Monthly Threat Actor Group Intelligence Report, March 2024 (ENG)
This report is a summary of Threat Actor group activities analyzed by the NSHC ThreatRecon team based on data and information collected from 21 February 2024 to 20 March 2024.
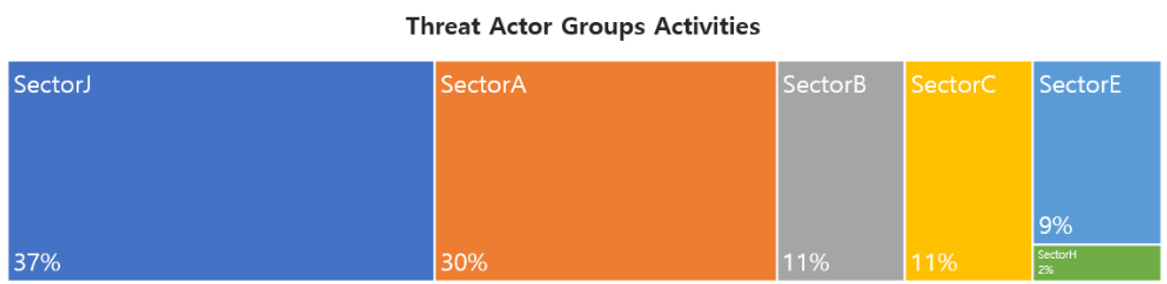
In March, activities by a total of 33 Threat Actor Groups were identified, in which activities by SectorJ groups were the most prominent by 37%, followed by SectorA and SectorB groups.
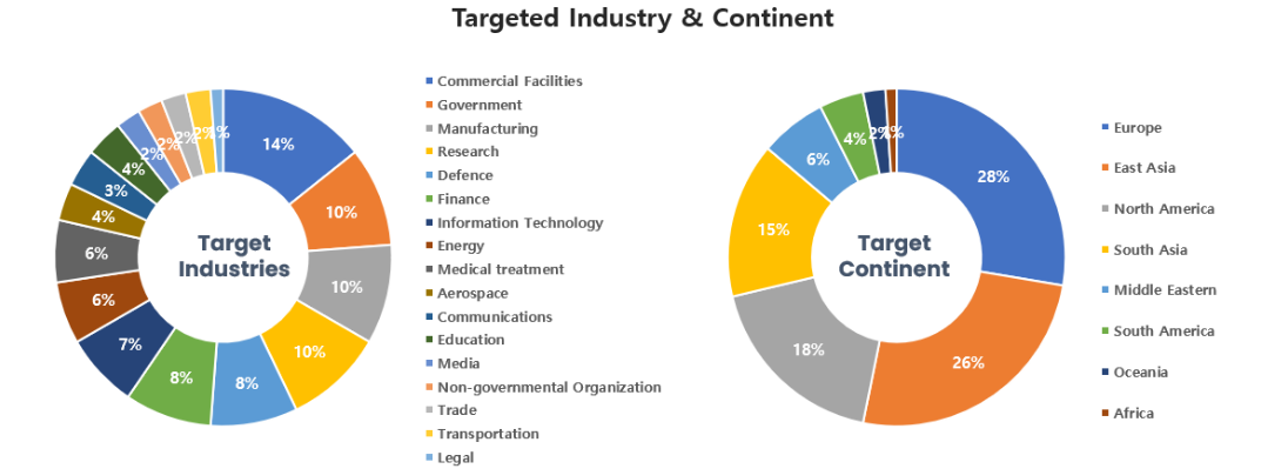
Threat Actors identified in March carried out the highest number of attacks on workers and systems in government agencies and commercial sectors. Regionally, Europe and East Asia were seen as the continents with the highest number of hacking activities targeted on.
1. Characteristics of SectorA Group Activities
In March 2024, activities by a total of 4 hacking groups were identified, and the groups were SectorA01, SectorA02, SectorA05, and SectorA07.
SectorA01 group was found to be active in South Korea, Taiwan, and the United States. The group distributed malicious Python packages through the official Python repository, Python Package Index (PyPI), and ultimately used malware with information gathering and remote-control capabilities.
SectorA02 group was found to be active in China and South Korea. The group used phishing emails pretending to be officials from the North Korean Human Rights Information Center and induced the execution of malware disguised as a security column document inside a compressed file attached to the email in the form of a Windows shortcut (LNK). The final executed malware used cloud services such as Yandex and pCloud and performed functions such as information gathering and remote control.
SectorA05 group was found to be active in South Korea, Pakistan, the United States, Hong Kong, the United Kingdom, France, Romania, Norway, Russia, and China. The group used malware in the form of Windows shortcut (LNK) files disguised as lecture request forms, and downloaded additional malware through the Dropbox API, ultimately using open-source remote control tools.
SectorA07 group was found to be active in Russia and South Korea. The group disguised their identity as a virtual currency exchange and induced the execution of malware in the form of a Windows shortcut (LNK) disguised as a personal information collection consent form. The group also used Visual Basic Script and batch script malware to collect information and perform various functions according to command control.
Hacking activities of SectorA hacking groups that continue to date aim to collect advanced information regarding South Korean governmental activities such as political, diplomatic activities, while targeting hacking activities on the whole world to secure financial resources at the same time. This aim for hacking activities has continued over a long period of time and is expected to be carried on without changes for some time.
2. Characteristics of SectorB Group Activities
In March 2024, activities by a total of 5 hacking groups were identified, and the groups were SectorB22, SectorB71, SectorB86, SectorB92, and SectorB93.
SectorB22 group was found to be active in Portugal, Russia, and Taiwan. The group distributed malware known as PlugX through infected USB devices for their attacks. The group executed the malware’s remote-control function on targeted systems and performed various malicious actions according to commands received from the C2 server.
SectorB71 group was found to be active in Tibet, China, Malaysia, India, Taiwan, Hong Kong, Australia, and the United States. The group took advantage of international interest in the Tibetan Buddhist festival, Monlam, to carry out watering hole attacks targeting Tibetans by distributing malicious droppers for Windows and macOS when visiting a specific Monlam festival website. The group also executed malware with remote-control capabilities on targeted systems, carrying out various malicious activities according to commands received from the C2 server.
SectorB86 group was found to be active in South Korea, Slovakia, China, India, and the United States. The group carried out attacks targeting government and institutions, energy, and financial industries by exploiting vulnerabilities in Ivanti Connect Secure and Policy Secure solutions and distributing malwares The group also downloaded and executed cryptocurrency mining malware on the targeted systems.
SectorB92 group was found to be active in Egypt, Pakistan, Taiwan, France, Switzerland, Greece, Macau, South Korea, Algeria, the United States, China, the United Kingdom, Thailand, Singapore, India, Hong Kong, South Africa, and Japan. The group exploited vulnerabilities in publicly accessible servers on the internet to gain access and distribute various types of malwares.
SectorB93 group was found to be active in the United States. The group carried out attacks targeting the defense industry by exploiting vulnerabilities in the Ivanti Connect Secure solution to distribute malware.
Hacking activities of SectorB hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, and is targeted at the whole world.
3. Characteristics of SectorC Group Activities
In March 2024, activities by a total of 3 hacking groups were identified, and the groups were SectorC01, SectorC04, and SectorC08.
SectorC01 group was found to be active in the United States, Israel, France, Germany, Ukraine, Sweden, Belgium, Brazil, Latvia, Lithuania, Norway, Poland, South Korea, United Kingdom, Czech Republic, Italy, Jordan, Montenegro, Slovakia, Turkey, United Arab Emirates, and Spain. The group installed a modified malware on routers with weak security settings, which allowed them to remotely control the devices and prepare a foothold for additional cyberattacks, such as credential harvesting and malware distribution.
SectorC04 group was found to be active in Latvia. The group used an Adobe PDF document disguised an invitation to a wine tasting event for diplomats and ultimately used malware to perform information gathering and remote-control functions.
SectorC08 group was found to be active in Russia and Ukraine. The group used malware disguised as a document related to the Imperial Guard in the form of a Portable Executable (PE), and ultimately attempted to steal information using the remote-control tool UltraVNC.
Hacking activities of SectorC hacking groups that continue to date are seen to be aiming to collect advanced information on governmental activities such as political, diplomatic activities, targeted at the whole world, including countries near the supporting government’s borders.
4. Characteristics of SectorD Group Activities
In March 2024, activities by a total of 1 hacking groups were identified, and the groups was SectorD15.
SectorD15 group was found to be active in Germany, United Arab Emirates, India, Israel, Iran, Romania, Turkey, and Albania. The group used fake job offers and topics on Israel-Hamas war to target the aerospace and defense industries in Middle Eastern countries, ultimately using malware to collect credentials and information through phishing websites and perform malicious activities through remote-control function of the malware.
SectorD hacking groups mostly served hacking activities targeted on countries in political conflicts with supported government, and the group is recently seen to be collecting advanced information such as political, diplomatic activities of individuals or governments against the supporting government.
5. Characteristics of SectorE Group Activities
In March 2024, activities by a total of 3 hacking groups were identified, and the groups were SectorE01, SectorE04, and SectorE05.
SectorE01 group was found to be active in Pakistan. The group distributed Windows shortcut (LNK) files disguised as documents containing password information necessary to open Adobe PDF documents and carried out attacks. The group downloaded and executed malware written in Go lang on the targeted systems.
SectorE04 group was found to be active in Canada, China, Sri Lanka, and Maldives. The group distributed Windows shortcut (LNK) files disguised as Special Envoy Speech or MS Word documents disguised as employee guide documents and executed malware on the targeted systems to perform various malicious activities according to commands received from the C2 server.
SectorE05 group was found to be active in Pakistan and Hong Kong. The group distributed MS Word documents disguised as resumes and executed malware on the targeted systems and registered a curl command in the task scheduler to send usernames and computer names to a C2 server. The group then downloaded and executed additional malware to lay the groundwork for future attacks.
Hacking activities of SectorE hacking groups that continue to date are seen to be aiming to collect advanced information regarding such as political, diplomatic, military activities. However, considering that they have expanded their targets to East Asian countries including China and other areas recently, it is analyzed that the proportion of hacking activities to collect advanced information related to politics, diplomacy, and technology from these countries have increased.
6. Characteristics of Cyber Crime Group Activities
In March 2024, activities by a total of 17 hacking groups were identified, and the groups were SectorJ21, SectorJ25, SectorJ40, SectorJ45, SectorJ64, SectorJ74, SectorJ85, SectorJ94, SectorJ110, SectorJ113, SectorJ146, SectorJ147, SectorJ148, SectorJ150, SectorJ153, SectorJ154, and SectorJ155.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
SectorJ21 group was found to be active in Slovenia. The group exploited the Program Compatibility Assistant Service (pcalua.exe) and created a task scheduler to continuously run malware. The group also downloaded and executed additional malware from a C2 server, laying the groundwork for future attacks.
SectorJ25 group was found to be active in Brazil, the United Kingdom, and France. The group distributed a cryptojacker that mines cryptocurrency by exploiting the Atlassian Confluence Server and Data Center remote code execution vulnerability (CVE-2022-26134).
SectorJ40 group was found to be active in France. The group performed DLL side loading attacks targeting DeviceEnroller.exe, one of the default files in the Windows system, and distributed the Dridex malware through this method.
SectorJ45 group was found to be active in the United Kingdom and India. The group distributed malicious MS Word files with Visual Basic for Applications scripts attached to spear phishing emails disguised as invoices.
SectorJ64 group was found to be active in the United States, Iran, Colombia, and South Korea. The group distributed a cryptojacker that mines cryptocurrency.
SectorJ74 group was found to be active in Germany, the United States, Saudi Arabia, Spain, Italy, the Czech Republic, and South Korea. The group distributed malicious Adobe PDF files that downloaded malicious JavaScript by attaching the files to spear phishing emails disguised as hotel reservation refund information.
SectorJ85 group was found to be active in the United States, Canada, and Thailand. The group constructed phishing websites similar to specific corporate domains and collected credentials of users related to the company through typosquatting technique.
SectorJ94 group was found to be active in New Zealand, Germany, the United States, Ukraine, Italy, Japan, the Czech Republic, Canada, and South Korea. The group distributed a ZIP compressed file containing an HTML file through spear phishing emails and collected NTLM hash information of the attacked system to an external SMB server through the HTML file.
SectorJ110 group was found to be active in the United States, Ukraine, and the Czech Republic. The group distributed malicious MS Word files containing PowerShell scripts through phishing emails disguised as invoices.
SectorJ113 group was found to be active in Taiwan, Germany, the United States, Ukraine, India, and Colombia. The group distributed the RA Group Ransomware with the aim of securing financial profit.
SectorJ146 group was found to be active in the Netherlands, the United States, Russia, and Vietnam. The group disguised malicious attachments in phishing emails disguised as criminal investigation materials and induced the target to execute it.
SectorJ147 group was found to be active in Taiwan, Germany, the United States, Ukraine, India and Columbia. The group stole personal information entered by users through a phishing site disguised as an investment platform.
SectorJ148 group was found to be active in the United States. The group attached a QR code disguised as an Adobe PDF document related to a bid proposal which leads to a phishing site. The group ultimately collected credentials entered by the targets on the phishing site.
SectorJ150 group was found to be active in the Netherlands, Germany, the United States, Spain, Singapore, Ireland, the United Kingdom, Canada, and Thailand. The group distributed backdoor malware through vulnerabilities in Ivanti Connect Secure and Policy Secure.
SectorJ153 group distributed PowerShell script that performs backdoor functions through JetBrains TeamCity vulnerabilities (CVE-2023-42793, CVE-2024-21798).
SectorJ154 group was found to be active in Russia. The group distributed a stealer malware, which steals system information and screenshots of the targeted system, through phishing emails pretending to be a construction company.
SectorJ155 group was found to be active in Russia. The group distributed malware by compressing a batch script file disguised as an Adobe PDF file through phishing emails and exploited the WinRAR vulnerability (CVE-2023-38831) to remotely control targeted systems, steal data, and send it through the Telegram messenger.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
