Activity of Hacking Group Targeted Financial Industry in 2023 (ENG)
Executive Summary
This report is a summary of Threat Actor group activities in the financial industry analyzed by the NSHC ThreatRecon team based on data and information collected in 2023.
This report contains detailed analysis on the hacking activities of the Threat Actor groups targeting the financial industry including banks, finance companies and institutions, and insurance companies.
Statistics of Hacking Group Activity
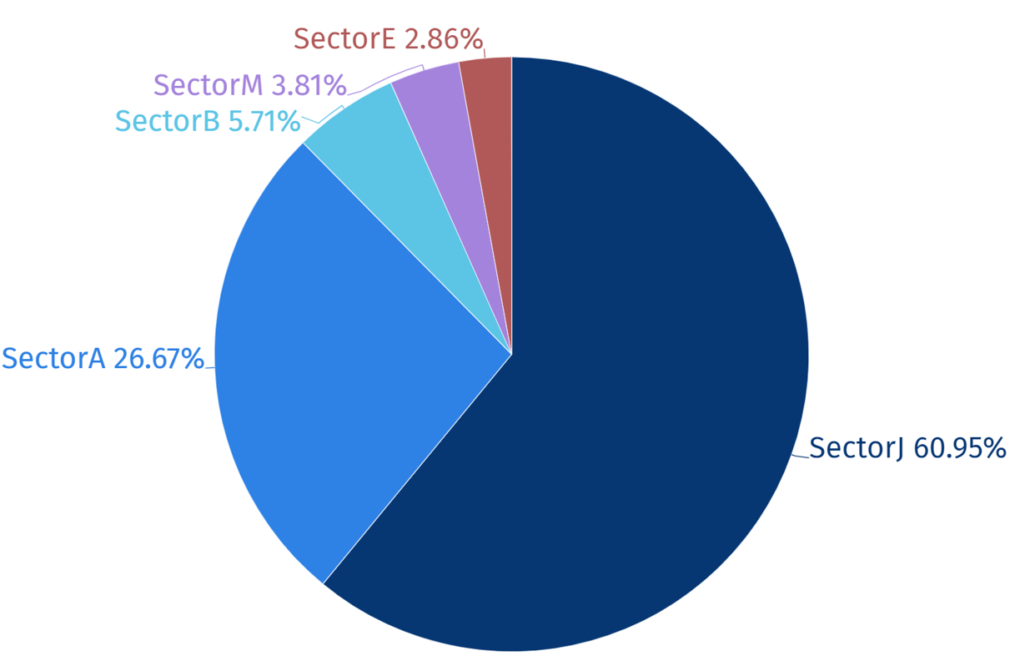
In 2023, activities by a total of 34 Threat Actor Groups were identified and among the top 5 Threat Actor groups, activities by SectorJ groups were the most prominent by 60%, followed by SectorA and SectorB groups.
Unlike other government-supported hacking groups, they steal online information that have monetary value in real life, hack specific companies and organizations to disseminate ransomwares in the intranet, or steal important industrial confidential information and demand for ransom in return.
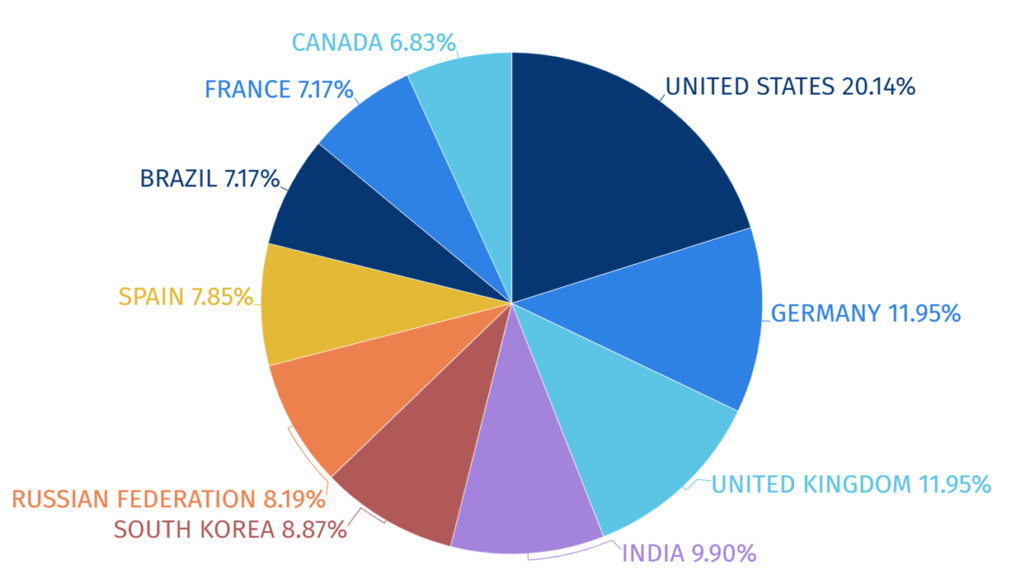
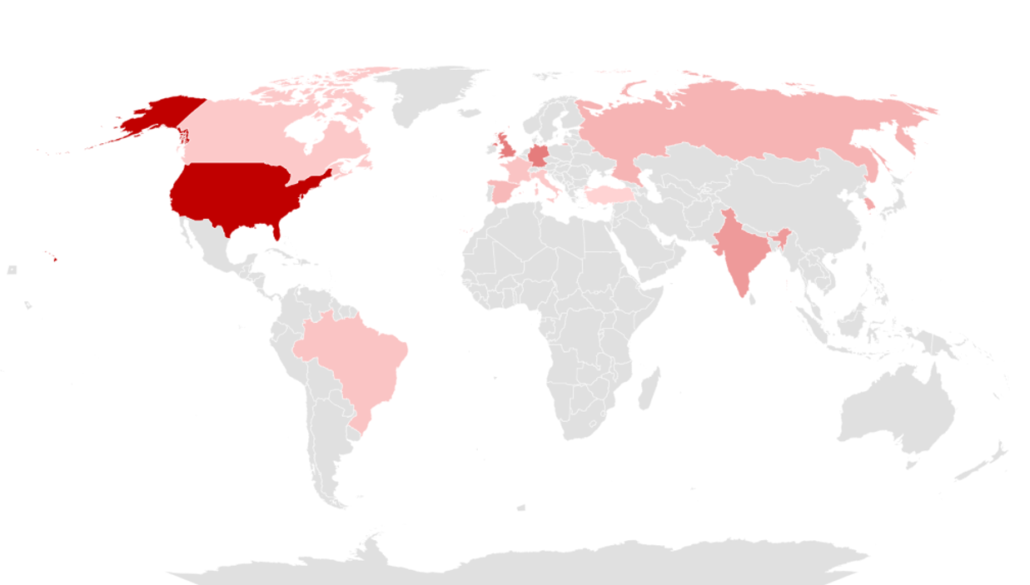
Statistics of Target Countries
In 2023, the attacks on the United States were the most prominent by 20% of the top 10 attack target countries, followed by Germany and the United Kingdom.
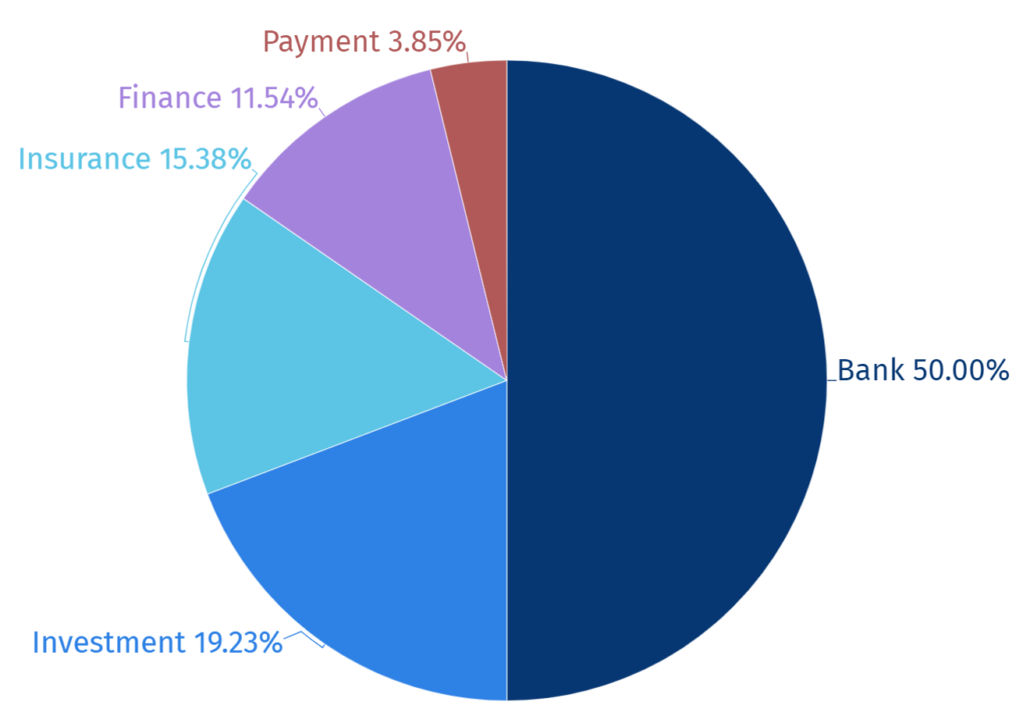
Statistics of Target Companies
In 2023, a total of 26 target companies in the financial industry were identified and attacks on banking sector were the most prominent by 50%.
The groups also carried out attacks on other finance companies and institutions as well as insurance companies.
Statistics of Initial Infiltration Route
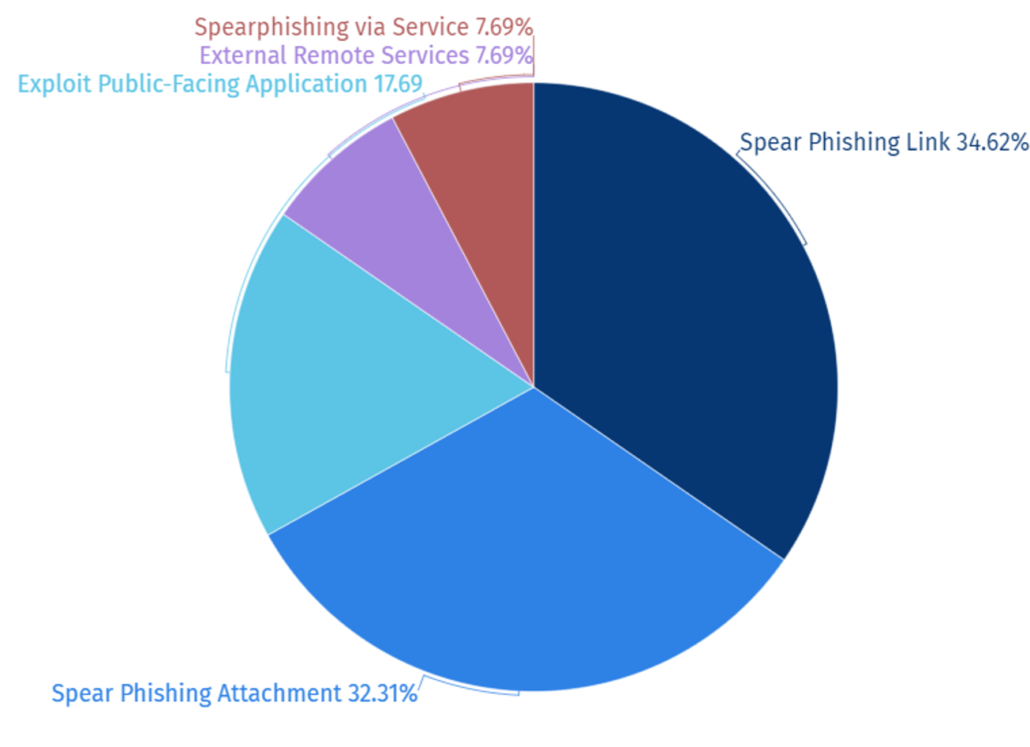
In 2023, distributing malicious URL and file attachments through spear phishing was the most prominent initial infiltration route among the top 5 routes.
Spear phishing attacks are social engineering attacks that target specific individuals or organizations which induce the target to enter their credentials through malicious links and execute malwares.
By disguising their identity as trusted personnel of the target, successful initial infiltration via the spear phishing route is highly likely which explains the prominence of spear phishing among other routes used by the hacking groups.
Statistics of Exploited Vulnerabilities
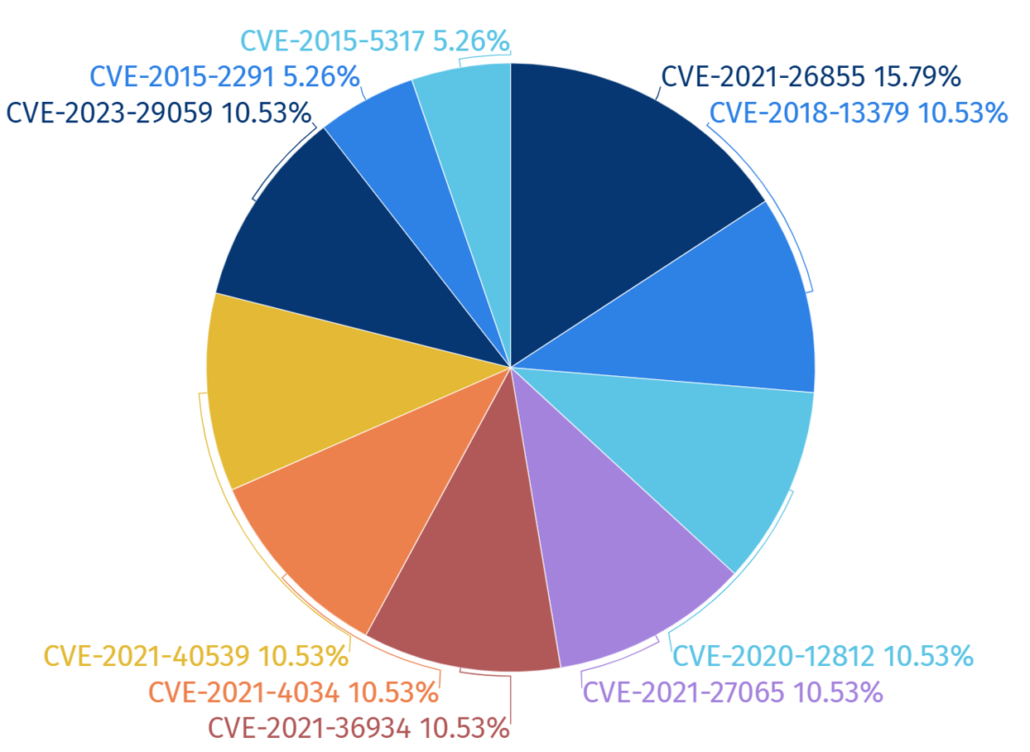
In 2023, among the vulnerabilities exploited by the hacking groups in their attacks, the exploitation of CVE-2021-26855, a Remote Code Execution (RCE) vulnerability found in Microsoft Exchange Server was the most prominent by 16%.
It was analyzed that the groups exploited this vulnerability while achieving the purpose of installing malware or software on target systems for their attacks.
|
Vulnerability |
Classification |
Target |
|
CVE-2021-26855 |
Remote Code Execution Vulnerability | Microsoft Exchange Server |
|
CVE-2018-13379 |
Path Traversal Vulnerability | Fortinet FortiOS |
|
CVE-2020-12812 |
Improper Authentication Vulnerability | Fortinet FortiOS |
|
CVE-2021-27065 |
Remote Code Execution Vulnerability | Microsoft Exchange Server |
|
CVE-2021-36934 |
Elevation of Privilege Vulnerability | Security Accounts Manager (SAM) Database |
|
CVE-2021-4034 |
Elevation of Privilege Vulnerability | Polkit |
|
CVE-2021-40539 |
Authentication Bypass Vulnerability | Zoho ManageEngine ADSelfService Plus |
|
CVE-2023-29059 |
embedded malicious code | 3CX DesktopApp |
|
CVE-2015-2291 |
Windows Denial-of-Service Vulnerability | Intel Ethernet Diagnostics Driver
(iqvw64.sys) |
|
CVE-2015-5317 |
Information Disclosure Vulnerability | Jenkins User Interface (UI) |
Statistics of Target System
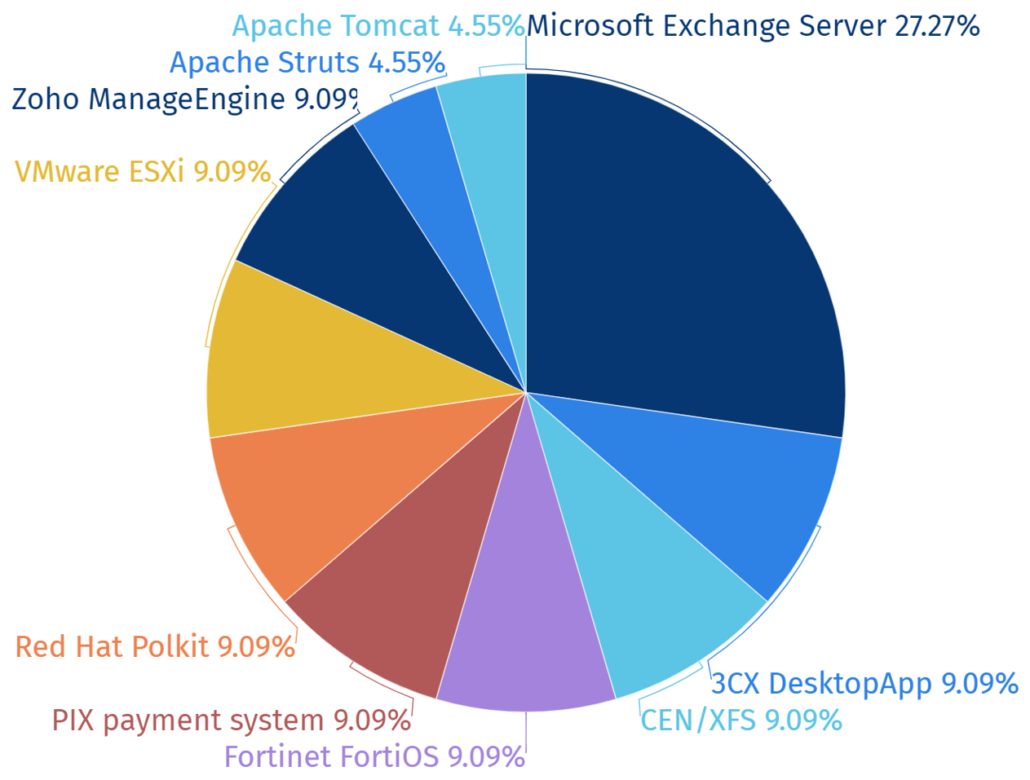
The software with vulnerabilities be classified into servers and clients, and the hacking groups locate themselves in the center of system networks to perform hacking activities through vulnerabilities in the server which allows them to perform additional attacks on internal networks with ease.
In 2023, it was confirmed that among the top 10 systems targeted by hacking groups, the most attacks were carried out on the widely used Microsoft email service product, Microsoft Exchange Server. This is believed to have been done in order to gain access to internal systems and steal valuable information.
Utilized Open Source and Freeware Tools
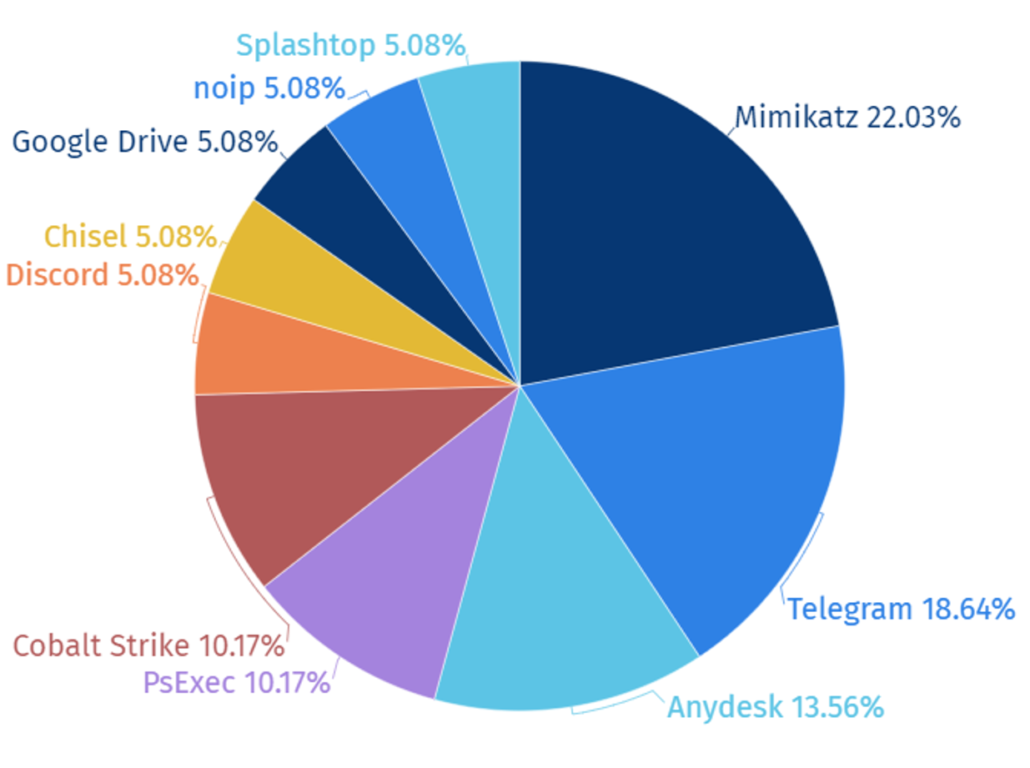
Hacking groups have been adopting the strategy of exploiting pre-developed open source and freeware tools, which is becoming one of their main strategies as the time and cost of developing new malware is reduced with little trace left in the invaded system.
In 2023, among the top 10 open source and freeware tools utilized by hacking groups, Mimikatz, used for privilege escalation, was the most prominently used tool with the percentage of 22%. Additionally, Telegram was also used in sending stolen data through Telegram channels or to control targeted systems through the Telegram API.
|
Name |
Function |
URL |
|
mimikatz |
Windows Credential Information Collection Tool | https://github.com/gentilkiwi/mimikatz |
|
Telegram |
Messenger Program | https://telegram.org/ |
|
AnyDesk |
Remote Controlling Program | https://anydesk.com/ |
|
PsExec |
Remote Execution Program | https://learn.microsoft.com/en-us/sysinternals/downloads/psexec |
|
Cobalt Strike |
Penetration Testing Tool | https://www.cobaltstrike.com/ |
|
Discord |
Messenger Program | https://discord.com/ |
|
Chisel |
Network Tunneling Program | https://github.com/jpillora/chisel |
|
Google Drive |
Google Cloud Service | https://www.google.com/drive/ |
|
No-IP |
IP Address Look-up Web Service | https://www.noip.com/ |
|
Splashtop |
Remote Controlling Program | https://www.splashtop.com/ |
|
ifconfig |
IP Address Look-up Web Service | http://ifconfig.me/ip |
CONCLUSION
This Report provides an overview of the various attack techniques and tools used by hacking groups targeting the financial industry in 2023 and highlights the diversification of their attack techniques and strategies.
Based on the statistics of hacking group activities, SectorJ group was found to have carried out the most hacking activities on the financial industry in 2023.
SectorJ engaged in information theft and ransomware distribution along with other attacks with the aim of securing financial resources. Such attacks often lead to significant damages such as data breaches and service disruptions, highlighting the pressing need for preventive measures and response systems.
Therefore, acquiring Cyber Threat Intelligence on the latest attack trends of hacking groups targeting the financial sector is essential in the development of proactive response systems that leverages on recent attack techniques and related data.
The full report detailing each event together with IoCs (Indicators of Compromise) and recommendations is available to existing NSHC ThreatRecon customers. For more information, please contact service@nshc.net.
