Monthly Threat Actor Group Intelligence Report, January 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 December to 20 January 2024.
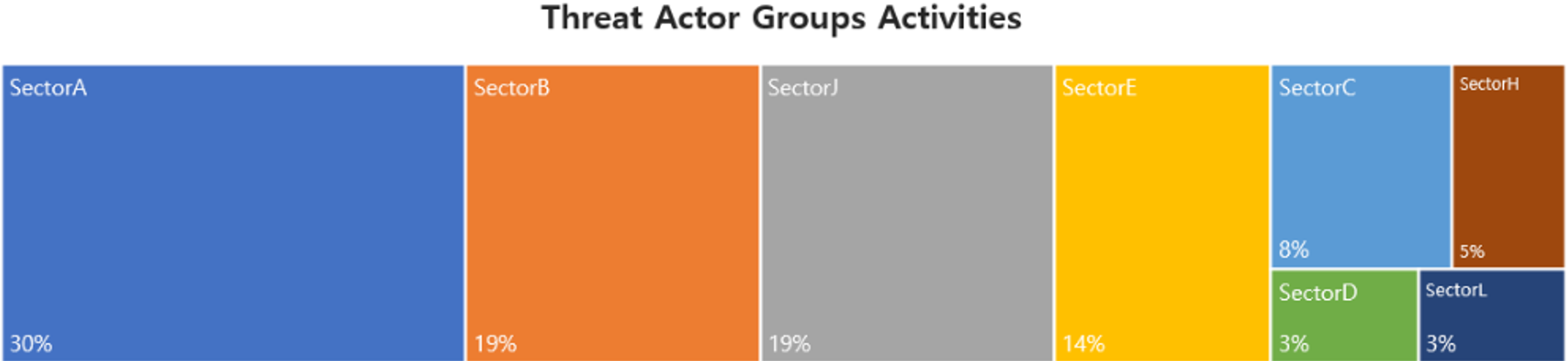
In January, activities by a total of 26 Threat Actor Groups were identified, in which activities by SectorA groups were the most prominent by 30%, followed by SectorB and SectorJ groups.
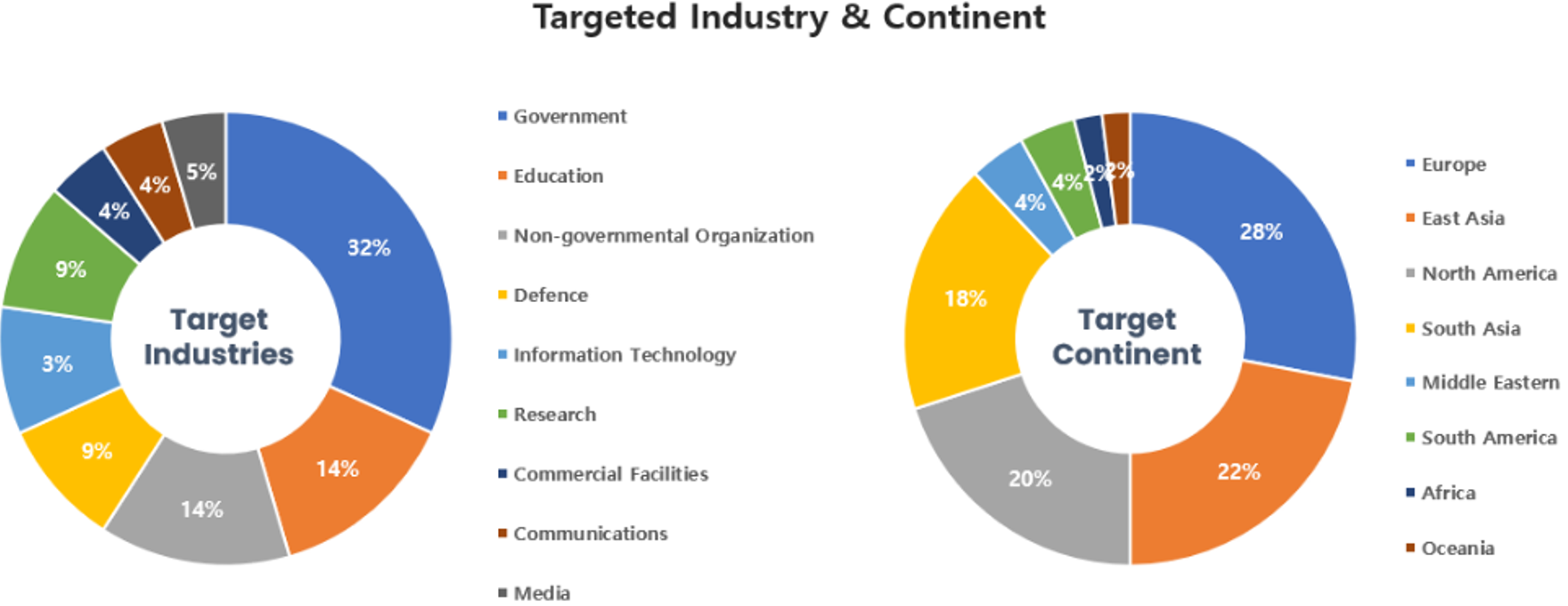
Threat Actors identified in January carried out the highest number of attacks on workers and systems in government agencies and education sectors. Regionally, Europe and East Asia were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In January 2024, activities by a total of 5 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, SectorA06, and SectorA07.
SectorA01 group was found to be active in Spain, the United States, Germany, Brazil, France, Serbia, Bangladesh, Turkey, Israel, India, Russia, Switzerland, and South Korea. The group used malware in the form of PE (Portable Executable) disguised as Putty software, mainly used for SSH and Telnet terminal connections.
SectorA02 group was found to be active in the United States, Romania, and South Korea. The group used malware in the form of a Windows shortcut (LNK) disguised as a unification strategy forum guide document, and ultimately downloaded additional malware through PowerShell commands to execute it in memory.
SectorA05 group was found to be active in Slovakia, South Korea, Hong Kong, China, Russia, Turkey, Thailand, Germany, and Singapore. The group used malware in the form of PE (Portable Executable) disguised as an update file for the free-to-use Foxit PDF Reader for individuals and institutions.
SectorA06 group was found to be active in Colombia. The group used Mach-O malware disguised as image files with the extension (JPG) to target macOS users.
SectorA07 group was found to be active in the United States. The group used malware disguised as a patent fee payment confirmation certificate in the form of a Windows Help file format (Compiled HTML Help), and ultimately downloaded and executed additional malware through PowerShell commands.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In January 2024, activities by a total of 6 hacking groups were identified, and the groups were SectorB01, SectorB22, SectorB38, SectorB73, SectorB75, and SectorB86.
SectorB01 group was found to be active in China, the United Kingdom, Taiwan, and South Korea. The group distributed malicious 7-Zip compressed file that contains a malicious Windows shortcut (LNK) file disguised as a document titled “China-Africa Relations” and a malicious JavaScript file to carry out their attack. Ultimately, they executed the penetration testing tool Cobalt Strike on the targeted systems and performed malicious actions according to various commands received from the C2 server.
SectorB22 group was found to be active in the United States and Myanmar. The group distributed a Windows disk image (ISO) file disguised as a note by the Association of Southeast Asian Nations (ASEAN) and ultimately used a malicious DLL file with download function to download additional malware from a C2 server in order to lay the groundwork for future attacks.
SectorB38 group was found to be active in the Philippines and Malaysia. The group distributed MS Rich Text Format (RTF) documents disguised as defense-related documents from the Ministry of Defense, pertaining to the United State releasing documents on a specific issue in Vietnam, and carried out attack activities. Ultimately, they downloaded additional malware from the C2 server through the download function on the target system, laying the groundwork for future attacks.
SectorB73 group was found to be active in the United States, United Kingdom, and Australia. The group carried out attacks by exploiting vulnerabilities in Cisco RV320 and RV325 router devices, and ultimately installed a WebShell on the target systems to perform malicious activities remotely.
SectorB75 group exploited the zero-day vulnerability of the Barracuda Networks Email Security Gateway Appliance to carry out malicious activities.
SectorB86 group carried out attack activities exploiting the zero-day vulnerability of the Ivanti Connect Secure (ICS) virtual private server (VPN) hardware and installed a WebShell on the targeted system to execute remote commands and laid the groundwork to execute additional attack commands. In addition, the group also distributed XMRig cryptocurrency miner and Rust-based malware to the target systems by exploiting the same vulnerability for their attacks.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In January 2024, activities by a total of 2 hacking groups were identified, and the groups were SectorC01, and SectorC14.
SectorC01 group was found to be active in Ukraine and Poland. The group used a malware in the form of a Windows shortcut (LNK) disguised as accounting documents from Polish Waters, a major National Institution responsible for managing water resources in Poland. The malware has the ability to receive commands from the attacker through the Internet Message Access Protocol (IMAP) and upload, download, and execute files.
SectorC14 group was found to be active in Czech Republic, Ukraine, and Romania. The group used decoy documents disguised as encrypted PDF files and induced the targets to execute malware disguised as a decryption program in PE (Portable Executable) format to decrypt the document for viewing.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In January 2024, activities by a total of 1 hacking groups were identified, and the groups was SectorD05.
SectorD05 group was found to be active in Seychelles. The group disguised their identity as a news reporter and requested the targets to share their opinions on an article on the Israel-Hamas War via phishing mails to carry out their attacks.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In January 2024, activities by a total of 3 hacking groups were identified, and the groups were SectorE02, SectorE04, and SectorE05.
SectorE02 group was found to be active in Hong Kong and the Netherlands. The group distributed MS Excel documents disguised as fax copies to carry out their attacks. Ultimately, they downloaded additional malware through the download function on the targeted system, laying the groundwork for future attacks.
SectorE04 group was found to be active in India and Nepal. The group distributed MS Word documents disguised as overseas travel guides to carry out their attack. Additionally, the group downloaded and executed remote template files on target systems to lay the groundwork for future attacks.
SectorE05 group was found to be active in China, Bangladesh, and Pakistan. The group distributed Adobe PDF documents disguised as overseas education recommendation documents and Windows Help (CHM) files disguised with the title “Project Application Version” to carry out attacks. Ultimately, they collected computer names and usernames from the target systems and after sending them to the C2 server, they downloaded and executed additional malware to lay the groundwork for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of SectorH Group Activities
In January 2024, activities by a total of 1 hacking groups were identified, and the groups was SectorH03.
SectorH03 group was found to be active in India, Japan, the Philippines, Canada, and Thailand. The group distributed MS PowerPoint documents disguised as quarterly reports on the Indigenization plan, targeting the Indian government and institutions for their attacks. Ultimately, they collected a list of files with specific extensions from the targeted systems and uploaded them to Oshi.at file storage, leaking confidential documents.
Hacking activities of SectorH hacking group consists of cybercrime hacking activities and government supported hacking activities. Diplomatic clashes has been ongoing between the backing country and the bordering country, so it is analyzed that they will continue activities to collect advanced information regarding government agencies’ military and politics to their need.
7. Characteristics of SectorL Group Activities
In January 2024, activities by a total of 1 hacking groups were identified, and the groups was SectorL03.
SectorL03 group was found to be active in the Netherlands. The group initially gained access by logging into the cPanel, a web hosting control panel used by the targeted system, using the IP address of a virtual private network (VPN) provider. They then proceeded to carry out various malicious activities according to commands received from a C2 server using a reverse shell on the targeted system.
Hacking activities of SectorL hacking groups that continue to date are seen to be aiming to collect advanced information regarding governmental activities such as political, diplomatic, military activities in nearby countries. However, considering that they have expanded their targets to other areas recently, the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology are analyzed to have been increased.
8. Characteristics of Cyber Crime Group Activities
In January 2024, activities by a total of 7 hacking groups were identified, and the groups were SectorJ01, SectorJ09, SectorJ57, SectorJ90, SectorJ138, SectorJ139, and SectorJ142.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ01 group was found to be active in the United States and the United Kingdom. The group distributed malware in the form of a Microsoft App Package (MSIX) disguised as an installation manager program.
SectorJ09 group maintained the existing hacking method of collecting usernames, addresses, emails, phone numbers, and credit card payment information by inserting obfuscated skimming scripts on websites.
SectorJ57 group was found to be active in the United States. The group used obfuscated JavaScript malware and ultimately attempted to control the targeted systems using open-source RAT (Remote Access Trojan) malware.
SectorJ90 group was found to be active in the United States and the Netherlands. The group used malware in the form of Visual Basic Script (VBS) files or Microsoft Installer (MSI) malware with embedded JavaScript malware. The final JavaScript malware executed in the attack has the ability to save and transfer the screen of the target system as an image file.
SectorJ138 group disguised their identity as Microsoft’s services or other companies and delivered messages with malicious links on Microsoft Teams to induce the targets to access the link. Ultimately, the group seized access privileges of the target system for Initial Access Broker (IAB) activities.
SectorJ139 group was found to be active in the United States and Canada. The group used Search Engine Optimization (SEO) poisoning attack techniques to lure unsuspecting users to phishing sites that impersonated official websites of legitimate softwares such as Zoom and TeamViewer.
SectorJ142 was found to be associated with other cybercrime groups that engage in Initial Access Broker (IAB) activities and used Black Basta Ransomware to encrypt files for financial gain, targeting systems that have been compromised by initial access brokers.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
