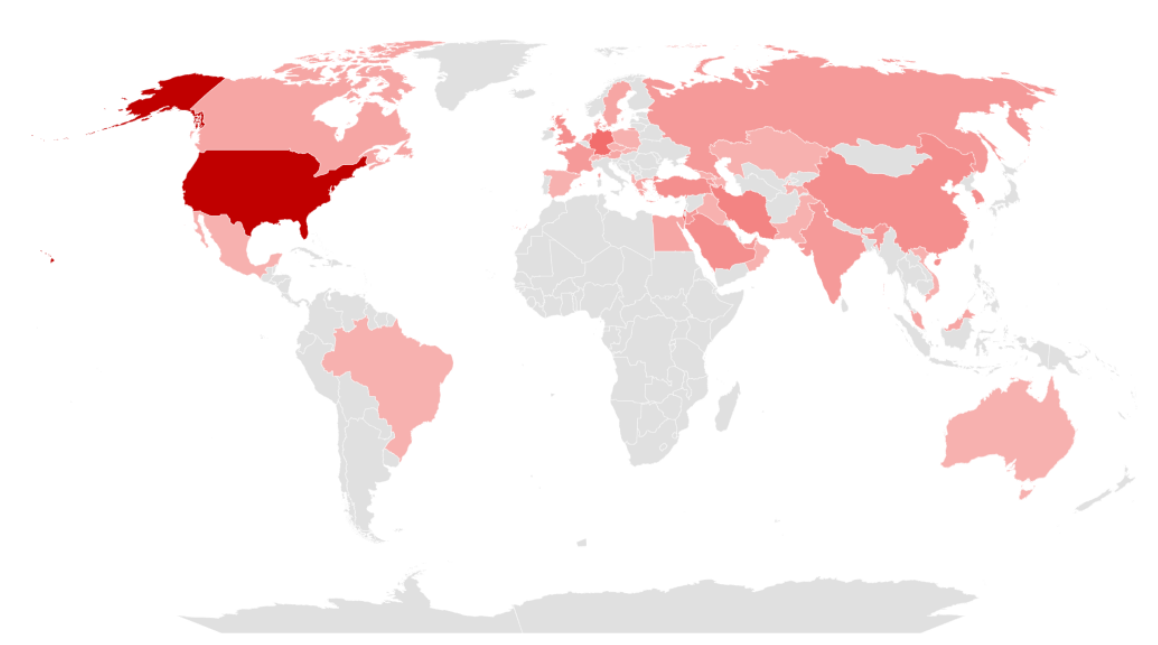
The following figure is a map showing the countries that were targeted by SectorD Groups in 2022, with a darker shade of red indicating a higher frequency of attacks. From the figure, it could be deduced that the group carried out the greatest number of hacking activities on the United States in the North America and Israel in the Middle East.
In the case of Israel, the hacking activities are carried out in conjunction with the deteriorating relationship between Iran and Israel due to the Shadow War, an ongoing conflict between the two countries regarding nuclear development in Iran.
[Figure 3: Mainly targeted countries of SectorD in 2022
2022 Activities of SectorD Groups
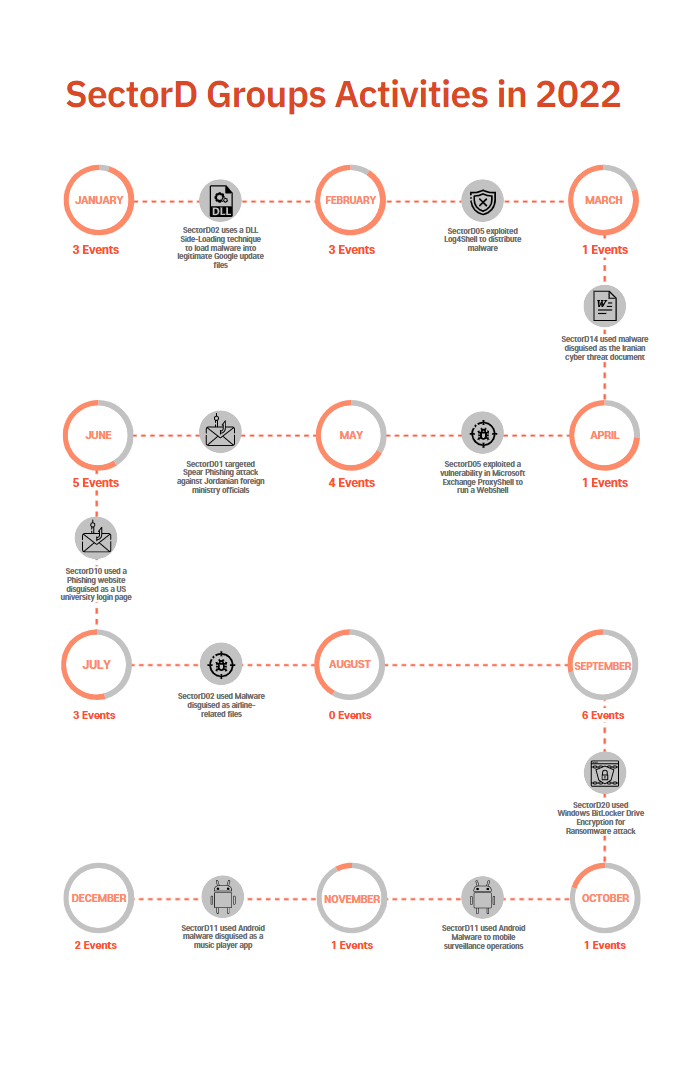
The following is a timeline of the hacking activities carried out by SectorD groups as identified in 2022 and the detailed information of monthly activities of the group.
[Figure 4: Main activities and major events of SectorD Group in 2022]
JANUARY
Among the SectorD groups receiving support from the Iranian government, activities by a total of 2 hacking groups were identified in January, and the groups were SectorD02 and SectorD05.
SectorD02 was found to be active in Saudi Arabia, Russia, Iran, the United States, Armenia, Turkey, Austria, and Germany. The group distributed malware disguised as documents related to a specific university workshop in the United Arab Emirates and collected basic environmental information from infected systems.
SectorD05 exploited the Log4j vulnerability and, after infiltrating the system, used a new PowerShell-based backdoor called CharmPower to perform additional malicious activities such as system information gathering or command controls.
FEBRUARY
Among the SectorD groups receiving support from the Iranian government, activities by a total of 2 hacking groups were identified in February, and the groups were SectorD02 and SectorD05.
SectorD02 was found to be active in Israel, Iran, the United Kingdom, Turkey, South Korea, Pakistan, Armenia, Russia, Germany, Sweden, Denmark, Saudi Arabia, France, the United States, and China. The group targeted on the Turkish government agencies to distribute document-based malware in various formats such as Microsoft Word and Excel, as well as PDF-based malware containing phishing links that induce clicking.
SectorD05 was found to be active in Germany, the Netherlands, Iran, the United States, Georgia, France, Turkey, Austria, Greece, South Korea, and Israel. The group exploited the vulnerability of Log4j to penetrate systems and used tactics such as reverse proxy and reverse shell to perform additional malicious actions such as system information gathering and command control.
MARCH
Among the SectorD groups receiving support from the Iranian government, activities by a total of 1 hacking group was identified in March, and the group was SectorD14.
SectorD14 was found to be active in Turkey, Israel, Canada and Tunisia. The group used social engineering techniques of disguising as HR department employees to approach the targets and increased their credibility by creating fake accounts on social networking services. In this operation, the group disguised the icon of a malware as a PDF icon to make it appear as a legitimate PDF document.
APRIL
Among the SectorD groups receiving support from the Iranian government, activities by a total of 1 hacking group was identified in April, and the group was SectorD05.
SectorD02 was found to be active in the United States. The group exploited the Microsoft Exchange ProxyShell vulnerabilities (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207) to run a web shell that allowed file uploads and downloads as well as PowerShell commands.
MAY
Among the SectorD groups receiving support from the Iranian government, activities by a total of 3 hacking groups were identified in May, and the groups were SectorD01, SectorD10 and SectorD20.
SectorD01 was found to be active in Jordan. The group disguised themselves as a vocational education institution and distributed backdoor malware with various functions by sending spear-phishing emails.
SectorD10 was found to be active in the United States. The group used phishing sites disguised as university libraries and portal webpages to collect attack target information.
SectorD20 was found to be active in Iran, Malaysia, Israel, the United States, and France. The group exploited various vulnerabilities, including PowerShell vulnerabilities, to gain initial access to the targeted systems. They also engaged in ransomware attacks to obtain financial resources in addition to collecting information from the compromised systems.
JUNE
Among the SectorD groups receiving support from the Iranian government, activities by a total of 4 hacking groups were identified in June, and the groups were SectorD05, SectorD10, SectorD14 and SectorD22.
SectorD05 was found to be active in Israel. The group sent spear-phishing emails to Israeli officials, soldiers, and others as part of their efforts to steal email account credentials.
SectorD010 was found to be active in the United States. The group used phishing sites disguised as university libraries and portal websites to collect information of their targets.
SectorD14 was found to be active in the United States and the United Arab Emirates. The group used malicious code disguised as a PDF file of an article written by an Israeli online newspaper.
SectorD22 was found to be active in the United States and India. The group disguised themselves as a recruiter and sent spear-phishing emails, subsequently using malware that can steal financial information and credentials from within the system.
JULY
Among the SectorD groups receiving support from the Iranian government, activities by a total of 2 hacking groups were identified in July, and the groups were SectorD02 and SectorD10.
SectorD02 was found to be active in Israel. The group used malicious code in the form of a Windows Installer package file disguised as airline-related files.
SectorD10 was found to be active in Sweden, the United States, and the United Kingdom. The group used phishing sites disguised as university libraries and portal websites to collect information of their targets.
SEPTEMBER
Among the SectorD groups receiving support from the Iranian government, activities by a total of 4 hacking groups were identified in May, and the groups were SectorD02, SectorD05, SectorD14 and SectorD20.
SectorD02 was found to be active in Israel. The group targeted servers with unpatched Log4j vulnerability and attempted to install commercial remote control software through exploiting vulnerable SysAid Server instances.
SectorD05 was found to be active in Egypt, Jordan, Israel, India, and the United Arab Emirates. The group attempted phishing attacks targeting organizations in the maritime and shipping industries, and it is believed that they stole mail server information from the targeted organizations to collect information for further attacks.
SectorD14 was found to be active in Slovakia, the United States, Albania, Greece, Russia, Vietnam, South Korea, Saudi Arabia, Brazil, Germany, and Switzerland. The group used malicious code disguised as a Java update. The malware uploaded files, executed additional command codes and captured the current screen of the target.
SectorD20 was found to be active in Kazakhstan, South Korea, the United States, the United Kingdom, Australia, and Canada. The group used the ProxyShell vulnerability and Log4j vulnerability to gain access to the target system and ultimately activated BitLocker to encrypt data and generate a ransom note.
OCTOBER
Among the SectorD groups receiving support from the Iranian government, activities by a total of 1 hacking group was identified in October, and the group was SectorD11.
SectorD11 was found to be active in Iran and China. The group disguised a phishing site as a translation news site and distributed Android malware, attempting to steal information such as SMS data, photos, and call recordings from the targeted victims.
NOVEMBER
Among the SectorD groups receiving support from the Iranian government, activities by a total of 1 hacking group was identified in November, and the group was SectorD11.
SectorD11 was found to be active in Germany. The group distributed Android malware disguised as a music player application and attempted to steal the victim’s information such as SMS, photos, and call recordings.
DECEMBER
Among the SectorD groups receiving support from the Iranian government, activities by a total of 2 hacking groups were identified in May, and the groups were SectorD02 and SectorD30.
SectorD02 was found to be active in man, Poland, Azerbaijan, United Arab Emirates, United Kingdom, Armenia, Israel, Malaysia, Turkey, Tajikistan, Jordan, Iraq, and Egypt. The group used phishing emails with malicious links or attachments containing malware, and ultimately attempted to steal information by installing remote access tools on the system.
SectorD30 was found to be active in Oman, Poland, Azerbaijan, the United Arab Emirates, the United Kingdom, Armenia, Israel, Malaysia, Turkey, Tajikistan, Jordan, Iraq, and Egypt. The group has stolen mail login credentials to obtain information from emails and cloud storage, as well as used phishing sites disguised as login pages to steal contacts stored on the targeted system.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.