2023 The First Half Activities Summary of Ransomware Threat Actors (EN)
Executive Summary
NSHC Threat Research Lab has analyzed information about hacking groups that have used Ransomware during the first half of 2023. Hacking activities using Ransomware have been continuously occurring up to now and it has been confirmed that the effects caused by the dissemination of Ransomware with the purpose of obtaining monetary compensation are great.
Therefore, it is necessary to prepare prevention and response systems based on information about the attack techniques and tools used by hacking groups using malware recently. This report describe the attack techniques and attack tools used by hacking groups using malware and information about infrastructure.
Activities of Hacking Groups Using Ransomware
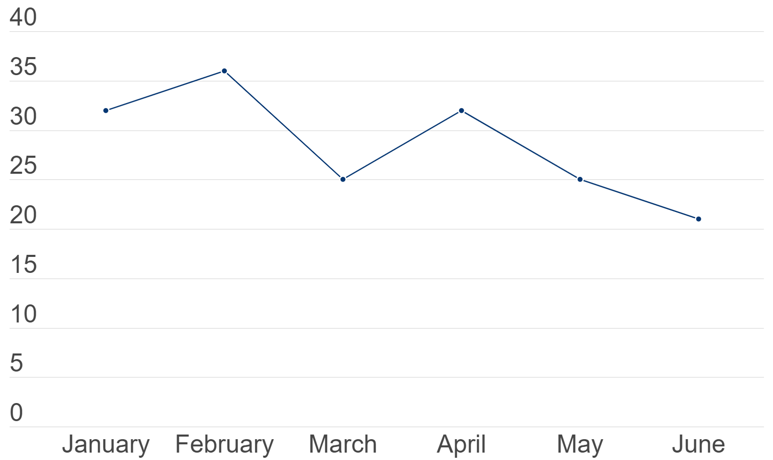
Based on the data and information collected and analyzed by the NSHC Threat Research Lab from January 1, 2023 to June 30, 2023, a total of 141 hacking events related to Malware were confirmed in the first half of 2023.
[Figure 1: Monthly Status of Ransomware Events in the First Half of 2023]
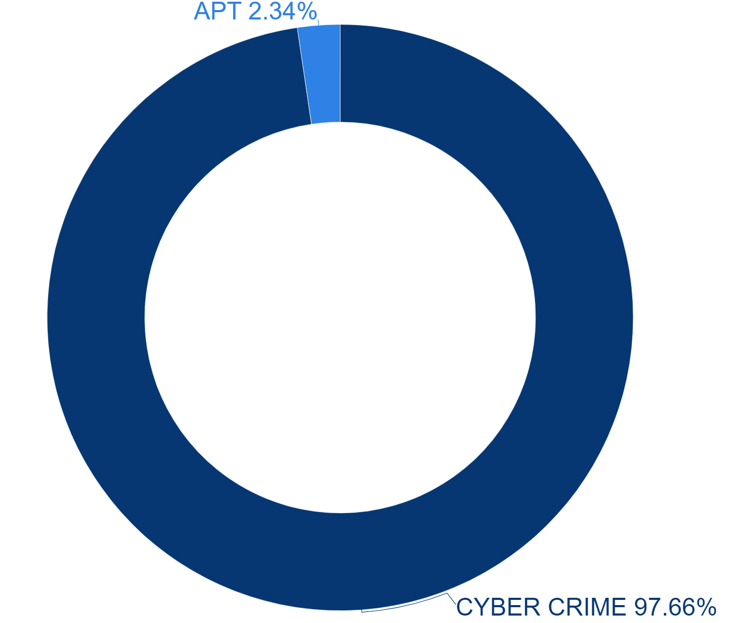
Hacking groups using malware can be classified into cybercrime groups aiming to obtain financial gains and hacking groups receiving government support for special purposes. It has been confirmed that in the first half of 2023, 97% of the hacking activities of cybercrime groups were using malware. Therefore, it has been confirmed that the purpose of malware detected in the first half of 2023 is mainly to obtain financial gains.
[Figure 2: Statistics on Ransomware Hacking Groups in the First Half of 2023]
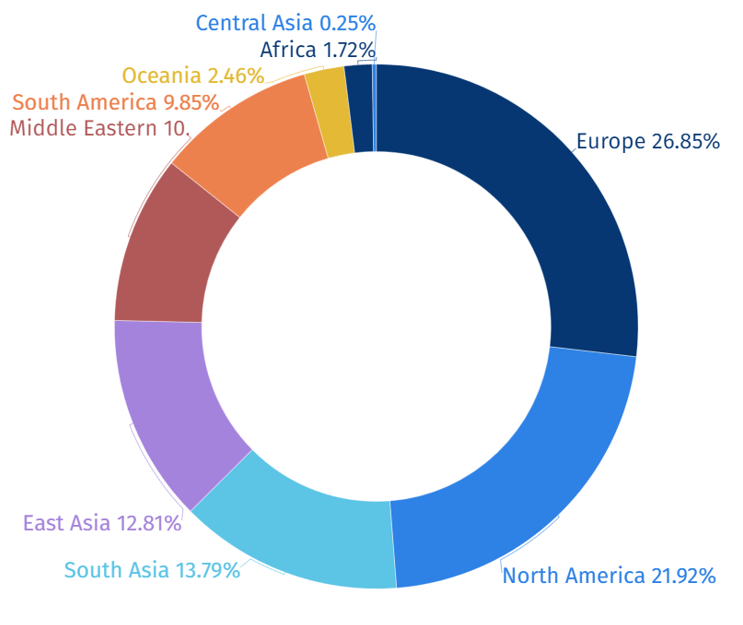
Classifying the regions where hacking groups using malware have been discovered, as shown in Figure 3, it has been confirmed that most hacking activities were conducted on organizations located in Europe and North America.
[Figure 3: Statistics of Areas Targeted in the First Half of 2023]
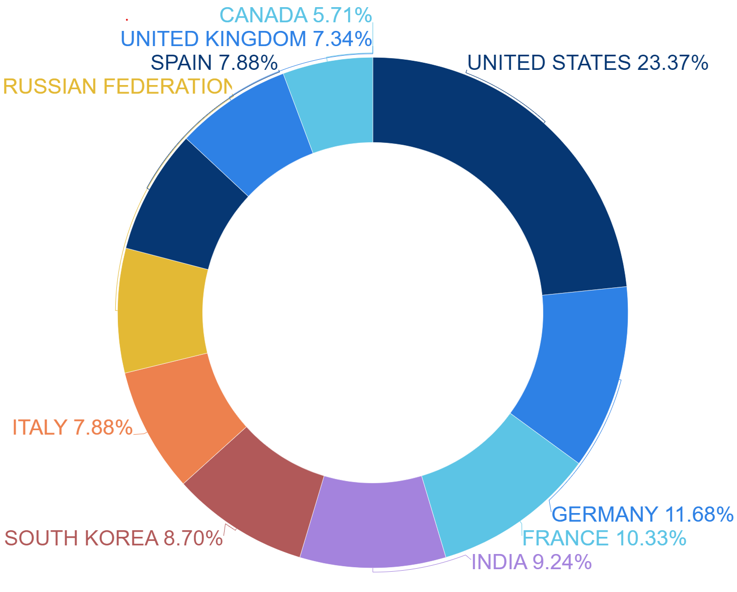
Additionally, the countries that were the targets of hacker groups using malware during the first half of 2023 were found to be the highest with the United States at 23.37%, followed by Germany and France in the higher rankings.
[Figure 4: National Statistics Targeted in the First Half of 2023]
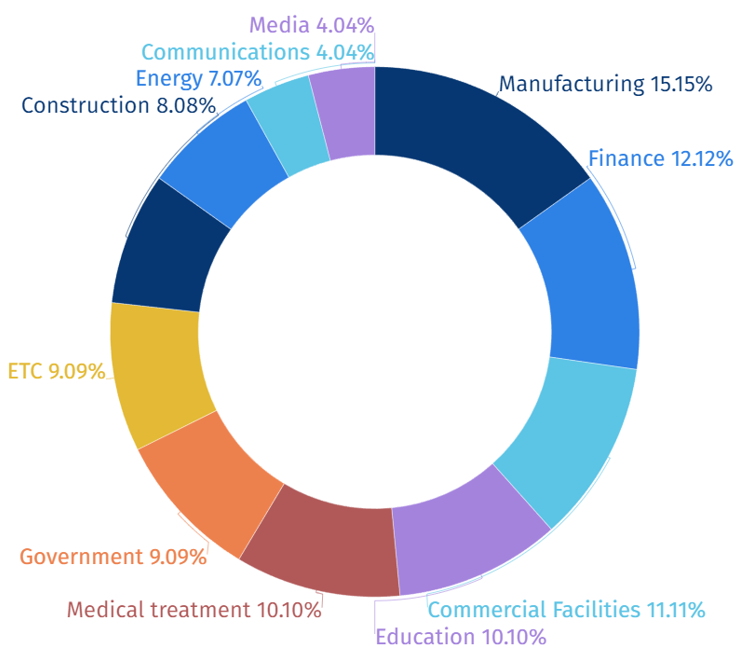
In the first half of 2023, it was confirmed that hacking groups using Malware conducted the most hacking activities targeting personnel or systems working in the manufacturing, financial and commercial facilities sector. It is analyzed that these hacking groups, which are active for cybercrime purposes, become the main targets of hacking activities using Malware when a Malware attack occurs, resulting in significant damage to production activities.
[Figure 5: Statistics of Industries Targeted in the First Half of 2023]
ATTACK TECHNIQUES OF HACKING GROUPS USING MALWARE
1. VULNERABILITY EXPLOITATION
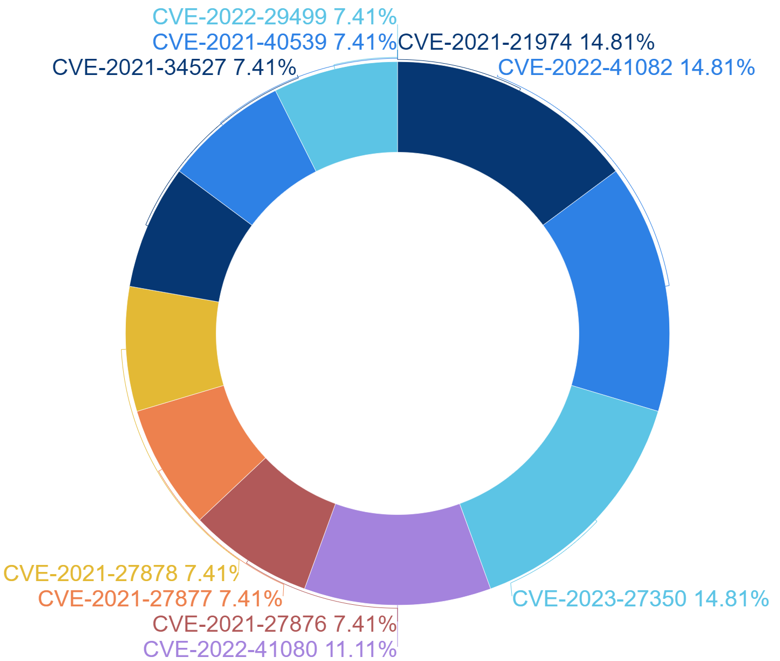
Hacking groups using malware have been found to check if vulnerable versions of software exist in the target organization and use the vulnerabilities of this software for attack. According to a survey conducted in the first half of 2023, the most exploited software vulnerabilities by hacking groups using malware are shown in Table 1.
| Vulnerability | Type of Vulnerability | Target |
|
CVE-2021-21974 |
Remote Code Execution Vulnerability | VMware ESXi OpenSLP Services |
|
CVE-2022-41082 |
Remote Code Execution Vulnerability |
Microsoft Exchange Server |
|
CVE-2023-27350 |
Improper Access Control Vulnerability |
PaperCut MF/NG Improper |
|
CVE-2022-41080 |
Privilege Escalation Vulnerability |
Microsoft Exchange Server |
|
CVE-2021-27876 |
File Access Vulnerability |
Veritas Backup Exec Agent |
|
CVE-2021-27877 |
Improper Authentication Vulnerability |
Veritas Backup Exec Agent |
|
CVE-2021-27878 |
Command Execution Vulnerability |
Veritas Backup Exec Agent |
|
CVE-2021-34527 |
Remote Code Execution Vulnerability |
Microsoft Windows Print Spooler |
|
CVE-2021-40539 |
Authentication Bypass Vulnerability |
Zoho ManageEngine ADSelfService Plus |
| CVE-2022-29499 | Data Validation Vulnerability |
Mitel MiVoice Connect |
[Table 1: List of Vulnerabilities Utilized by Hacking Groups Using Malware]
Hacking groups using malware have been found to heavily utilize Remote Code Execution Vulnerabilities (RCE) which allow them to remotely execute certain commands, as well as Improper Access Control Vulnerabilities which allow them to control access to files and directories, and other resources on the target of attack.
Of the particularly identified vulnerabilities, eight out of the top ten were identified as applications classified as servers. When an attack is performed by exploiting the vulnerabilities on the server, not only can the attacker gain persistent access and evade detection by elevating privileges, but also gain access to sensitive data, and can spread the damage by performing internal reconnaissance (Lateral Movement). It is confirmed that attackers target servers to exploit such characteristics.
[Figure 6: Statistics on the use of vulnerabilities by hacking groups using Malware]
2. OPEN-SOURCE TOOLS AND FREEWARE UTILIZATION
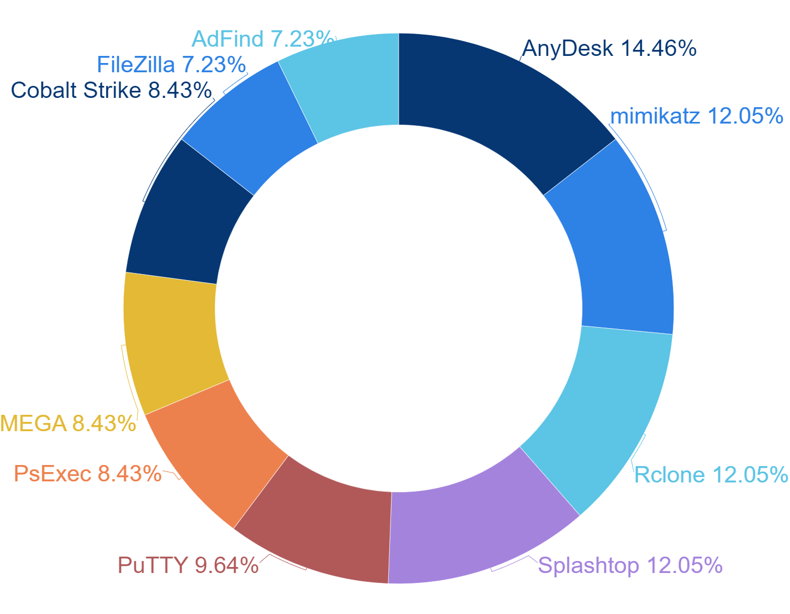
Hacking groups using malware are known to use Open-Source tools and Freeware for moving within the target organization and spreading malware. It was confirmed that the most frequently used Open-Source tools and Freeware by hacking groups using malware during the first half of 2023 were “AnyDesk”, which provides remote control functions.
Additionally, the group utilized widely known credential collecting tools, “Mimikatz” and “Rclone” which aids to manage cloud storage services remotely with command-line commands occupying the place.
[Figure 7: Tool Statistics Utilized By Hacking Groups Using Malware]
[Figure 8: AnyDesk Homepage Screen]
Based on the results of checking the characteristics of the tools used mainly by hacking groups using malware, programs that can remotely control the targets of attack or tools to collect and manage account information to gain administrator privileges were found to be used. In addition, file transfer programs used to move data collected from the target of attack to the outside, as well as cloud storage related programs, are also often used.
|
Tool |
Tool Function |
Link |
|
AnyDesk |
Remote Controlling Programme | https://anydesk.com/ |
|
mimikatz |
Collecting Windows Credential Information |
https://github.com/gentilkiwi/mimikatz |
|
Rclone |
Cloud Storage Service |
https://rclone.org/ |
|
Splashtop |
Remote Controlling Program |
https://www.splashtop.com/ |
|
PuTTY |
Remote Controlling Program |
https://www.putty.org/ |
|
PsExec |
Remote Controlling Program |
https://learn.microsoft.com/en-us/sysinternals/downloads/psexec |
|
MEGA |
Cloud Storage Service |
https://mega.io/ |
|
Cobalt Strike |
Penetration Testing |
https://www.cobaltstrike.com/ |
|
FileZilla |
File Transfer Program |
https://filezilla-project.org/ |
|
AdFind |
Collecting Windows Active Directory Information |
http://www.joeware.net/freetools/tools/adfind/ |
[Table 2: List of Tools Used by Hacking Groups Utilizing Malware]
INFRASTRUCTURE OF HACKING GROUPS USING MALWARE
When a ransomware detects that data has been encrypted in the system of the targeted organization, it generates a ransom note indicating the procedures of making financial payments to the hacking group that has used the ransomware. Generally, the generated ransom note contains infrastructure details such as methods to communicate with the hacking groups or a cryptocurrency wallet address to receive the ransom.
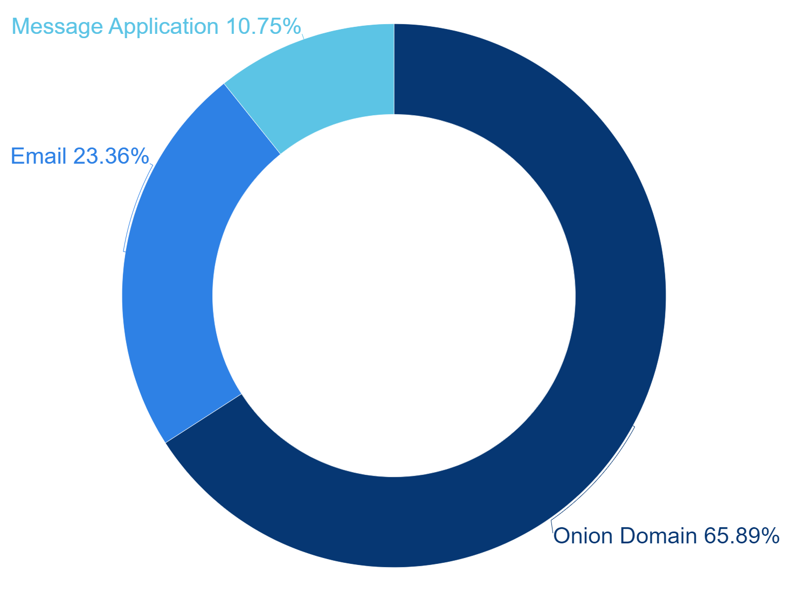
During the first half of 2023, it was confirmed that the infrastructure used by hacking groups utilizing Ransomware existing on Ransom Note was mainly consisting of Onion domains, email addresses, and social media platforms.
During the first half of 2023, analysis if infrastructure indicated in the ransom note shows that Onion domains, email addresses and social media platform were commonly utilized by hacking groups using ransomware. Among them, Onion domains were utilized most frequently.
[Figure 9: Infrastructure Statistics of Hacking Groups Using Malware]
1.ONION DOMAIN ADDRESS UTILIZATION
The Onion domain is a unique domain that is only accessible through Tor Browser, which is used to access the Deep and Dark web. The domain is often utilized by attackers as it provides anonymity, making the process of tracking difficult.
The reason to why hacking groups using ransomwares utilize the Onion domain could be classified into three main categories. Firstly, hacking groups may use it to publish the list of victimized organizations. Secondly, it is used as a contact point for the victimized companies. In this case, the group uses a unique ID provided in the ransom note as a means of identifying the victim. Lastly, there are cases where websites are operated with multiple contents, including those that are unrelated to ransomwares.
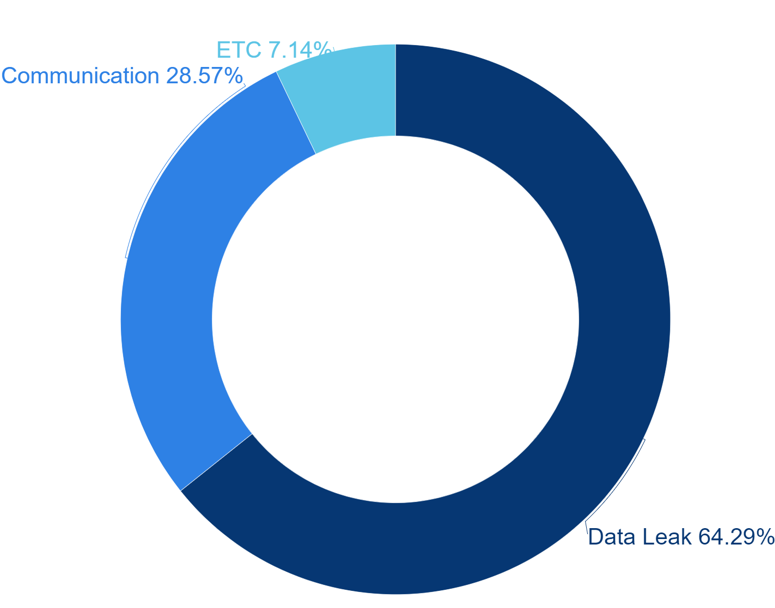
Among ransomware identified in the first half of 2023, it was found that Onion domains were most commonly used to publish the list of companies that had been targeted by the hacking groups.
[Figure 10: Statistics of Group Utilization of Onion Domains Using Malware]
1) Publishing lists of victimized companies
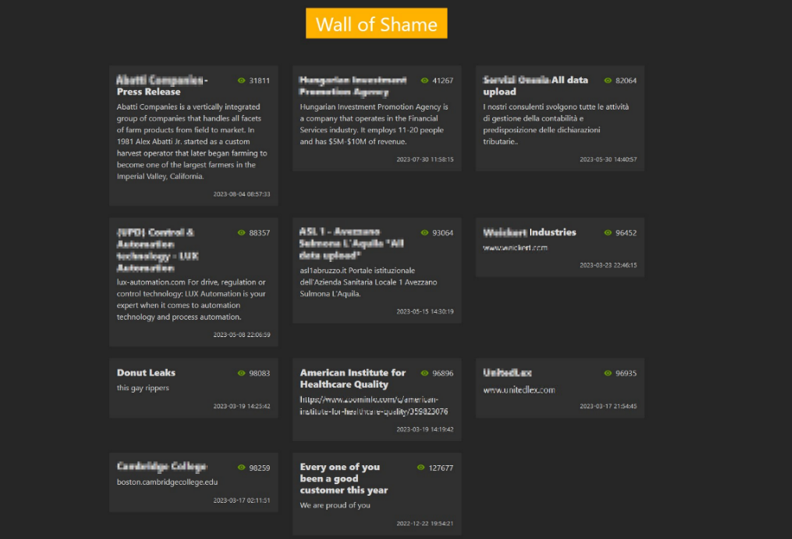
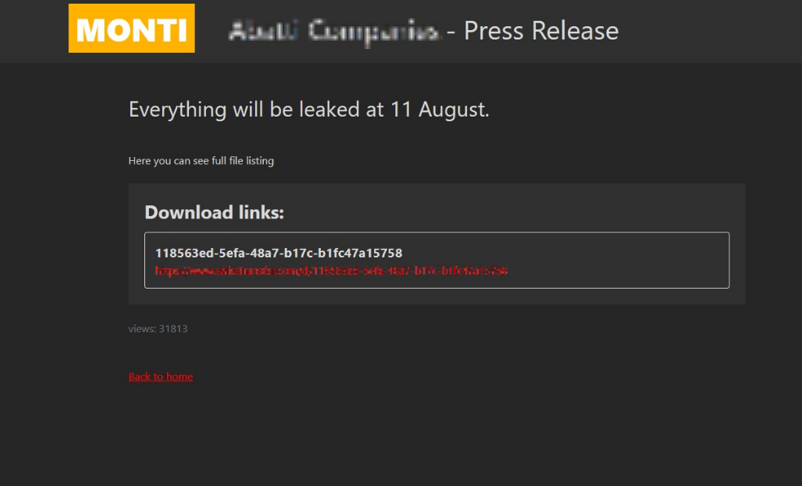
Hacking groups employing ransomware utilize Onion domain addresses for the purpose of publishing lists of victimized companies. When doing so, they publicly disclose certain stolen data, such as file names and file paths, through file-sharing websites, thereby demonstrating that they have successfully exfiltrated the target’s data. Additionally, they often indicate a deadline for monetary transactions, creating an atmosphere of pressure to pay the ransom for data recovery.
[Figure 11: Utilizing Onion Domain Addresses Operated For The Purpose Of Posting A List Of Affected Companies (1)]
[Figure 12: Utilizing Onion Domain Addresses Operated for the Purpose of Posting a List of Victim Companies (2)]
2) Contacting specific attack targets
In the case of using Onion domains as a means of contacting the victimized companies, access is granted only after entering a specific string. The specific string used to differentiate the targets are called differently across various ransomware groups, such as “Personal ID” or “Decryption ID”, and they are provided in the ransom note generated during the target data encryption process.
[Figure 13: Onion Address Operated for the Purpose of Contacting Specific Attack Targets]
3) Others
Some ransomware hacking groups were identified to be selling drugs and hacking tools in their Onion domain address, on top of ransomware.
[Figure 14: Screen of Onion Website Utilized for Multiple Purposes]
2. Social Media Platform Utilization
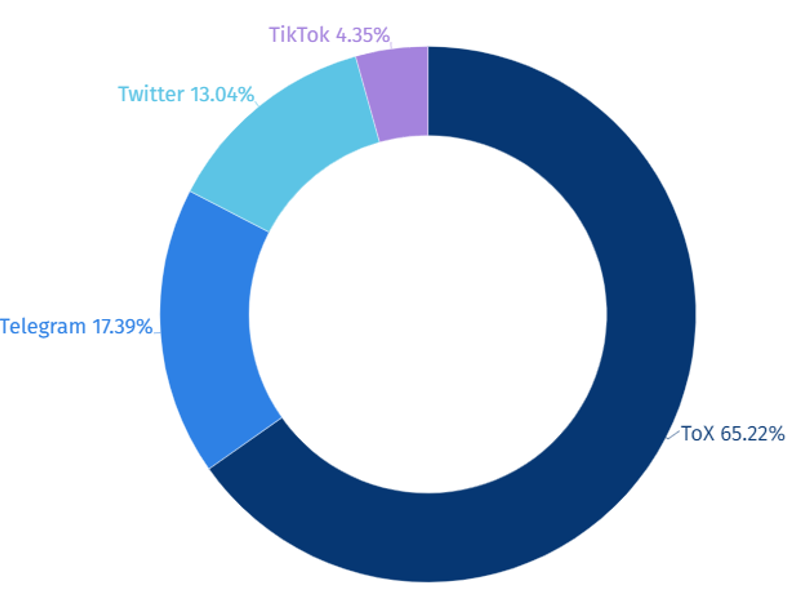
Ransomware hacking groups predominantly utilize the social media platform Tox, accounting for 65% of their contact methods with their targets. Tox is a messenger service that does not require personal information such as phone numbers or email addresses during registration, and it offers encryption features similar to Telegram, thus it has been observed that Tox messenger applications are actively employed by these groups.
[Figure 15: Statistics of Social Media Platforms Utilized by Hacking Groups Using Malware]
[Figure 16: Tox Settings Screen]
3. Email Domain
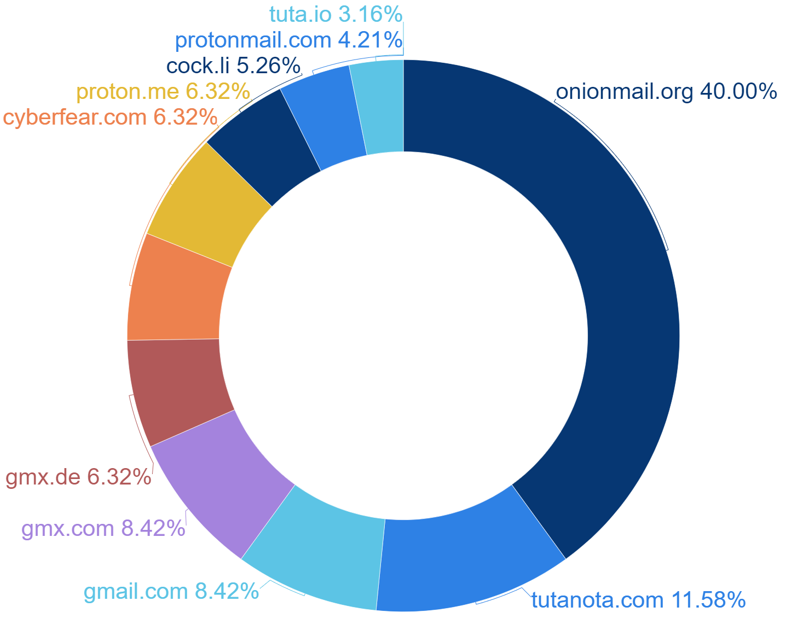
Ransomware hacking groups also employ email as a means to contact their targets, with the most frequently used email domain being “onionmail.org,” accounting for 30% of their communications. The “onionmail.org” domain is preferred for its ability to encrypt emails using PGP keys and ensure anonymity, making it the top choice for these groups.
[Figure 17: Statistics on Email Domains Used by Ransomware Hacking Groups]
[Figure 18: Onion Mail Homepage]
4. TYPES OF CRYPTOCURRENCIES
Ransomware hacking groups have been utilizing cryptocurrencies as a means to receive monetary gains from their victims. Cryptocurrencies offer the advantage of anonymity, as only the transaction address and ID are recorded, with no personal information being publicly disclosed. This characteristic allows these groups to conceal their identities and evade tracking by law enforcement agencies, making cryptocurrencies the preferred form of payment for the funds they receive.
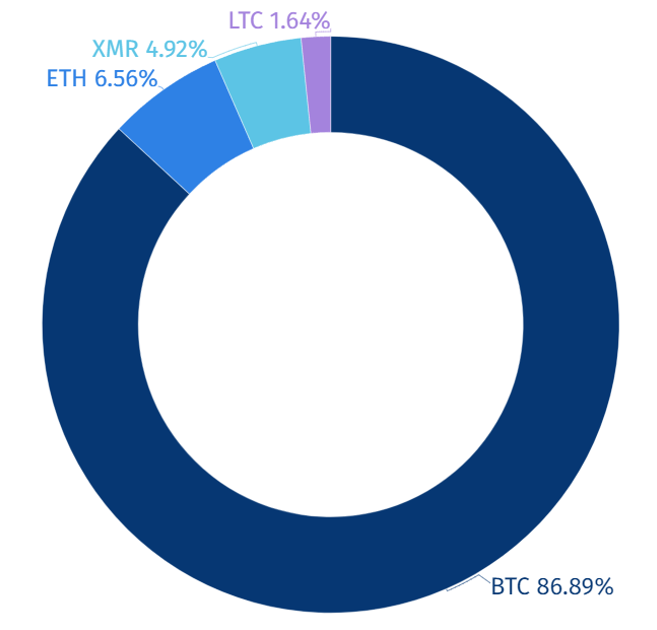
During the first half of 2023, it has been confirmed that ransomware hacking groups have used four types of cryptocurrencies: Bitcoin (BTC), Ethereum (ETH), Monero (XMR), and Litecoin (LTC). Among these, Bitcoin is the most widely used, constituting 86% of their transactions. Bitcoin is a well-known cryptocurrency with high public awareness and accessibility, making it the preferred choice for ransomware hacking groups to receive payments.
|
Cryptocurrency |
Symbol |
Characteristics |
|
Bitcoin |
BTC |
The oldest, widely recognized and able to operate without involvement of central authorities |
|
Ethereum |
ETH |
A highly flexible cryptocurrency platform capable of executing smart contracts |
|
Monero |
XMR |
A cryptocurrency that prioritizes privacy and anonymity, concealing transactions history and ownership |
|
Litecoin |
LTC |
A cryptocurrency with fast transaction processing speed and low fees |
[Table 3: Cryptocurrencies Utilized by Hacking Groups Using Malware]
[Figure 19: Cryptocurrency Statistics Used by Hacking Groups Utilizing Malware in the First Half of 2023]
Conclusion
This report provides an overview of the various attack techniques and tools used by ransomware hacking groups during the first half of 2023. It illustrates that these groups have diversified their technology and infrastructure, indicating the evolving nature of their ransomware attacks.
As evident from the ransomware incident cases described in this report, ransomware attacks can lead to significant disruptions and damages, such as service outages. To mitigate such damages, it is crucial to establish preparedness and response mechanisms based on recent attack-related data and intelligence.
Therefore, obtaining cyber threat intelligence regarding the attack techniques and tools employed by ransomware hacking groups allows for the development of proactive response systems using the latest attack techniques and related data.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.