2023 Activities Summary of SectorJ groups (ENG)
Activity of SectorJ Group
Unlike other government-supported hacking groups, cybercrime SectorJ hacking groups steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
Among the SectorJ hacking groups, activities by a total of 78 subgroups were identified in 2023, with the activity of SectorJ94 group being the most prominent.
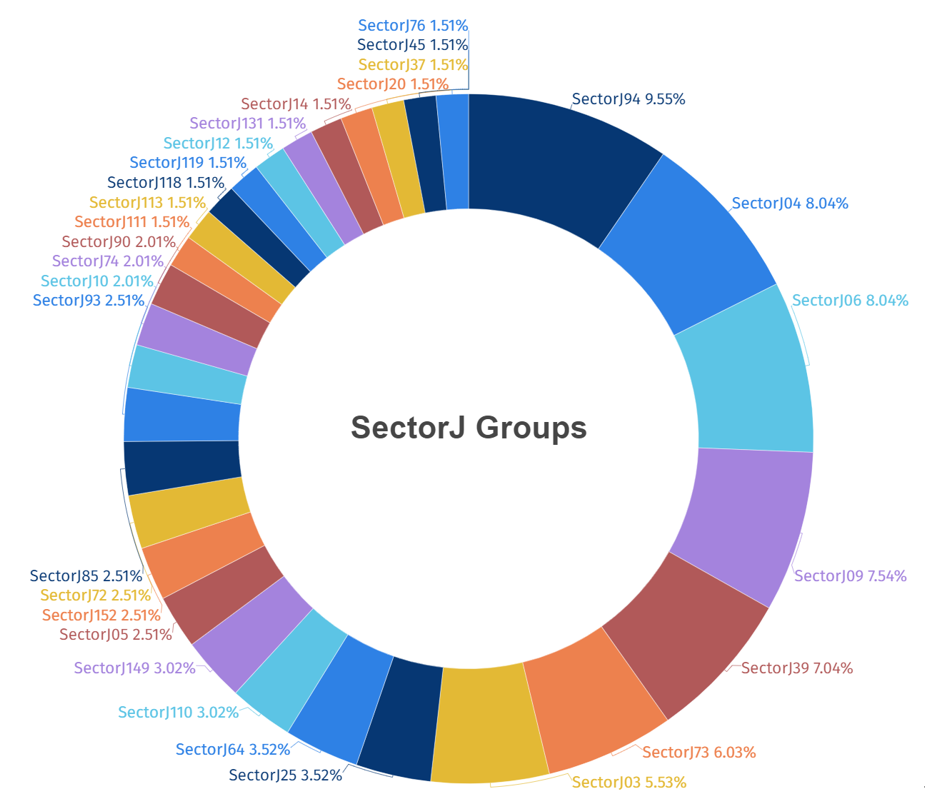
[Figure 1: Statistics of Activities of Top 30 SectorJ Groups identified in 2023]
SectorJ hacking groups identified in 2023 carried out the highest number of attacks on workers and systems in government agencies, followed by financial sectors.

[Figure 2: Statistics of Industries Targeted in 2023]
The following map illustrates the countries targeted by SectorJ groups in 2023, with darker shades of red indicating higher frequencies of attacks. This shows that SectorJ Group conducted the most hacking activities on the United States, located in the North American continent.
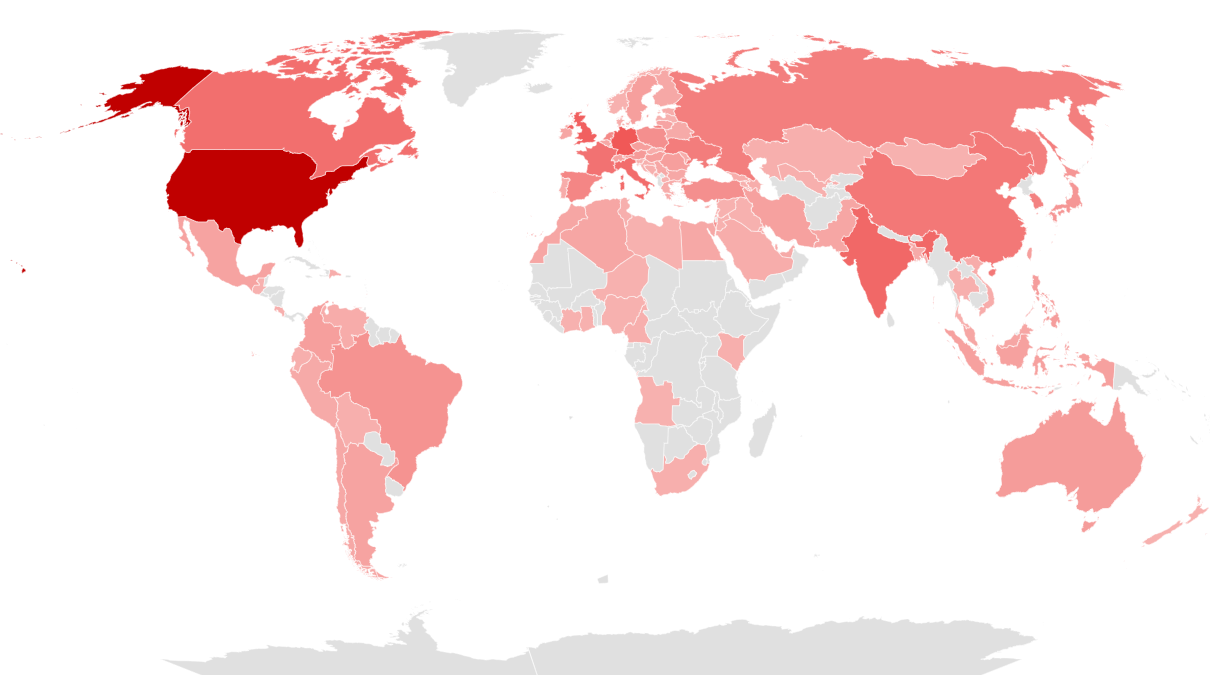
[Figure 3: Countries Targeted by SectorJ Group in 2023]
Initial Access Route of SectorJ Group
Among the initial access routes used by SectorJ groups, Exploit Public-Facing Application was found to be the most prominently used access route used in 2023.
Cyber Crime hacking groups like Sector are confirmed to have utilized exploit attacks on public-facing systems as the initial penetration pathway to conduct widespread cyberattack activities targeting systems affected by specific vulnerabilities, rather than targeting specific individuals or organizations.
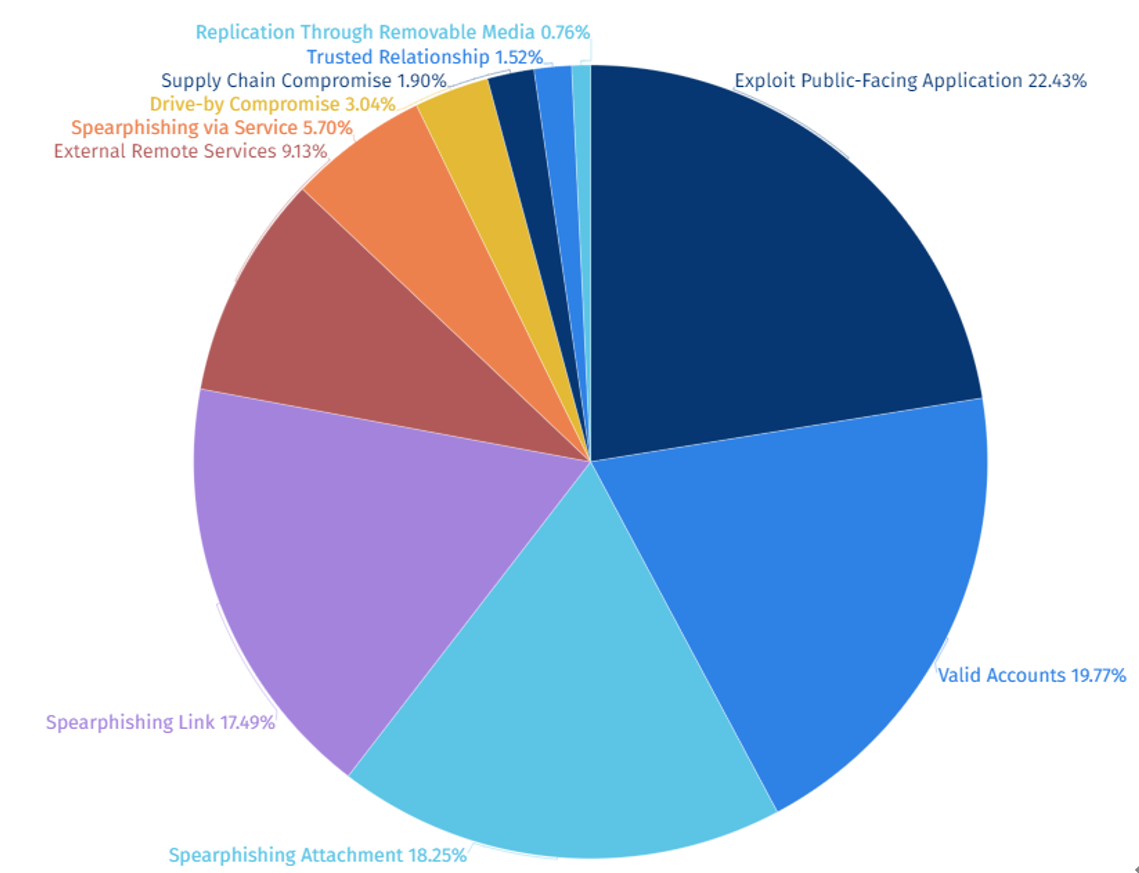
[Figure 4: Statistics of Initial Access Routes used by SectorJ Groups]
Vulnerabilities Exploited by SectorJ Group
Among the top 5 vulnerabilities exploited by SectorJ groups, CVE-2020-1472 (Microsoft Netlogon Privilege Escalation Vulnerability) and CVE-2023-34362 (MOVEit Transfer SQL Injection Vulnerability) were most prominently exploited in 2023.
SectorJ group is confirmed to have extensively utilized the CVE-2020-1472 (Microsoft Netlogon Privilege Escalation Vulnerability) due to its ability to secure persistence, evade detection, acquire privileges for accessing sensitive data, and perform lateral movement, thus potentially spreading the scope of damage.
Additionally, the group exploited CVE-2023-34362 (MOVEit Transfer SQL Injection Vulnerability), enabling them to steal sensitive data through attacks on externally accessible web applications or gain access to the target’s internal network. This access can be leveraged for various attacks such as ransomware deployment, cryptocurrency mining.
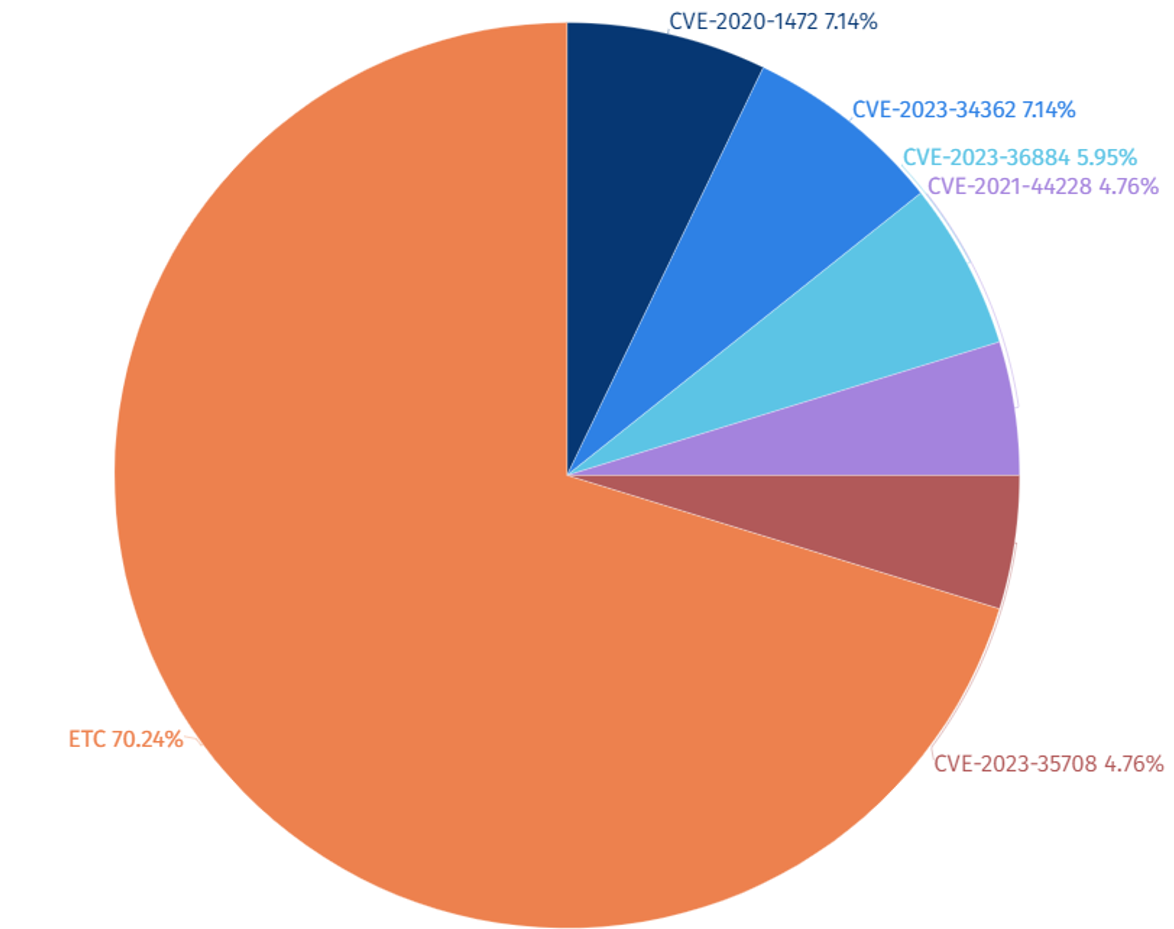
[Figure 5: Statistics of Top 5 Vulnerabilities Exploited by SectorJ Group in 2023]
|
Vulnerability |
Classification |
Target System |
|
CVE-2020-1472 |
Privilege Escalation Vulnerability |
Microsoft Netlogon |
|
CVE-2023-34362 |
SQL Injection Vulnerability |
MOVEit Transfer |
|
CVE-2023-36884 |
Remote Code Execution Vulnerability |
Microsoft Windows Search |
|
CVE-2021-44228 |
Remote Code Execution Vulnerability |
Apache Log4j2 |
|
CVE-2023-35708 |
Privilege Escalation Vulnerability |
MOVEit Transfer |
[Table 1: Top 5 Vulnerabilities Exploited by SectorJ Group in 2023]
SectorJ Group Attack Target Systems Statistics
Software vulnerabilities are typically categorized into server and client types. Hacking groups, strategically positioned at the heart of networks, exploit vulnerabilities within server systems to facilitate further attacks on internal networks.
Among the top 5 attack target systems by SectorJ groups, the greatest number of attacks were carried out on the Oracle WebLogic Server, the web application server in 2023.
This is believed to be aimed at establishing a foothold to infiltrate internal organizational systems and for the purpose of exfiltrating high-value information, thus making server-type systems the primary target of the attacks.
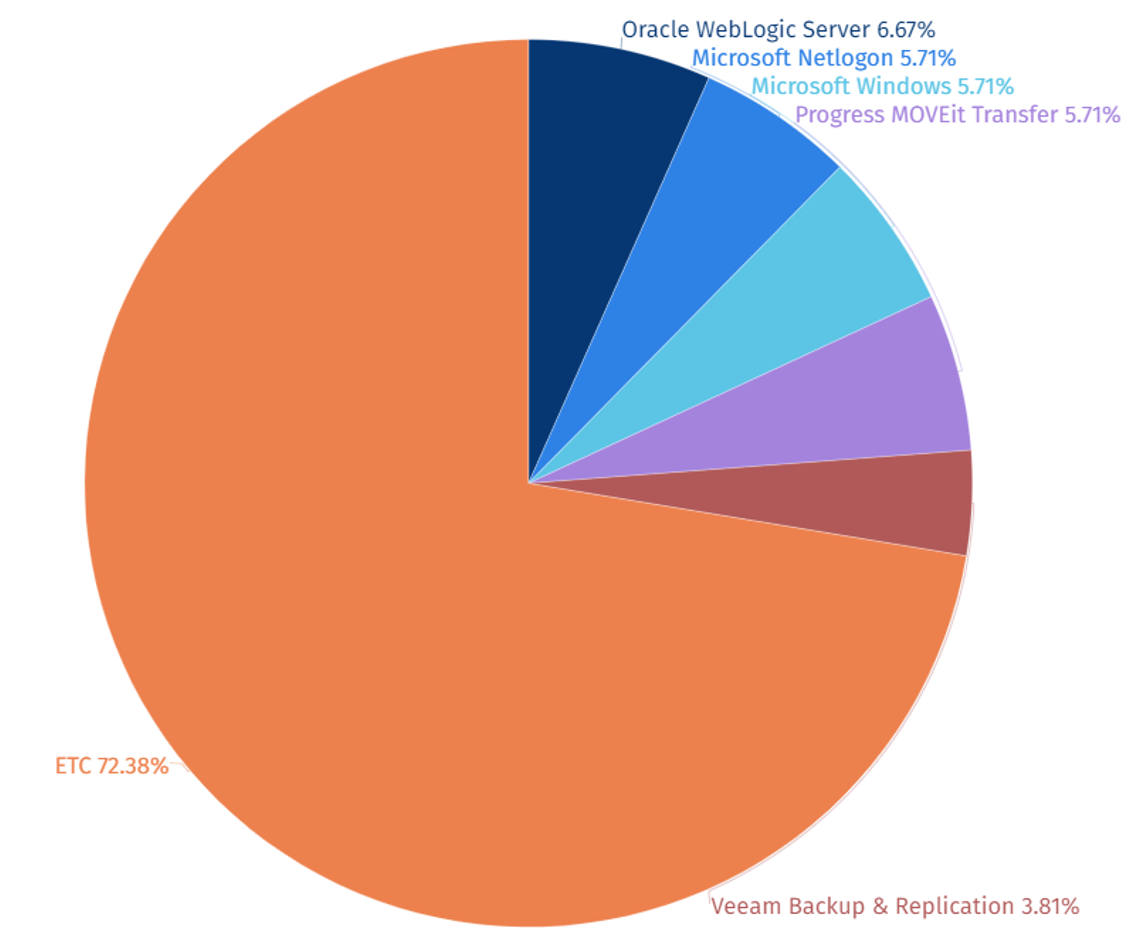
[Figure 6: Statistics of Top 5 Attack Target Systems of SectorJ Group in 2023]
Open Source and Freeware Tools Utilized by SectorJ Group
Among the top 5 open source and freeware tools utilized by SectorJ groups, the penetration testing tool “Cobalt Strike” was identified as the most frequently used tool in 2023.
It is analyzed that Cobalt Strike was most utilized due to its ability to efficiently control targets through various functions such as privilege escalation, information exfiltration, and command and control (C2) communication.

[Figure 7: Statistics of Top 5 Open Source and Freeware Tool used by SectorJ Group in 2023]
|
Tool Name |
Function |
|
Cobalt Strike |
Penetration Testing Tool |
|
PsExec |
Remote Execution Program |
|
AnyDesk |
Remote Control Program |
|
Mimikatz |
Windows Credential Information Collection Tool |
|
Telegram |
Messenger Program |
[Table 2: Top 5 Open Source and Freeware Tool used by SectorJ Group in 2023]
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
