Monthly Threat Actor Group Intelligence Report, August 2023 (ENG)
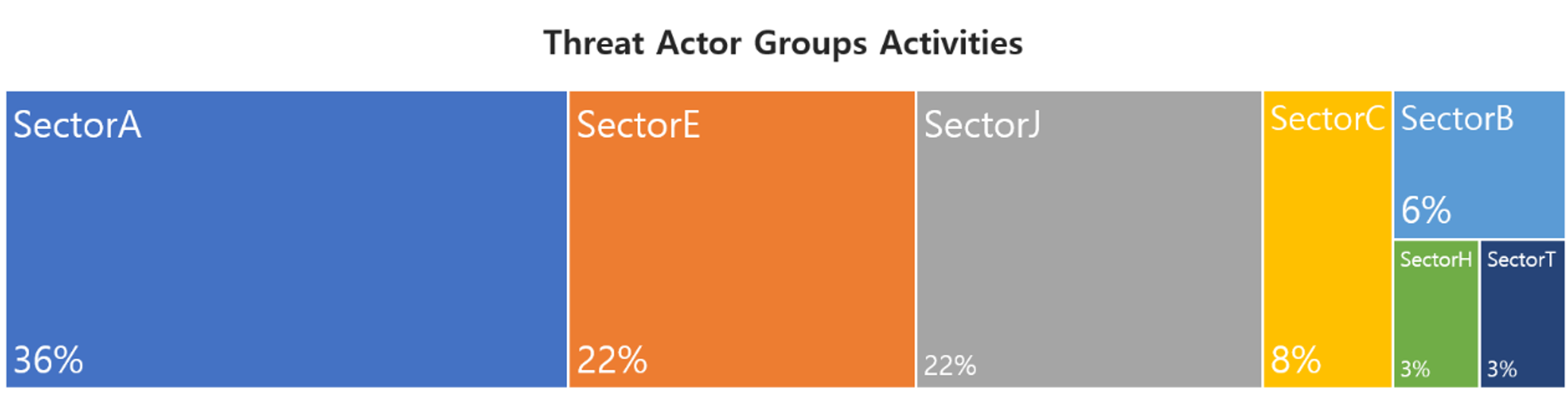
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 July 2023 to 20 August 2023. In August, activities by a total of 22 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 36%, followed by SectorE and SectorJ groups.
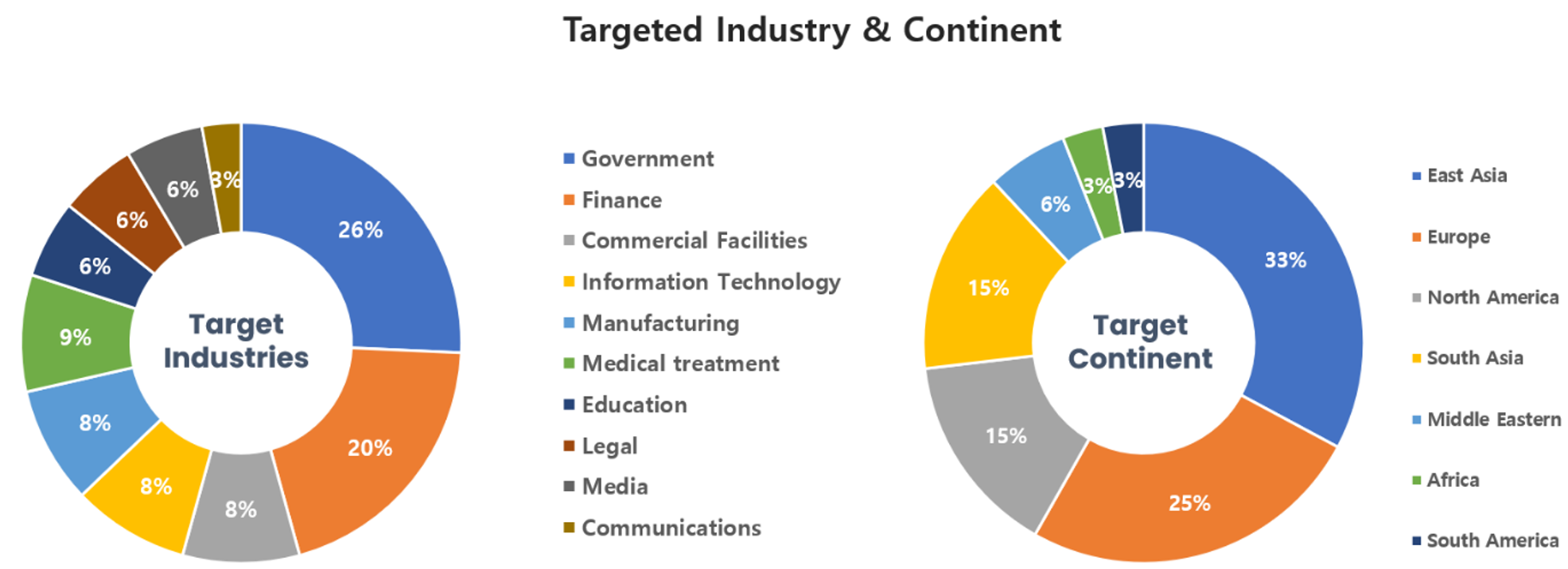
Hacking group activities discovered in August targeted most of their attacks on government officials or systems engaged in the financial sector, and it has been confirmed that the most hacking activities were directed at countries located in East Asia and Europe.
1. Characteristics of SectorA Group Activities
In August 2023, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA07 groups.
SectorA01 group was found to be active in Russia, the United States, Korea, Hong Kong, and Singapore. This group attempted cyber-attacks on various companies using the US server management software company JumpCloud. Ultimately, they downloaded and executed Malware that collected system information and executed shell commands.
SectorA02 group was found to be active in China, Russia, South Korea, Russia, the United States, and Philippines. The group used a Windows Help File (CHM) in the guise of an insurance contract status topic, and ultimately downloaded and ran additional Malware via the PowerShell command.
SectorA05 group was found to be active in South Korea, the United Kingdom, and the United States. The group used malicious code in the form of Visual Basic Script (VBS) files disguised as agreements, and the final executed VBS malicious code acts as a Dropper, which generates and executes Batch file-formatted malicious code based on the data sent by the attackers.
SectorA07 group was found to be active in South Korea and Hong Kong. The group used a Windows shortcut (LNK) disguised as a cooperation guide, and eventually used a Visual Basic Script (Visual Basic Script) to collect system information and a Batch (Batch) script file.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In August 2023, activities by a total of 2 hacking groups were identified, and the groups was SectorB01, SectorB04.
SectorB01 group was found to be active in Hong Kong, Thailand, Japan, Bangladesh, Taiwan, Afghanistan, Cambodia, Czech Republic, Bhutan, India, Malaysia, Nepal, Palestine, Pakistan, Philippines, the United States, Laos, and Vietnam. The group distributed penetration testing tools and remote control tools targeting various organizations including government agencies, aerospace, media, and research and development (R&D), and abused the tools to maintain long-term access to the networks of the targeted organizations.
SectorB04 group was found to be active in Japan and Taiwan. The group distributed the Cobalt Strike Penetration Testing tool, targeting the gambling sector in Asia, to carry out information theft activities.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In August 2023, activities by a total of 2 hacking groups were identified, and the groups were SectorC04, SectorC08.
SectorC04 group was found to be active in the United States, Poland, Slovakia, and Romania. The group used malicious code in the form of an Adobe PDF file disguised as a German embassy document, and if the targeted PDF malicious code is executed, additional malicious code is downloaded through HTML scripts contained in the file. The PE-formatted malicious code eventually executed collects system information and performs various commands according to commands from the C2 server.
SectorC08 group was found to be active in Poland. The group used Malware disguised as military flight plan documents, and if the target of the attack executed the document, additional Malware would be downloaded and executed.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorE Group Activities
In August 2023, activities by a total of 4 hacking groups were identified, and the groups was SectorE01, SectorE04, SectorE05, SectorE06.
SectorE01 group was found to be active in China, Micronesia, and Taiwan. The group distributed a Windows shortcut file (LNK) disguised as an International Society for Scientometrics and Informetrics conference, and conducted information theft activities such as system information and screen capture according to commands received from the C2 server on the target system.
SectorE04 group was found to be active in the United States and Hong Kong. The group distributed a MS Excel (Excel) document disguised as employee details and employee list, and through the download macro feature, allowed for the download of Malware to create a platform for future attacks.
SectorE05 group was found to be active in China, the United Kingdom, Pakistan, Israel and the United States. This group distributed a Windows Help file (CHM) disguised as the 8th China-Southeast Asia Think-Tank Forum and Letter, and installed malicious code with remote control function on the targeted system to perform various malicious activities such as system information theft, file download, screen capture, etc. according to the commands received from the C2 server.
SectorE06 group was found to be active in India and Singapore. The group disguised itself as a secure chat app and distributed Android Malware, and performed malicious behavior such as monitoring Messenger apps, stealing sensitive information such as SMS messages, call records and contacts, according to commands received from the C2 server.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
5. Characteristics of SectorH Group Activities
In August 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorH03.
SectorH03 group was found to be active in India. This group distributed MS Excel (Excel) documents disguised as personal information, and eventually used malicious code known as the CrimsonRAT, which is known for its remote control capabilities, to steal system information from the target system, keylogging, and screen capture.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
6. Characteristics of SectorT Group Activities
In August 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorT02.
SectorT02 group used malicious code disguised as an anti-virus update file targeted at diplomats, ultimately collecting various document files such as DOC, XLS, PDF, and using the SMTP protocol to extract data.
SectorT hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
7. Characteristics of Cyber Crime Group Activities
In August 2023, activities by a total of 8 hacking groups were identified, and the groups were SectorJ04, SectorJ06, SectorJ12, SectorJ45, SectorJ73, SectorJ74, SectorJ110, SectorJ123.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ04 group was found to be active in the United Kingdom, Pakistan, France and India. The group attempted to steal data from systems exposed to MOVEit Transfer vulnerability (CVE-2023-34362) or distribute Cl0p Ransomware.
SectorJ06 group was found to be active in Israel, South Korea, Belgium, Germany, and Qatar. The group used Monit Ransomware targeting government and legal service agencies.
SectorJ12 group was found to be active in Italy, United Kingdom and Germany. The group disguised itself as an Italian logistics and courier company and distributed spam mail, ultimately attempting to gain control of targeted systems by deploying a form of remote controlled malware.
SectorJ45 group was found to be active in the United States. The group targeted users who used web browsers no longer supported by Microsoft and used Exploit Kits, eventually using Cryptocurrency Mining Malware.
SectorJ73 group was found to be active in Japan, Sweden, France, Arab Emirates, Poland, India, Ghana, Czech Republic, Italy, Nigeria, Indonesia, Turkey, Germany and the United States. The group used Ryhsida Ransomware against educational and manufacturing sectors to gain financial gains.
SectorJ74 group was found to be active in Brazil, San Marino, Hong Kong, Switzerland, France, Italy, Spain, Peru, Argentina, Germany, the United States, Austria, India, and the United Kingdom. The group distributed phishing emails with attached compressed files containing malicious code in the form of Windows Control Panel files (CPL) disguised as tax-related documents and has attempted to install malicious code with remote control capabilities on systems through PowerShell scripts for the purpose of system information collection and commands and control.
SectorJ110 group was found to be active in Slovakia and Ukraine. The group sent phishing mails with an attached compressed file that contained a malicious JavaScript file disguised as an invoice inside. Finally, it used malicious code which had the capability of downloading and executing additional Malware.
SectorJ123 group was found to be active in Brazil and Spain. The group used a phishing site pretending to be a bank, and induced victims to enter financial information or transfer money directly.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
