Monthly Threat Actor Group Intelligence Report, October 2023 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 September 2023 to 20 October 2023.
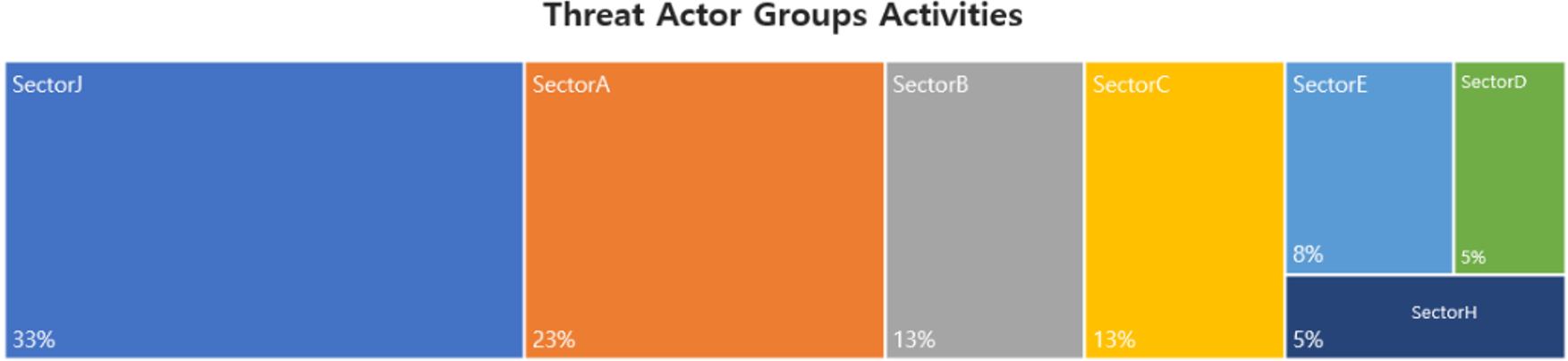
In October, activities by a total of 31 Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 33%, followed by SectorA groups and SectorB groups.
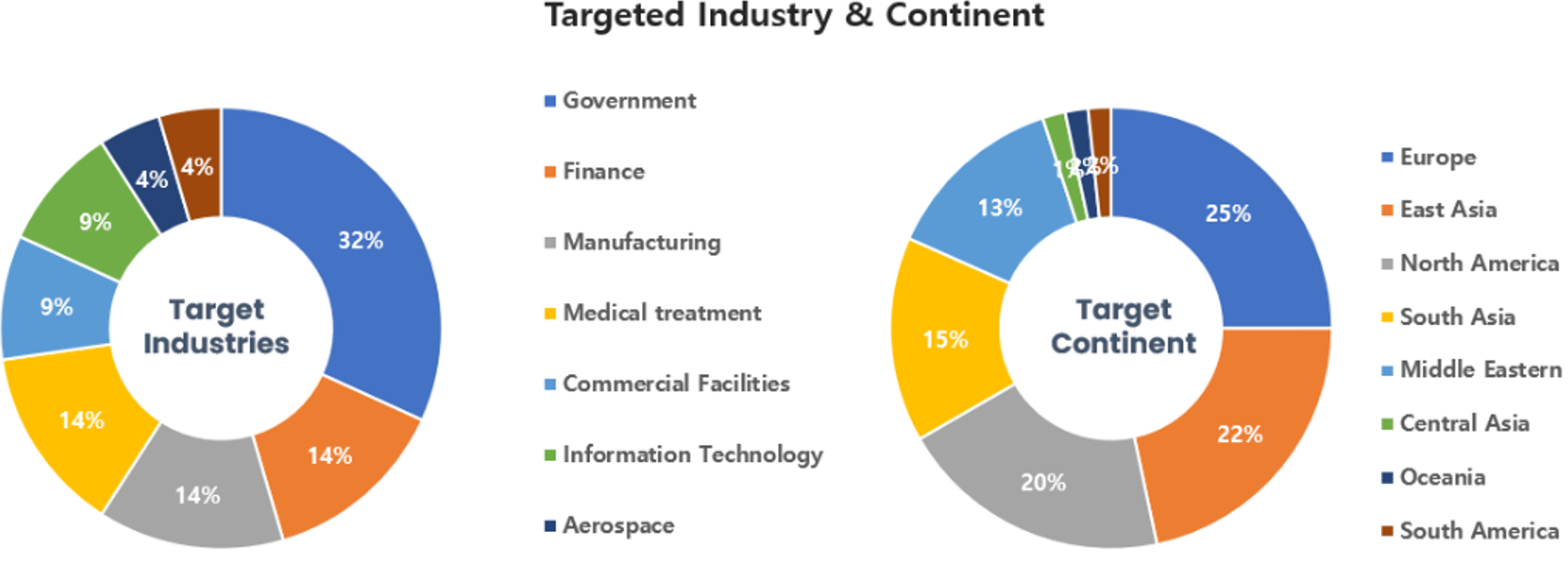
Threat Actors identified in October carried out the highest number of attacks on workers and systems in government agencies and commercial sectors. Regionally, Europe and East Asia were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In October 2023, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, and SectorA07.
SectorA01 group was found to be active in Singapore, India, Poland and the United Kingdom. The group deceived recruiters and induced them to deliver and execute malicious code disguised as a recruitment offer PDF file via a social platform and, ultimately, the malicious code that is executed performs various functions depending on the information collected and attacker server commands.
SectorA02 group used a malicious code in the form of a Windows shortcut (LNK) disguised as a document related to the results of the Supreme People’s Assembly of North Korea, and eventually downloaded additional malware through a PowerShell command to run in the memory area.
SectorA05 group was found to be active in South Korea, Israel, and Ireland. The group attempted to collect account information using a phishing web page that spoofed the Korean portal site log-in page.
SectorA07 group was found to be active in South Korea and the United States. The group used malware in the form of Windows Help (CHM, Compiled HTML Help) files disguised as payroll records and ultimately downloaded and executed additional malware through PowerShell commands.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In October 2023, activities by a total of 7 hacking groups were identified, and the groups were SectorB01, SectorB08, SectorB21, SectorB22, SectorB80, SectorB82, and SectorB83.
SectorB01 group was found to be active in Hong Kong, Taiwan, Singapore, and the United States. The group distributed malware with loader capabilities that executed Cobalt Strike on the semiconductor industry in the East Asia region. According to the commands received from the C2 server, the group performed various commands such as keylogging, screen capture, and system information theft.
SectorB08 group distributed malicious code with a loader function to execute additional malicious code through a Spear-Phishing Email and executed various commands according to the commands received from the C2 server in the target system, such as keylogging, screen capture, and system information theft.
SectorB21 group was found to be active in India, Thailand, Hong Kong, Taiwan, Kazakhstan, the United Kingdom, and China. The group distributed various malicious code apps targeting Android and Apple iOS devices and executed various commands to steal sensitive information such as device information, SMS messages, call records, and contact information on the target terminal according to the command from the C2 server.
SectorB22 group was found to be active in the United States, Thailand, and Japan. The group abused various open-source tools to launch attacks against governments in Southeast Asia and uploaded sensitive documents and information to the file hosting service Dropbox.
SectorB80 group was found to be active in the United States, Netherlands, and Mongolia. The group distributed various backdoors to target diplomatic entities of the Association of Southeast Asian Nations (ASEAN) members and conducted attack activities. In the targeted systems, it collected various system information in accordance with the commands of the C2 server, downloaded malware remotely, and loaded additional functions.
SectorB82 group was found to be active in the Czech Republic, Taiwan, Hong Kong, the United States, Poland, and China. This group has launched attacks, with the purpose of collecting information, targeting various organizations in the manufacturing, IT, and biomedical fields in Taiwan.
SectorB83 group exploited the private vulnerability (CVE-2023-22515) of Atlassian Confluence’s Confluence Data Center and Server instance.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In October 2023, activities by a total of 3 hacking groups were identified, and the groups were SectorC01, SectorC04, and SectorC08.
SectorC01 group was found to be active in Romania, Poland, Turkey, Germany, Czech Republic, Ukraine, and Italy. The group used phishing websites disguised as news media and portal websites with search engine functions with the aim of stealing account credentials.
SectorC04 group was found to be active in Russia, Poland, Ukraine, and the United States. The group used phishing webpages disguised as a homepage of a defense contractor company and Telegram login page to steal credentials from web mail users.
SectorC08 Ukraine, Australia, Moldova and the United States. The group used spear phishing emails disguised as legal document for criminal litigation. The Microsoft HTML Application program (MSHTA) which could execute HTA (HTML Application) was used to attempt download of additional malware.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In October 2023, activities by a total of 2 hacking groups were identified, and the groups was SectorD01 and SectorD02.
SectorD01 group was found to be active in Russia, Netherlands, the United States, and Israel. The group had used MS Word malware disguised as vehicle license applications and the malware eventually runs to collect username, computer name, and local domain name, and performs various functions according to the attacker’s server commands.
SectorD02 group was found to be active in Israel and Australia. The group used malicious code in the form of Windows Help (CHM, Compiled HTML Help) files disguised as personnel documents, and downloaded and ran VBS (Visual Basic Script) files via PowerShell commands.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In October 2023, activities by a total of 3 hacking groups were identified, and the groups was SectorE02, SectorE04, and SectorE05.
SectorE02 group was found to be active in Pakistan. The group disguised MS Word documents with protected documents and distributed them for attack activities. They also downloaded additional malware from external servers to the attacked systems and executed them to prepare for future attacks.
SectorE04 group was found to be active in Hong Kong. The group disguised their MS Word documents as lecture updates and distributed malicious programs to carry out their attack activities, performing various commands according to the commands of the C2 server on the target systems.
SectorE05 group was found to be active in Singapore and Mongolia. The group distributed Spear-Phishing Emails targeting government and institutions and prepared a foothold for subsequent attacks by downloading additional malicious codes from external servers and executing them on the target systems.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In October 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorH03.
SectorH03 group was found to be active in Pakistan and the United States. The group distributed disguised MS PowerPoint (PowerPoint) documents and MS Word (Word) documents for their attack activities, and in the target systems they carried out various commands such as system information theft, keylogging, and screen capture according to the commands received from the C2 server.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of Cyber Crime Group Activities
In October 2023, activities by a total of 15 hacking groups were identified, and the groups were SectorJ03, SectorJ06, SectorJ09, SectorJ12, SectorJ39, SectorJ55, SectorJ64, SectorJ68, SectorJ90, SectorJ94, SectorJ110, SectorJ125, SectorJ127, SectorJ128, and SectorJ130.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ03 group was found to be active in Palestine and the United States. The group used a malicious code disguised as a Windows Media provisioning plugin, and the malicious code eventually executed could perform various functions according to the attacker server commands, such as downloading and executing additional malicious codes, keylogging, and screen capture.
SectorJ06 group was found to be active in Russia, the United States and Hong Kong. The group attempted attacks using RaaS (Ransomware-as-a-Service) targeting the medical-related industry.
SectorJ09 attempted to collect various information including usernames, addresses, emails, and credit card payment information by inserting obfuscated skimming scripts targeting a wide range of websites including the food and retail industries on payment pages.
Based on the domains and IP addresses used by the SectorJ12 group in the past, additional analysis revealed additional domains starting with avast strings and domains containing the debian strings.
SectorJ39 group was found to be active in Azerbaijan. The group used malicious code in the form of HTML files disguised as PDF documents related to the Azerbaijan-Armenia conflict, and the malicious code that is eventually executed collects and sends system information.
SectorJ55 group was found to be active in United States, South Korea, China, Canada, and Iran. The group used a Cryptominer Malware for virtual currency mining targeted at Docker and Redis servers accessible from the external internet.
SectorJ64 group was found to be active in China, Mexico, South Korea and Peru. The group attempted unauthorized access to Redis servers that were accessible from the external internet without proper security settings and used WebShell.
SectorJ68 group was found to be active in France. The group used malicious code which utilized Telegram bot as the C2 server, and the malicious code had the capability of collecting and exfiltrating system information.
SectorJ90 group was found to be active in the United States, Germany, Luxembourg, India, and Ukraine. The group used a Portable Executable (PE) format of malicious code disguised as images of the day of the Republic of Tajikistan, and if it was determined that additional attack was needed, additional malicious code with remote control functions was distributed.
SectorJ94 group was found to be active in Australia. The group used Windows shortcuts (LNK) in the form of malicious code disguised as PDF documents related to manufacturing technology.
SectorJ110 group was found to be active in Ukraine, Hong Kong, Germany, and the United Kingdom. The group distributed phishing emails with attached archives containing JavaScript files disguised as invoices, which had malicious code that could ultimately download and execute additional malware.
SectorJ125 group was found to be active in the United States. The group sent phishing messages containing Windows Script File (WSF) format malicious code through Microsoft Teams, and ultimately used malicious code with command control capabilities to steal the system privileges of the target of attack.
SectorJ127 group was found to be active in China. This group used Microsoft Word (Word) malware disguised as Red Cross blood donation documents, and if the target of the attack executes the corresponding Microsoft Word (Word) malware, an encrypted macro will be executed. Eventually, the malware executed collects various system information and performs various functions according to the attacker’s server commands.
SectorJ128 group was found to be active in China and France. The group used a PDF document disguised as a resume with a link to download a compressed file inside the document, and the malicious code in the form of a Windows shortcut (LNK) inside the compressed file executes a DLL file type of malware.
SectorJ130 group was found to be active in the United States, United Kingdom, Turkey, Ukraine, Israel, Malaysia, Russia, Poland, Cyprus, Philippines, Italy, and India. This group used instant messengers such as Skype and Microsoft Teams to distribute malware, and VBS (Visual Basic Script) file format malware and Windows shortcut (LNK) file format malware.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
