Monthly Threat Actor Group Intelligence Report, April 2023 (ENG)
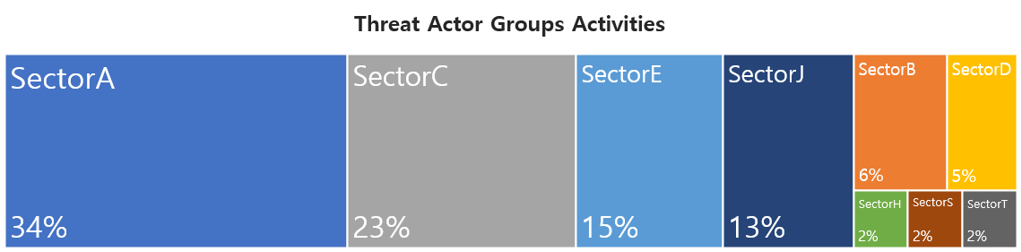
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 March 2023 to 20 April 2023. In April, activities by a total of 29 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 34%, followed by SectorC groups.
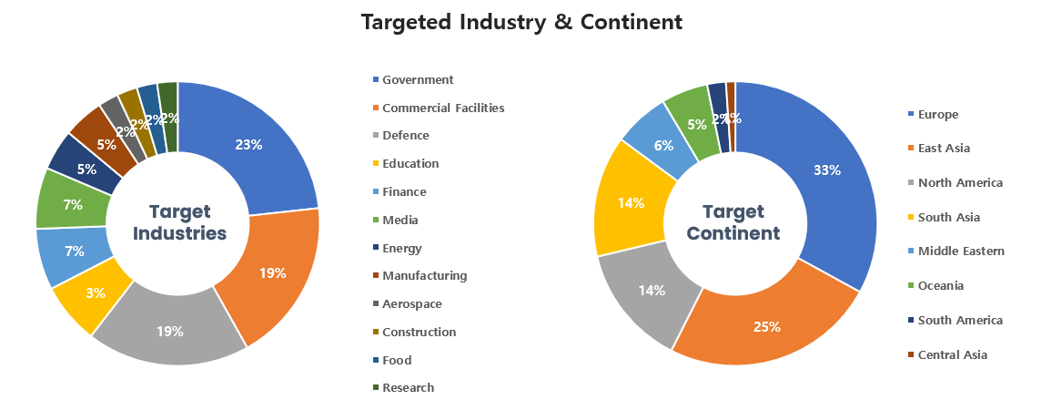
Threat Actors identified in April carried out the highest number of attacks on workers and systems in government agencies and commercial sectors. Regionally, Europe and East Asia were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In April 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, SectorA07 groups.
SectorA01 group was found to be active in South Korea, Ukraine, Italy, the United States, Israel, Czech Republic, India, Germany, Canada, Luxembourg, China, Russia, Georgia, and Romania. The group carried out supply chain attacks on a VOIP (Voice Over Internet Protocol) service provision company, and distributed malwares to users of Windows and Mac OS systems with a specific software installed. In the final stage, the malware that collects system and web browser information was downloaded and executed to consistently monitor the infected system.
SectorA02 group was found to be active in Netherlands, South Korea, and Australia. The group compressed a Windows LNK malware into an ISO image format for distribution purposes, and disguised the file under various topics such as North Korea diplomacy policies or North Korean diplomat selection and dispatch. In the final stage, an additional malware was used to collect system information and send the collected information to cloud services such as pCloud and Yandex.
SectorA05 group was found to be active in South Korea. The group targeted on workers in the field of diplomacy and national security to deliver spear phishing emails disguised to have been sent from a worker of a specific research center. The MS Word malware attached to the email downloaded and executed an additional malware. In the final stage, information saved in the web browser was collected and sent to the C2 server.
SectorA06 group was found to be active in England, South Korea, the United States, and Canada. The group distributed MS OneNote document disguised as documents related to cryptocurrencies, leading the targets to click on the PDF file within the document. In the final stage, the MSI (Microsoft Software Installer) file attached to the MS OneNote executed a DLL malware to gain system privileges and take over system controls.
SectorA07 group was found to be active in South Korea. Windows LNK format malwares were disguised as document related to tax investigations by the National Tax Service, such as enforcement rule of National Tax Collection Act or Stamp Tax regulations for businesses, and compressed into a ZIP format for distribution purposes. A legitimate document was compressed together with the malware to disguise the compressed file as a regular file. In the final stage, a Batch script was used to collect information such as list of processes, list of files in download folder and desktop, list of installed files, and network information, which were saved as individual text files and sent to the C2 server.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In April 2023, activities by a total of 4 hacking groups were identified, and the groups were SectorB01, SectorB10, SectorB22 and SectorB23.
SectorB01 group was found to be active in Germany, Australia, Taiwan, Hong Kong, the United States, Japan, Singapore, Latvia, Micronesia, China, Vietnam, and South Korea. The group distributed ELF (Executable and Linkable Format) malware with the aim of attacking Linux systems. In the final stage, system information was compromised and the distributed malware was used to set the base for downloading and executing Penetration testing tools such as Cobalt Strike.
SectorB10 group was found to be active in Kazakhstan. The group distributed RTF (Rich Text Format) document malware disguised as project documents written in the Kazakhstan language. When executed, the malware generated and executed additional DLL malware by exploiting vulnerabilities. The malware created in the final stage registered itself in the registry to maintain persistence, and set the base for downloading and executing Penetration testing tools such as Cobalt Strike.
SectorB22 group was found to be active in Poland, Germany, Turkey, Hungary, Egypt, and Australia. The group compressed Windows LNK malware disguised under the topic of Prague Process as a ZIP file for distribution purposes. The malware contained a PowerShell command that generated and executed additional DLL format malware upon execution. The malware executed in the final stage consistently monitors and collects information from the infected system.
SectorB23 group was found to be active in South Korea. The group targeted on workers of construction, diplomacy, education, and politics to carry out their attacks by distributing CHM (Compiled HTML Help) and PE (Portable Executable) malwares disguised under topics related to the Ministry of Unification. In the final stage, the malware consistently monitors the infected system, and carries out various functionalities such as stealing system information or downloading and executing additional malware.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In April 2023, activities by a total of 5 group was identified, and the group was SectorC01, SectorC05, SectorC08, SectorC13 and SectorC19.
SectorC01 group was found to be active in Romania, Poland, Turkey, Germany, Czech Republic, Ukraine, and Italy. The group used phishing websites disguised as news media and portal websites with search engine functions with the aim of stealing account credentials.
SectorC05 group was found to be active in Russia, Poland, Ukraine, and the United States. The group used phishing webpages disguised as a homepage of a defense contractor company and Telegram login pages to steal credentials from web mail users.
SectorC08 group was found to be active in Ukraine, Australia, Moldova and the United States. The group used spear phishing emails disguised as legal document for criminal litigation. The Microsoft HTML Application program (MSHTA) which could execute HTA (HTML Application) was used to attempt download of additional malware.
SectorC13 group was found to be active in Russia. The group used spear phishing emails disguised under contents related to compensation for destroying enemy equipment, and the MS Word malware delivered through emails utilized the template injection technique to download and execute MS Word templates with malicious codes inserted.
SectorC19 group was found to be active in Poland and the United States. The group targeted on European nations registered under NATO to deliver spear phishing emails exploiting Zimbra vulnerabilities with the aim of stealing email account credentials and approach email storage.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In April 2023, activities by a total of 2 hacking groups were identified, and the groups were SectorD01 and SectorD33.
SectorD01 group was found to be active in Jordan. The group used malware with information stealing properties, and exploited the API for EWS(Exchange Web Services) management in order to leak the data.
SectorD33 group was found to be active in the United States. The group targeted on On-premises and cloud environments to use DarkBit Ransomware, and used a ransomware persona to conceal their geopolitical goals.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In April 2023, activities by a total of 4 hacking groups were identified, and the groups were SectorE01, SectorE02, SectorE04, and SectorE05.
SectorE01 group was found to be active in Hungary, Russia, Hong Kong and Singapore. The group targeted on workers of government institutions, national security and defense industries to deliver spear phishing emails disguised as meeting notes for Bangladesh navy joint operations, and was analyzed to have inserted a link to downloading the malware in the body of the email. In the final stage, a remote access malware was used to gain system privileges and take over system controls.
SectorE02 group was found to be active in Estonia, Sri Lanka, Singapore, Iran, India, and Nepal. The group distributed document malwares disguised under various topics such as the Kashmir region of India, monthly execution plans, and PMDU (Prime Minister Deliver Unit). Afterwards, additional malware was used to carry out information collection activities such as keylogging, screen capturing, and collecting file details from desktop and download folders.
SectorE04 group was found to be active in Nepal and Pakistan. The group distributed MS Word malware disguised as documents from the Pakistan Ministry of Home Affairs, which exploits the template injection technique to download MS Word templates containing malicious codes. The template file was seen to be of the RTF (Rich Text Format) format based on the URL address for download, and analysis shows that the downloaded file would have been used to steal information from the infected system.
SectorE05 group was found to be active in the United States, Pakistan, and England. The group used CHM malware disguised under contents related to contract termination due to a breach of a specific obligation, and project plans. The malware was compressed into RAR format for distribution. Afterwards, an additional malware collected information from the system such as network information, system information, list of files in desktop and download folders and sent them to the C2 server.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In April 2023, activities by a total of 1 groups were identified, and the groups were SectorH03.
SectorH03 group was found to be active in India. The group distributed MS PowerPoint malware disguised under topics related to revision of policies, and executing the document leads to the generation and execution of additional malwares through malicious macros. In the final stage, remote access malware was used to gain system authorizations in the infected system and take over system controls.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, India, so it is analyzed that they will continue activities to collect advanced information regarding Indian government agencies’ military and politics to their need.
7. Characteristics of SectorS Group Activities
In April 2023, activities by a total of 1 groups were identified, and the groups were SectorS01.
SectorS01 group was found to be active in Hong Kong and Columbia. The group targeted on workers of government institutions to deliver spear phishing emails impersonating the Columbia Directorate of National Taxes and Customs as well as judicial authorities, prompting the targets to execute the attached PDF malware. In the final stage, the downloaded malware carried out information stealing activities such as keylogging, screen capturing, and collection of system information.
Hacking activities of SectorS group activities to date is to collect advanced information on governmental activities of South American countries such as political, diplomatic, and military activities.
8. Characteristics of SectorT Group Activities
In April 2023, activities by a total of 1 groups were identified, and the groups were SectorT01.
SectorT01 group was found to be active in Ukraine. The group impersonated workers of a Ukrainian passport office to deliver phishing emails, leading the targets to access phishing websites disguised as Ukrainian mail systems or portal sites. The phishing websites were built similarly to the legitimate service, and was deduced to have been attempting to steal credentials such as email or account information of the targets.
It is analyzed that the purpose of the SectorT hacking group’s hacking activities to date is to collect advanced information on government activities of EU countries such as political, diplomatic, and military activities.
9. Characteristics of cybercrime group activities
In April 2023, activities by a total of 6 hacking groups were identified, and the groups were SectorJ06, SectorJ09, SectorJ25, SectorJ64, SectorJ72, and SectorJ103.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ06 group was found to be active in the United States, Hungary, Slovenia, Singapore, Italy, and the United Kingdom. The group used .NET format malwares to steal various information saved in systems.
SectorJ09 group continued to use their hacking strategy of inserting obfuscated skimming scripts in websites to collect username, address, email, phone number and credit card details from the payment page.
SectorJ25 group was found to be active in Mongol, the United Kingdom, and Indonesia. The group targeted on cloud and container environments to use cryptojackers that mines cryptocurrencies.
SectorJ64 group was found to be active in Germany. The group targeted on VMware Horizon servers with weak security settings or exposed to the Log4Shell vulnerabilities (CVE-2021-44228, CVE-2022-26134) to attempt cryptocurrency mining.
SectorJ72 group used Windows LNK format malwares, and used QNAP NAS devices with credentials compromised due to weak security settings as the C2 server.
SectorJ103 group was found to be active in Germany. The group sold various malwares including information stealer malwares and remote access malwares, through MaaS (Malware-as-a-Service).
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
