Monthly Threat Actor Group Intelligence Report, November 2023 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 October 2023 to 20 November 2023.
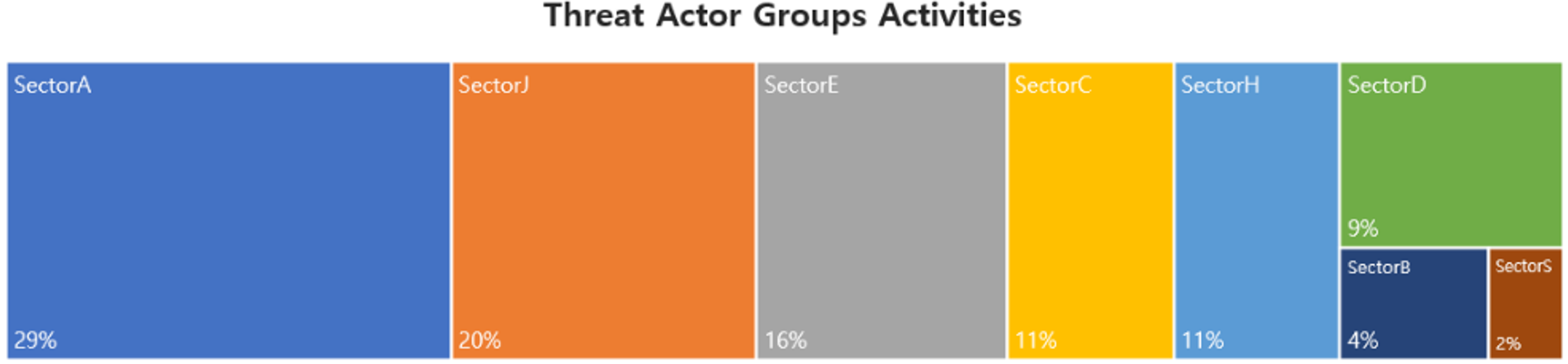
In November, activities by a total of 29 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 29%, followed by SectorJ and SectorE groups.
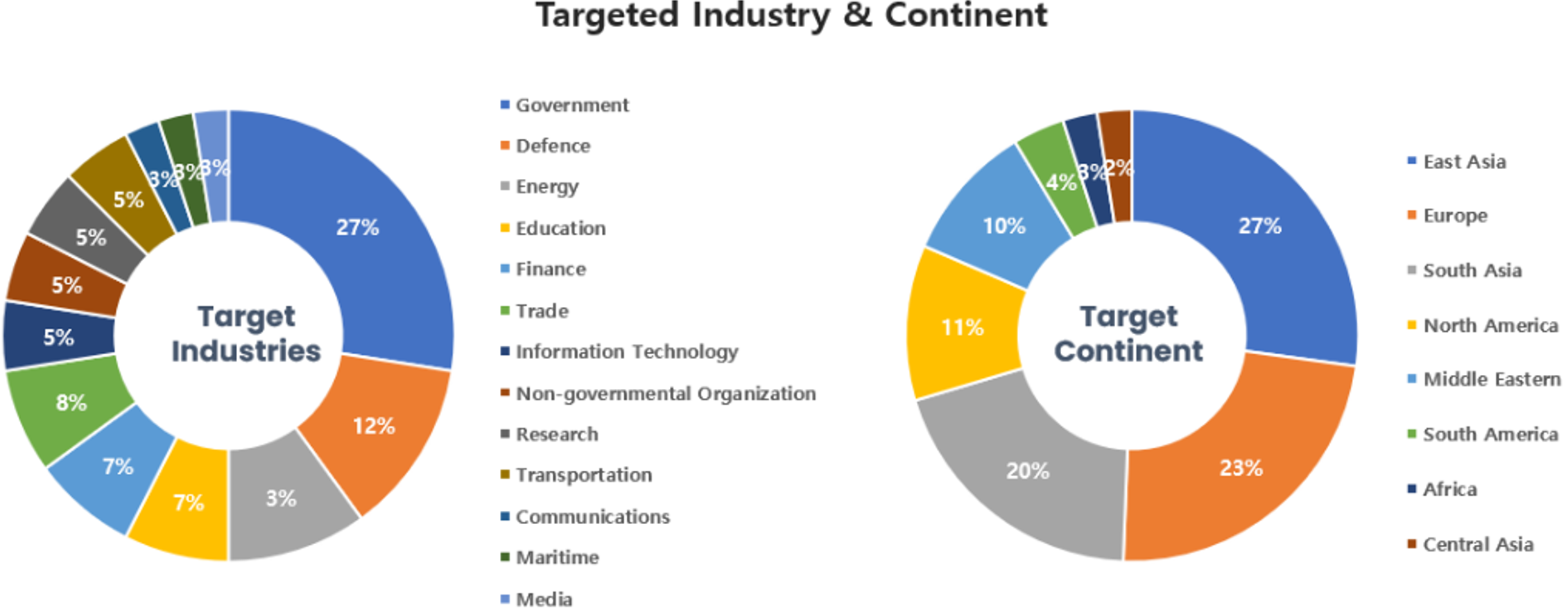
Threat Actors identified in November carried out the highest number of attacks on workers and systems in government officials or systema. Regionally, East Asia and Europe were seen as the continents with the highest number of hacking activities.
1. Characteristics of SectorA Group Activities
In November 2023, activities by a total of 5 hacking groups were identified, and the groups were SectorA02, SectorA04, SectorA05, SectorA06, and SectorA07.
SectorA02 group was found to be active in South Korea and the United States. The group utilized malicious code in the form of a Windows shortcut (LNK) disguised as documents related to North Korean international security and military affairs, ultimately downloading additional malware through PowerShell commands and executing them in memory areas.
SectorA04 group was found to be active in South Korea and Russia. The group abused the vulnerability (CVE-2023-46604) of Apache ActiveMQ to distribute malware with remote control and backdoor functions.
SectorA05 group was found to be active in South Korea. The group used HTML format files disguised as security emails, and induced Windows shortcut (LNK) format malicious code execution disguised as conference fee documents. Eventually, PE file format malicious code was downloaded and executed according to the attacker’s command to perform various functions such as keylogging and information theft.
SectorA06 group was found to be active in Israel, the United States, Mexico, Austria, China, and Japan. The group lured Blockchain engineers on public Discord channels with the impersonation of Blockchain engineers and delivered macOS malware disguised as Python tools, prompting them to execute it.
SectorA07 group was found to be active in South Korea. The group used malicious code in the form of Windows shortcut (LNK) disguised with a tax certificate from the National Tax Service, and ultimately used a Visual Basic Script (VBS) and Batch Script files to collect system information.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In November 2023, activities by a total of 2 hacking groups were identified, and the groups were SectorB04 and SectorB22.
SectorB04 group was found to be active in France, Hungary, and Canada. The group distributed Spear Phishing emails with MS Word documents disguised as bank account information and used the remote-control tool known as QuasarRAT to collect system information, keylogging, video capture with commands received from the C2 server.
SectorB22 group was found to be active in the Philippines, the United States, and Sweden. The group distributed ZIP compressed files disguised as diplomatic policy strategy reports targeting government agencies to conduct attacks. They attempted to disguise C2 server communications as Microsoft Traffic, and then performed various commands according to the instructions received from the C2 server.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In November 2023, activities by a total of 4 hacking groups were identified, and the groups were SectorC05, SectorC08, SectorC13, and SectorC19.
SectorC05 group was found to be active in Ukraine, Taiwan and Denmark. The group attempted malware attacks against Industrial Control Systems (ICS) and arbitrarily operated circuit breakers to cause power outages in important infrastructure facilities.
SectorC08 group was found to be active in the United States, Vietnam, Chile, Poland, Germany, Hong Kong, and Ukraine. The group used malicious code in the form of a Visual Basic Script (VBS) file with a function that propagates through a portable USB drive.
SectorC13 group was found to be active in Russia. The group used malware disguised as basic information registration MS Word document. When executed, a MS Word template containing malicious code was downloaded and executed via the Template Injection technique.
SectorC19 group was found to be active in Greece, Moldova, Vietnam, Pakistan and Tunisia. The group targeted government agencies and abused vulnerabilities in the RoundCube Web Mail server (CVE-2023-5631) and Zimbra Collaboration (CVE-2023-37580).
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In November 2023, activities by a total of 3 hacking groups were identified, and the groups was SectorD02, SectorD15, and SectorD28.
SectorD02 group was found to be active in Jordan, Estonia, Israel and the United Arab Emirates. The group used Malware disguised as Israeli war related Windows shortcut (LNK) and ultimately used a Remote Monitoring Management (RMM) tool to control the target system.
SectorD15 group was found to be active in Israel and the United Kingdom. The group attempted a watering hole attack on transport and logistics-related websites, and used malware created in .NET with a feature to send emails through Internet Messaging Access Protocol (IMAP) accounts.
SectorD28 group was found to be active in the United Arab Emirates, Jordan, Kuwait, Oman, Iraq, Saudi Arabia, and Israel. The group attempted to perform command execution remotely through HTTP requests using Windows HTTP stack driver and continued their malicious activities using WebShell or Backdoor type of additional malware.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In November 2023, activities by a total of 5 hacking groups were identified, and the groups was SectorE01, SectorE02, SectorE03, SectorE04, and SectorE05.
SectorE01 group was found to be active in Pakistan, Bangladesh, and China. The group distributed malicious Windows shortcuts (LNK files) disguised as recruitment documents to launch attacks, sending system information such as user account names, public IP addresses, and MAC addresses to a C2 server. The execution results of Command Prompt commands were received and sent back to the C2 server.
SectorE02 group was found to be active in Pakistan, Netherlands, United Kingdom, and India. The group distributed malicious Microsoft Excel documents and Microsoft Word documents disguised as fax copies and cyber security research programs documents for attack. They also prompted the target to download additional malicious code with download functions on the target systems to prepare for future attacks. Additionally, the group distributed Android malware disguised as messaging applications and carried out further attack. The Malware on the target devices was used to steal sensitive data such as call records, contacts, calendar events, SMS messages, files, and screen recordings, sending them to C2 servers according to the commands received from the C2 servers.
SectorE03 group was found to be active in Russia, Tajikistan, Kyrgyzstan, Vietnam, India, and Japan. The group targeted government and institutions of the Commonwealth of Independent States (CIS) countries and distributed malware, which executed PowerShell commands and download files following commands received via Telegram API on target systems. They carried out further attacks by distributing the Malware rewritten in Rust and Go languages and Windows shortcuts disguised as safe Internet use guides to steal computer name, username, volume serial number of C drive, and hash information of files in certain paths.
SectorE04 group was found to be active in Myanmar, Bhutan, China, Japan, Nepal and Singapore. The group disguised Microsoft Word documents as global leadership programs and Seniority List and conducted attack activities. They used malware on the target systems, and encoded data such as computer name and Command Prompt execution results in BASE64 before transmitting them to the C2 server.
SectorE05 group was found to be active in Belarus. The group disguised itself behind an event schedule document and distributed Windows Help (CHM) files to conduct attacks. They used malware on the targeted systems to collect computer names and usernames and sent them to a C2 server, downloading and executing malware to prepare for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In November 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorH03.
SectorH03 group was found to be active in India, Thailand, Ireland, and Japan. The group targeted Windows and Linux platforms and distributed a Windows shortcut (LNK) file disguised as an Indian military-related document. The group used remote control malicious code to execute various commands according to commands received from a C2 server, such as stealing system information, deleting specific directories or files, downloading and uploading files. In addition, the group also distributed malicious code with remote control functionality for Linux targets from the same C2 server to carry out attack activities. Moreover, the group also distributed Microsoft Excel documents disguised as seminar invitation lists, job recruitments, and monthly reports and stole data such as computer names, usernames, system information, file and folder information, process lists to send them to the C2 server.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of SectorS Group Activities
In November 2023, activities by a total of 1 hacking groups were identified, and the groups was SectorS01.
SectorS01 group was found to be active in Germany, Colombia, the United States, Canada, South Africa and Peru. The group distributed Adobe PDF documents disguised as invoices to carry out attack activities and installed remote control malware known as AsyncRAT and the Amadey botnet to steal system information such as computer name, username, and administrator permission to send to C2 servers.
SectorS hacking groups continue to carry the aim of collecting advanced information on governmental activities such as political, diplomatic and military activities, targeted at the whole world, including countries near the supporting government’s borders.
8. Characteristics of Cyber Crime Group Activities
In November 2023, activities by a total of 8 hacking groups were identified, and the groups were SectorJ03, SectorJ04, SectorJ09, SectorJ39, SectorJ57, SectorJ73, SectorJ85, and SectorJ131.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ03 group was found to be active in Kuwait, Jordan, Germany, Romania, the United States, and Ireland. The group disguised themselves as a foreign ministry and sent phishing emails to deliver PE file format normal files and compressed files containing malicious code.
SectorJ04 abused the On-Premise SysAid server vulnerability (CVE-2023-47246) and used a WebShell and ultimately used PowerShell commands to download and execute the Cobalt Strike.
SectorJ09 group has maintained the traditional hacking method of collecting users’ names, addresses, emails, phone numbers, and credit card payment information on payment pages by inserting obfuscated skimming scripts on web sites.
SectorJ39 group was found to be active in in China, Kazakhstan, United Arab Emirates, United States, and Israel. The group used malicious code in the form of Microsoft Word documents disguised as investigation documents. When the target of the attack executed the document, additional malicious code was downloaded and executed through an exploit code.
SectorJ57 group was found to be active in Germany, France, the United States, and Indonesia. The group used phishing mails with compressed file download links, and through the Visual Basic Script Malware in the compressed file, additional Malware was downloaded and executed according to the attacker server command.
SectorJ73 group used malicious code disguised as WinSCP, a file transfer tool between local and remote computers for financial gains and ultimately used Rhysida Ransomware for the purpose of financial gain.
SectorJ85 group obtained credentials from employees of the target organization using social engineering techniques, and attempted security bypasses by impersonating the organization’s Helpdesk or IT personnel using the obtained credentials. Finally, they attempted data theft using ransomware or remote-control tools for financial gain.
SectorJ131 group was found to be active in Pakistan, Singapore, the Philippines, France, and Palestine. The group exploited a vulnerability (CVE-2023-46604) in Apache ActiveMQ to distribute cryptocurrency mining scripts.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
