Monthly Threat Actor Group Intelligence Report, March 2023 (ENG)
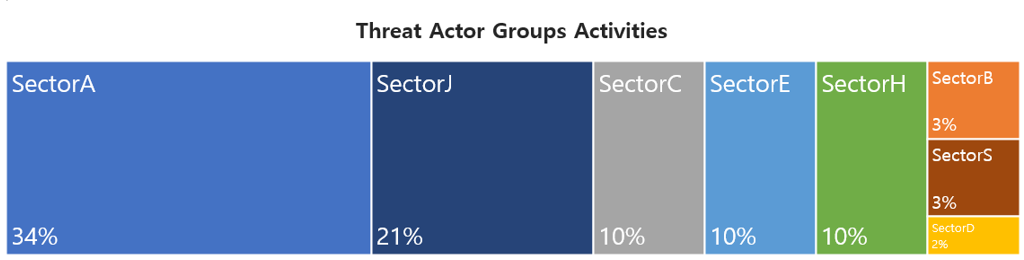
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 February 2023 to 20 March 2023. In March, activities by a total of 28 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 34%, followed by SectorJ groups.
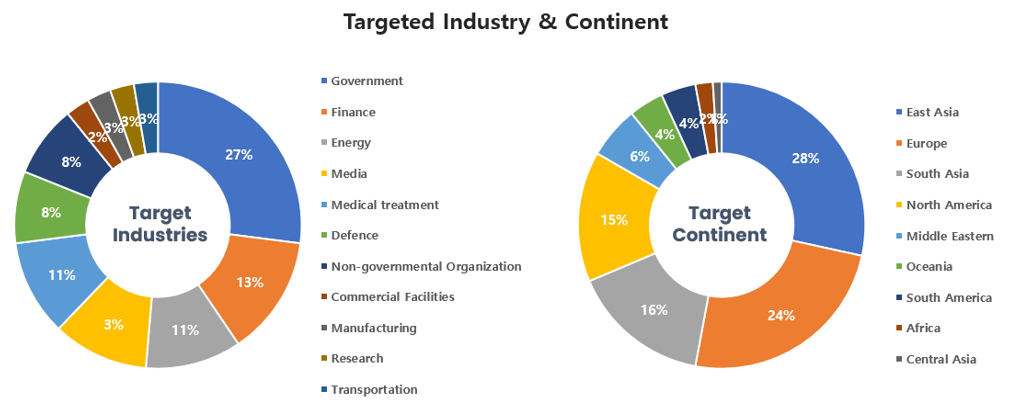
Threat Actors identified in March carried out the highest number of attacks on workers and systems in government agencies and financial sectors. Regionally, East Asia and Europe were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In March 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, SectorA07.
SectorA01 group was found to be active in Ukraine. The group targeted on workers in the field of finance and investment to disseminate MS Excel malware that was disguised as a fee promotion event for VIPs of a cryptocurrency exchange. The malware contained a macro that downloaded additional malware from the C2 server and executed it. In the final stage, the additional malware was used to steal system authorizations.
SectorA02 group was found to be active in South Korea and the United States. The group compressed a CHM (Compiled HTML Help) malware into RAR format for distribution and disguised the malware under various topics such as card usage history, guidelines, request forms, and admission application. Upon execution, the malware downloaded additional malware from the C2 server through MSHTA (Microsoft HTML Application) for execution and registered it in the scheduler to maintain persistence. Afterwards, the malware carried out the function of collecting computer name and username from the infected system and sent them to the C2 server.
SectorA05 group was found to be active in South Korea, Singapore, and Pakistan. The group used MS Word malware disguised as divorce intent confirmation application forms, which contained a macro that downloaded a malware from the C2 server and executed it. In the final stage, the group used the tactics of using additional malware to take over system controls.
SectorA06 group was found to be active in the United States, and South Korea. The group impersonated the National Police Agency and delivered spear phishing emails on promotion of information and communications network utilization and information protection to workers in the field of North Korean policies. The malware registered itself in the registry to maintain persistence and carried out functionalities such as keylogging and clipboard data collection.
SectorA07 group was found to be active in South Korea. The group compressed a Windows LNK malware disguised as tax audit documents from the National Tax Service into a ZIP file for distribution. In the final stage, the malware downloaded and installed additional Visual Basic Script and Batch script files that collected information such as list of processes, list of files in download file, list of files in desktop, list of installed files, and network information.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In March 2023, activities by a total of 2 hacking groups were identified, and the groups were SectorB03 and SectorB22.
SectorB03 group was found to be active in India, the United States, the United Kingdom, Taiwan, the Philippines, and China. The group distributed PE (Portable Executable) and ELF (Executable and Linkable Format) files to carry out attacks on Windows and Linux systems. The code of the malware was protected using VMProtect, and the malware carried out the function of collecting information such as process information, file information, system information and delivered them to the C2 server.
SectorB22 group was found to be active in Netherlands, Czech Republic, Taiwan, Australia, Bulgaria, and Lithuania. The group uploaded malware disguised as resume, diplomacy documents, and passports on GitHub Repository, a source code repository, and distributed it to workers in government institutions. When executed, the malware-maintained persistence in the registry and carried out functions such as additional malware download and execution, or malware termination and duplication depending on the command received.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In March 2023, activities by a total of 3 group was identified, and the group was SectorC04, SectorC08 and SectorC13.
SectorC04 group was found to be active in Chile, Italy, Germany, Egypt, Poland, and France. The group used a HTML file format malware disguised as ‘LegisWrite’, a program used by European countries in document writing and edit, to avoid suspicion of the targets. Notion and Trello APIs were used in command control.
SectorC08 group was found to be active in Ukraine, Bulgaria, South Korea, the United States and Romania. The group targeted on local governments to send out spear phishing emails disguised as criminal procedure legislation documents. In the process, MSHTA, a Microsoft HTML application program that could execute HTA (HTML APllication) files were used to attempt download of additional malicious files.
SectorC13 group was found to be active in Russia. The group used MS Word malware disguised as an article on cooperation between Belarus and China. The malware utilized the template injection technique to download and execute MS Word template containing malicious data.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In March 2023, activities by a total of 1 hacking groups were identified, and the groups were SectorD05.
SectorD05 group created a fake Twitter persona to approach the targets. The group used social engineering techniques to deliver malware or lead the targets to access phishing websites, by building trustworthy relationships with them to discuss about common interests or request for interviews.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In March 2023, activities by a total of 4 hacking groups were identified, and the groups were SectorE02, SectorE03, SectorE04 and SectorE05.
SectorE02 group was found to be active in Bangladesh and Japan. The group distributed MS Word and Excel document malware disguised under topics related to cyber security awareness of workers, such as cyber security guidelines and training nominations. The executed malware generated and executed an additional DLL malware and carried out the function of collecting infected system information such as file information and process details, which were sent to the C2 server.
SectorE03 group was found to be active in Spain, China, Azerbaijan, Turkey, Germany, the United States, Russia, Israel, Australia, the Netherlands, China, Uzbekistan, and Italy. The group targeted on government institutions and energy company workers to deliver spear phishing emails disguised under various topics that would interest the target, such as national progress tactics and president tactics. The LNK malware attached to the email was used to set the base for executing additional malware that could carry out information collection and command control functions. In the final stage, the Bot API of Telegram messenger was used to compromise system information.
SectorE04 group was found to be active in Nepal, Pakistan, India, Myanmar, Australia, and Poland. The group compressed a Windows LNK malware into a ZIP format then distributed the malware disguised under topics such as budget plan and research project proposal. When the malware was executed, a legitimate document file was shown to the target to conceal the infection from the targets, and additional malware downloaded through PowerShell commands was used to compromise system information.
SectorE05 group was found to be active in Pakistan, Australia, Japan, Hong Kong, China, and the United States. The group compressed a CHM (Compiled HTML help) file disguised as a software update file into RAR format for distribution, and in the final stage, sent the computer name and username of the system infected through msiexec, the Window Installer Utility.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In March 2023, activities by a total of 1 groups were identified, and the groups were SectorH03.
SectorH03 group was found to be active in the United States, Pakistan, Russia, Oman, Egypt, India, the United Kingdom, Singapore, Virgin Islands, and Germany. The group distributed Window LNK malware disguised under various topics such as risk allowance, profile of human resources, and Defense Research and Development Organization. When the malware was executed, it showed a legitimate document to conceal the infection, then used MSHTA (Microsoft HTML Application) to download additional script files from the C2 server and executed them.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, India, so it is analyzed that they will continue activities to collect advanced information regarding Indian government agencies’ military and politics to their need.
7. Characteristics of SectorS Group Activities
In March 2023, activities by a total of 1 groups were identified, and the groups were SectorS01.
SectorS01 group was found to be active in Ecuador, Spain, Chile, Germany, Columbia, and Luxembourg. The group targeted on finance and medical workers to deliver spear phishing emails impersonating the Columbia Directorate of National Taxes and Customs, leading the targets to execute the attached Adobe PDF document. In the final stage, the malware with system information collection and command control functions is executed to steal system controls.
Hacking activities of SectorS group activities to date is to collect advanced information on governmental activities of South American countries such as political, diplomatic, and military activities.
8. Characteristics of cybercrime group activities
In March 2023, activities by a total of 11 hacking groups were identified, and the groups were SectorJ04, SectorJ06, SectorJ14, SectorJ20, SectorJ25, SectorJ37 SectorJ53, SectorJ64, SectorJ74, SectorJ95, and SectorJ96.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ04 group was found to be active in the United States, the United Kingdom, Canada, Cameroon and Singapore. The group used a dropper malware known as IcedID, which could be used in dissemination of additional malwares, to set the base for downloading and executing Conti and LockBit Ransomwares.
SectorJ06 group was found to be active in Macedonia, Russia, Germany, Belarus, China, the United States, Spain, France, Brazil, Norway, Czech Republic, and Serbia. The group used the Monti Ransomware with the aim of securing financial resources.
SectorJ14 group was found to be active in South Korea and Japan. The group attempted to attack a specific Wi-Fi router for DNS Hijacking purposes and disseminated an information stealer Android malware disguised as a Chrome browser to users accessing the damaged router.
SectorJ20 group was found to be active in Israel, Cyprus, and Turkyie. The group used a Windows LNK malware disguised as a passport image. In the final stage, a malware with various functionalities such as system information collection and file upload and download were used.
SectorJ25 group used cryptojackers that carried out cryptomining activities in cloud and container environments and modified multiple system settings to set an optimized environment for mining cryptocurrencies.
SectorJ37 group was found to be active in Russia, China, Canada, Palestine, Turkiye, USA, Brazil, Morocco, Costa Rica, Argentina, Germany, Pakistan, Switzerland, Britain, India, France, the Netherlands, Antigua and Barbuda, Sweden, Romania, Malaysia, Syria, Ukraine, Hungary, Poland, and Azerbaijan. The group attached a VBS (Visual Basic Script) format malware disguised as airfare quotations to a phishing email and delivered it to the targets. In the final stage, a malware with remote access functionalities was installed in the system to attempt system information collection and command and control.
SectorJ53 group was found to be active in Canada, Netherlands, Germany, China, India, Italy, and the United States. The group used a spear phishing email disguised as invoices and included a phishing link in the body of the email to lead the targets to download a compressed file containing malwares. In the final stage, a Downloader malware was used to set the base for downloading and executing pentesting tools such as Cobalt Strike and Sliver.
SectorJ64 group was found to be active in Italy, Hong Kong, Malaysia, Guatemala, the United States, Hungary, Singapore, Türkiye, Spain, India, Finland, Russia, and China. The group targeted on Oracle WebLogic Servers that had weak security settings or were susceptible to vulnerabilities to attempt cryptocurrency mining.
SectorJ74 group was found to be active in Pakistan. The group sent out spear phishing emails disguised as reservation history and attached a MS Word malware utilizing the template injection technique to lead the targets to execute them. In the final stage, a malware with remote access functions was installed in the system to attempt system information collection and command and control.
SectorJ95 group was found to be active in Russia. The group used JavaScript format malware disguised as purchase orders. The malware executed in the final stage executed the NirCmd tool that allows tasks to be carried out without user interface, to perform additional malicious activities.
SectorJ96 group was found to be active in Chile, China, and the United Kingdom. The group used various open-source tools to attempt system privilege escalation and lateral movement in networks, and remote access tools were used to set the base for downloading and executing additional malware in the future.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
